VAPT is the process of finding and exploiting all possible vulnerabilities in your infrastructure, with the primary goal of mitigating them. VAPT is done by security experts who are experts in offensive exploitation. Simply put, VAPT is a proactive “hacking” activity in which you hack your infrastructure before hackers come looking for loopholes.
Conducted by security experts from external companies under a VAPT (Vulnerability Assessment & Penetration Testing), these security professionals leverage their expertise to mimic hacker tactics, uncover critical security gaps, and collaborate with you to implement effective remediation strategies.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a methodological approach to improving an organization’s security posture by identifying, prioritizing, and mitigating vulnerabilities in its infrastructure. It also helps organizations stay compliant with various industry standards throughout the year.
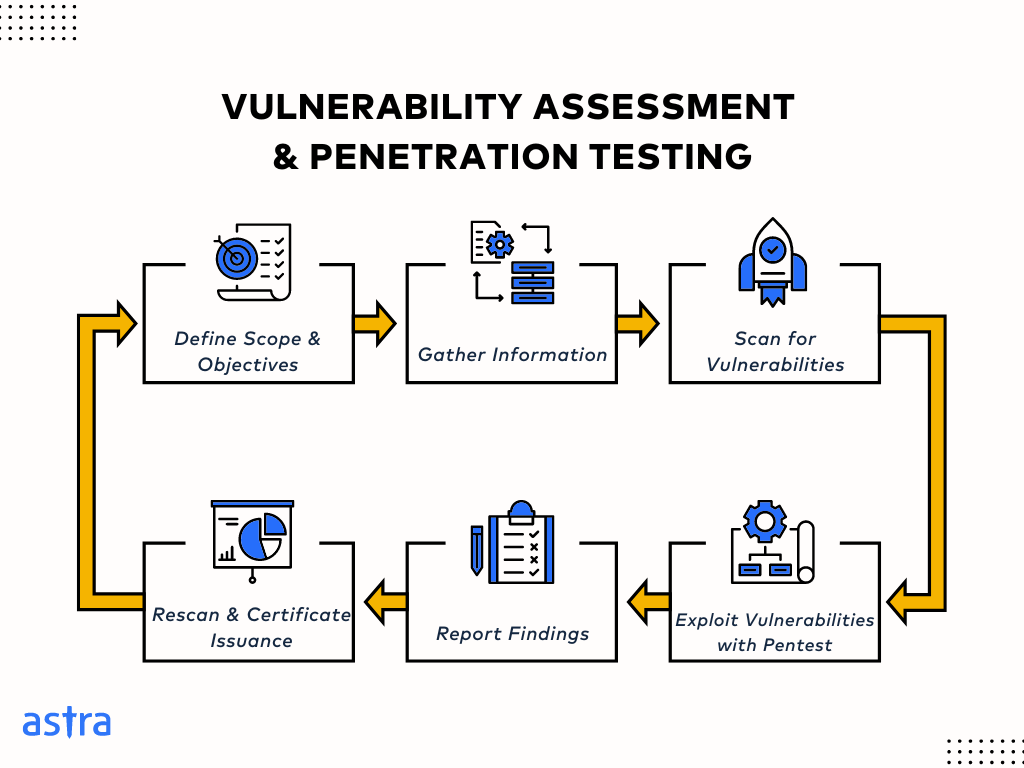
Within a VAPT, the VA (Vulnerability Assessment) leverages security engineers & a wide array of automated tools to identify potential vulnerabilities. VA is followed by a PT (Penetration Test), where a real-world attack is simulated to exploit the vulnerabilities found during the VA process.
In fact, did you know? According to a recent Surfshark report, India ranked fifth globally for data breaches in 2023, with 5.3 million leaked accounts.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Why Do You Need Vulnerability Assessment and Penetration Testing (VAPT)?
Leverage Comprehensive Evaluation:
By combining vulnerability assessments with pentests, VAPT offers a multifaceted approach as it not only pinpoints weaknesses in your systems but also simulates real-world attacks to determine viability, impact, and attack vectors stemming from the same.
Adopt a Security-First Approach:
Regular VAPT reports can be a powerful tool for improving SDLC security practices. By identifying vulnerabilities during the testing and staging phases, developers can address them before deployment. This helps you seamlessly shift from DevOps to DevSecOps to adopt a security-first approach.
Strengthen Your Security Posture:
Regularly scheduled VAPTs allow you to benchmark your security posture year-over-year. This enables you to track improvements, identify recurring weaknesses, and measure the effectiveness of your security investments.
Stay Complaint to Security Standards:
Many regulations and compliance standards require organizations to perform regular security testing. Regular vulnerability scans help ensure you meet these requirements, while pentest reports facilitate compliance audits for SOC2, ISO27001, CERT-IN, HIPAA, etc. compliances.
Build Trust with Stakeholders:
By proactively identifying and addressing vulnerabilities, a VAPT assessment demonstrates your commitment to data security to all stakeholders. This builds trust and confidence in your organization’s ability to protect sensitive information, especially for your customers and vendors.
What Does the VAPT Process Look Like?
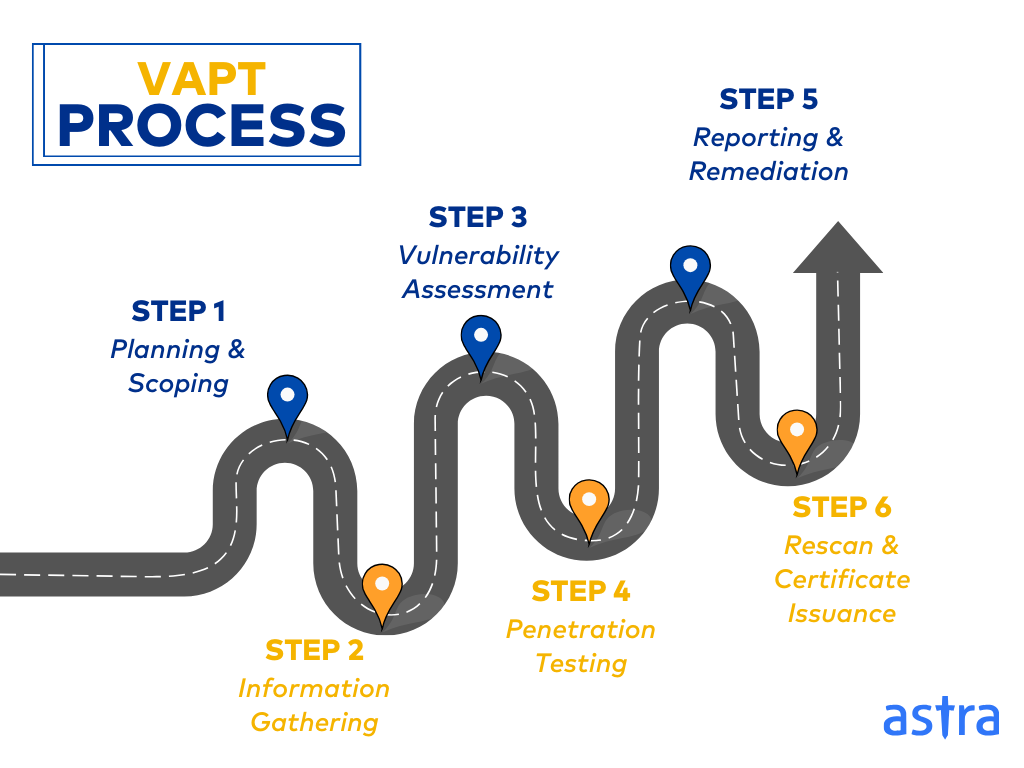
Step 1: Planning & Scoping:
This stage defines the VAPT’s goals, objectives, and boundaries. It involves identifying critical assets to be tested, determining the testing methodology and compliance prioritizations, and outlining communication protocols with your VAPT testing provider.
Step 2:Information Gathering:
In this stage, the team gathers information about the target systems, network architecture, and potential vulnerabilities using publicly available data and authorized techniques. In the case of a grey box, they also gather information from you and start mapping your target systems.
Step 3: Vulnerability Assessment:
In this stage, the providers leverage mature scanners and automated tools to scan your systems for known vulnerabilities. This stage identifies potential weaknesses in software, configuration settings, and security protocols.
Step 4: Penetration Testing
Here, security professionals attempt to exploit identified vulnerabilities using hacking techniques. This stage simulates real-world attacks to assess the potential impact and effectiveness of your security controls.
Step 5: Reporting & Remediation:
Post exploitation, they deliver a comprehensive report detailing the vulnerabilities identified, the exploitation attempts made, and recommendations for remediation. This stage also involves creating a plan to address the vulnerabilities and strengthen your overall security posture.
Step 6: Rescan and Certificate Issuance:
Once the vulnerabilities have been patched, some penetration testing companies sometimes offer rescans to verify the above, generate clean reports, and issue publicly verifiable pentest certificates that facilitate compliance audits.
How Does Vulnerability Assessment Differ From Penetration Testing?
| Features | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Goal | Identify potential vulnerabilities, CVEs and attack paths | Exploit vulnerabilities to assess real-world impact |
| Methodology | Automated scans with mature vulnerability scanners, doxing & relevant reconnaissance | Manual offensive attack simulation done by security professionals |
| Depth & Scope | Surface-level scans for attack scenarios, documented CVEs etc. | In-depth exploration to uncover zero-days, business logic vulnerabilities, and attack vectors |
| Regression Tests | Automate and trigger scans after every update in staging or production environments | It is not possible for every update due to the depth of analysis |
| Time Taken | 24-72 hours depending on the scope | 10-15 business days |
| Frequency | Can be conducted regularly (weekly, monthly) | Typically conducted less frequently (quarterly, bi-annually, annually) |
| Price Range | $199 to $4500 annually | $2500 to $50,000 per Pentest |
| Compliance | It is not essential, but it can help prepare for compliance | Necessary for most compliance standards |
What Are The 6 Significant Types of VAPT?
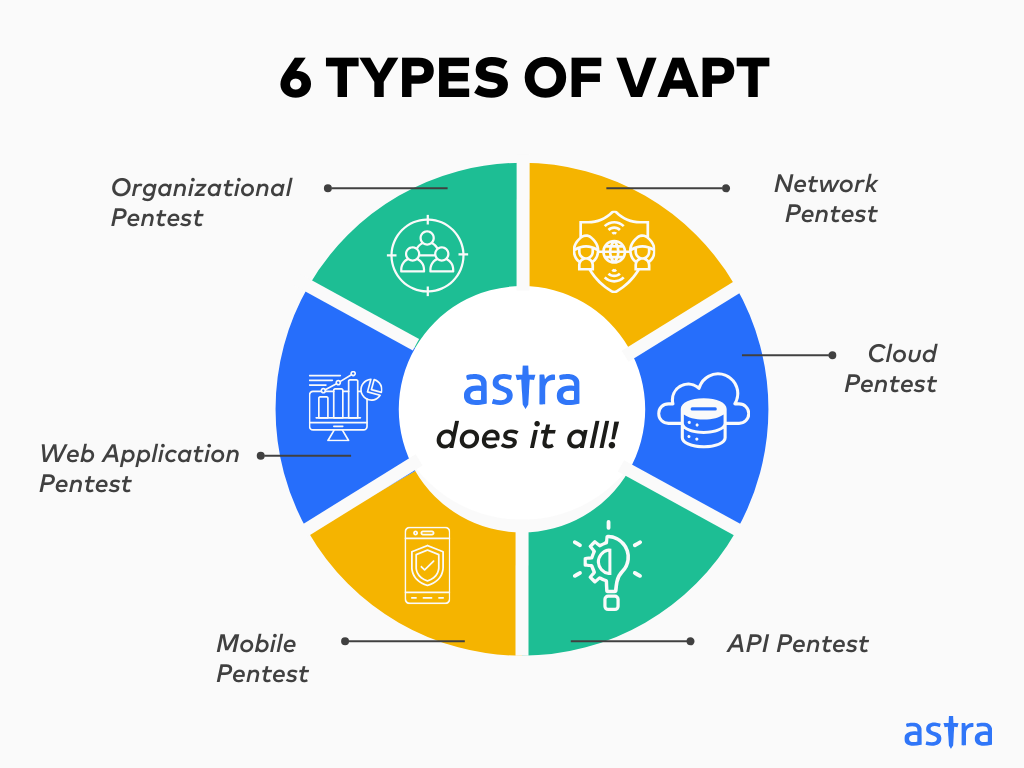
1. Organizational Penetration Testing
Organization penetration testing is a holistic assessment that simulates real-world attacks on an organization’s IT infrastructure, including cloud, APIs, networks, web and mobile applications, and physical security.
Pen testers typically employ a multi-pronged approach, leveraging vulnerability assessments, social engineering techniques, and exploit kits to identify vulnerabilities and related attack vectors.
2. Network Penetration Testing
Network penetration testing employs ethical hacking methodologies to meticulously probe your network defenses for exploitable data storage and transfer vulnerabilities. Standard techniques include scanning, exploitation, fuzzing, and privilege escalation.
Adopting a phased approach, penetration testing experts map the network architecture, identify systems and services, and then leverage various automated tools and manual techniques to gain unauthorized access, mimicking real-world attacker behavior.
3. Web Application Penetration Testing
Web app pentests leverage manual and automated tools to probe for weaknesses in authentication, authorization, input validation, and business logic.
Expert pentesters attempt to inject malicious code (e.g., SQL injection, XSS), manipulate sessions, and exploit logic flaws to help you identify, prioritize, and mitigate risks before attackers exploit them.
4. Mobile Penetration Testing
Mobile penetration testing utilizes static and dynamic analysis to uncover vulnerabilities in a mobile application’s code, APIs, and data storage, helping you strengthen your security posture.
Often, pentesters focus on areas such as insecure data storage (cleartext passwords), intercept sensitive data in transit, exploit business logic vulnerabilities, and flaws in inter-app communication or API integrations, among others, to identify CVEs and zero days.
5. API Penetration Testing
API vulnerability assessment and penetration testing mimic real-world attacks by meticulously crafting requests to uncover vulnerabilities such as broken authentication, Injection flaws, IDOR, and authorization weaknesses.
Pentesters may also use automated tools like Postman to automate attacks, manipulate data packets (fuzzing), and identify exploitable business logic vulnerabilities, such as payment gateway manipulation.
6. Cloud Penetration Testing
Cloud pentests and VAPT audits aim to assess vulnerabilities in your cloud configurations, APIs, storage mechanisms, and access controls.
It leverages a combination of automated tools and manual testing to probe for zero-days and cloud-based CVEs using various techniques. These often include SAST, DAST, API fuzzing, serverless function exploitation, IAM, and cloud configuration techniques.
What are VAPT Tools?
1. Astra Pentest: The Complete VAPT Suite
Key Features:
- Platform: Online
- Pentest Capability: Continuous automated scans with manual tests
- Accuracy: Zero false positives
- Compliance: PCI-DSS, HIPAA, SOC2, and ISO27001
- Expert Remediation: Yes
- Integration: Slack, Jira, GitHub, GitLab, Jenkins, and more
- Price: Starting at $1999/yr
Astra’s VAPT Suite integrates the powerful, AI-driven Astra vulnerability scanner with expert manual penetration testing, ensuring compliance with industry benchmarks like OWASP TOP 10 and SANS 25.
With a portfolio of 9,300+ tests, vetted scans help guarantee zero false positives. In-depth pentests and custom AI test cases help identify unique attack vectors and business logic vulnerabilities, such as user privilege escalation.
Lastly, the scan-behind-logins, seamless integrations with your CI/CD pipeline, custom resorts for CXOs and developers, and Astra’s publicly verifiable security certificate make it the best VAPT Suite for your business.
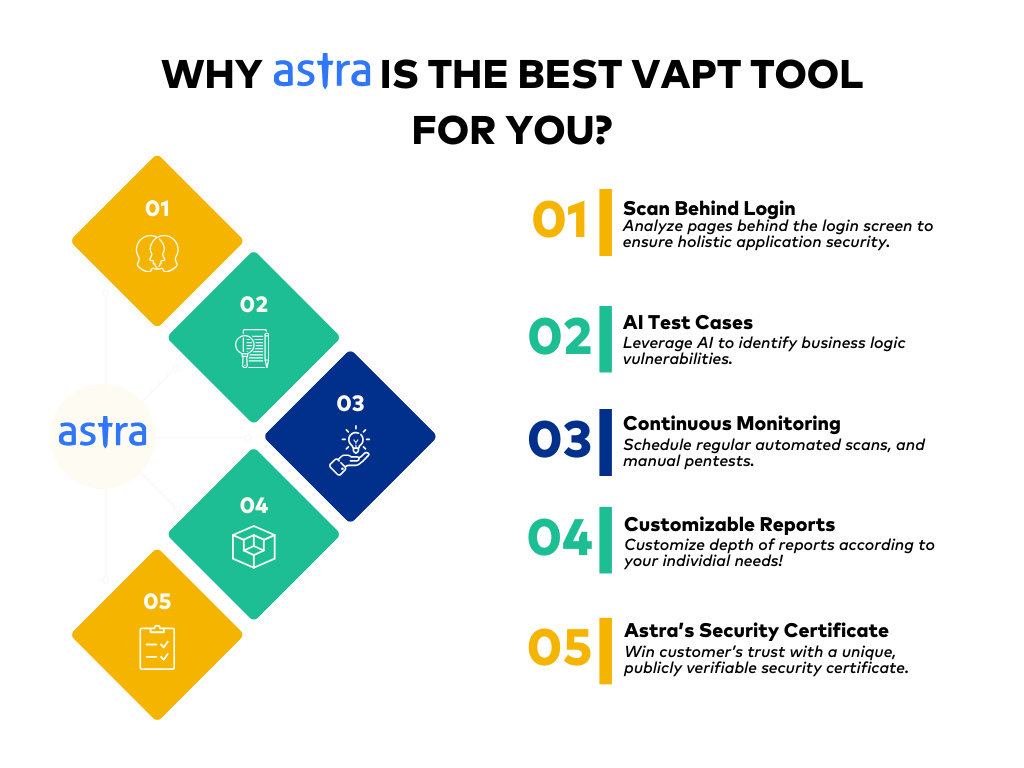
Pros:
- Seamlessly integrate with your CI/CD pipeline
- Continuously scan for vulnerabilities with regularly updated scanner rules
- Collaborate with security experts with OSCP, CEH & CVEs under their name
- Quick turnaround with GPT-powered chatbot
- Generate custom executive and developer-friendly reports
Limitations:
- Only 1-week free trial is available
Open Source VAPT Tools
2. ZAP
Key Features:
- Target: Web applications
- Pentest Capabilities: Automated and manual pentests
- Deployment Capabilities: Manual installation from source code pre-built packages and Docker
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: OWASP Top 10
ZAP (Zed Attack Proxy) is a feature-rich open-source VAPT security tool specifically designed for web application penetration testing. It facilitates a comprehensive approach to security assessments through session manipulation, traffic analysis, and fuzzing.
It operates as a Man-in-the-Middle (MITM) proxy, enabling security analysts to intercept, inspect, and even manipulate HTTP(S) traffic flowing between a web browser and the target web application.
Pros:
- Intuitive user interface with a gentle learning curve
- Identifies vulnerabilities based on OWASP Top 10
Limitations:
- Some advanced functionalities require plugin installation
- False positives possible
3. Kali Linux
Key Features:
- Target: Online and physical systems, applications, and networks
- Pentest Capabilities: Unlimited Scans for vulnerability scanning, exploitation, privilege escalation, and post-exploitation
- Deployment Capabilities: Installer packages for live boot and disk installation
- Accuracy: False positives are possible
- Price: Open-source OS
Kali Linux is a Debian-derived distribution specifically designed for penetration testing and security auditing. With a pre-installed arsenal of 600+ security tools, it empowers security professionals to tackle VAPT engagements throughout the penetration testing lifecycle.
Moreover, the operating system offers granular control over its pre-installed tools, allowing security professionals to tailor their testing environment to specific needs and engagements.
Pros:
- Extensive user forums and knowledge base
- Low-latency execution with regular updates to maintain optimal performance
Limitations:
- Requires proficiency in the Linux commands
- May require a more gradual learning approach
4. NMAP
Key Features:
- Target: Network infrastructure, IoT devices, limited cloud instances
- Pentest Capabilities: Unlimited scans for network discovery, vulnerability scanning, service identification, and OS fingerprinting
- Deployment Capabilities: Flexible deployment through the command line, scripting, and graphical interfaces
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Network VAPT
Nmap is a ubiquitous open-source network discovery and vulnerability assessment tool. It empowers security professionals to efficiently map network infrastructure, pinpoint potential attack surfaces, and identify running services on connected devices.
Using a combination of techniques, Nmap conducts efficient and insightful network scans using port scanning, version detection, and NSE scripting.
Pros:
- Multi-faceted penetration testing platform
- Offers a robust automation framework
Limitations:
- Aggressive scanning techniques can be very intrusive at times
- False positives possible
5. Wireshark
Key Features:
- Target: Network
- Pentest Capabilities: Vulnerability detection, deep packet inspection, and traffic analysis
- Deployment Capabilities: Installer packages for traditional and portable versions
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Network traffic-centered VAPT
While Wireshark is primarily known as a network packet analyzer, its versatility extends to VAPT, particularly for internal penetration testing.
Wireshark’s ability to capture and dissect real-time and historical network traffic in granular detail empowers security analysts to reconstruct attack timelines, identify attack vectors, and develop more robust defenses through attacker behavior analysis.
Pros:
- Conducts real-time and retrospective analysis
- Provides a comprehensive set of pre-defined filters for tailored analysis
Limitations:
- Large database queries can lead to slower response times
- Cannot perform packet injection
How to Choose The Best VAPT Provider for You?
Understand Your Needs
Before exploring provider options, assess your organization’s specific needs. Consider factors such as the size and complexity of your IT infrastructure, industry regulations you comply with, budget, timeline, and the desired scope of the VAPT.
Seek Methodological Depth:
Look for VAPT providers who leverage established methodologies such as the OWASP Testing Guide (OTG) or PTES (Penetration Testing Execution Standard) to ensure a comprehensive assessment.
Inquire about their testing methodologies and how they tailor them to your unique needs.
Prioritize Transparent Communication:
Since a VAPT can take 10-15 business days, choose a provider that fosters open and transparent communication throughout the VAPT process.
They should provide you with regular progress updates, clear explanations of findings, and a collaborative remediation approach to minimize bottlenecks and maximize the VAPT cycle’s efficacy.
Look Beyond Cost:
While cost is an essential factor, look for VAPT providers that offer value and ROI beyond the initial assessment. Evaluate the depth of reports, customization metrics (if any), post-assessment support, remediation guidance, and retesting options.
Prioritize those with a proven track record in VAPT, specifically in your industry and asset types. Certifications such as OSCP and 3+ years of experience in pentesting your specific type of application can also be helpful.
Final Thoughts
With the current stage of cybercrime, the question is no longer whether to engage in a VAPT but rather which VAPT is best for you.
Beyond fortifying your security posture, a comprehensive VAPT with continuous scanning helps cultivate a security-first approach, stay compliant throughout the year, and strengthen customer trust.
Lastly, while the above VAPT tools list is far from exhaustive, choose a provider who goes beyond the basics. Evaluate their scanning capabilities, methodologies, VAPT experience within your specific industry, and the expertise of their team.
A VAPT can be a significant investment, but the ROI is definitely worth it!
FAQs
1. What is the difference between VAPT and Pentest?
VAPT (Vulnerability Assessment and Penetration Testing) combines vulnerability scanning with manual pentesting, offering a more comprehensive security evaluation. Pentesting focuses solely on simulating attacks to exploit vulnerabilities.
2. How much does a VAPT cost?
The cost of VAPT usually ranges between $500 and $50,000+. Pricing often varies based on different VAPT companies, the services provided, the depth of analysis, and your requirements.
















