Penetration Testing in cyber security is a vital process that aids in evaluating an application’s security through hacker-style exploitation to expose and assess security risks. Security risks can be present in various areas such as system configuration settings, and, login methods.
It is also present in end-users’ risky behaviors which comes into play when a business gives the average end-user access to system-based processes. This can be mitigated through end-user computation risk management.
On this page
- What is Penetration Testing?
- Importance of Penetration Testing
- 3 Different Approaches To Penetration Testing
- Types of Penetration Testing
- Phases of Penetration Testing
- Methodology in Penetration Testing
- Best 7 Penetration Testing Tools
- Penetration Testing For Compliance
- Who Needs Penetration Testing?
- Penetration Testing Report
- Penetration Testing Cost
- For Pentesters: How To Become a Qualified Pentester?
What is Penetration Testing (In Cyber Security)?
Penetration testing is the process of evaluating the security of an application and exploiting found vulnerabilities and security risks within an asset like websites, servers, databases, networks, or mobile applications to see the extent of severity they pose to the security.
In a pentest, a security engineer finds security vulnerabilities in the application, network, or system, and helps you fix them before attackers get wind of these issues and exploit them. Pentesting is a non-negotiable fundamental step for any application or business owner.
Importance Of Penetration Testing
Penetration testing one’s assets is important for the following reasons:
- Identification of Vulnerabilities: Penetration testing helps identify vulnerabilities in computer systems, networks, and applications that can be exploited by attackers. This allows organizations to prioritize and fix these vulnerabilities before they can be exploited.
- Enhanced Security: Penetration testing helps organizations to enhance their security posture by identifying potential security gaps and improving their security controls.
- Meeting Compliance Requirements: Many regulatory and industry standards require regular penetration testing to ensure that organizations meet their security requirements. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires regular penetration testing of networks and applications that process credit card data.
- Cost-Effective: Penetration testing helps identify potential security threats in a cost-effective manner, as it allows organizations to identify and fix security issues before they become major security incidents.
These are just a few of the reasons that make penetration testing a valuable process in the continued maintenance of asset security.
3 Different Approaches To Penetration Testing
There are three approaches to penetration testing, they are:
- White/ Black/ Grey Box Penetration Testing
- Internal and External Penetration Testing
- Manual and Automated Penetration Testing
Every test is customized based on the needs of your organization. Factors that influence this decision are:
- Cost of penetration testing.
- Time taken for conducting the penetration test.
- Required invasiveness for the penetration test.
- Amount of information that you can provide.
- Frequency of the penetration tests.
- Scope of pentest
Let us check out these different approaches that you need to be aware of in further detail.
1. White/ Black/ Grey Box Penetration Testing
The varied approaches to pentesting are chosen depending on the level of information available to the testers as provided by the organization.
1.1 White Box Penetration Testing
In a white box test, the testers have complete knowledge of the system and complete access. The advantage, in this case, is that since the tester has unbridled access and knowledge of the system, including code base code quality, API documentation, and internal designs, the pentest can identify even remotely located vulnerabilities, thus giving a nearly complete picture of the security.
1.2 Black Box Penetration Testing
The tester here has no knowledge of the system and designs the test as an uninformed attacker. Black box penetration testing by third party requires the pentester to think outside the box and employ methods that a true hacker would carry out to break into a system. This would allow the detection, exposing, and exploitation of vulnerabilities to their fullest extent.
1.3 Gray Box Penetration Testing
As suggested by the name, this approach stands midway between white box pentesting and black box testing. The tester has only limited knowledge of the system. The advantage of this approach is that with the limited amount of knowledge, the tester has a more focused area of attack and thus avoids any trial-and-error method of attack.
2. Internal and External Penetration Testing
Internal and external penetration testing are pentests based on the environment and perspective from which a test is conducted.
2.1 Internal Pentest
An internal pentest is more concerned with testing your application from within by focusing on its internal environment. The pre-assumption, in this case, is that the attackers have been able to breach the outer layer and are already within the network.
External threats are riskier than internal ones as gaining access to the internal networks is a result of a breach in the external security protocols. Thus, beginning with an external pentest is a good idea.
2.2 External Pentest
This scenario simulates an attack from an outsider with access to the internet and no prior knowledge of the system. The tester will attempt to break into your system by exploiting vulnerabilities from outside and accessing internal data and systems.
Below are some of the external penetration tests that are done:
- Testing routers
- Firewall bypasses
- DNS footprinting
- Evasion of IPS/IDS
- Scanning and testing open ports
- SSH attacks
- Tests on proxy servers
3. Manual and Automated Penetration Testing
3.1 What Is A Manual Pentest?
In a manual penetration test, certified pentesters manually and methodically assess the security posture of the systems. Employing hacker-style techniques helps to break into the designated system and evaluate the vulnerabilities based on their exploitability and the impact of such an exploit.
Manual exploits are more in-depth and can result in the identification of vulnerabilities that may be missed by an automated pentest scanner. They can be carried out once or twice a year or when major upgrades or changes are made to an application.
With manual penetration testing, the results are all vetted to make sure there are no false positives thus saving organizations plenty of time and expense.
3.2 What Is An Automated Pentest?
An automated penetration test involves the use of a pentest tool that would probe into a target system and analyze the responses by referencing a vulnerability database. Automated pentest tools will produce scan results at a radically quicker pace and also help you categorize the vulnerabilities based on their severity.
You can integrate modern-day automated pentest tools with your SDLC and or CI/CD solutions to achieve continuous pentesting. This helps you turn pentest into a consistent process instead of a one-time affair.
Automated pentests are fast and mostly accurate but they come with the issue of false positives. Nevertheless, you can get around it by partnering with pentest companies that offer vetted scans to ensure zero false positives.
3.3 How does Penetration Testing differ from Vulnerability Assessment?
Penetration testing and vulnerability assessment are often used interchangeably. However, they are not one and the same. While penetration testing plays a huge role in the process of vulnerability assessment, they are two processes with some stark differences.
| Vulnerability Assessment | Penetration Testing |
|---|---|
| Vulnerability assessment is focused on detecting and categorizing vulnerabilities in a system. | Penetration testing involves exploiting vulnerabilities to draw insights about them. |
| It is a mostly automated process involving vulnerability scanning tools. | Penetration testing requires manual intervention on top of automated scanning. |
| It is almost impossible to achieve zero false positives with an automated vulnerability assessment. | Manual penetration testers can ensure zero false positives. |
| Vulnerability assessment often misses critical and complex vulnerabilities. | Thanks to the human element of penetration testing, it detects business logic errors that remain undetected in a vulnerability scan. |
| Automated vulnerability assessment takes significantly less time and money than pen testing. | Penetration testing is a consuming and expensive procedure and for good reason. |
Both these processes are complementary in nature and are usually performed together, in a combined process called VAPT, or Security Audit.
Types of Penetration Testing in Cyber Security
Penetration testing can be done for applications and even content management systems as explained below.
- Application-Based Penetration Testing
- CMS Penetration Testing (for Joomla, WordPress, Drupal, and more)
1. Application-Based Penetration Testing
1.1 Cloud Penetration Testing
Cloud penetration tests analyze the cloud computing environment and platforms for vulnerabilities that could be exploited by hackers. Cloud pentesting forms an essential component of cloud security as it reveals any potential weaknesses in the currently implemented security controls.
Such a pentest can be performed manually or through automated means and is often integrated into the cloud security strategy for optimal maintenance of security. Some of the commonly found vulnerabilities include
- Insecure APIs
- Server Misconfigurations
- Weak credentials
- Outdated software
- Insecure codes
1.2 Network Penetration Testing
The objective of a network penetration test is to find vulnerabilities in the network infrastructure, either on-premise or cloud environments such as Azure and AWS penetration testing. It is one of the basic tests, and a crucial one too to protect your data and the security of your application. In this test, a wide range of areas such as configurations, encryption, and outdated security patches, are tested and checked.
Below are some of the network penetration tests that are done:
- Testing routers
- Firewall bypasses
- DNS footprinting
- Evasion of IPS/IDS
- Scanning and testing open ports
- SSH attacks
- Tests on proxy servers
1.3 Web Application Penetration Testing
With the rise in web-based applications, huge amounts of data are stored and transmitted through them, making them attractive targets for cyber attackers. Organizations and individuals with web apps must conduct web application pentesting periodically to keep up with the latest attacks methodologies and security flaws. Some of the common vulnerabilities include:
- Wireless encryption and network traffic
- Unprotected access points and hotspots
- Spoofing MAC address
- Weak credentials
- DDoS Attacks
- SQL/Code Injections Attacks
- Cross-Site Scripting
- Misconfigured web servers
1.4 API Penetration Testing
An application Programming Interface is a set of standards that let applications communicate with each other. It enables developers to create customized experiences within a given application.
API penetration testing is the process that aims to find any vulnerabilities within the API for a web application by simulating the actions of a malicious user.
Some of the major security issues tested for during an API pentest are:
- Broken authentication flaws in identification measures.
- Broken authorization due to exposed endpoints.
- Exposure of data.
- Misconfigurations.
- Injection flaws such as SQL, command injections, and more.
1.5 Mobile Penetration Testing
In this type of pentesting, mobile applications are tested by expert penetration testers to find security vulnerabilities which can then be reported to the developers. Mobile penetration testing isn’t just applicable to android applications, but also for iOS, Native and Hybrid applications.
Mobile application penetration is done to gain access to sensitive data or disrupt the application’s functioning. Some of the major security issues in mobile apps include:
- Lack of transport layer protection
- Insecure Communication
- Insecure Authentication
- Weak Encryption
- Lack of Binary protection
1.6 Smart Contract Penetration Testing
Smart contract penetration testing is a process of evaluating a smart contract for security vulnerabilities and compliance with best practices. These are essential to safeguard the money put into them. Because all transactions on the blockchain are permanent, stolen money cannot be recovered if it is stolen.
2. CMS Penetration Testing (for Joomla, WordPress, Drupal, and more)
CMS or Content Management Systems like Drupal, WordPress, Joomla, and more are garnering increasing attention for providing an ideal content editing and management platform.
Here are some of the most common CMS platforms that require penetration testing:
2.1 WordPress Penetration Testing
Before starting a WordPress Penetration Test it is vital to seek permission from the respective WordPress site owner to avoid any legal complications later on. Using virtual machines for WordPress pentests is much advised.
Along with this, thorough scoping and establishing good rules of engagement are essential to avoid encroaching into assets that weren’t approved for scanning and identification of vulnerabilities.
2.2 Drupal Penetration Testing
Drupal is a popular choice for CMS. However, like every other CMS platform, Drupal has also faced its fair share of security bugs. In a Drupal penetration test, manual pentesters attempt to exploit vulnerabilities found during a scan using hacker-style methods.
This helps in estimating the level of damage that can be caused by vulnerabilities when they are maliciously exploited. Drupal is most vulnerable to attacks such as XSS, DoS, and SQL injections among others.
2.3 Joomla Penetration Testing
Joomla Penetration Testing involves attacking and exploiting vulnerabilities within a Joomla website using automated or manual methods to gain access. Joomla has over 909 CVEs that have been recorded so far, making them popular targets for hacks.
Such hacks can be fuelled by websites running on outdated versions or having unpatched vulnerabilities in their extensions or themes.
8 Phases of Penetration Testing: How It Is Performed
Rigorous and detailed planning for penetration testing is required to successfully conduct one.
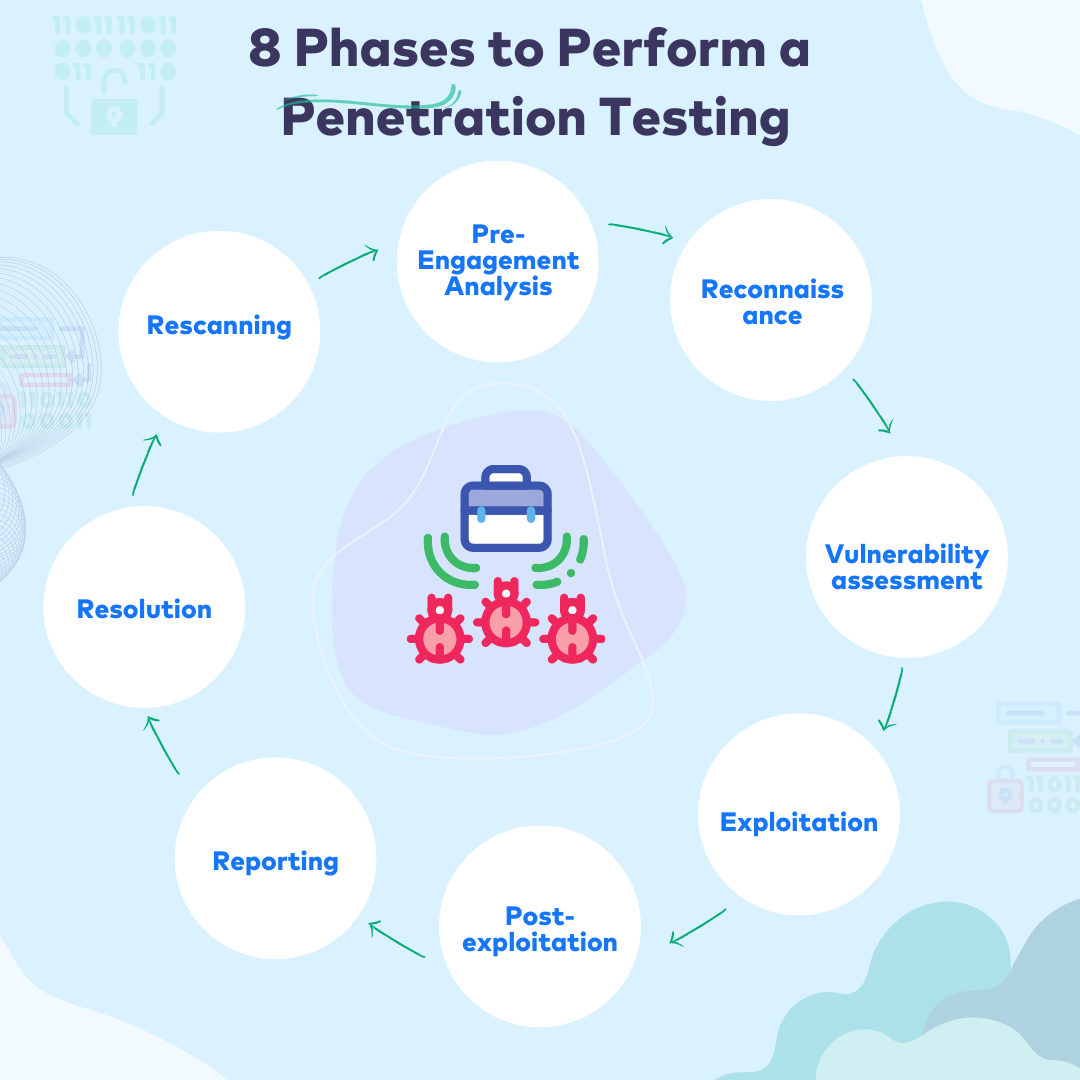
There are 8 phases of penetration testing in cyber security:
Step 1: Pre-Engagement Analysis
Before even planning a test, it’s imperative that you along with your security provider discuss topics such as the scope of the test, budget, objectives, etc. Without these, there won’t be a clear enough direction for the test and will result in a lot of wasted effort.
Step 2: Information gathering
Before commencing the pentest, the tester will attempt to find all publicly available information about the system and anything that would help in breaking in. These would assist in creating a plan of action as well as reveal potential targets.
Step 3: Vulnerability assessment
In this stage, your application is checked for security vulnerabilities by analyzing your security infrastructure and configuration. The tester searches for any opening or security gaps that can be exploited to break into the system.
Step 4: Exploitation
Once the tester is armed with the knowledge of vulnerabilities present in the system, they will start exploiting them. This will help in identifying the nature of the security gaps and the effort required to exploit them.
Step 5: Post-exploitation
The main objective of a pentest is to simulate a real-world attack without actually causing any real damage. Thus, once the tester can enter the system, they will use all available means to escalate their privileges.
Step 6: Reporting
Everything done during this penetration testing is documented in a detailed manner along with steps and suggestions to fix the flaws in the security. Since the nature of the report is highly sensitive, it is ensured that it is safely delivered to authorized personnel. Testers often have meetings and debrief with executives and technical teams to help them understand the report.
Step 7: Resolution
Once the target organization obtains the detailed report upon the scan completion of its assets and its security, it is used to rectify and remedy the vulnerabilities found. This helps avoid any breaches and threats to security.
Step 8: Rescanning
Upon the completion of patching of vulnerabilities based on the penetration testing report provided, a rescan is conducted to scan the new patches to test their air tightness. The application is rescanned to find any additional or new vulnerabilities that could have arisen from the patching.
Once this final step is completed and no vulnerabilities have been detected, the organization or asset is said to be secure and is provided with a penetration test certificate that is publicly verifiable and adds visible authenticity.
Methodologies In Penetration Testing in Cyber Security
Here are some of the methodologies that can be opted for carrying out pentest that is more customized to the needs of your organization’s security.
1. NIST Penetration Testing Methodology
NIST or the National Institute of Standards and Technology is a regulatory agency with the mission to promote industrial innovation and competitiveness. NIST penetration testing refers to conducting a pentest using the NIST framework to find out the compliance status of an organization with respect to the framework.
The NIST framework is built on five basic components which include Identification, Protection, Detection Response, and Recovery. This helps businesses operate securely using their own critical infrastructure.
2. OWASP Penetration Testing Methodology

OWASP or Open Web Application Security Project is an online community that was developed to help the internet fight against vulnerabilities and subsequent cyberattacks. OWASP puts out a list of the top 10 vulnerabilities and attacks for various systems and applications like cloud, networks, web, and mobile applications.
OWASP penetration testing refers to the testing of systems for these specific vulnerabilities and attacks.
Top 7 Penetration Testing Tools
Here are some of the top penetration testing tools (both commercial and open-source tools) that can be considered by you for an application or CMS-based penetration test.
1. Astra Pentest
This leading provider of penetration testing services for various applications and CMS platforms assures zero false positives. This is done through a comprehensive scan that is capable of running more than 8000 tests. The reports are vetted by expert pentesters who also provide remediation assistance.
The website penetration testing tool is capable of testing for compliances like GDPR, HIPAA, PCI-DSS, and ISO 27001. Besides website pen testing, Astra Pentest also provides firewall penetration testing and pentesting online for networks, cloud environments, mobile apps, and APIs.
Astra offers penetration testing for different modern-day applications. Some of them include:
- Web applications
- Mobile applications (Android/ iOS Penetration Testing)
- API Penetration Testing
- Cloud infrastructures
- Network devices
2. Burp Suite
Provided by Portswigger, Burp Suite is an evolving penetration testing tool that provides numerous integrations. It has a free version called the community edition as well as an advanced commercial solution, Professional Edition.
It provides manual and advanced automated pentesting services. Along with this, the tool also gives step-by-step advice for every vulnerability found. Lastly, it can crawl through complex targets with ease based on URLs and content.
3. Nmap
Nmap is an open-source network pen-testing tool that helps with network discovery, management, and monitoring. It is designed to scan large networks, however, it also works fine against singlet networks.
This freely available tool shows open ports, running serves, and other critical facets of a network. It is usable for large and small networks alike.
4. OWASP ZAP
Zed Attack Proxy is an open-source penetration testing tool provided by OWASP. It can be used for Linux, Microsoft, and MAC systems to run web application penetration tests for the detection of flaws.
This beginner and expert-friendly tool sends automated alerts after crawls and scans. However, being an open-source tool, its reports are often very cluttered and extremely long.
5. Metasploit
Metasploit is an open-source penetration testing tool that helps in the identification and exploitation of vulnerabilities. This is done with the aid of its built-in security scanner that detects flaws and other attack vectors. The tool is capable of carrying out nearly 1677 exploits.
6. SQLmap
Yet another open-source online penetration testing tool, SQLmap is the best tool for finding SQL injection vulnerabilities in web applications. It is popular for its automatic exploitation of found SQL injections in various databases like Microsoft, MySQL, IBM, Oracle, and others.
7. Wireshark
Wireshark is famous among free pen test tools that allow the inspection of protocols as well as the analysis of network traffic. The contributions of numerous expert pentesters all over the world help boost the efficiency and credibility of this pentest tool.
Penetration Testing Standards And Compliance
This section aims to analyze the need for penetration tests in achieving and maintaining compliance with various international standards like ISO 27001, PCI-DSS, SOC2, HIPAA, and GDPR.

How Pentest Helps Stay Compliant
For some regulatory standards like PCI-DSS, ISO 27001, and GDPR penetration testing is a mandatory requirement for the continued maintenance of these compliances. This means that penetration tests need to be carried out whenever major upgrades are made to the systems in use.
In the case of regulatory bodies like HIPAA and SOC2, penetration testing isn’t explicitly mentioned as a mandatory requirement. However, these international standards also mention regular risk assessments to be carried out. One of the best ways to ensure this is through penetration tests or vulnerability assessments as recommended by these standards.
Penetration Testing in Cyber Security For Various Compliances
1. PCI-DSS (Payment Card Industry Data Security Standard)
PCI-DSS does not compel compliance. However, it is considered cardinal for every company that processes credit and or debit card transactions. The PCI-DSS compliance is divided into four levels depending on the number of transactions that they can handle (Level 1 – 6 million to Level 4 – 20,000).
Companies at all levels are advised to conduct PCI scans regularly, however, Level 1 companies have to conduct internal audits and scans. In order to qualify this criterion with ease companies generally opt for PCI penetration tests as part of the requirements set forth by the PCI-SSC.
2. ISO 27001 (International Organization for Standards 27001)
This compliance scheme was developed to standardize the adequate and controlled measures that promote information security. It covers everything from company security policy to asset and incident management.
ISO 27001 Penetration testing is an annual requirement that must be met by organizations in order to stay 27001 compliant. This allows testing their security posture to identify growing concerns and vulnerabilities in the ever-evolving cyber threat landscape.
3. GDPR (General Data Protection Regulation)
GDPR is a pan-European data protection law that sets one of the sternest and most rigorous standards for data protection and security. GDPR applies to any and all organizations that collect, store or possess the personal data of EU residents.
Article 32 of GDPR states that organizations should implement further solutions to maintain data security. This is generally achieved by penetration testing.
4. HIPAA (Health Insurance Portability and Accountability)
HIPAA is a regulatory standard set for the protection of personal health information and is a mandatory compliance for any healthcare organization that stores confidential health information of patients. This includes pharmaceutical companies, medical colleges, hospitals, clinics, and other services.
HIPAA penetration testing refers to the scanning and exploitation of security systems employed in healthcare organizations to find hidden vulnerabilities that leave confidential information exposed to malicious attacks.
5. SOC 2 (Service Organization Control 2)
SOC 2 is a compliance standard created by AICPA for the regulation of security, integrity, confidentiality, and privacy. It was designed for technology and SaaS companies that store customer data in the cloud.
As such, SOC 2 compliance comes with penetration testing as a requirement along with monitoring of network assets, conducting regular audits, and more.
Who Needs Penetration Testing and How Often?
Penetration testing is ideally to be carried out by any and every organization that has a cyber presence, namely as websites or in the form of data storage in a cloud platform.
This includes everything from startups to SMEs, SaaS companies, e-commerce sites, healthcare organizations, financial institutions like banks, government and private companies, and even educational institutions.
Regular penetration testing of one’s cyber-facing assets can help in the timely identification of vulnerabilities before they are exploited by malicious attackers.
Why does an organization need frequent pentesting?
The cyber threat landscape is in a constant state of flux. New vulnerabilities are discovered and exploited regularly, some of them are publicly recognized, and some are not. Being alert is the best thing you can do.
Pentest goes beyond just detecting common vulnerabilities with the help of automated tools and finds out more complex security issues like business logic errors like issues related to payment gateways, Excessive Trust in Client-Side Controls, Flawed Assumptions About User behavior, etc. It helps you get a clearer picture of your organization’s security posture and fix the issues to harden your security.
The primary purpose of penetration testing is performed is:
- Keeping up with the changing cyber threat landscape
- Detecting and mitigating business logic errors
- Preparing for compliance audits
- Protecting your business’s reputation by stopping security breaches.
How Often Should Pentests Be Conducted?
Web services pentest helps you root out the vulnerabilities in your system that can lead to security breaches, data theft, and various different security vulnerabilities. As such, it should be conducted at least annually, bi-annually, or after every major update or feature addition to your application.
Penetration Testing Report

Penetration testing reports are customized according to the findings and requirements for each client’s assets. Here’s a brief list of sections that a powerful, actionable pentest report should include:
- Details of scope and rules of engagement.
- Detailed outline of detected vulnerabilities.
- Precise summary of vulnerability findings.
- Assessment of impact with actionable risk scores.
- Exploitability of vulnerabilities.
- Step-by-step remediation measures and recommendations.
- Video PoCs and screenshots
- Selenium scripts for the developers to reproduce the vulnerabilities
- Threats ranked with CVSS score
Penetration Testing Cost
Generally, the cost of penetration tests varies from $400 to $5000. A lot of factors influence the prices, namely:
- Application or system that is to be tested – Cloud, network, API, web, or mobile applications.
- Size of the company and scalability of the solution you’re considering.
- Scoping the number of assets that are to be tested.
- Experience and reputation of the pentesting solutions under consideration.
- The customizability of their prices and features provided.

Here are the penetration testing packages available with Astra:
- Scanner: $1,999/year
- Pentest: $ 5,999/year
- Enterprise: $7,999/year
For Pentesters: How Can You Become a Qualified Penetration Tester?
The right effort and choices make becoming a penetration tester a totally achievable dream. Find and enroll for monthly or short courses that provide you with a deeper insight into how penetration testing works and how you can get started.
Simultaneously, during the duration of the course strive to become familiar with open-source easy-to-use penetration testing tools like Nmap, BurpSuite, OWASP ZAP, and others. Now, it’s all about practice. Practice, practice, practice, through bug bounty sites and other simulations, to perfect your skill.
Lastly, appear and obtain reputable certifications that cement your pentesting qualifications:
- eLearnSecurity Junior Penetration Tester (eJPT)
- GIAC Penetration Tester
- Offensive Security Certified Professional
Conclusion
This article is a one-stop destination to clear all your penetration testing-related queries and doubts. From its definition to various approaches, types, and tools available, this article has given a detailed overview of what a penetration test entails along with its steps.
Lastly, it mentions the need for pentests for achieving and maintaining compliance, the costs associated with getting one, and also how to become a qualified pentester.
FAQs
What is the purpose of penetration testing?
Penetration testing aids in the detection and identification of vulnerabilities that may be plaguing your security system. Subsequently, it also helps in increasing and updating the existing security measures.
Will a Pentest be disruptive to our application? Should we expect a system crash?
A well-planned and coordinated penetration testing will not be disruptive to the system. It is important to ensure that all stakeholders are aware of the timeline and that relevant teams are kept informed. With proper expertise and a focused approach, you would not face any likely system crash.
How much time is required for Penetration Testing?
The overall time depends on factors such as the size of the environment, size of the testing team, type of test, etc. Reserve adequate time for the test and assign extra time for reporting. A good estimate would be 4 to 6 weeks, including the planning and reporting stage. The actual test takes around 2 to 3 weeks, depending on the complexity and size of the environment.
How much access is given to pen testers?
The access given to pentesters varies depending on the methodology of the pentest opted. In the case of black box pentesting, no access is given whereas with gray and white box pentesting, partial and complete access is given respectively.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report

















Thorough, informative, and truly helpful post. Delivers what it promises in the title. Great work.
Does Penetration testing ensure PCI-DSS compliance?
It doesn’t. There are other procedures involved in the PCI-DSS compliance process than the pentest. Getting a pentest does improve your chances of nailing the PCI-DSS compliance audit for sure.
So, if I get a pentest today, how long will it be valid?
Usually, we recommend quarterly Penetration Testing. However, any major update on your software within that time will invalidate the pentest report.
This was helpful. However, I was looking for more detailed coverage of the Vulnerability Assessment part.
Thanks. We might actually have something for you. You’ll find a more detailed take on vulnerability assessment here. https://www.getastra.com/blog/security-audit/vulnerability-scanning/
How is this any different from ethical hacking?
Penetration testing is a focused procedure with a predefined scope. That means the security experts work under strict guidelines from the client organization and test only certain systems or certain areas of the business. Ethical hackers enjoy more freedom in terms of choosing the attack vectors as well as the techniques they apply. They usually take a broader approach to security testing where they employ every invasive and noninvasive tactic in their arsenal to try and exploit security loopholes.
Do you reckon that cyber security engineers will be replaced by AI?
Not in the foreseeable future. While the use of machine learning augments the security testing processes like vulnerability assessment and pentesting, it cannot yet cover for human instinct in terms of finding security errors.
Is it possible to automate the entire process of pentest?
Well, it really depends on what exactly you mean by pentest, and what you want to get out of it. If you are looking at a vulnerability scan, which is often passed as an automated pentest, then sure, you can schedule the scans, automate it, even integrate the scanner with your CI/CD to perform continuous scanning for new updates. But there will be false positives, and the scanner will miss some vulnerabilities, including business logic errors. If you want to find all vulnerabilities, with zero false positives and detailed guidelines to fix the vulnerabilities, you will have to go for… Read more »