Third-party penetration testing is the process of hiring an external penetration testing company for carrying out a thorough hacker-style evaluation of one’s security systems in place. This aids in finding any hidden vulnerabilities before they can be exploited by malicious attackers for data theft or deletion.
Third-party penetration testing should be done by an experienced professional at least twice a year or when any updates or changes have been made to the existing security system.
Penetration tests can be carried out internally or externally. When carried out externally it is known as third-party penetration testing since providers are hired externally. Let us check out the benefits of carrying out third-party penetration testing, the important steps for it, and the factors in choosing the right service provider.
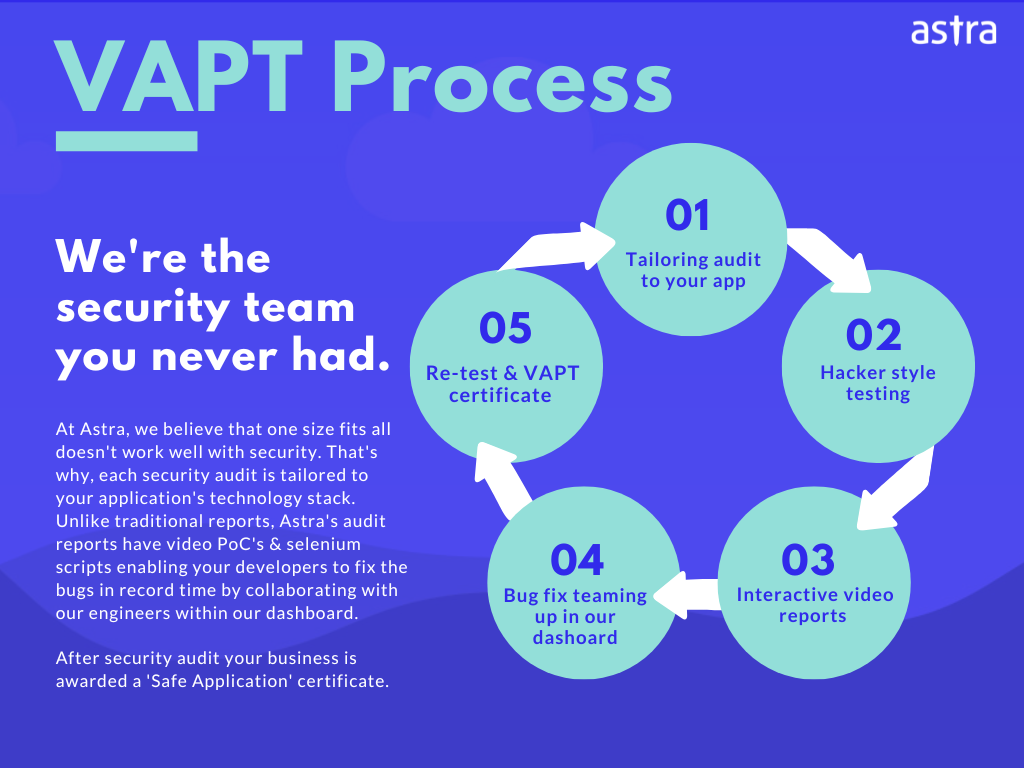
Benefits Of Third-Party Penetration Testing
1. Discover Unidentified Vulnerabilities
Third-party penetration testing can help organizations identify vulnerabilities that might have been missed during an internal pentest. This usually occurs since the internal pentests are already well aware of the system they need to penetrate.
Whereas, in the case of 3rd-party penetration testing the pentesters do not have many details other than what has been divulged by the company. This means that their tests are more unbiased in nature.
2. Attain and Maintain Compliance
Most of the regulatory compliances like GDPR, SOC2, ISO 27001, HIPAA, and PCI-DSS require security testing to be carried out externally for quality checks and assurance. Since external penetration testing is more comprehensive than in-house pentests, it is generally preferred to ensure compliance and find any possible areas of non-compliance that might be missed by an internally conducted pentest.
3. Efficient Risk Management
Carrying out such pentests can help identify the vulnerable areas within a security system that could potentially be missed by internal pentests. Finding such vulnerabilities before they’re exploited by malicious attacks plays a vital role in efficient risk management.
Since even the most minute risks stand a better chance of being detected by a third-party pentest. Such tests definitely help manage and fix vulnerabilities before they get exploited.
4. Assessment Of Threat Response Time
A 3rd party pentest is usually hacker-style, conducted with very less or no prior knowledge of the target system. Such a test can not only help identify flaws but also help in assessing the time taken for a security response to an event like this.
Such assessments can help companies improve the security measures in place to speed up the response time. This in turn will be highly beneficial in the quick detection of threats and fast responses against them.
5. Increased Reputation
Having a third-party penetration testing provider conduct a thorough security assessment is a requirement for some companies to consider your organization’s services.
This helps assure that your organization meets the potential client’s security needs completely. Thus it can be said that carrying out 3rd party pentesting can increase your company’s reputation and trustworthiness among the existing and potential clientele as well.
6. Enhanced Protection
3rd party penetration testing periodically helps enhance and strengthen the security system in place. This is through the comprehensive detection of any and all vulnerabilities, their immediate fixing, and the strengthening of existing security measures in place to make the detection and response to threats as fast as possible.
7. Vendor Certification
A pentest certification helps a SaaS vendor qualify as ‘secure for business. This increases the likelihood of that vendor’s services being chosen. Third-party penetration testing vendor certification also ensures that the company or vendor is completely compliant with the existing compliances.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Important Steps In Third-Party Penetration Testing?
1. Detailed Scoping
Scoping involves developing an extensive understanding and agreement between the third-party pentester and the target. This is done to avoid any liability issues and to avoid missing the testing of any important assets.
Scoping is the stage where discussions and decisions on what can and cannot be done are made, i.e. the rules of engagement are set prior to the testing. This includes answering the scoping questionnaires prepared by the pentesting team.
It is also important for the testing team to know and understand the motives that require the target organization to conduct a security scan. This includes understanding what areas of security they are most worried about, why they require a penetration test, any specific compliance that needs to be checked for, and when to start the penetration test as such.
2. Reconnaissance (Identification of Assets)
This step includes the identification of assets that need to be tested as well as gaining as much information about the target as possible without the target’s assistance. This can be done passively or actively but when doing the latter permission is absolutely mandatory.
Two major parts of a successful reconnaissance are the discovery of assets and content. Assets discovered usually include domains and their sub-domains. Whereas content involves the resources specific to a particular asset.
3. Exploitation
The earlier two stages constituted the pre-attack phase while this step is the actual attack phase where the exploitation of discovered assets occurs.
The assets found are scanned using automated scanners thoroughly to find vulnerabilities. Here tools like Astra’s Pentest and BurpSuite are made use of. Once such vulnerabilities are found they are exploited using different tactics to gain access internally.
They exploited to the maximum possible extent within the constraints of the ROE to understand the extent of damage that could be caused by a vulnerability.
4. Reporting
Once the exploitation stage is over and the systems are restored, a detailed report is generated by the pentesting team. This report would mainly detail the rules of engagement decided prior, the assets and content discovered during the exploitation, and the vulnerabilities found during the scanning phase of exploitation.
Each vulnerability will be listed, and the extent of damage caused by it will be explained in detail with its severity scores. Along with this, possible remediation measures are also mentioned. Additionally, the methods and tactics used to exploit these vulnerabilities are also explained.
How To Select The Right Third-Party Penetration Testing Provider?
1. Type of Service Required
The selection of the right third-party pentesting provider largely depends on your organization’s needs and requirements. Why are you looking to hire a third-party penetration testing service provider? Is it for maintaining or achieving specific compliance like PCI-DSS, SOC 2, ISO 27001, and HIPAA?
Having these questions and their answers in mind will help you narrow down the right kind of services and third-party penetration testing adapted specifically for your needs. Penetration tests can also be customized according to your needs if you want them to be areas specific or if you want them to be generally comprehensive.
2. Based on Compliance
Does third-party penetration testing cater to the right compliances required by your organization? This is an important detail to figure out before settling on your top choices.
Such compliances can be industry specific like HIPAA for the healthcare industry, PCI-DSS for the financial industry, and others like GDPR, SOC 2, and ISO 27001 which are generalized regulations set for security.
3. Experience And Reputation
Does the company have longstanding years of experience and an associated reputation? Are customers satisfied with the services offered by them? This can be checked by inquiring with the previous customers. Online reviews and testimonials are also a great way to ensure the quality of services provided by a well-reputed company.
Experience and reputation for a penetration testing company do not necessarily need to go hand in hand as some companies with lesser experience may provide better services and customer care than their far more experienced counterparts. This means that they will have a better reputation than experienced companies.
4. Skillset
What are the skillsets and qualifications of the pentesters in the companies you have narrowed down? Having the right qualifications points to having the right knowledge for carrying out pentests specific to one’s requirements. Are their qualifications and certifications up to date on the most relevant forms of skills required in the field currently?
These are a few of the factors to consider when opting for a 3rd party penetration testing service provider for your needs.
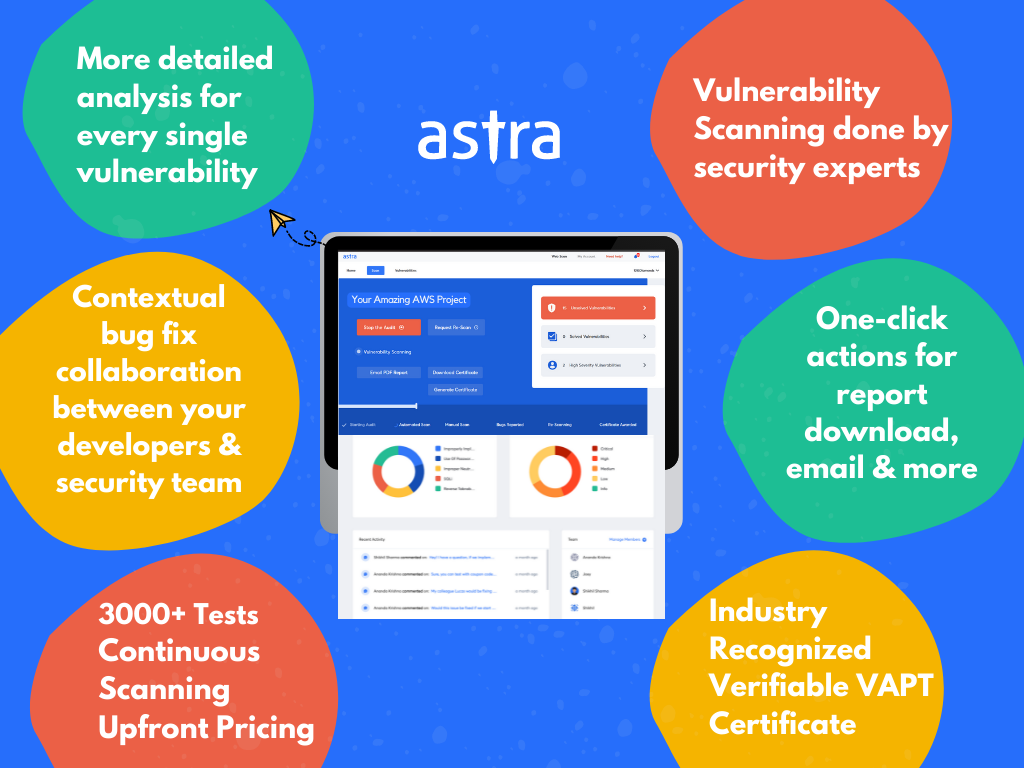
Best Third-Party Penetration Testing Provider: Astra Security
Astra Security is one of the leading VAPT platforms that also caters to the need for external penetration testing that is budget-friendly and easily customizable. Its automated penetration testing tool- Astra Pentest, comes with the perfect combination of automated and manual pentesting along with some incredible features. They include:
- Comprehensive Scanner: Having a comprehensive scanner capable of detecting vulnerabilities based on known CVEs, OWASP Top 10, and SANs 25. The comprehensive scanning tool does this by carrying out more than 3000 tests to find out any and every flaw within the security system.
- Zero False Positives: Astra Pentest ensures zero false positives by vetting out every vulnerability found. This vetting is done by expert pentesters thus ensuring its accuracy.
- Detection Skills: Astra’s pentest can carry scans behind logins and is also capable of finding business logic errors. Not many pentesting tools are capable of detecting such issues due to their organic nature.
- Intuitive Dashboard: Astra Pentest’s dashboard is CXO-friendly and displays all the vulnerabilities found on the dashboard. It is also interactive since the customers can communicate and clarify any doubts about each vulnerability by commenting on any vulnerability.
- 24*7 Customer Care: Astra boasts genuine and capable customer service that is available 24*7. This can be carried out via mail or even through calls if deemed necessary.
- Compliance: Astra helps its customers achieve and maintain compliance with specific regulatory standards by carrying out compliance-specific checks for them. With this option, customers can choose the compliance they want to check for and areas of non-compliance will be shown in detail in a compliance-specific dashboard.
- Detailed Reports: Astra provides its customers with intricately detailed reports which talk about the exploits carried out, the vulnerabilities found the damage inflicted by them, their CVSS scores, and possible measures for fixing them. Customers are also provided with POC videos to make such remediations easier.
- Verifiable Certificate: Once a pentesting process including the rescanning is complete, Astra provides its customers with a publicly verifiable certificate that provides assurance of the quality of one’s security measures in place. Such a certificate can boost sales and the trust within the existing and potential clients of pentesting customers.
- Rescans And Gap Analysis: Rescanning is an option offered after the completion of vulnerability patching to ensure that the new fixes have no further flaws in them. While gap-analysis is carried out initially before deciding on any tests to find out the possible gaps in the security system to decide the further steps.
With these epic qualities, it is truly understandable why Astra Pentest outshines the other pen test providers available out there.
Conclusion
Third-party penetration testing is a boon for all companies, it saves on cost and ensures a thorough assessment of security for every nook and cranny of your organization. It helps with compliance, and vendor certifications, both of which help attract clients like bees to nectar. So secure your organization today and find those nearly impossible-to-find vulnerabilities using Astra Pentest, your trust VAPT service provider.
FAQs
What are the three penetration testing methodologies?
The three main penetration testing methodologies are Black-Box, White-Box, and Gray-Box.
What is an internal pentest?
An internal pentest is when penetration testing is carried out by members within an organization or to meet the need and requirements within the organization.
What is an external pentest?
An external pentest is carried out remotely by professionals who are hired professionally to rake out the vulnerabilities within a security system if any have been missed during an internal pentest.
















