According to a recent report by IT Governance, there were 71 publicly disclosed security incidents in September 2023 alone, accounting for 3,808,687,191 compromised records, bringing the year’s total to over 4.5 billion.
Thus, ensuring the integrity, confidentiality, and availability of data stored and processed in the cloud has become a paramount concern for enterprises worldwide. This is where cloud security assessments become an indispensable tool in your cybersecurity arsenal.
In this article, we will discuss the same in detail including benefits, steps, and important considerations.
Action Points
- Cloud security assessment is a process where security professionals evaluate the security of an organization’s cloud infrastructure for security risks.
- It mitigates risks, enhances proactive security measures, and ensures compliance with industry standards.
- Performing a cloud security assessment involves scoping, discovery, testing, reporting, and retesting for comprehensive security evaluation.
- Considerations before starting a security assessment include assessing current and future environments, allocating assessment time, and evaluating costs.
- Key practices for cloud security assessment include data encryption, access control, identity authentication, monitoring, patch management, incident response, compliance, data recovery, vendor security, and employee training.
What is Cloud Security Assessment?
Cloud security assessment is a process where security professionals evaluate the security of an organization’s cloud infrastructure for security risks. The security assessment of a cloud-based application examines the security controls in place and whether the controls are appropriate for the specific use cases that the application is designed for.
Why is it Important to Conduct a Cloud Security Assessment?
Cloud-based solutions are a significant asset for organizations but can also present risks. The security assessment should help you identify whether those risks are appropriate for your specific use cases.
Cloud security assessments are a proactive measure in a cloud security architecture that can help you avoid a data breach and minimize the damage in case of a breach.
Cloud Security Assessment is also a key part of cloud compliance requirements as most of the commercial cloud service providers (CSPs) adhere to the security standards of ISO/IEC 27001, ISO/IEC 27002, and NIST SP 800-53. A successful cloud security assessment provides the following benefits:
- Helps in improving the cloud security posture
- Uncovers security vulnerabilities and their remediation
- Provides a structured framework for cloud security assessment
- Helps in identifying the configuration and vulnerability issues of the cloud infrastructure and applications
- Provides a more secure environment for cloud services, applications, and data
- Helps in achieving compliance with the industry standards, regulations, and guidelines
How to Perform a Cloud Security Assessment?
Performing a successful cloud security assessment is not an easy task. It takes time, resources, and experience to accomplish. Here are the five steps to conducting a successful cloud security assessment:
Step 1: Initial Scoping
The first step in the process is to understand your cloud application’s current state. This will help you to determine the scope of your assessment. This involves identifying all the components, configurations, and data repositories within your cloud environment, along with clarifying the specific objectives of the assessment.
During the process, you also identify the resources required for the assessment, such as personnel, tools, and any third-party services.
Step 2: Reconnaissance/Discovery
Reconnaissance is the second step after the scoping phase, in which the auditors perform recon on the agreed scope. This step involves meticulous examination and documentation of assets, services, and processes including probing into the intricacies of the cloud architecture, discerning how data flows within the network, and mapping out potential attack vectors..
The primary aim is to discover or gather information about an organization’s assets and weaknesses and how hackers can attack it.
Step 3: Vulnerability Testing
Vulnerability Testing is a process to detect the potential vulnerabilities in the already discovered assets. Vulnerability testing aims to assess the risks that can be seen in the discovered assets. Testers use various tools to test the cloud and search for vulnerabilities in the cloud infrastructure.
They approach this phase with a hacker mindset, actively seeking security loopholes and simulating exploitation scenarios.
Step 4: Reporting
The output of the vulnerability scanning is passed to the reporting team to prepare a detailed report. This phase is essential as it synthesizes the findings and insights gathered throughout the assessment process into a structured and comprehensive report that details the security status of the infrastructure and the applications.
It serves as a roadmap for mitigating vulnerabilities, ensuring compliance, and improving overall security resilience in the cloud environment.

Step 5: Retesting
Retesting is the last phase of the assessment by cloud security companies, and it is done only once the issues are fixed, and the customer wants to get it tested again. A retest is essential to verify the issues have been fixed.
Retesting is a critical stage of the cloud assessment; hence, it is recommended to include it in the project and not ignore this phase.
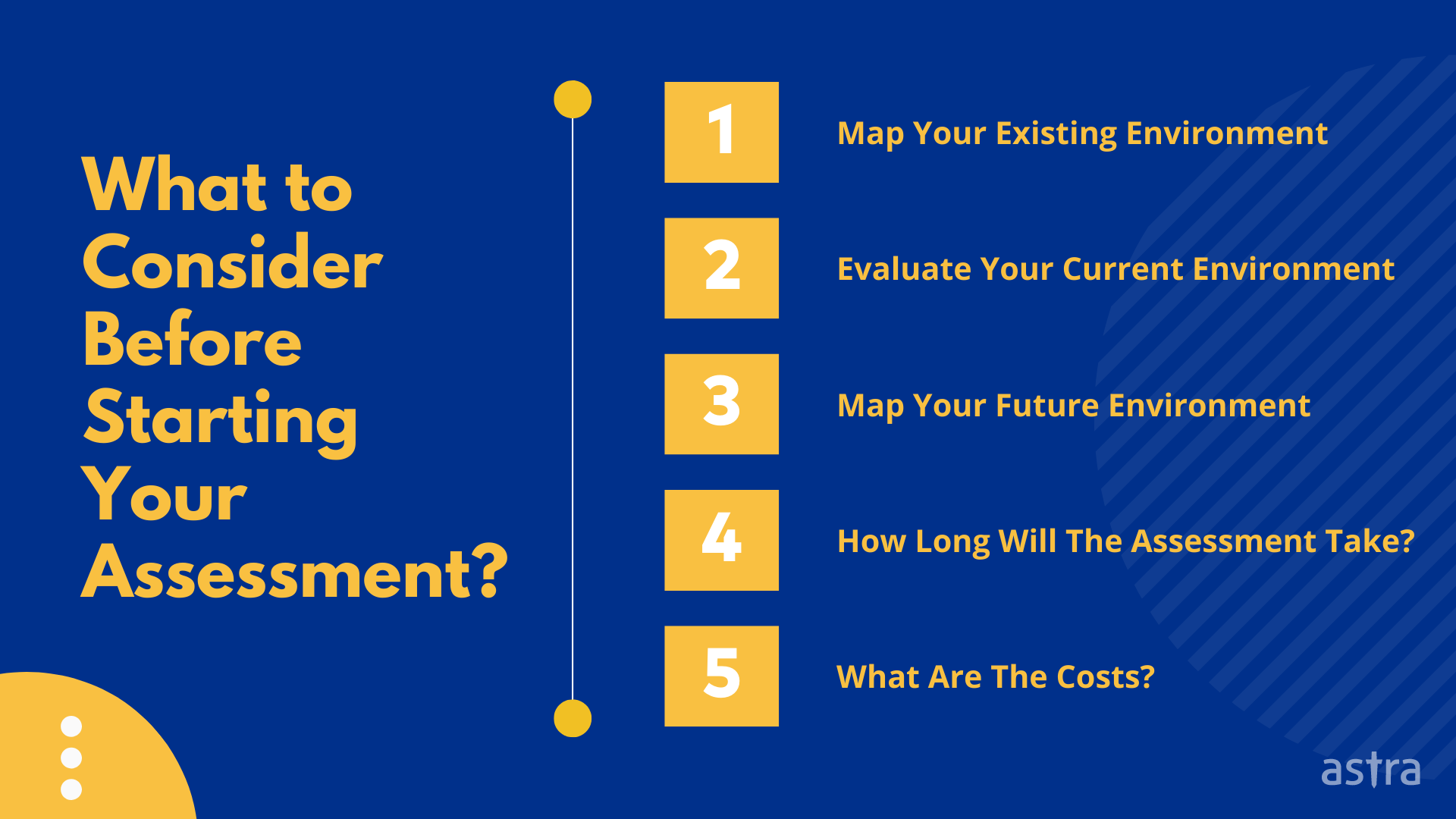
5 Things to Consider Before Starting Your Cloud Security Assessment
Before starting a cloud assessment, you must understand what you are evaluating. There are multiple components to a cloud security assessment, including mapping your existing environment, evaluating your current environment, and mapping your future environment.
Below, we walk you through each of these steps.
1. Map Your Existing Environment
This step will help you map your current environment to determine what you are already doing. You will want to map both your existing internal resources and your external environment.
Internal resources include network infrastructure, user access management, and user permissions. External resources include things like data storage and network connectivity.
2. Evaluate Your Current Environment
Three areas need to be evaluated: the technology, the security controls being used, and how they are implemented. This can be done using various tools, including security analytics and monitoring tools, security assessment tools, and security scanning tools.
You will want to determine what factors have the most significant impact on your organization’s security posture. These factors will give you context for your assessment findings.
3. Map Your Future Environment
Cloud services come in all shapes and sizes, and your assessment will help you determine which options are best for your organization. You will want to map your future environment based on what you know about your current environment, your desired environment, and your budget.
4. How Long Will The Assessment Take?
This is hard to predict, but you should expect to spend 10 to 15 percent of your assessment time mapping your existing environment, 65 to 70 percent evaluating your current environment, and 10 to 15 percent mapping your future environment.
5. What Are The Costs?
Cloud services can be cost-effective, but they can also pose security risks. It’s important to understand the cost of the tool/service provider that you opt for. The assessment you will want to perform will depend on your budget and risk appetite.
Cloud Security Assessment Checklist
Here’s a simple checklist to keep in mind while evaluating the security of your cloud environment:
1. Data Encryption:
Ensure that data both in transit and at rest is encrypted using strong encryption algorithms and that encryption keys are managed securely.
2. Access Control:
Implement robust access control mechanisms, including role-based access control (RBAC) and least privilege access, to restrict unauthorized access to cloud resources.
3. Identity and Authentication:
Utilize multi-factor authentication (MFA) and strong identity management practices to verify and secure user and system identities.
4. Logging and Monitoring:
Set up comprehensive logging and monitoring solutions to detect and respond to suspicious activities and potential security breaches in real time.
5. Patch Management:
Regularly apply security patches and updates to cloud resources, including virtual machines, containers, and serverless functions.
6. Incident Response Plan:
Develop and test an incident response plan to effectively respond to security incidents, including breach detection, containment, and recovery procedures.
7. Compliance and Auditing:
Ensure compliance with relevant security standards and regulations (e.g., GDPR, HIPAA) and conduct periodic security audits and assessments.
8. Data Backup and Recovery:
Implement a reliable data backup and recovery strategy to mitigate data loss and ensure business continuity in the event of a disaster or cyberattack.
9. Vendor Security:
Assess the security practices of your cloud service provider (CSP) and ensure they meet your organization’s security requirements. Review their adherence to industry standards and certifications.
10. Employee Training and Awareness:
Provide security awareness training for employees with the help of training software and ensure they understand and follow best practices for cloud security, such as recognizing phishing attempts and securely handling data
Why Choose Astra’s Cloud Security Assessment Solution?
The cloud offers increased flexibility and time savings for companies. Cloud-based solutions have become a trendy way of doing business in the modern world.
At Astra, we understand that businesses will continue to take advantage of cloud-based solutions to improve their business processes. We also understand that security is a high priority for many businesses using cloud-based applications and data storage.
Astra’s cloud security testing solution is a uniquely powerful and highly customizable cloud service that can be used to conduct automated, continuous, and on-demand assessments of the security of any cloud environment.
The service is offered as a SaaS, which means that it can be accessed whenever you need it, and it comes with several powerful features.

Conclusion
Fretting about the security of your data is a waste of time and energy. Taking proactive measures to protect your data is the best way to ensure that your organization is safeguarded.
If you’re in the process of conducting a cloud security assessment or just looking for ways to protect your company’s sensitive data better, you’ve come to the right place.
At Astra, we provide an easy-to-use cloud security platform that gives you visibility into your data and helps in securing them. To learn more about getting started with a cloud security assessment process, don’t hesitate to get in touch with us; one of our security consultants will be happy to help you.
















