Till today, more than 150 CVEs recorded in the Joomla CMS. Getting your site hacked not only costs you heavily but also is a nuisance. Each hack on a Joomla website incurs a loss of data, money, business, trust & reputation to the website as well as CMS. There have already been countless cases of Joomla hacks. On close inspection, we found that most of these hacked websites were either running an outdated version or had an unpatched vulnerability in its core, extension or themes.
Hackers are lurking around the corner to attack poorly configured websites. Are you sure that is not yours?
Find out with a thorough Joomla Security Audit & Penetration Testing. This blog post talks about what, why & how of a Joomla Security Audit & Penetration Test. Read till the end to find handy tools that can catalyze the whole process.
What is a Joomla Security Audit?
A Joomla Security Audit evaluates your web system and identifies vulnerabilities and loopholes in it. A thorough Joomla Security audit includes code analysis, business logic error testing, infrastructure & server misconfiguration checks, etc.
Another name for security audits is Vulnerability Assessments. A reliable security audit assesses your system and discovers all security loopholes.
What is Joomla Penetration Testing?
Pentesting or Penetration Testing is the practice of testing the security of a web app, network or computer by attacking it like it would get attacked in a real environment. It is generally the second step in the combined process of Joomla Security Audit & Pentesting.
Joomla Penetration Testing involves attacking the Joomla site manually and/or with automated tools to gain access. The main motive of a penetration test is to exploit security vulnerabilities found in the security audit to analyze the risk attached to it.
A good Penetration Test will help to simulate real-life attacks that your website may face. The main difference between Joomla Security Audit and Penetration Testing lies in the fact that whereas a security audit focuses on enlisting the issues, penetration test revolves around exploiting them.
Together these processes improve the security and integrity of your Joomla site by identifying the risk in due time. Thus, this is a recommended practice.
Why do you need Joomla penetration testing?
Data Breach is the worst thing that can happen to your company. It will ruin your customer’s trust in you forever. Furthermore, about 43% of data-breaches are targeted at small businesses like yours.
Hackers are after monetizable data such as email addresses, phone numbers, bank account numbers, etc. If a hacker can access this information through your Joomla site (which is the case mostly), it invariably becomes a hot target.
Most Joomla sites are easy targets because they are not tested against real-life attacks. Therefore it is recommended to perform a penetration test on your Joomla site before deploying it for public access.
Also Read: API Penetration Testing: What You Need to Know
How to do a Joomla Security Audit & Penetration Test?
A good penetration will simulate all real-world attacks on your Joomla Site. The Joomla Penetration Testing will map out all the security vulnerabilities and issues in a detailed report containing how to reproduce them and (if possible) their fix.
We will discuss each stage of the Joomla Penetration Testing in detail along with the tools to perform those steps.
1. Enumeration
The very first step in order to audit anything it enumeration/reconnaissance. Here you will map out all the resources, webpages and functionality of the Joomla app.
A few popular tools used in the process are:
JoomScan
JoomScan automated vulnerabilities scanner is an open-source tool that is developed with the aim of automatically enumerating common information about the Joomla Site.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed] | Top 6 Web Pentest Tools You Should Not Miss

This common information includes
- The version number
- CVEs that may work (based on version number)
- Firewall Detector
- Finding Common Logs
- Finding Common Backup Files, etc
Get the ultimate Joomla security checklist with 300+ test parameters
Also Read: 11 Top Penetration Testing Tools/Software of 2022
JoomScan is fast, simple to use and industry-standard tool to use when attacking Joomla Site. You can install the tool and get it working with the following steps:
Note
These steps are for Linux based distributions. If you are on windows step up a VM machine following the guide from here.
1. First, git clone the repository
git clone https://github.com/rezasp/joomscan.git
cd joomscan
2. Second, install Perl
sudo apt install perl
3. Done, you can now run the JoomScan
perl joomscan.pl --url www.example.com
It is also recommended to perform some manual enumeration while tools run in the background to get the best results. Also, you can read more about JoomScan here.
2. Exploitation
Once you have enumerated the feature or CVE that you will exploit. It is time for exploitation. In this step, you will follow the attack vector that you found in the previous step.
This may include CVEs, Login Form, Logic flaw, RFI/LFI, Access Control, etc. A few tools and attack vectors that will help you along the way are listed below.
SQLMAP
sqlmap is a useful tool when testing for SQL Injection vulnerabilities in a login form or URL. It automates the process of detecting and exploiting SQL injection flaws and taking over database servers.

Its support for various databases such as MariaDB, MySQL, Postgresql, etc makes it a suitable tool to use during the Joomla Penetration Testing.
It is already available on most pentesting distributions such as Kali, Parrot, Black Arch, etc. Also, it can be installed in a few simple steps as follows:
Step 1, git clone the repository
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
Step2, You are Done. Run the tool with the command
python sqlmap.py -h
LFI/RFI
Local File Inclusion or Remote File Inclusion flaws allow an attacker to include a local file such as “/etc/passwd” or a remote file (mostly a malicious script) to be hosted on the server.
This attack can allow an attacker to read source code file which may help in further exploitation or get Remote Code Execution(RCE).
The trick to noticing this attack is pretty simple. Since this attack depends on improper validation which can be exploited, you may be able to leak contents of file “/etc/passwd” on a Linux server.file “/etc/passwd” on a Linux server.http://example.com/index.php?option=com_blabla&view=../../../../../../../../../../../../../../../etc/passwd
if the above payload works you have potential LFI/RFI vulnerability. Try out some of these payloads to increase damage.
Password Brute Forcing
If the login form you found is not vulnerable to SQL Injection, Password Brute Forcing might get you access.
The idea is to try all common passwords for a user until one of them works. The tool used for this process is Hydra.

Hydra is a popular brute-forcing tool used for this attack. You also can write your own script but hydra is optimized for speed thus will lot quicker. To use hydra simply run the command.
hydra [some command line options] [-s PORT] TARGET PROTOCOL [MODULE-OPTIONS]
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]

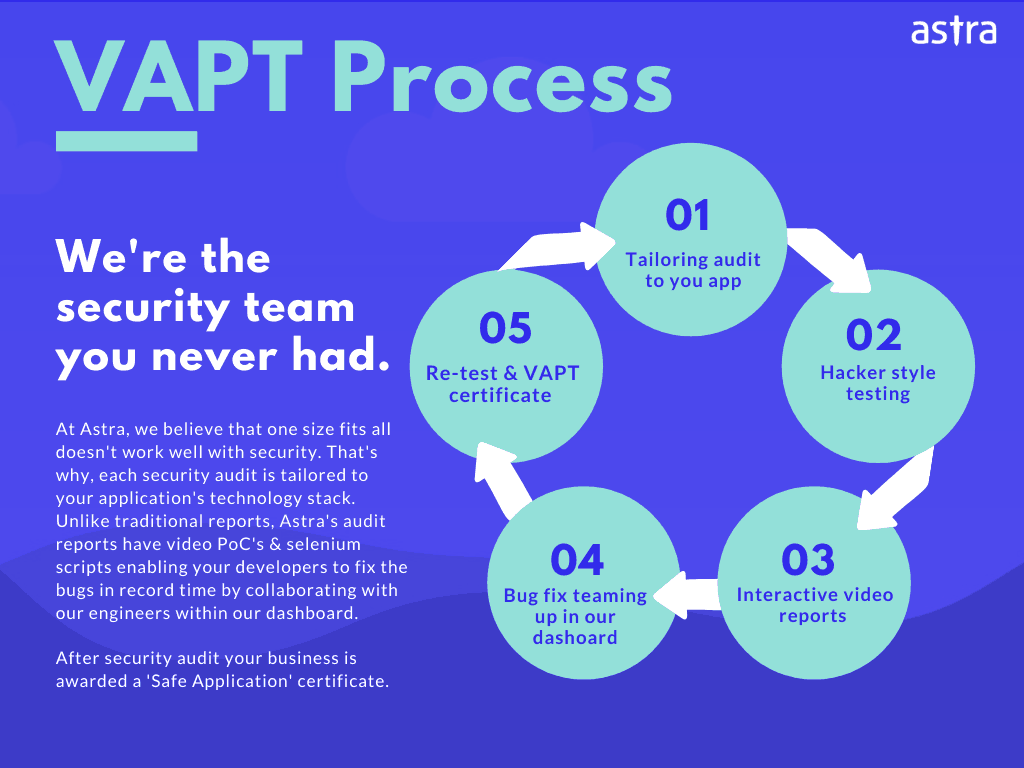
Joomla Security Audit & Penetration Testing by Astra
If the above process seems like a task for you, get security experts to do this. Astra offers a Joomla VAPT Solution that will make sure all the security vulnerabilities & loopholes are recognized and fixed before it’s too late. Manage bugs, collaborate with our security team, verify fixes at your own pace under one unified platform.
We make sure that no security bug or vulnerability in your website is gone unseen.
Summing up
In this blog, we talked about why Joomla Security audit & Joomla Penetration Testing are crucial for your web store. It also broke down the process in a few simple steps. The blog also listed Joomla Security Audit tools. Patching your website’s vulnerabilities and regularly auditing it to find new vulnerabilities is a security practice you should always abide by.
You are busy. We get it. Sign up for Astra’s VAPT for Joomla websites today and leave the hard part to us. From assessment to pentesting, we will take care of it all. Our security experts go out of their way to assist your developers with the patch and re-testing until it’s fixed.
Don’t wait to be hacked. Secure while there is time.
Have questions to ask? Talk to us.