The online space opens up new opportunities but also avenues for cyber attacks. It is vital that we ensure that our systems and applications have enough security to protect against these. Penetration testing helps in answering vital questions in regard to security standards and vulnerabilities.
This pentest methodology guide is here to help you navigate this complex process by providing a framework and steps. Read on to find the types of areas to penetration test and the various stages and their requirements.
What is Penetration Testing Methodology?
Penetration testing methodology is a specific course of action taken by a pentest provider to conduct the pentest of a target website or network. There are multiple penetration testing methodologies that can be put to use depending on the category of the target business, the goal of the pentest, and its scope.
What Is A Penetration Testing Framework?
The penetration testing framework is a list of penetration testing methods for different security testing tools in every category of testing. Discovery, probing, reconnaissance, enumeration, and vulnerability assessments are some of the various uses of a penetration testing tool.
Penetration Testing Methodologies and Standards
There are various standards and methodologies that ensure the penetration test is authentic and covers all important aspects. Some of them are mentioned below:
What is OSSTMM?
OSSTMM is short for Open-Source Security Testing Methodology Manual. It is one of the most widely used and recognized standards of penetration testing. It’s based on a scientific approach to penetration testing that contains adaptable guides for testers. You can use this to conduct an accurate assessment.
What is OWASP?
OWASP stands for Open Web Application Security Project. Widely known, this pentest standard is developed and updated by a community keeping in trend with the latest threats. Apart from application vulnerabilities, this also accounts for logic errors in processes.
What is NIST?
National Institute of Standards and Technology (NIST) offers very specific pentesting methodology for pentesters to help them improve the accuracy of the test. Both large and small companies, in various industries, can leverage this framework for a penetration test.
What is PTES?
PTES or Penetration Testing Execution Standards is a pentest methodology designed by a team of information security professionals. The goal of PTES is to create a comprehensive and up-to-date standard for penetration testing as well as to build awareness among businesses as to what to expect from a pentest.
What is ISSAF?
The Information System Security Assessment Framework (ISSAF) is a pentesting guide supported by the Open Information Systems Security Group. This is one of the security testing methodologies is not updated anymore, hence it is a bit out of data. Nevertheless, it is still in use for its comprehensive nature – it links different steps of the pentest process with relevant tools.
Also Read: Continuous Penetration Testing: The Best Tool You’ll Find in 2022 | A Complete Guide Cloud Penetration Testing
Why are Penetration testing methodologies important?
There is no one size that fits all when it comes to penetration testing. Each target organization comes with its own requirements in terms of security, compliance, and tolerance. The scope of the pentest is determined based on these factors and more. A penetration testing methodology is important to apply some standardization to this seemingly improvised effort.
When a certain pentest methodology is agreed upon, it helps the pentesters narrow down their focus, and follow certain important steps without failure, and the test retains its validity in the industry.
Stages common to most penetration testing methodologies
Once the audit universe is ready, testers are ready to move on to further stages in the penetration testing methodology.
- Pre-engagement and Planning
- Intelligence Gathering
- Vulnerability Analysis & Exploitation
- Post Exploitation (Remediation)
- Reporting & Certification
1. Pre-engagement & Planning
The first step in the penetration testing methodology is to create a plan. A properly curated plan provides a way through the complex IT structure of an organization. To begin creating a plan one needs to have a complete understanding of the organization and its operations. Also, knowledge of their systems and applications is important. Once we have this information, we can go on to build the audit universe.
Creating the Audit Universe. To create an audit universe, testers might use a top-down approach to state the business objectives, important applications and processes, and infrastructure. Roles of various departments are also included here. This helps in creating this universe which serves as an inventory for the testers, and forms the foundation of the penetration testing methodology.
It is important to fix one since there are different kinds of it, such as network penetration testing methodology, methodologies for web applications, and so forth.
This is essential to begin the pentest in any organization. Based on the audit universe, testers will create a comprehensive plan for the test. This includes stating the objectives and goals of the test, stakeholders involved, areas to penetration test, and proper authorization, to name a few. This plan contains the details of how to proceed with the penetration test.
Also Read: API Penetration Testing: What You Need To Know
2. Intelligence Gathering
To have an effective penetration test, it is necessary to conduct proper reconnaissance and gather intel on the systems. By using various tools, automated and manual, testers will check the system to find any potential vulnerability or entry points. These would be then exploited by the testers in further steps. Tools such as Recon-Ng, Nmap, Spiderfoot, Metasploit, Wireshark, are commonly used for this.
3. Vulnerability Analysis & Exploitation
Once the potential vulnerabilities are discovered, testers will leverage these to further enter the system. This closely resembles how a cybercriminal would exploit these security gaps and helps provide a better understanding. All the steps, tools used, location, and methods of entry for a particular issue are properly documented to capture the entire process for further review. As a step in the penetration testing methodology, these security issues are ranked based on their ease of exploitation and the damage they can cause. This enables the organization to prioritize the fixes.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed] | Why Firewall Penetration Testing is Essential to Your Security Strategy
4. Solution Development
Once security vulnerabilities are unearthed, testers will devise strategies and solutions to fix them. in their final reports, solution steps will be compiled for all the issues and additional suggestions to keep the system secure.
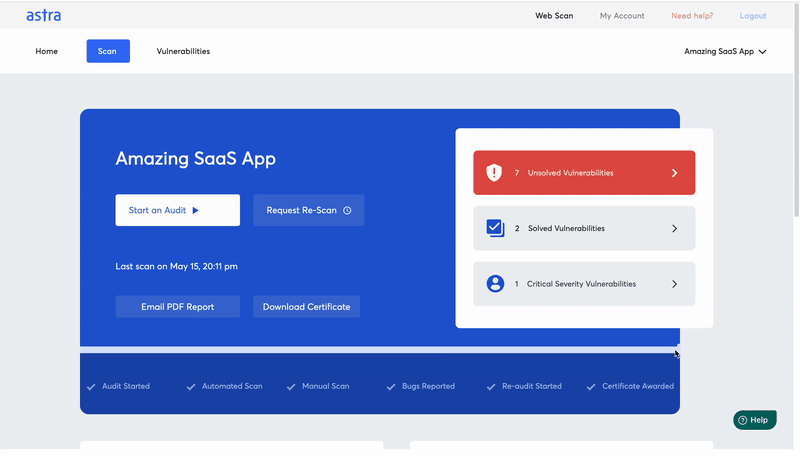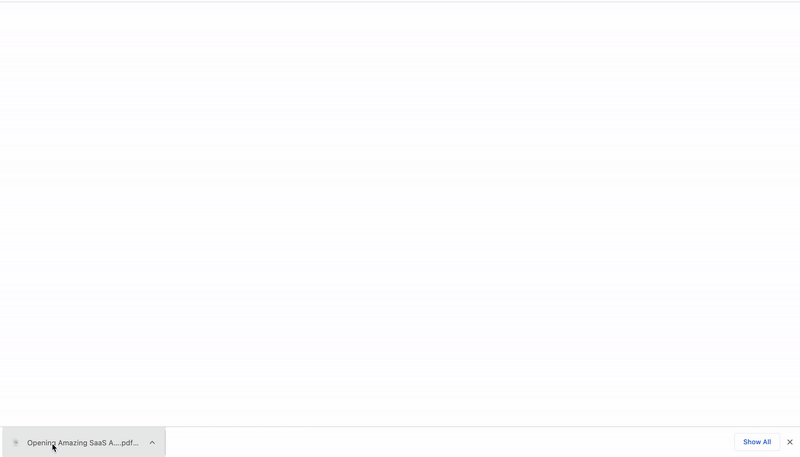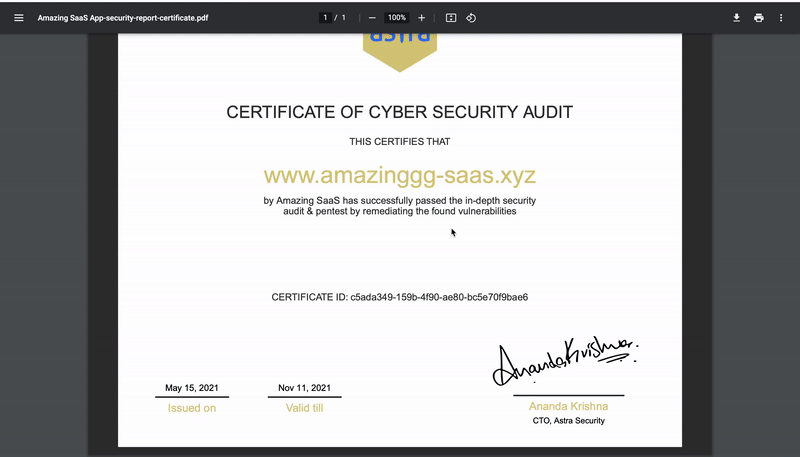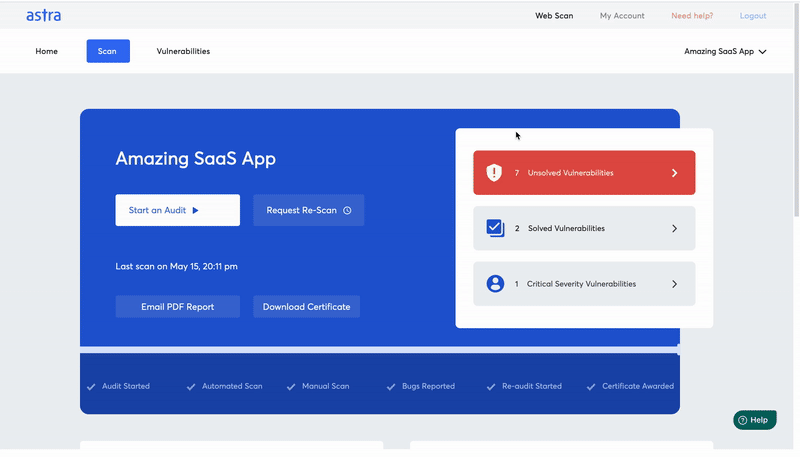
5. Report Drafting and Certificate Issuance
The final stage of a penetration test is reporting. From planning to execution and solution, all details are compiled in a report that is sent out to all the stakeholders. Steps to fix the issues and future steps are also mentioned in this report. The final report should be so made that it is consumable by both technical and non-technical personnel. It should also cater to the requirements of both executives and IT, support teams.
Hacker-style penetration testing by Astra Security
At Astra, we offer manual & automated penetration testing with our one-of-a-kind Pentest Suite. We follow OWASP penetration testing methodology for our hacker-style manual pen tests.
Our automated scanner lets you take the reign of your system’s security. You can conduct vulnerability discovery (with 8000+ tests) with a click of a button with this scanner. It shows results in real-time, that is, as the scan progresses. So that you don’t face the slightest of delays in fixing the vulnerabilities 🙂
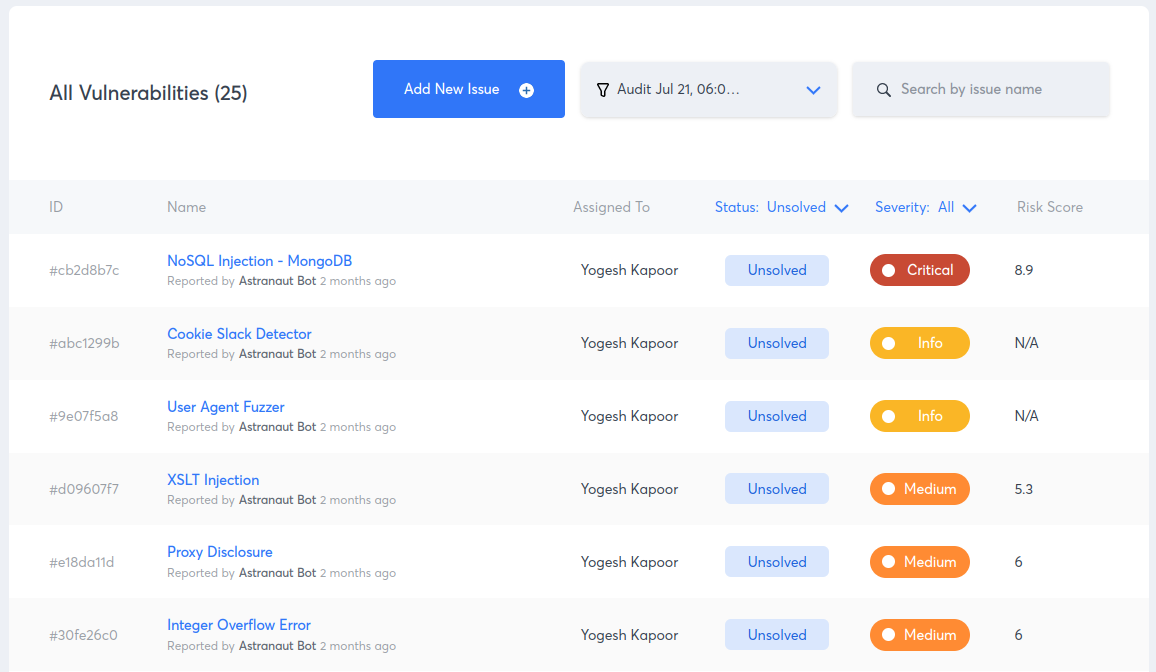
Astra’s Pentest also simplifies tedious vulnerability management for your developers. You can add your team members and developers to Astra’s collaborative dashboard where they can directly collaborate with the security researcher on the reported vulnerabilities. You don’t have to hit your head while iterating to and fro.
You also receive detailed steps (including video PoCs, selenium scripts, etc.) on how to reproduce the vulnerability. so that you don’t have to guess where to find the vulnerability.
Our security researchers go the extra mile and assist your developers with remediation. Not to mention, you get detailed steps to fix as well.
Check out more Astra Pentest features here.
Summary
Penetration testing methodologies should be flexible enough to account for different organizations and their requirements. But also, should have a strong foundation for encompassing all the critical areas and aspects. By following a methodology, such as this, you ensure that you conduct a comprehensive penetration test and safeguard your IT infrastructure.
If you need help pentesting your web-facing system, get in touch!
FAQs
1. What is a Penetration Testing Methodology?
A penetration testing methodology is a combination of processes and guidelines according to which a pentest is conducted.
2. Why Are Penetration Methodologies Important?
Pentesting methodologies are important because they create a definitive path to follow during a pentest which makes the process more efficient and effective.
3. What are the top 5 penetration testing methodologies?
The top 5 penetration testing methodologies are OSSTM, OWASP, NIST, PTES, and ISSAF.
This post is part of a series on penetration testing, you can also check out other articles below.
Chapter 1. What is Penetration Testing
Chapter 2. Different Types of Penetration Testing?
Chapter 3. Top 5 Penetration Testing Methodology to Follow in 2024
Chapter 4. Ten Best Penetration Testing Companies and Providers
Chapter 5. Best Penetration Testing Tools Pros Use – Top List
Chapter 6. A Super Easy Guide on Penetration Testing Compliance
Chapter 7. Average Penetration Testing Cost in 2024
Chapter 8. Penetration Testing Services – Top Rated
Chapter 9. Penetration Testing Report
















