Article Summary
Drupal has been a popular choice for CMS however, it’s security has been a point of debate. The Drupal team has always claimed it to be the more secure CMS among the popular ones. Contrary to this claim, some critics have claimed that Drupal’s security is no different than any other CMS.
Drupal has been a popular choice for CMS however, it’s security has been a point of debate. The Drupal team has always claimed it to be the more secure CMS among the popular ones. Contrary to this claim, some critics have claimed that Drupal’s security is no different than any other CMS. These claims were backed by serious bugs, Drupalgeddon 1, 2 & 3 discovered during a Drupal security audit and Drupal penetration testing.
Commenting on this in 2018, researcher Troy Mursch said,
Drupal sites are still vulnerable, including websites of a large television network, a mass media and entertainment conglomerate and two well-known computer hardware manufacturers.
What is Drupal Security Audit?
A Drupal Security Audit is a process in which an authorized individual/group tries to identify various security vulnerabilities & loopholes present in a system or a website. It includes – code inspections of the core, plugins & modules; configuration checks, business logic error checks, and more.
In a nutshell, a Drupal Security Audit identifies and enlists security loopholes present in your web system that runs the risk of exploitation.
Get the ultimate Drupal security checklist with 300+ test parameters
What is Drupal Penetration Testing?
A Drupal Penetration Test is a step further into the Drupal security audit. In a Drupal Penetration Test, an individual/group tries to actively exploit the vulnerabilities (identified in the audit) emulating a hacker. This is to estimate the damage that each vulnerability can cause, if or when exploited. A penetration test also helps in weeding out false positives, that might have been flagged in the earlier step – Drupal Security Audit.
Why do you need Drupal Security Audit & Penetration Testing?
According to Drupal’s hacking stats, Drupal sites are vulnerable to attacks such as XSS, DoS, Code Execution, SQL Injection, HTTP Response Splitting, and various others.
Another study by Verizon shows that 43% of all data breaches target small and medium-sized businesses.
SMBs (Small & Medium Businesses) are a hacker’s paradise for they are usually vulnerable to sophisticated hacks. Plus, they do not attract much limelight.
Nevertheless, securing a website is not impossible.
A strategic investment in security solutions and measures can make your website impenetrable. One such proven ways remain – Drupal Security Audit & Pentesting. Finding vulnerabilities and then patching them can save a lot of your time and resources which would have otherwise been used in cleaning up a hack.
Also Read: 11 Top Penetration Testing Tools/Software of 2022 | Penetration Testing Quote
How to carry-out a Drupal Penetration Test?
To conduct a Drupal penetration test or Drupal security audit, certain tools are used. Manually downloading and install each tool may become cumbersome. So, it is advisable to use Kali Linux for this purpose. As this operating system comes loaded with most of the tools. Kali Linux can also be run on a windows machine using virtual box. Now that our Drupal security audit and Drupal Penetration testing environment is ready, let us begin!
1. DroopeScan
Before we begin with Drupal penetration testing, it is important to conduct a Drupal security audit first. So, the information gathered during a security audit can help us determine the attack points for penetration testing.
DroopeScan is a tool built using python for specifically finding vulnerabilities in sites using Drupal. To scan your site using this tool:
- Firstly, download it by visiting this link.
- Thereafter, install it using this guide.
- Now open the terminal on your system and type:
droopescan scan drupal -u example.org
Replace example.org with the name of your website and you are good to go!
2. Nikto
Another great tool for the Drupal security audit is Nikto. This tool is designed for scanning web server vulnerabilities. However, it is very noisy and may generate many false positives. So, turn off the firewall before using Nikto. These false positives can be later on weeded out during the Drupal penetration testing.
To scan your web server using this tool, open up the terminal in Kali Linux and type:
nikto -h www.example.orgReplace example.org with your website name. For more help, type:
nikto -H
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed] | Top 6 Web Pentest Tools You Should Not Miss
3. Sqlmap
After the injection points have been detected on the website during a Drupal security audit, it is now time for Drupal penetration testing. Here we will attempt to break into the website.
One of the best tools to pentest the database of a website is Sqlmap. Using this tool, we can not only enumerate the databases of your Drupal site but also obtain a reverse shell.
To see the databases of a vulnerable Drupal site, open the terminal in Kali Linux and type the following command:
sqlmap -h "example.com?param1=a" --random-agent --dbs --batchHere, replace example.com with your website and param1 with the vulnerable parameter. If the website is vulnerable, it will show all the databases. Similarly, any of the Drupal modules or plugins can be pentested for any SQL injection bugs.
For more help, type:
sqlmap -h

Also Read: API Penetration Testing: What You Need to Know
4. Commix
Commix is a tool that can check if your Drupal website is vulnerable to command injections. Therefore, it is a handy tool for Drupal penetration testing. This tool can exploit vulnerable parameters found during the Drupal security audit and upload reverse shells. It can also be used to find OS command injection bugs in Drupal core, modules, plugins, etc. Various examples of commix usage are given here.
For more help, open the terminal and type:
commix -h

Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
5. Xsser
Another most common vulnerability found in the popular CMSes is cross-site scripting vulnerability. To pentest your Drupal modules, plugins, etc for XSS bugs, use the tool Xsser. Moreover, this tool comes with a GUI interface, making it easy for beginners.
To use the graphical interface, open the terminal of your Kali Linux and type:
xsser --gtk
Thereafter, an interface like this will open. Use it to exploit XSS bugs in your Drupal site.

For more help check out the official documentation.
Professional Drupal Penetration Testing by Astra
By now, it may be clear that Drupal security audit and pen-testing is not an easy task, especially for beginners. Even experienced users may find it cumbersome.
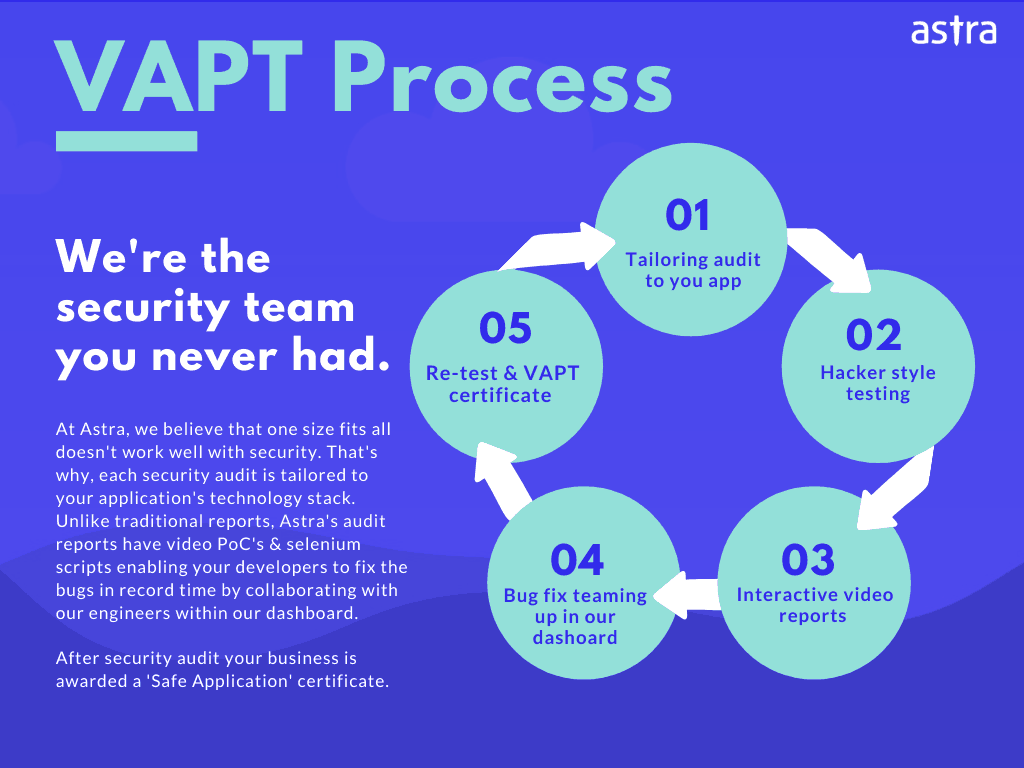
So how to tackle this? The answer is – hire an expert to do the job. Astra Security offers professional Drupal Security audit & Penetration Testing tailored for your website. Our Vulnerability Assessment & Penetration Testing (VAPT) program is done by security experts with the right mix of automated tools and human intelligence. This Drupal security audit finds key vulnerabilities like:
- Configuration and Deployment Misconfiguration.
- Drupal Core, Plugins & Theme Specific Vulnerabilities.
- Broken or Improper Authentication.
- Identifying Technical & Business Logic Vulnerabilities.
and many more in your system!
Get started today!
Don’t forget to download our Comprehensive Drupal Security Checklist developed by our security experts
FAQs
What is the timeline for Drupal Penetration Testing?
The timeline for Drupal Pentesting is 7-10 days. The rescan after fixing the vulnerabilities takes 3 more days. The timeline may differ slightly based on the scope of the test.
How much does penetration testing cost?
The cost for Drupal penetration testing ranges between $99 and $399 per month depending on the product, and the plan you are on.
Why choose Astra for Drupal Penetration Testing?
8000+ tests, adherence to global security standards, intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, multiple rescans, these are the features that give Astra an edge over all competitors.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.



















Hi there, is there any way I can secure drupal store? Just want to make sure that my site is safe.
Thanks for responding to the article. Drupal CMS is being used by various important organizations. In certain countries, it is used by governments also. This admiration can be attributed to its open-source framework and the spectrum of modules on Drupal. The modules enable site administrators to organize, customize and manage content easily on Drupal. For more info, visit here: https://www.getastra.com/blog/drupal-security/drupal-security-guide/
Is there any way I can block countries in drupal? If possible can you tell me how?
Thanks for responding to the article. Country blocking is a great & smart way to put your website off the radar for countries which do not cater to your needs. Most importantly, there are some countries which are notorious for sending attack vectors. Hence, blocking them would only be a prudent decision for your website. For more info, visit here: https://www.getastra.com/blog/category/cms/drupal-security/
I want to know more about file permissions in drupal? We have a drupal site and I don’t know much about file permissions.
Thanks for responding to the article. Drupal is an open source PHP written content management system. In other words, the source codes in Drupal are rewritable by everyone. If the Drupal file permissions aren’t set properly, it becomes really convenient for hackers to gain access to these files and then manipulate them. For more info on file permission visit here: https://www.getastra.com/blog/drupal-security/drupal-file-permissions/
My drupal site is redirecting to a strange website. How can I fix this? I am a bit worried.
Thanks for responding to the article. Don’t worry we got you covered. The Drupal redirect hack occurs after an attacker exploits the vulnerability in your website and modifies the site content to install malware. As a result, visitors to your website are redirected to spam and questionable links. For more info visit here: https://www.getastra.com/blog/911/drupal-hack-redirect/
Hi , I am thinking of developing a drupal site. Are there any recommendations I need to follow?
Thanks for responding to the article. Our Drupal security checklist contains easy to implement steps for beginners and experts alike. Following this Drupal secure coding checklist will help you to protect your website from hackers and make your website stand out and shine. You can get the checklist here: https://webpro.getastra.com/checklist/drupal
I own a drupal site and am looking for a decent scanner that can protect it. What features does your plugin offer?
Thanks for responding to the article. Astra’s hacker tested firewall protects your website against SQLi, XSS, LFI, RFI, Bad Bots, Spam & 100+ threats in real time. Apart from OWASP’s top 10 threats found in websites, the firewall is tailored to protect against known CVE’s. Our intelligent firewall detects visitor patterns on your website & automatically blocks hackers with malicious intent. For more info visit here: https://www.getastra.com/features
Hi, looking to take a security audit for our drupal site. Can you tell me what tests will be performed and info about security issues?
Thanks for responding to the article. Sure, you can visit here for more info on tests that we will perform while audit and pricing info: https://www.getastra.com/drupal-vapt. Looking forward to securing your site.