Cyber security audits are periodic reviews of your organization’s security posture. The prospect of a security audit can be quite daunting for a small or midsize business considering the resources required and the comprehensive scope of the undertaking.
And yet it is a necessary process. So, the best a business owner can do is look for cyber security audit companies that make it easier for the business in terms of expense as well as the efforts required.
We will talk about 10 of the best cybersecurity audit companies and security consulting services in this article. Quickly compare with our pricing.
Here’s a list of the companies for you to find out more about them quickly.
10 Best Cyber Security Audit Companies of 2024
- Astra Security
- Flashpoint
- CyStack
- SecurityScorecard
- Sprinto
- KROLL
- CyberSecOp
- Romano Security
- Symantec
- AltiusIT
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Introduction
As cybercrime rates continue to rise, it becomes increasingly important for businesses to take steps to protect their data and networks. Cyber security audits are concerned with a number of different components ranging from the physical security of data centers to the logical security of databases.
In the scope of this article, we will talk about information security audits and companies that help you with them.
What to look for in a security audit company?
There are two types of features that you should be looking for in cyber security audit companies. The first type consists of broad characteristics including the number of test cases, the involvement of manual security testing, the quality of the report, etc.
And then, there are the smaller features that hold great significance in terms of shaping the impact of the security audit. These are features like scan behind logged-in pages, the inclusion of video PoCs in the report, the ease of navigating the vulnerabilities, etc.
We will try to focus on both types of features and give you a list of good signs.
The combination of manual and automated security testing
The security audit company definitely uses some automated tools to look for vulnerabilities in your systems. Automated scans are great for their speed but they lack the depth of manual security testing.
You want to work with security audit companies that use both types of scans, come with an assortment of SAST, DAST, and software composition analysis approaches, and give you a comprehensive picture of your organization’s security posture.
Also Read: Third-Party Penetration Testing And Why You Should Consider It
A wide range of test cases
When you are getting a security audit done, you are actually preparing for a compliance audit (we will talk about the difference later). The security audit provider needs to check your system for a large number of vulnerabilities factoring in popular vulnerability indexes like the OWASP top 10 and the SANS 25. So, the number of test cases does play a role in the impact of the audit.
The thoroughness of the audit report
The security audit report needs to have two qualities. One, it has to be thorough, two, it has to be actionable.
On one hand, the report should cover the entire gamut of test cases, and all the vulnerabilities along with their properties and remedies, on the other hand, it should simply tell the target organization what to do.
Remediation support
The cyber security audit company should provide you with all the resources you need to fix the vulnerabilities, including a help desk, training sessions for your staff, and regular check-ups. The opportunity to collaborate with security experts to fix the
Ease of use
Last but not least, ease of use is an important factor that decides how much impact the security audit will have. A good cyber security audit company will make it easy for you to find and fix vulnerabilities by flagging them clearly, providing video PoCs, and giving you step-by-step instructions.
Compliance support
While most security audit companies can’t assign you a compliance certificate, they can help you with pinpointing the problems that need fixing for you to become eligible for a certain type of compliance. Compliance-specific vulnerability scans are a nifty inclusion by some security audit companies.
10 Best Cyber Security Audit Companies
Now that you know what to look for in a cyber security audit provider, let us walk you through the offerings of some of the best security audit providers and security consulting companies. You might find just what you are searching for.
Astra Security
Astra Security is a security testing company that offers a penetration testing platform complete with a dynamic dashboard, automated vulnerability assessment, thorough reporting, step-by-step remediation support, and a publicly verifiable pentest certificate. Astra helps you materialize the goal of building DevSecOps
Astra is the most comprehensive solution on our list today, so we will take a bit of time to talk about it. Their offerings are
- Web app and mobile app pentest
- Cloud configuration audit
- Smart contract audit
- API pentest
- Continuous vulnerability assessment
Astra’s pentest platform supports single-page apps.
Some very specific features make Astra security the top choice among security audit companies. For instance,
Continuous penetration testing
Instead of giving you a point-in-time report about your company’s security posture Astra helps you set up a system that monitors your systems ceaselessly.
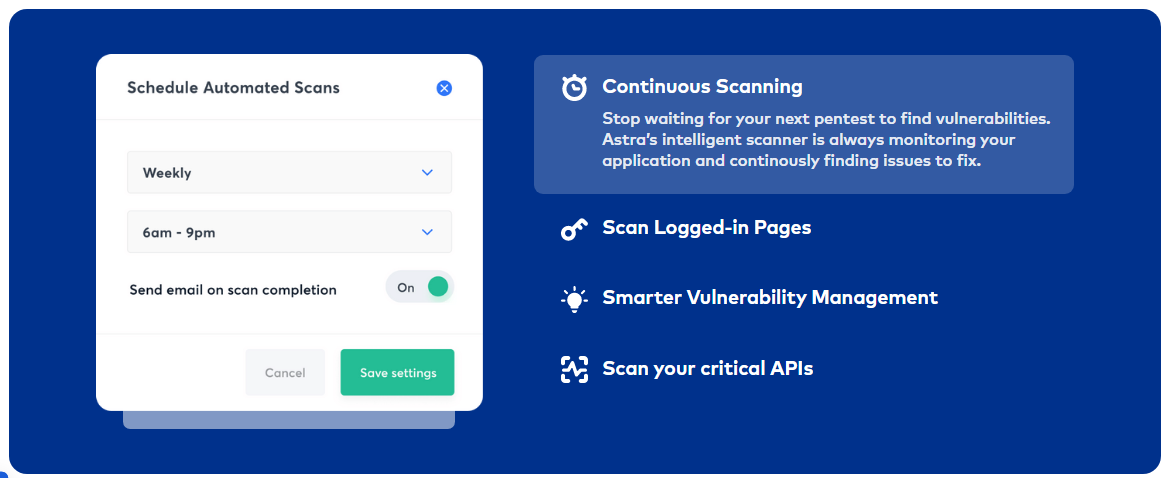
The pentest suite integrates with your CI/CD pipeline and runs scans whenever you launch an update for your application. It helps you detect and fix vulnerabilities before they affect your users.
Read also: Continuous Penetration Testing: The Best Tool You’ll Find
Compliance support
With Astra, you can easily pinpoint vulnerabilities that are blocking your organization’s compliance with a specific set of regulations.
Interactive dashboard
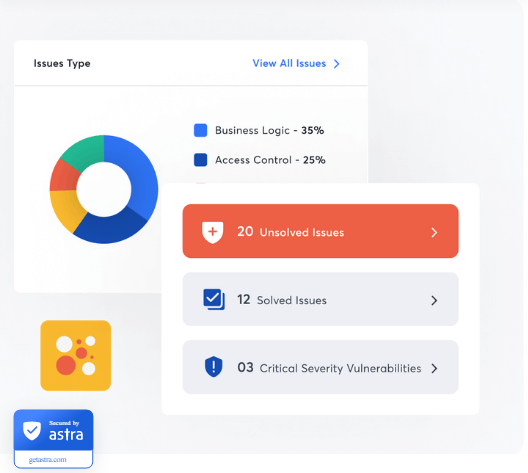
Astra’s pentest dashboard is your one-stop destination to gain any information about the vulnerabilities found in your systems. You can monitor them, assign them to your team, update them, and inspect their risk scores, all from that very place.
More than just risk scores
Astra gives you accurate predictions as to the potential impact of a certain vulnerability. it categorizes the vulnerabilities, and even creates a graph for you to monitor the status of the security issues in real-time.
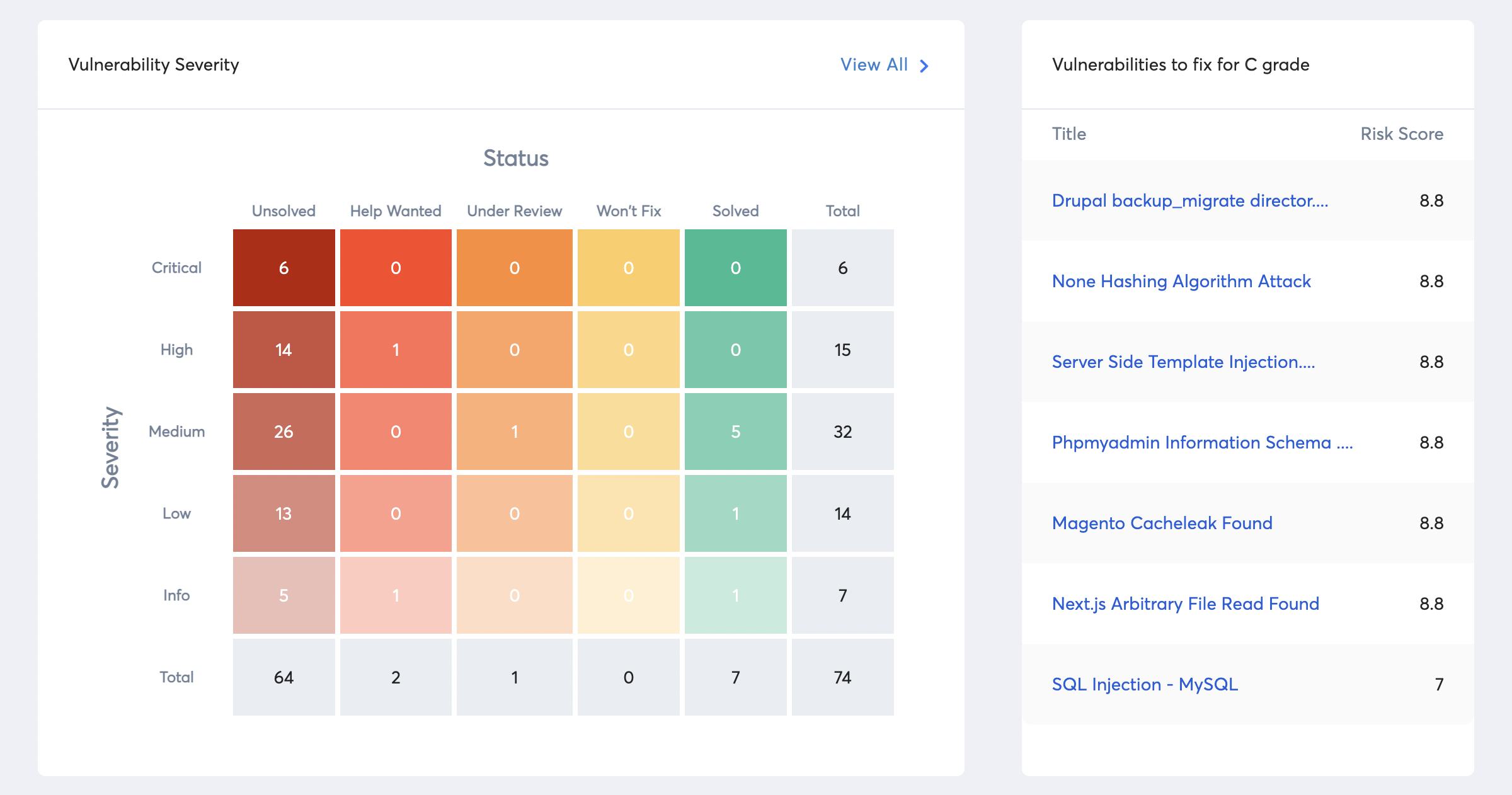
Zero false positives
All results of scans are confirmed through vetted audits by security experts so that you do not lose any time chasing false positives.
Reporting and remediation
The security testing report by Astra ticks all the boxes when it comes to quality and actionability. It contains separate breakdowns of the situation for the developers and the executives. It contains remediation guidelines, and video PoCs to help you reproduce the vulnerabilities.
Sprinto

Sprinto is a compliance readiness platform. It helps you organize your security protocols, educate your employees, and create easily accessible reports for compliance auditors. You will still need a pentest company to check your organization for vulnerabilities, but Sprinto will take care of the rest.
- Sprinto helps you comply with PCI-DSS, HIPAA, SOC2, GDPR, and ISO 27001
- They have templates for security policies
- Efficient onboarding and offboarding workflows
Flashpoint

Flashpoint is a cyber threat intelligence platform that helps you detect, prioritize, and remediate vulnerabilities. They have a solid vulnerability management offering that can help you with regular security checkups. Some other services offered by flashpoint include
- Fraud detection
- Physical security assessment
- DevSecOps
CyStack
CyStack is a provider of crowdsourced penetration testing. That means they help you organize bug bounty programs through which you can attract experts from a wide pool of pentesters to help you find issues in your systems. This approach may not suit you if you are looking for a continuous solution. More services offered by CyStack include
- Cloud infrastructure audit
- Smart contract audit
- Incident response
SecurityScorecard
As the name would suggest, this is a security rating platform. And you have also realized that we are trying to make this list as variegated as possible.
SecurityScorecard helps you attain instant visibility into vendors and business partners across your entire ecosystem. They also help you with compliance. Some notable services are
- Cyber insurance
- Digital forensics
- Incident response
KROLL

KROLL provides cyber security solutions for a wide range of industries. They have a comprehensive offering that helps you with everything from risk management to identity theft. Kroll is one of the oldest and most experienced companies on this list. Some notable services are
- Identity theft protection
- Digital forensics
- Crisis management
CyberSecOp
CyberSecOp is a very old player on the cyber security stage. They have offerings like risk assessment, security consultation, and enterprise-wide IT security audits. Some services include
- Compliance security consulting
- Network security testing
- Gap analysis
Romano Security

Romano Security is a cyber security solutions provider with a very strong focus on compliance. They have offerings like a 1-day security audit and a 2-day in-depth audit. They offer compliance consultation for all major regulations. Services offered include
- Risk management
- Business continuity
- Incident management
Symantec
Symantec deals in information security, web security, and endpoint security. They help you with threat detection, prevention of attacks, and vulnerability remediation. Apart from these they also have a compliance support program which can be very helpful. Their services include
- Attack prevention
- Data protection
- SaaS and corporate asset protection
Also Read: Smart Contract Audit | Services & Best Practices
AltiusIT
AltiusIT is involved in IT security audits, penetration testing, and privacy audits. Their web app pentest program helps you detect SQLi, XSS, and buffer overflow, among other vulnerabilities. On top of that, they also provide social engineering detection services. Their services include
- Penetration testing
- Risk assessment
- Social engineering assessment
Why are cyber security audits necessary?
With the speed of software development today, the number of plugins we use to keep the apps functional, and the amount of customer data a SaaS company handles on a daily basis, it is ridiculously easy for a small vulnerability to wreak havoc.
That being said, it is also not very hard for a business to stay ahead of emerging vulnerabilities, given they have the right practices in place.
Take the recent PrestaShop vulnerability, for instance, it is a small vulnerability in a rarely used feature that allows malicious actors to execute arbitrary code.
As a store owner, you can easily avoid being exploited by upgrading to the latest version of the software or having a solid website protection program. The problem here is not being equipped to fight vulnerabilities but being aware of their presence.
6 reasons why cyber security audits are necessary
We tend to get complacent about our cyber security after a while. The thing is, cyber threats are always evolving, and what worked yesterday might not work today.
This is why cyber security audits are essential because they help you:
- Understand your current cyber security posture
- Identify gaps in your defenses
- Implement best practices
- Stay ahead of emerging cyber threats
- Build a security compliant business
- Gain customer trust
Cyber security audit companies, as well as security consulting services, help a business bring their security back on track, imbibe the right security practices, and stay compliant with security regulations like PCI-DSS, HIPAA, ISO 27001, and GDPR. It is imperative that you find a security audit provider that truly understands and meets your needs.
How is a security audit different from a compliance audit?
A compliance audit is a type of security audit but with a focus on whether the systems meet specific regulatory requirements. The organization being audited has to show evidence that its systems are configured as per the guidelines set by the relevant authority.
A security audit, on the other hand, is a broad assessment of an organization’s cyber security posture. The goal is to find out the vulnerabilities and risks in the system and provide recommendations for fixing them.
Security testing checklist for small and midsize enterprises
- Define the scope of the assessment. This will help you zero in on the systems and data that need to be tested.
- Choose an appropriate time for conducting the assessment. You don’t want to interfere with regular business operations.
- Identify the stakeholders who need to be involved in the assessment process.
- Draft a cyber security policy for the organization if you don’t have one already.
- Decide on the tools and techniques that will be used for testing.
- Prepare the test environment.
- Conduct the tests and analyze the results.
- Prepare the cyber security audit report.
- Implement the recommendations from the report.
- Monitor and review the progress regularly.
Conclusion
Choosing the right cyber security solution can alleviate the overall stress and anxiety associated with the process. A security testing company like Astra security can add great value to your security audit campaign in terms of remediation support, and pushing your security in the right direction. Consider your needs, put them side by side with the services we have mentioned, and you should be able to make the right choice.
FAQs
What is the cost of a security audit?
The cost of a complete security audit depends on a bunch of factors like the scope of the audit, size of the company, etc. A ballpark figure would be $5000.
How much time does it take to complete a security audit?
A security audit could take anywhere between 3 days to a month.
How often should security audits be conducted?
If you have a consistent security monitoring system in place, conducting a full-scale security audit once a year should be fine.
![10 Best Cyber Security Audit Companies [Features and Services Explained]](https://cdn-blog.getastra.com/2022/08/Featured-Images-31.png)















