A firewall is a network security system that prevents unauthorized access to or from a private network. A firewall isn’t enough if you have a properly secure network, and all the sensitive data you have needs to be secure.
Firewall penetration testing is part of a larger strategy that aims to ensure that the corporate network is protected and secure at all times. With the rise in the number of cyber-attacks on the corporate network, it has become clear that a firewall penetration test is essential.
This blog will help you understand why firewall penetration testing is essential to your security strategy.
What is a Firewall Penetration Testing?
A firewall penetration test assesses how well a firewall protects an organization’s network from unauthorized access. It is a form of security testing used to evaluate a firewall’s effectiveness in blocking unauthorized traffic.
The test is conducted by attempting to access the network from an external location using various methods, such as port scanning and packet sniffing. If the firewall is effective, the tester should not be able to gain access to the network.
Firewall penetration tests can be conducted manually or with the help of automated tools. Manual testing is more time consuming and requires more significant expertise, but it can be more thorough.
Automated tools can be less expensive and can be used to test a more substantial number of targets.
Why Conduct Firewall Penetration Testing?
A firewall penetration test is a critical tool for security teams to identify vulnerabilities and assess the risk of an attack. A firewall test lets you map out your network from the outside to identify potential vulnerabilities in your network architecture.
Knowing where traffic enters and exits your network is essential because it can help you identify any weaknesses in your network architecture that might allow an attacker to gain access.
For example, if you have a wireless Access Point (AP) accessible through the Internet, you need to know where this traffic enters and exits your network.
Types of Firewall Penetration Testing
Firewall penetration testing is of further different types; let’s understand each one of them in detail:
- Man in the Middle (MiTM): In a MiTM test, a security researcher tries to intercept and modify traffic between the firewall and the clients trying to connect to the network. This test is often used against remote users because it could allow attackers to hijack traffic and get into the network without being detected. The attacker would then fully access the remote users and their data.
- Direct Traffic: In a direct traffic test, a security researcher is “directly” connecting to web servers and application servers on the internal network. The attacker would then try to map out the internal network, identify any vulnerabilities and potentially access sensitive data. This is often used against internal employees and is similar to an “internal reconnaissance” test.
- Spoofed Traffic: In a spoofed traffic test, the attacker uses a tool to send a fake, or “spoofed,” source of network traffic that simulates a remote user trying to connect to the internal network. The attacker has full access to the internal network once connected, similar to an “internal reconnaissance” test.
Also Read: API Penetration Testing: What You Need to Know | Continuous Penetration Testing: The Best Tool You’ll Find
3 Ways to Perform Firewall Penetration Testing
There are three primary ways to perform firewall penetration testing:
1. Black Box Testing: In black box testing, the tester has no prior knowledge of the firewall system and tests the system from the outside.
2. White Box Testing: In white box testing, the tester has complete knowledge of the firewall system and tests the system from the inside.
3. Gray Box Testing: In gray box testing, the tester has some prior knowledge of the firewall system and tests the system from the outside.
All three types of firewall penetration testing are essential to identify weaknesses in a system. By performing all three testing types, a comprehensive system analysis can be conducted, and potential vulnerabilities can be identified and addressed.
What to Consider Before Conducting Firewall Penetration Testing?
There are a few key factors to consider when deciding whether or not to conduct a firewall penetration test. First, you need to assess the risks posed to your organization’s network and determine if the benefits of testing outweigh the risks.
Second, you need to consider the resources required to conduct the test. And lastly, you need to have a clear understanding of the objectives and goals of the test.
If you decide that a firewall penetration test is right for your organization, there are a few things you need to do to prepare. First, you need to identify the stakeholders involved in the test.
Second, you need to create a test plan that outlines the test’s objectives, scope, and approach. And lastly, you need to identify the resources that will be required to conduct the test.
Firewall Penetration Testing Methodology
To perform a firewall penetration test, four key steps need to be followed:
1. Mapping Out Your Network: In the mapping out your network step, the security researcher attempts to “map out” your network from outside. This means that the researcher will try to identify the network devices available.
2. Connecting to Internal Services: During this stage, the pentester tries to connect to internal services such as databases, web servers, and file shares. The pentester would try to access these services using the fake source of network traffic generated while mapping out your network step or any possible way.
3. Identifying Vulnerabilities: Next, the team would try to identify any vulnerabilities in mapping out your network step. The penetration tester then tries to “exploit” these vulnerabilities to gain access to sensitive data.
4. Accessing Internal Devices: The final step is to access internal devices such as computers, servers, and portable devices. An attacker would then try to “hop” from device to device to identify any vulnerabilities that would give them access to sensitive data.
Firewall penetration testing can be risky, so it is essential to ensure that all security controls are in place before starting the test. Additionally, it is necessary to have a clear understanding of the risks involved and a plan to mitigate those risks.
Astra: Go To Solution For Firewall Penetration Testing
Astra provides the most comprehensive firewall penetration testing service, helping you identify and fix potential security vulnerabilities in your firewall configuration. With Astra’s easy-to-use web-based interface, you can quickly and easily test your firewall’s security and receive detailed reports of any vulnerabilities.
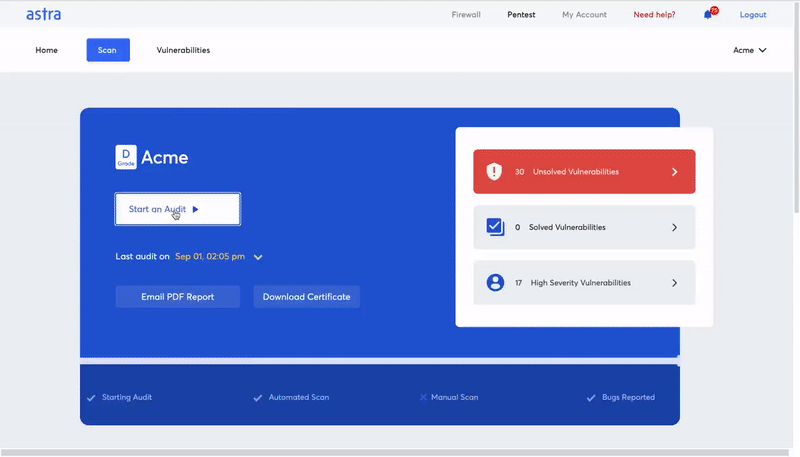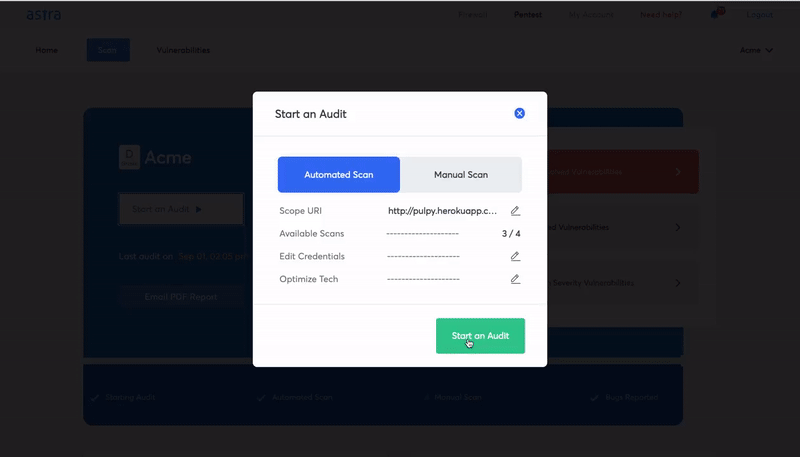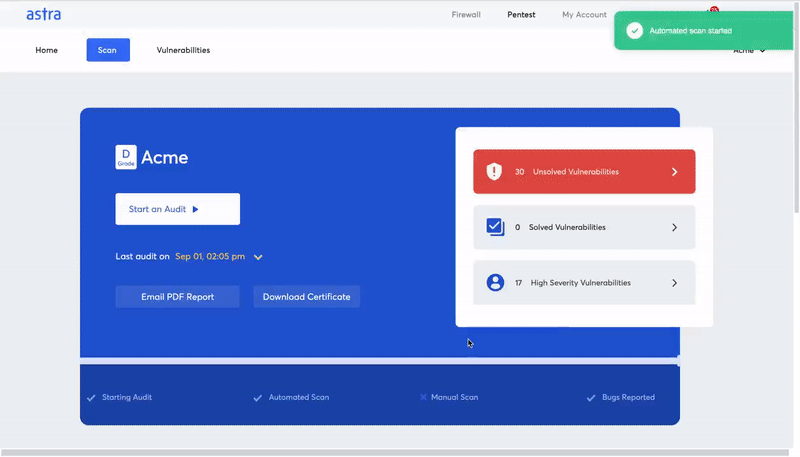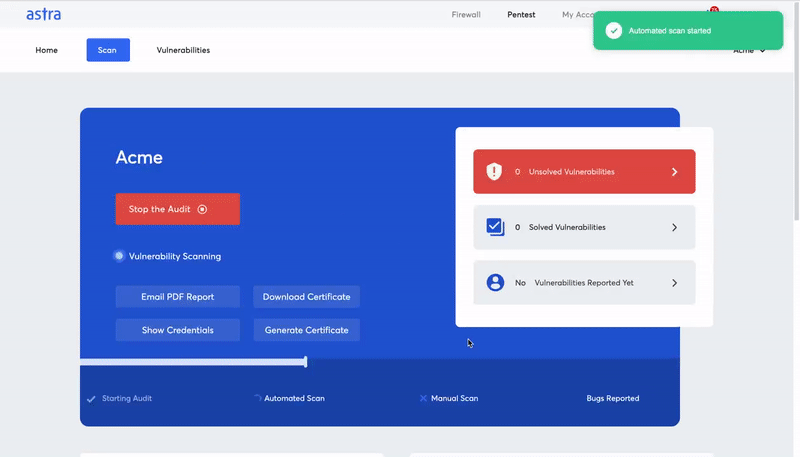
Some key features offered by Astra’s pentest platform include
- CI/CD integration
- Contextual collaboration
- Continuous pentesting
- Detailed remediation guidelines
- Video PoCs to help you reproduce issues.
Astra’s firewall testing solution is trusted by leading organizations worldwide and is the perfect tool for ensuring the security of your network. Our firewall testing methodology is based on years of experience and is constantly updated to ensure that it can find and exploit the latest vulnerabilities.
Conclusion
A firewall penetration test is critical for any organization’s security team. These tests can help security teams identify vulnerabilities in their network architecture and map out potential attack points. Given the ever-changing landscape of cybersecurity threats, it is imperative that you conduct a firewall penetration test to ensure your network is as secure as possible from outside threats.
FAQs
What is the cost of firewall penetration testing?
The cost of penetration testing firewalls is between $200 to $400 per month.
How often should I conduct penetration testing?
It is ideal to have quarterly penetration tests to tap into your organization’s security health.
















