An increase in data breaches, data exposures, and data leaks has been an ongoing trend for the past few years. This is a result of improperly secured networks and applications and hackers finding new ways to break into the systems. In the first half of 2021, more than 118 million people were impacted by data breaches, exposure, and data leaks. Defining penetration testing scope plays an essential role in avoiding data breaches and securing a company’s data.
Introduction to Penetration Testing
Penetration Testing is a process to find security bugs within a software program or a computer network. It is used to find flaws or weaknesses within an existing software or computer network to make it more secure.
Penetration Testing is often conducted by a third party that is not affiliated with the software company or network provider. The purpose of a Penetration Testing Service is to find the vulnerabilities within the IT infrastructure.
Penetration testers can perform Vulnerability Assessment and Penetration Testing manually or by using software tools. The software tools are automated, and they perform the scanning of the system.
What is Penetration Testing Scope?
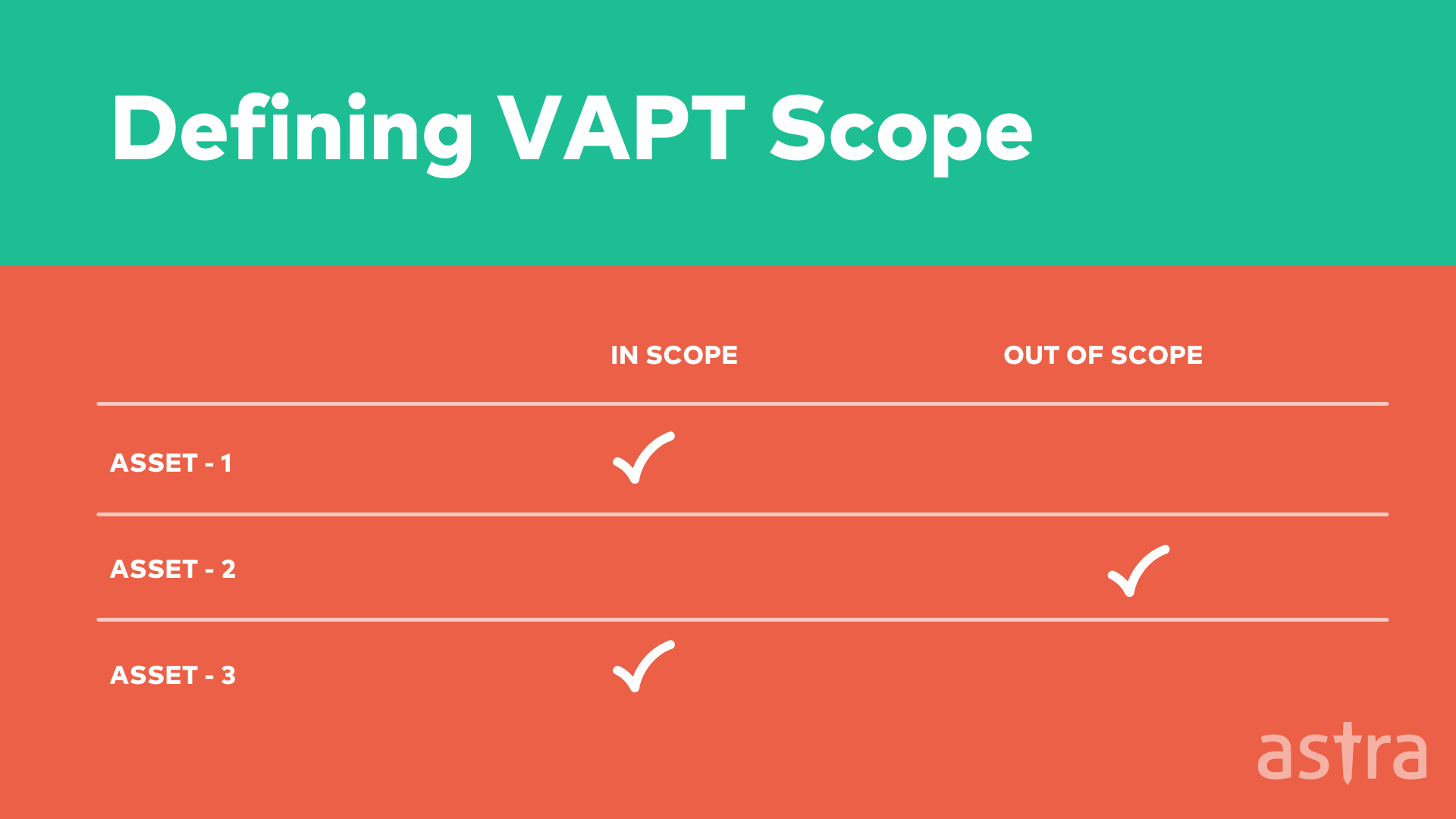
Penetration Testing scope is the combined list of everything that a penetration testing team will examine or has agreed to not examine in a pentest.
Pentesting scope is never a single variable or a sole component. The scope of an engagement is the sum of all variable factors to be tested or excluded. The pentesting scope is never something that is limited to just a list of items. It includes the enumeration of all variable factors surrounding the engagement, including its policies and any external factors that may affect the test.
Penetration testing scope is different from a test plan, which lists all the items to be tested. An organization’s project manager usually provides its scope. It’s usually written as a list of variable factors; the enumeration of the scope is usually a paragraph or a set of paragraphs.
Read more on- Pentest Related FAQs | Continuous Penetration Testing: The Best Tool You’ll Find in 2022
Why should you define Pentesting scope?
The scope of a penetration test is an essential part of a successful penetration test. A penetration test is a fantastic way to learn about your organization’s risk posture. However, it needs to be appropriately scoped to ensure that the organization gets the most value.
If a penetration test is too narrow, the organization may miss an opportunity to protect itself from an actual attack better. If a penetration test is too broad, the organization may waste time and resources that could have been put to better use.
Before you begin any penetration test, it is essential to understand why you need to define the scope of your test. This is very helpful if companies or customers send you a test if the objective isn’t communicated.
Also Read: A Complete Guide to Cloud Security Testing | Third-Party Penetration Testing And Why You Should Consider It
Understanding OOS: Out of Scope
If you’re wondering what exactly “out of scope” means in the penetration testing scope, it’s a term used by many companies to describe a specific area or a set of conditions that a penetration test cannot include.
Defining OOS in pentesting scope is a way for a company to ensure a clear understanding of what to expect from a penetration test and what isn’t going to be included in the test.
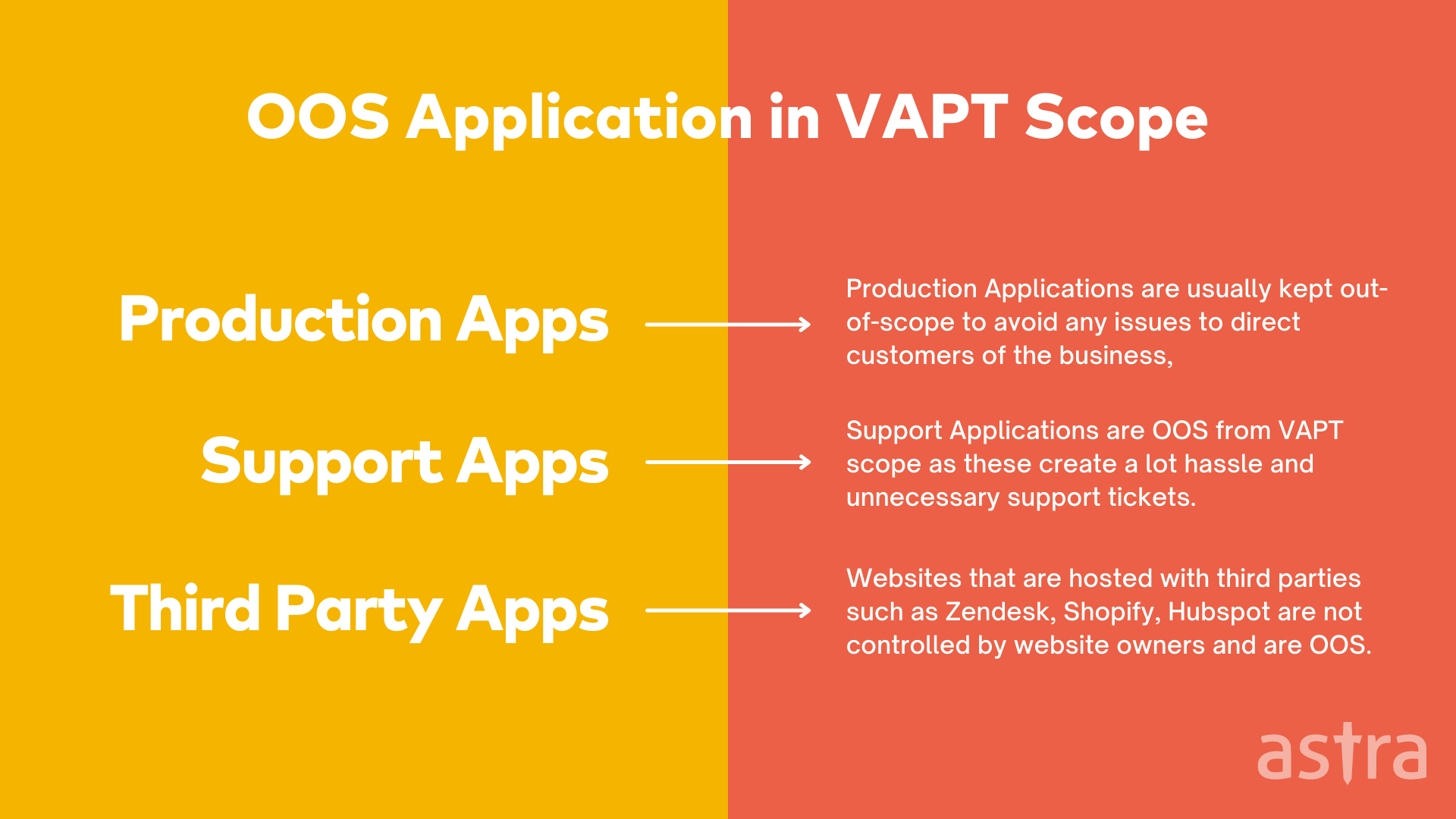
Some common assets that are usually out-of-scope of Penetration testing scope:
- Production applications
- Support platforms
- Customer-specific subdomains
- Subdomains managed by third parties such as Shopify, Zendesk
Also Read: 11 Best Penetration Testing Tools & Platforms of 2022 | API Penetration Testing: What You Need To Know
How is Vulnerability Assessment different from Penetration Testing?
A vulnerability assessment is a method used to determine a system (or network’s) risk for being exploited by a threat source. It is also used to identify weaknesses and vulnerabilities in a system and assess the impact of these weaknesses and vulnerabilities. Vulnerability assessments are performed to identify and address weaknesses in systems and networks before potential threats can exploit them.
On the other hand, penetration testing is a security testing technique to evaluate security mechanisms in place in a system or network. It is used to test the strength of the defenses in place to identify and exploit possible weaknesses in the system. It involves active attempts to breach security and determine the extent of possible damage that could be done.
Penetration testing usually involves performing a series of actions and analyzing how the system reacts to them. It is an essential process for assessing risk and improving overall security in a network or system. Penetration Testers can perform penetration testing in several ways: in a real-world environment to identify vulnerabilities and in a test lab setup to simulate a real-world environment to identify vulnerabilities and security breaches in a controlled manner.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
What is inside a Penetration Testing Scope?
The scope of a vulnerability assessment is one of the essential parts of the process. It’s the document that defines what you are doing. It’s where you define what you are testing for vulnerabilities, what you are not testing for, and what you are checking to ensure that the correct procedures are being followed.
Penetration Testing Scope document usually contains the following details:
- Assets in scope
- Assets out of scope
- Vulnerabilities in-scope
- Vulnerabilities out-of-scope
The scope is part of the contract between the customer and the security assessor. The scope defines what will be tested, in what manner, and in what time frame. A pentesting scope should be in writing (electronic or paper) to communicate clearly between the customer and the security assessor.
How Penetration Testing is performed?
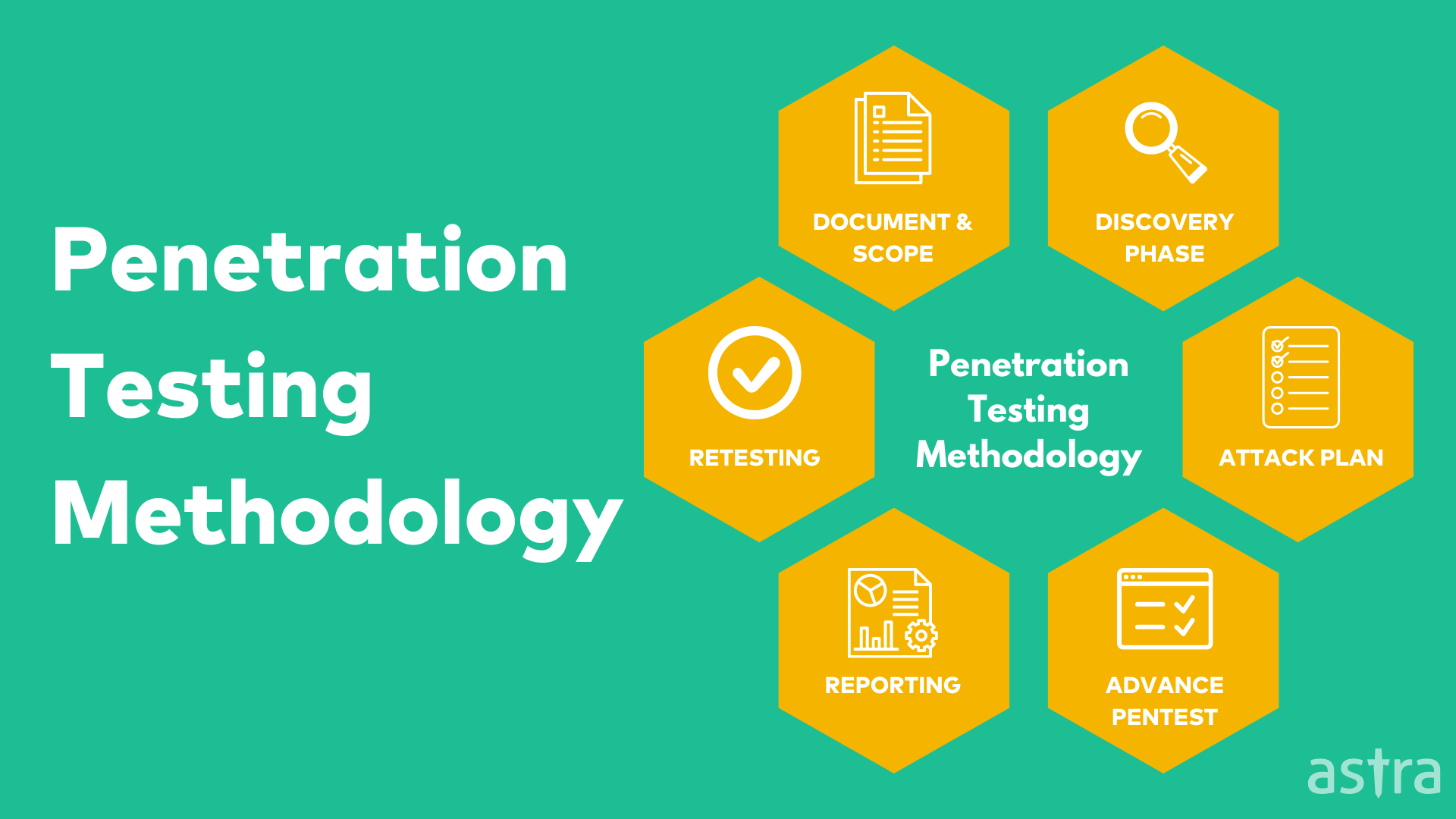
Penetration Testing is performed in 4 steps. Let’s understand them in depth:
Step 1: Information Gathering and Pentesting Scoping
Information gathering is the process of gathering data about a target using a variety of methods. The goal is to collect as much data as possible for a given target. This can include their network configuration, operating system, services, users, and so on.
Information gathering is the first step in any penetration testing engagement. It is also a significant step in incident response engagements. The data that is gathered from information-gathering is used in the following phases. It is used to decide which phases to do.
Step 2: Vulnerability Analysis
Vulnerability Analysis is a methodology used in the penetration testing process to test for vulnerabilities in a web application. It involves using a variety of tools and techniques to determine the security risks in a system. It is a way of examining a system with a completely open mind and curiosity about what you find.
Vulnerability analysis focuses on the security of a system. It is a way of looking at a system and determining whether it is secure enough, given its role and the conditions of its use. You can use vulnerability analysis to help determine what security controls you need to implement.
Step 3: Exploitation
After the Vulnerability analysis phase, the team of penetration testers starts gathering public exploits for the vulnerabilities that were found.
The exploitation phase is not limited to public exploits; the team tries all the possible exploits, even handcrafted, to exploit the vulnerability.
Step 4: Reporting and Remediation
The process of reporting and remediating the vulnerabilities found in the application is always a challenging part. It is important to document each vulnerability and its risk level, along with a detailed explanation of how to fix it. This will help developers in understanding the severity of the issue and help them in fixing the issue.
Checkout Astra’s Amazing Sample VAPT Report
Why should you know about Astra’s Pentesting Methodology?
When it comes to penetration testing, there are many different types of customers. Some of them are small businesses that need to protect their websites. Some are large enterprises with particular security needs.
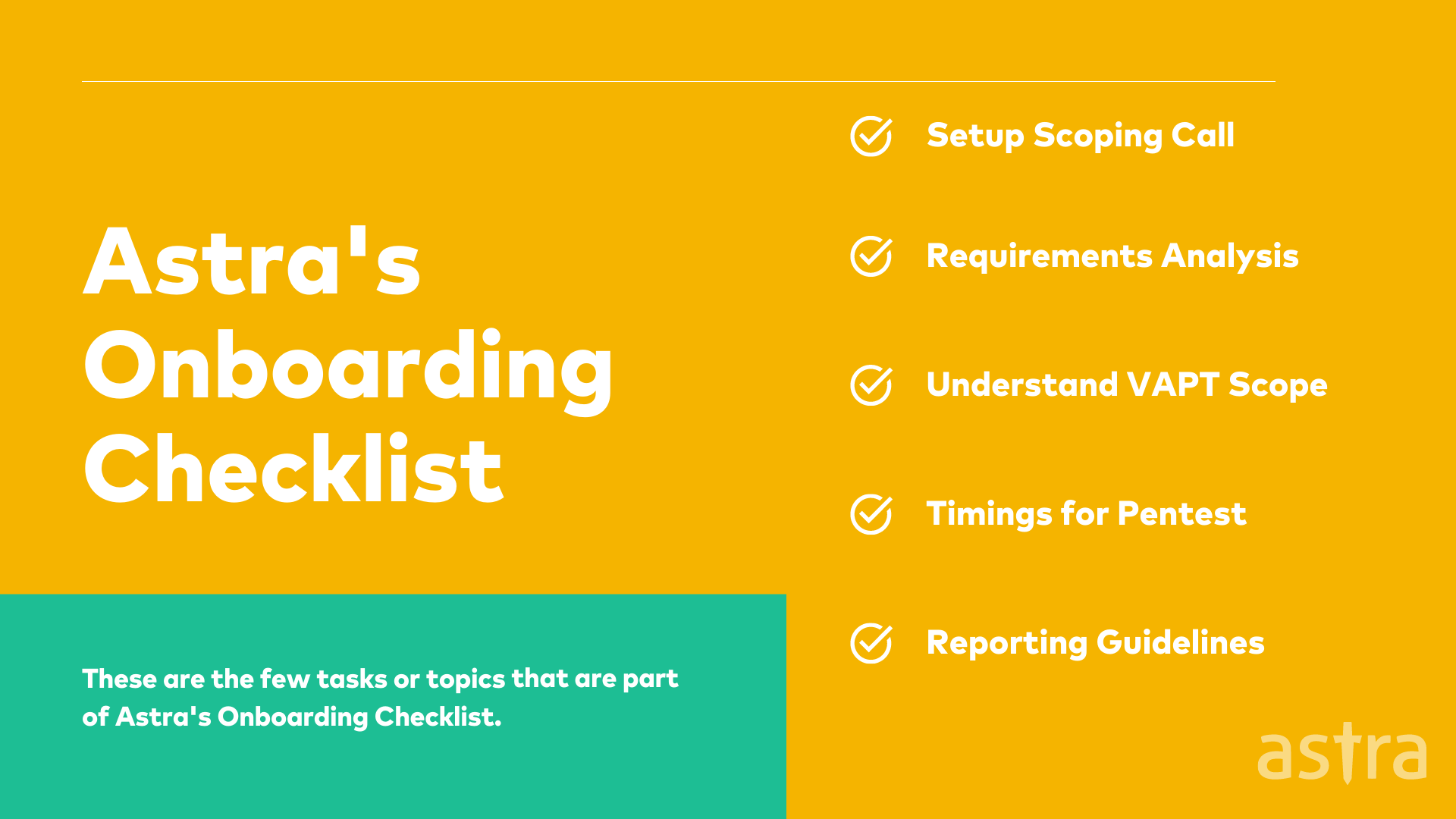
One of the biggest challenges penetration testers face is how to satisfy different customers with different needs. At Astra, we use our proprietary Pentesting methodology to help our clients understand what penetration testing is all about and how it will help them keep there infrastructure secure.
Astra’s Pentest solution starts with an initial call known as Penetration Testing scoping call as part of our on-boarding process. The main motive of this call is to understand the customer’s requirements to serve them in the best possible way.
Still not sure? Checkout why you should choose Astra as your VAPT Service Provider.
Conclusion
The scope is everything. It’s what separates the security professionals from the wannabes. The penetration testing scope is what defines how you go about doing your work for conducting a comprehensive vulnerability assessment and penetration testing for your website or network asset. At Astra, We understand the need for a well-defined scope; classifying assets into in-scope and out-of-scope is the first and foremost step.
FAQs
1. How is penetration testing performed?
Penetration testing consists of four key steps. Security experts use various methods to gather information from the target’s network configuration, operating systems, services, etc. The pentest scope is defined during this step. In the next step a combination of tools and techniques is used to test the target for security vulnerabilities. Then the security team tries all possible ways to exploit the vulnerabilities found in the earlier step. Each of the vulnerabilities is reported along the recommendations for remediation.
2. How much does penetration testing cost?
The cost for penetration testing ranges between $349 and $1499 per scan for websites. For SAAS or web applications it ranges between $700 and $4999 per scan, depending on your requirements. Learn more
3. How does Astra help with Penetration testing?
The security engineers at Astra perform extensive manual pentest on top of machine learning driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes.
















