Cloud security audits are necessary to ensure that cloud-hosted applications and data are kept safe from unauthorized access and theft. Cloud providers level the ground for businesses by allowing them to host their apps and data in the cloud.
But the agility comes with some security challenges. A cloud security breach can be costly as it could result in significant financial losses.
In this article, we will discuss everything you need to know about cloud security and the audits conducted to evaluate it. We will start by discussing what a cloud security audit is and why it is important. Then, we will talk about the steps involved in it. Finally, we will discuss some of the challenges involved in the cloud security testing process and how to choose the right audit provider.
What is a cloud security audit?
A cloud security audit is an inspection of the security controls placed by an organization to protect its data and other assets in the cloud. The audit is usually conducted by an external auditor who uses various test cases and checklists to find out if the target security posture is up to the mark.
What is the concept of security in the cloud?
Security in the cloud is a shared responsibility between cloud providers and customers. Cloud providers are responsible for the security of their infrastructure, while customers are responsible for securing their data and applications. The following table will help you understand it better.
| Type of Cloud Service | Security Responsibilities of Cloud Providers | Security Responsibilities of Clients |
|---|---|---|
| Infrastructure as a Service (IaaS) | Virtualization. Network, Infrastructure, Physical | User Access, Data, Application, Operating System |
| Platform as as Service (PaaS) | Operating System, Virtualization, Network, Infrastructure, Physical | User Access, Data, Application |
| Software as a Service (SaaS) | Application, Operating System, Virtualization, Network, Infrastructure, Physical | User Access, Data |
5 Reasons why cloud security audits are necessary
The cloud has become the new norm for businesses of all sizes. It offers many advantages in terms of cost, scalability, and agility.
However, the cloud also comes with some security challenges. Evaluating the security health of your cloud environment as well as the data hosted on the cloud on a regular basis is necessary for various reasons.
A cloud security audit is important because it
- Helps ensure compliance with regulations and industry standards: A cloud security audit helps identify compliance risks and provides recommendations for remediation.
- Helps ensure the confidentiality, integrity, and availability of data: A cloud security evaluation helps organizations understand their cloud environment and identify potential threats. It also helps organizations to develop appropriate controls to mitigate those risks.
- Helps assess the effectiveness of security controls: A cloud security assessment helps organizations to verify that their security controls are effective in detecting and preventing unauthorized access to data.
- Helps assess the risk of data loss: Organizations need to identify potential sources of data loss and prioritize fixing those areas, a security audit helps with that.
- Helps improve the overall security posture: Identifying weaknesses in security controls helps an organization assess its cloud security posture and make necessary improvements.
Also Read: A Complete Guide to Cloud Penetration Testing | Security Audit Services: Importance, Types, Top 3 Companies
How often should cloud security audits be conducted?
The frequency of security audits for cloud infrastructure depends on the organization’s risk tolerance and the sensitivity of the data stored in the cloud. For most organizations, cloud security audits should be conducted at least annually. However, some organizations may require more frequent audits due to the sensitive nature of their data or the high risk of a cloud security breach.
How is a cloud security audit conducted?
A security audit in the cloud is conducted by an independent third-party, such as Astra Security. The auditor will assess the customer’s security controls and make recommendations for improvement. The security audit process typically includes the following steps:
Steps involved in a security audit
Cloud security testing typically involves five steps:
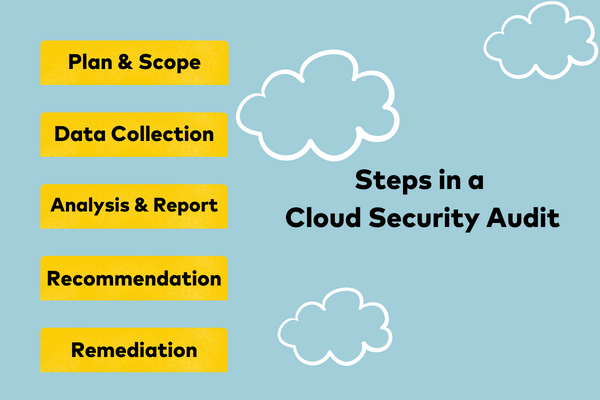
- Planning and scope definition: This step involves defining the audit’s objectives, scope, and approach.
- Data collection: This step involves collecting data about the cloud environment. This data can be collected manually or through automated tools.
- Analysis and reporting: This step involves analyzing the collected data and preparing a report that highlights risks and vulnerabilities.
- Recommendations: This step involves providing recommendations on how to mitigate risks and vulnerabilities.
- Remediation: The recommendations received in the previous step are used to fix the security loopholes in the cloud.
Read also: Complete Guide on AWS Security Audit
10-point cloud security audit checklist
Here’s a checklist followed by the best cloud security companies during an audit.
- Identify the cloud provider(s) and service(s) being used.
- Understand the cloud provider’s security controls.
- Identify who has access to the cloud environment and what level of access they have.
- Ensure that data in transit is encrypted.
- Ensure that data at rest is encrypted.
- Ensure that strong authentication and authorization controls are in place.
- Implement least privilege principles.
- Monitor activity in the cloud environment.
- Use tools to detect unusual or suspicious activity.
- Keep your cloud environment up to date with the latest security patches and updates.
Challenges involved in a cloud security audit
Security audits for the cloud can be challenging for a number of reasons.
- First, cloud environments are constantly changing, which makes it difficult to keep track of all the changes.
- Second, cloud providers have different security policies, which makes it difficult to assess all the risks and vulnerabilities. You have to be very careful about choosing the test cases lest you violate the cloud security policies.
- Third, cloud environments are often complex and large, making it difficult to collect all the data needed for the audit.
- Fourth, cloud providers often have different levels of security, which makes it difficult to ensure that all the risks and vulnerabilities are identified.
Also Read: Security Audit Company and Services [Top rated]: How to Pick
Things to look for in a cloud security testing firm
Cloud security testing can be a long, exhausting, and nerve-wrenching experience considering how much may ride on it. You want to enlist the support of the very best fit for your needs. Here are certain properties of the cloud pentest providers that you should look into.
- The cloud security test provider should be equipped with both automated and manual security testing abilities to conduct a wholesome security audit
- The security audit provider should be aware of and compatible with the cloud security policies placed by your cloud service provider
- There should be an opportunity for you to pick up cloud security best practices – it should be a learning experience for your employees
- It makes your life much easier if the audit provider also extends remediation support
- The security audit firm should help you prepare for the security compliances you are aiming to acquire
Cloud security testing with Astra Pentest
Astra Security has created a benchmark in the field of security testing with their Pentest Suite or Astra’s Pentest. When it comes to optimized cloud vulnerability assessment and penetration testing for AWS, Azure, or GCP, Astra’s Pentest is the most comprehensive, accurate, and user-friendly solution that you will find.
With Astra you get
- 8000+ tests to detect every single security loophole
- Prioritized vulnerabilities and accurate risk scores to help you tackle the most critical issues first
- Coverage of custom configurations and services
- A collaborative vulnerability management dashboard
- Step-by-step guidance to remediate the vulnerabilities

Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
The security experts at Astra inspect your cloud security posture from the inside. Apart from the manual pentesting skills they use a state-of-the-art vulnerability scanner supported by a regularly updated vulnerability database.
Your cloud setup is tested against CIS benchmarks, OWASP top 10, SANS 25, and other relevant industry standards. You also get a clear picture of your compliance scenario with the pentest compliance feature accessible from the vulnerability management dashboard.
Final thoughts
The anxiety, difficulty, and expenditure readily associated with cloud security can be alleviated manifold by partnering with the right security testing company and imbibing some simple security practices in your organization’s culture. The purpose of a cloud audit is to help you optimize, and secure your cloud-hosted operation and it should not feel otherwise.
If you have doubts, questions, confusion, or curiosity about cloud security audits, you are welcome to leave your questions in the comment box or get on a call with a security expert and have a fruitful discussion.
FAQs
How much time does a cloud security audit take?
It can take up to 10 days to complete the process of a security audit in the cloud.
What is the cost of a cloud security audit?
The cost of a cloud security audit can vary quite a bit based on the scope of the audit, the size of the company, and the type of operations you run in the cloud. $5000 is a ballpark figure.
Is cloud security audit and compliance audit the same?
A cloud security audit is something you conduct to detect and fix all vulnerabilities and assess the security controls. It prepares you for a compliance audit, but they are not the same.
















