Cybersecurity is of paramount importance today due to the increasing number and sophistication of cyber threats globally. As a result, there has been a rapid growth in the number of cybercrimes and cyberattacks. The reason cyberattacks are on the rise is the fact that they are so profitable for hackers and cybercriminals. However, there had many instances in the past where the hackers launched cyberattacks for just for fun. Yes, that’s right!
Cyberattacks such as data breaches and ransomware attacks are more profitable than traditional criminal activities. Many hackers are motivated by a genuine desire to make a difference in the world, and they see cyberattacks as a way to do this. The only way to put a full stop to these cyberattacks is by conducting regular cybersecurity audits.
Cybersecurity audits need to be a part of corporate governance and should be planned and executed as part of the overall audit plan. Cybersecurity is a process and not a product and therefore should be audited as such.
What is Cybersecurity Audit?
A cybersecurity audit is a process of evaluating an organization’s security to safeguard against any cyber-attack. A cybersecurity audit helps to identify the gaps and shortcomings that need to be fixed before any event of hacking attempt or network compromise due to a cyber-attack launched by cybercriminals.
The purpose of a cyber security audit is to identify vulnerabilities that could put an organization’s assets at risk and to suggest actions that can be taken to reduce those risks. The IT industry is a constantly changing environment. The rate of technical change is a challenge for all businesses, and cyber security is a particular area of concern.
Cyber security auditors need to have a broad understanding of both technical security and the business or IT environment. Suppose a cyber security audit is done correctly then it should give businesses a peace of mind as to the cyber security measures in place and suggest ways to improve the organization’s security posture.
Understanding the need to perform cybersecurity audit
Today, hackers are more sophisticated and well organized than ever before. The ever-increasing number of cyber attacks, the sophistication of the attacks, and the damage they can cause have increased the importance of having adequate cybersecurity controls. A cybersecurity audit is a methodical examination of the system with an eye on detecting security vulnerabilities and enforcing the cybersecurity controls.
In short, cyber-attacks can destroy a company’s reputation, cost them a fortune in damages, and cause the company to lose customers. One way to protect a business from a cyber-attack is to conduct a cyber-security audit. A cyber-security audit reviews a company’s cyber-security policies and procedures to identify deficiencies in a company’s cyber-security practices.
Also Read: Choosing The Right Security Audit Company Made Easy
Some expected benefits of performing cybersecurity audits are:
- Uncovers security risks
- Increases reputational value
- Saves the cost of a data breach
- Improves security posture
- Helps in achieving compliance
Who needs a Cybersecurity Audit?
If you are a business owner, you are probably aware of the importance of a security audit. But what are the main goals of a security audit? How do you ensure you have suitable security systems in place to protect your company?
Security audits are essential for any company that wants to ensure its business data is protected. A security audit also helps businesses identify possible loopholes that need to be fixed. It may turn out that your company’s infrastructure is not as secure as you thought. A security audit tells whether your network is suitable for business needs. It ensures your company’s security is up-to-date.
If your company wants to make sure it’s doing everything it can to protect its business data, you need to know the company’s security posture. A security audit will tell you whether you are doing everything you can to protect your data.
Also Read- Drupal Security Audit | 10 Best Cyber Security Audit Companies [Features and Services Explained]
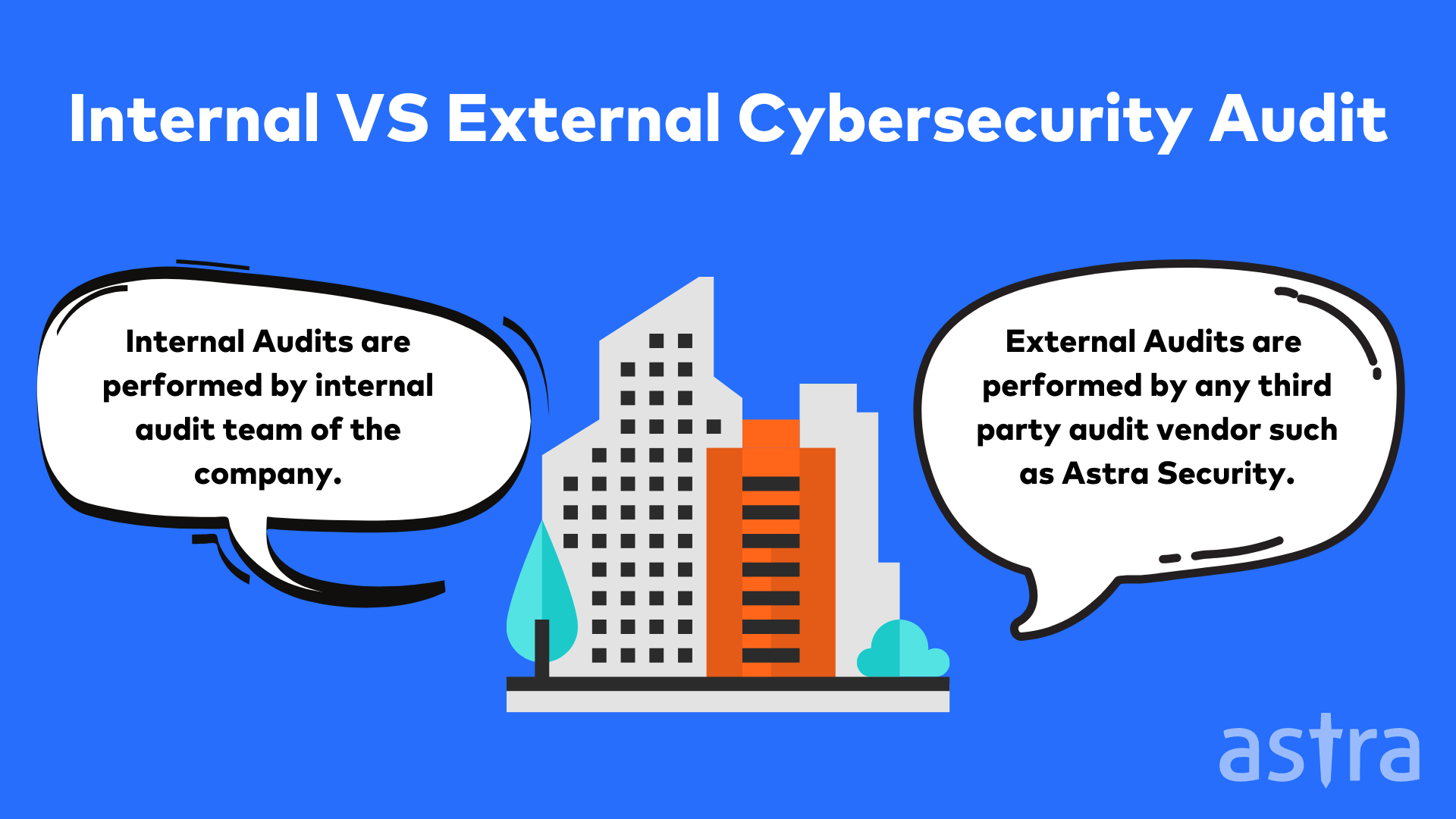
Types of Cybersecurity audit: Internal and External
External Cybersecurity Audit
An external cyber security audit examines a company’s IT security measures from an outside perspective. The security audit checks the effectiveness of the company’s security measures and identifies any gaps that can be filled. The external cyber security audit is a vital service for companies that want to protect their business and its data from unauthorized access.
Internal Cybersecurity Audit
An Internal Cyber Security Audit is a review of a company’s security systems, policies, and procedures. Companies often perform Internal Cyber Security Audits for a variety of reasons. Internal Cyber Security Audits are frequently performed to ensure compliance with regulatory requirements. An Internal Cyber Security Audit can be performed by a company’s staff or its internal audit department.
Also Read: Cloud Security Audit: Everything You Need to Know
5 Subsets of Cybersecurity
1. Network security
Network security protects information from unauthorized access. It is a process of controlling and protecting the resources and data shared and used by computers, networks, and organizations. Network security protects information from unauthorized access and modification and sometimes uses encryption to protect messages from unauthorized parties.
2. Application Security
Application security is the process of ensuring that the development, deployment, and operation of the software is protected from threats that could compromise its integrity, confidentiality, or availability. Application security focuses on identifying and mitigating all forms of application risks, including threats from internal and external sources. Security has been a primary concern from the inception of the project. Software security testing is conducted on every application from the first stages of development until the application is retired.
3. Data governance
Data Governance is a collection of processes, roles, policies, standards, and metrics that ensure the effective and efficient use of information in enabling an organization to achieve its goals. If you manage data and information, you need Data Governance.
4. Compliance
Regulatory compliance is a term used to describe the goal that organizations aspire to achieve in their efforts to ensure that they are aware of and take steps to comply with relevant laws, policies, and regulations.
5. Penetration Testing
With the help of Penetration Testing, an organization can find security risks that might otherwise go unnoticed. Penetration Testing identifies vulnerabilities that could be exploited by malicious hackers, which include: SQL Injection Cross-Site Scripting (XSS), Cross-Site Request Forgeries (CSRF), etc.
Related Read: Joomla Penetration Testing
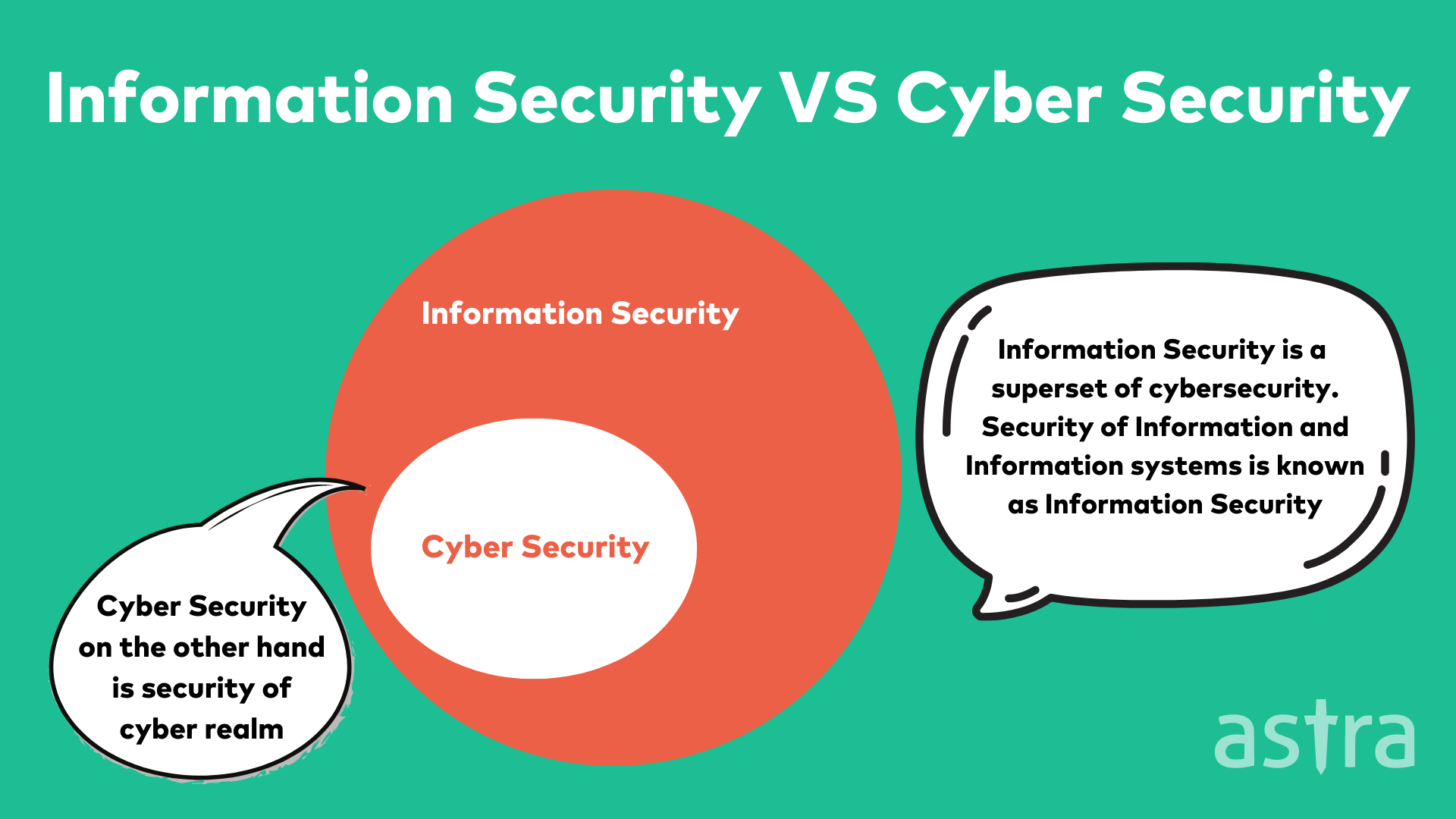
How is cybersecurity different from Information security?
Information security is one of the most important facets of today’s society. It plays an integral role in all our lives, whether we realize it or not. It’s not uncommon to hear the word “cybersecurity” used in place of “information security” or vice versa.
Both terms are used interchangeably, but, in reality, they are pretty different.
3 Best practices to perform cybersecurity audit
1. Define an Audit Scope
When you are planning to perform a cybersecurity audit, the first and most important thing you should do is define your scope. The scope of the audit is the foundation of your audit and dictates what you will and won’t do during your audit.
A solid scope ensures that the audit will provide the right level of assurance and be relevant to the stakeholders. When defining the scope, you need to include all the assets such as computers, servers, printers, storage devices, and networks that you want to test. You should also include all the information about the users who have access to these assets.
Reading Guide: Why Defining Penetration Testing Scope is Important?
2. Setup Scoping Meetings
While auditing cybersecurity management systems, an audit team will need to connect with a subject matter expert (SME) to get a complete view of your cybersecurity management. It’s more important than ever for auditors to communicate with an SME to get a comprehensive view of cybersecurity management.
An SME is a person who has a deep understanding of the system, project, or process being audited. In security management audits, an SME can be a staff member or a contractor who has been working on the system, project, or process being audited. Auditors need to have a conversation with an SME at the start of an audit to identify the controls audited and the cybersecurity management activities the auditor will be reviewing.
The SME will be a key partner throughout the audit, as the SME is the person who will help define the scope of the audit and help the auditor understand what they see during the audit.
3. Detect and Remediate Security Risks
You can’t manage what you don’t know exists. Vulnerability management is the process of identifying, prioritizing, remediating, and mitigating vulnerabilities in your organization. Vulnerabilities are weaknesses in your software, systems, network, and people that can be exploited to cause damage or gain unauthorized access.
A vulnerability is an entry point for an attacker. Vulnerability management includes the identification of vulnerabilities, prioritizing them, remediating them, and mitigating them.
Cybersecurity Audit Checklist
Cyber Security audit is challenging and a long process. Here are a few things to keep in note while performing the audit:
1. Policies and Procedures
- Company security policies in place
- Data Classification
- Physical Resources Classification
- Asset List
2. Training
- Secure Code training
- IT Training
- Anti-Phishing Training
- PCI-DSS Training
3. Physical Security
- Monitoring systems
- Screen locks
- Locked server rooms
- Fingerprint or Employee Card-based entry
4. Logging and Monitoring
- Logging and Monitoring standards
- Sensitive data in logs
- Logs retention
- File monitoring services
And the list goes on and on…
How can Astra help with Cybersecurity audits for your organization?
Astra is the leading cyber security company that provides all kinds of services to protect your and your customers’ data from hackers. We are a team of highly skilled and creative professionals passionate about delivering efficient, cost-effective cyber security services.
Our security experts are constantly working on developing new security tools to protect your data. We, at Astra, believe that if one is to survive in the digital world, one has to be constantly upgrading and improving its security posture.
What we offer:
1. All kinds of penetration testing services
2. Cybersecurity Audit
4. Rock-Solid Firewall
5. Top CMS security solutions (WordPress, Drupal, Joomla)
Learn more about what Astra offers!

Conclusion
When it comes to a company’s security, there are two things every business needs to do: audits and assessments. A good cybersecurity audit will let you know if your cybersecurity is where it needs to be. It could help you avoid a breach, improve your security features, and show customers, partners, and investors that you’re taking the proper steps to secure your data.
















