Vulnerability Assessment and Penetration Test (VAPT) has become a business no-brainer activity. Over the years, organizations have evolved from conducting an annual VAPT to continuous VAPT, which is in sync with the code push cycles.
If you are a security engineer trying to automate daily work using VAPT Tools or a company looking for more continuous pentests via PTaaS, having an effective arsenal of VAPT tools helps ensure the highest security standards. Here are the top 11 VAPT tools handpicked by our security analysts.
11 Best VAPT Tools of All Time
Features to Consider When Choosing a VAPT Tool
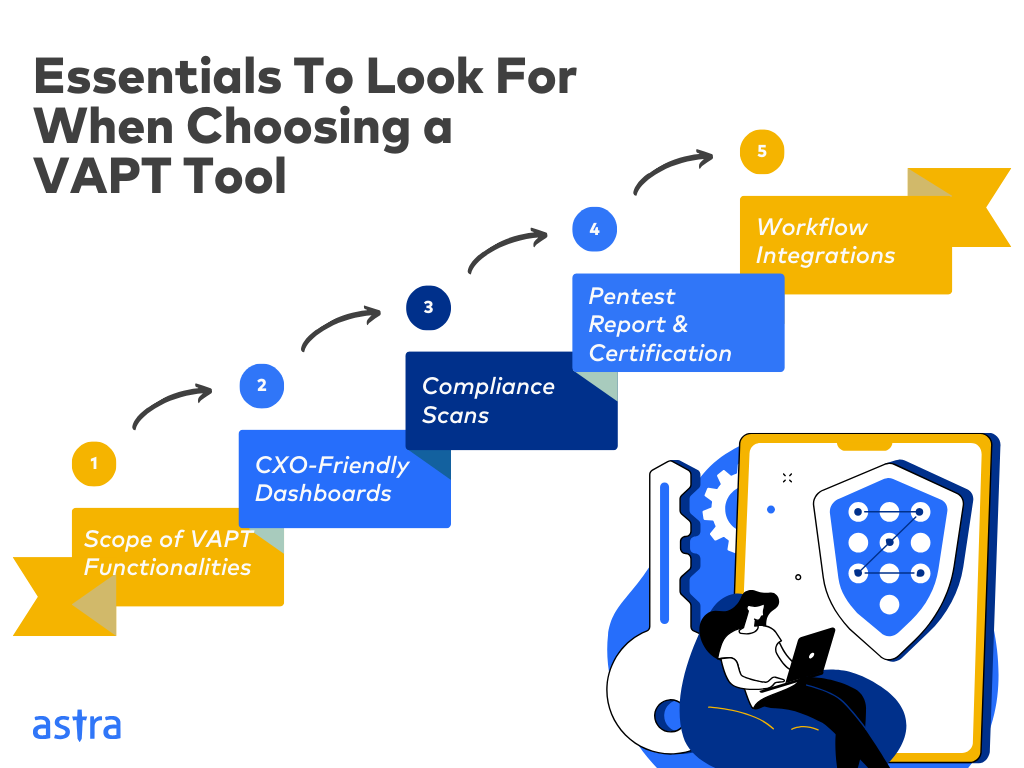
1. Scope of VAPT Functionalities:
As an enterprise, focus on the breadth of functionalities a VAPT tool offers. Prioritize tools that automate vulnerability scanning across diverse assets (web, APIs network, mobile) and offer vulnerability management features like scheduling, assigning, and tracking pentests across various stages.
On the other hand, as an analyst, focus on the depth. Prioritize individual tools based on their strengths against specific asset types and ease of use for particular tasks.
2. CXO-Friendly Dashboards:
While firms prioritize VAPT testing tools that offer CXO-friendly dashboards with real-time updates on pentest progress, key vulnerability reports, and overall infrastructure health. This empowers executives to make informed decisions.
An in-depth pentest, vulnerability scanner with wide coverage, intuitive interface, customizable views, and an active customer success team are more important to a security analyst.
3. Compliance Scans:
As a business or a security analyst, look for VAPT tools that adhere to various common industry compliance standards (CERT-IN, CREST, PCI-DSS, etc.) with compliance-focused scans and reporting aligned with the specific regulation guidelines.
This helps you improve your security posture, stay compliant throughout the year, and avoid hefty fines associated with non-compliance with various mandatory standards.
4. Pentest Report and Certification:
Companies should prioritize tools that offer multi-tiered VAPT reporting. This means generating custom executive reports for management and exhaustive reports for developers. Moreover, publicly verifiable certificates showcasing a clean bill of health build trust with your customers.
As a security analyst, the focus shifts to the availability of actionable reports with in-depth vulnerability details, CVSS scores, and clear steps to replicate and patch vulnerabilities.
5. Workflow Integrations:
To help companies avoid communication bottlenecks, seamlessly integrating your VAPT tool with existing tools in your CI/CD pipelines, such as Slack, JIRA, GitHub, GitLab, and Jenkins, is non-negotiable.
On the other hand, while endpoint mapping and robust authentication are essential for security analysts, the tool’s primary focus remains its core functionality: identifying vulnerabilities.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

11 Best VAPT Tools of 2024
Top 3 VAPT Tools for Enterprises:
| Features | Astra | Burp Suite | Intruder |
|---|---|---|---|
| Platform | SaaS | Windows, MacOS, Linux | SaaS |
| Pentest Capabilities | Continuous automated scans with 9300+ tests & manual tests | Automated scans for web apps | Mature scanner for web apps and cloud |
| Accuracy | Zero false positives | False positives possible | False positives possible |
| Compliance | PCI-DSS, HIPAA, GDPR, ISO, PCI-DSS & SOC2 | PCI-DSS, OWASP Top 10, HIPAA, and GDPR | SOC2, and ISO 27001 |
| Expert Remediation Assistance | Yes | No | No |
| Workflow Integrations | Slack, JIRA, GitHub, GitLab, Jenkins, and more | Slack, JIRA, Jenkins, GitLab, and more | GitHub, JIRA, Atlassian, and more |
| Pricing | Starting at $1999/yr | $449/yr/user | Starts at $1958/ year |
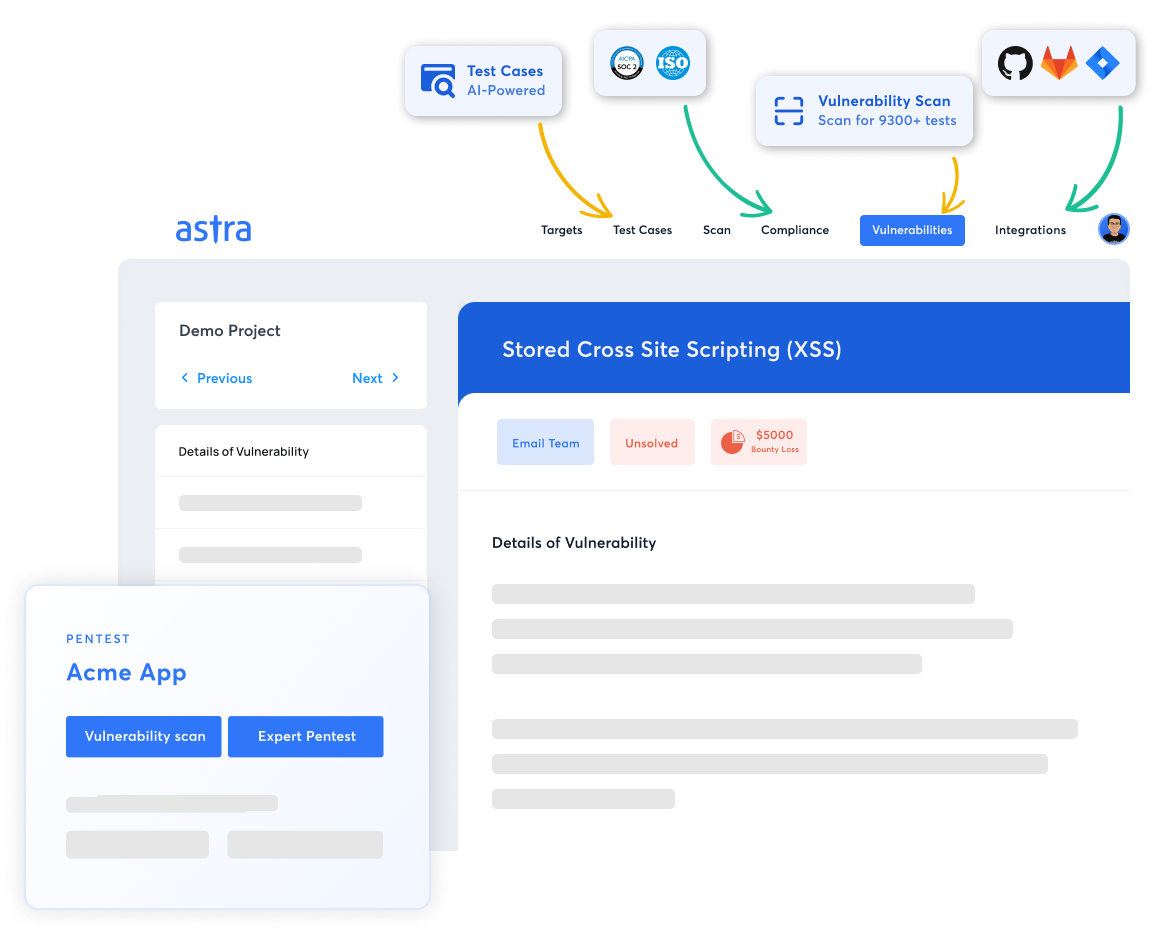
1. Astra Pentest
Key Features:
- Platform: SaaS
- Pentest Capabilities: Continuous automated scans with manual tests
- Accuracy: Zero false positives
- Compliance Scanning: PCI-DSS, HIPAA, ISO27001, and SOC2
- Expert Remediation Assistance: Yes
- Workflow Integration: Slack, JIRA, GitHub, GitLab, Jenkins, and more
- Price: Starting at $1999/yr
- Best Suited For: Holistic VAPT across assets
The Astra Pentest Platform is a comprehensive VAPT tool that combines the automated vulnerability scanner with AI and manual pentesting capabilities in compliance with various industry standards, including OWASP TOP 10 and SANS 25.
Moreover, our expert-vetted scans ensure zero false positives, and in-depth hacker-style manual penetration tests reveal critical vulnerabilities, such as payment gateway hacks and business logic errors.
Thus, with a portfolio of 9,300+ automated tests and customers across continents, Astra’s Scanner empowers enterprises and security analysts to achieve their security goals.
Pros:
- Seamlessly integrate with your CI/CD pipeline
- Continuously scan for vulnerabilities with regularly updated scanner rules
- Collaborate with security experts with OSCP, CEH & CVEs under their name
- Quick turnaround with GPT-powered chatbot
- Generate custom executive and developer-friendly reports
Limitations:
- Only 1-week free trial is available
2. Burp Suite
Key Features:
- Platform: Windows, macOS, Linux
- Pentest Capabilities: Automated and manual scans for web apps
- Accuracy: False positives possible
- Compliance Scanning: PCI-DSS, OWASP Top 10, HIPAA, and GDPR
- Expert Remediation Assistance: No
- Workflow Integration: Slack, JIRA, Jenkins, GitLab, and more
- Price: $449/yr/user
- Best Suited For: Web app VAPT
Burp Suite is one of the few VAPT tools that offers a variety of manual and automated testing features to identify vulnerabilities. These include intercepting and manipulating web traffic, automating repetitive tasks, fuzzing, and brute-forcing logins.
It effectively detects many common vulnerabilities, including SQL injection, cross-site scripting (XSS), and insecure direct object references (IDORs).
Pros:
- Smooth integration with CI/CD Pipeline
- Offers automated and manual pentesting capabilities
Limitations:
- A few cases of app crashes and socket connection bugs have been reported
- Burp Crawler sometimes misses out on end-points
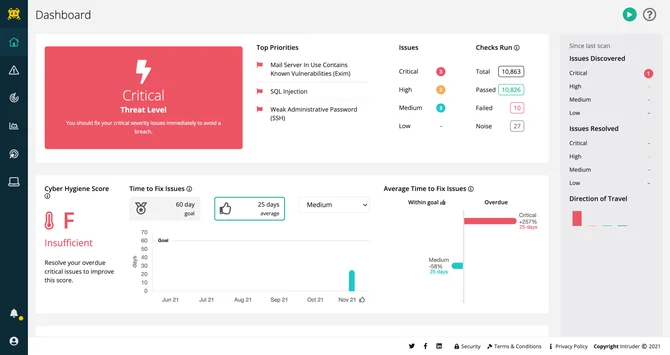
3. Intruder
Key Features:
- Platform: SaaS
- Pentest Capabilities: Websites, servers, and cloud.
- Accuracy: False positives present
- Compliance Scanning: SOC2, and ISO 27001
- Expert Remediation Assistance: No
- Workflow Integrations: GitHub, JIRA
- Cost: Starts at $1958/ year
- Best Suited For: Cloud pentesting
Going beyond traditional vulnerability scanning, Intruder, as a VAPT testing tool, offers a comprehensive VAPT platform designed primarily for web apps and clouds. Its mature scanner helps uncover critical security bugs before attackers can exploit them.
Renowned for their evidence-based formatting, their VAPT reports provide clear remediation steps to promote a proactive cyber risk education strategy.
Pros:
- Easy to deploy and manage alerts
- Designed to support scaling organizations
Limitations:
- The pricing is a bit steep
- Lacks zero false positive assurance.
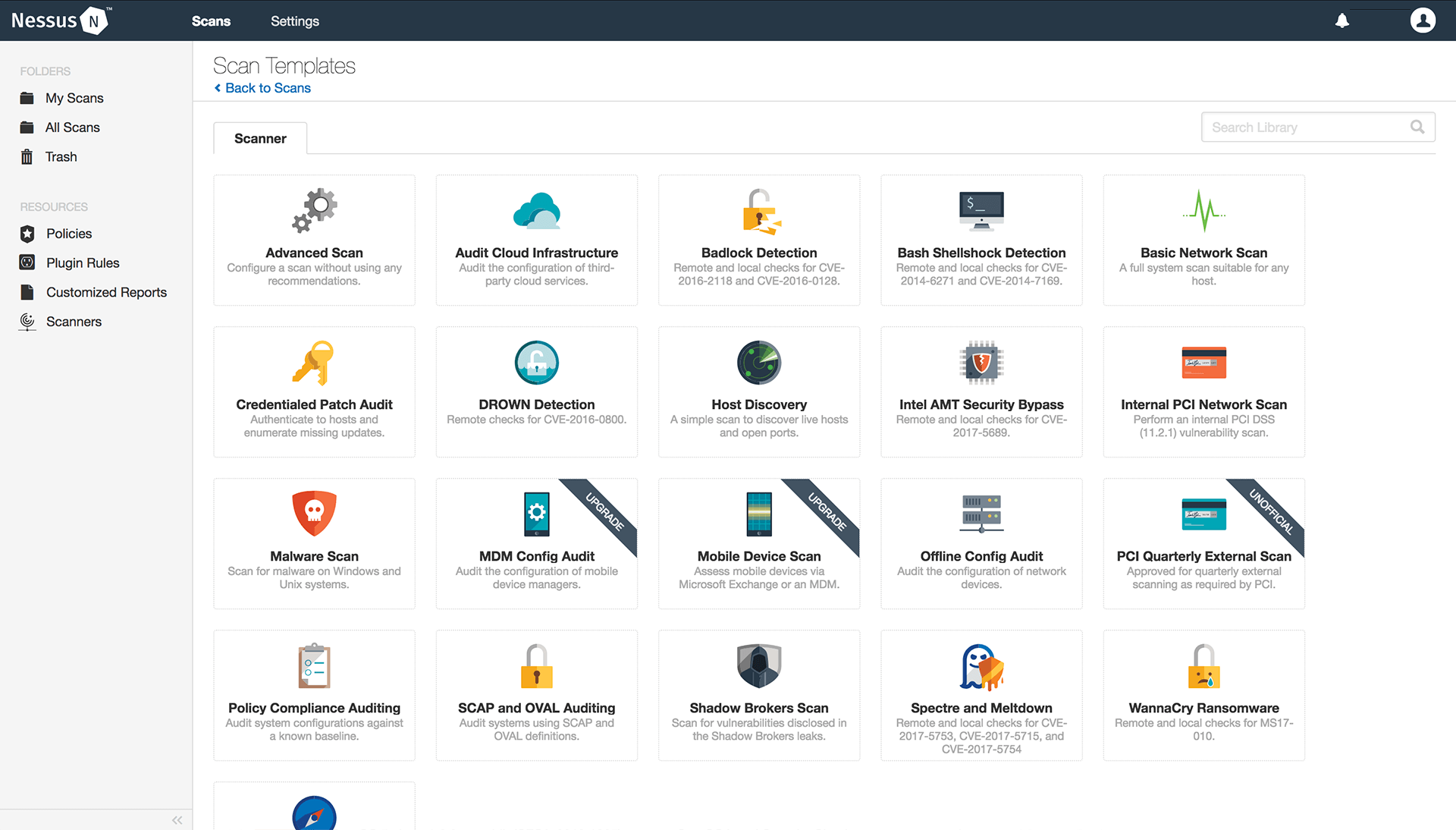
4. Nessus
Key Features:
- Platform: Windows, macOS
- Pentest Capabilities: Automated vulnerability scans for web apps, mobile & cloud
- Accuracy: False positives possible
- Compliance Scanning: HIPAA, ISO, NIST, and PCI-DSS
- Expert Remediation Assistance Available at extra cost
- Workflow Integration: IBM Security, Splunk, GitHub, and GitLab
- Price: Starting at $4,236/yr
- Best Suited For: Compliance VAPT across assets
Nessus is a powerful VAPT tool from Tenable that simplifies vulnerability identification and assessment across your enterprise’s digital infrastructure. Its extensive vulnerability database and robust automation features empower companies to streamline the testing process.
More importantly, it offers significant compliance support from ISO to GDPR to help organizations remain compliant throughout the year.
Pros:
- Offers a community version
- Significant automation capacity for scanning and reporting tasks
Limitations:
- Scanning timelines can be inconsistent
- Custom asset tags require separate automation
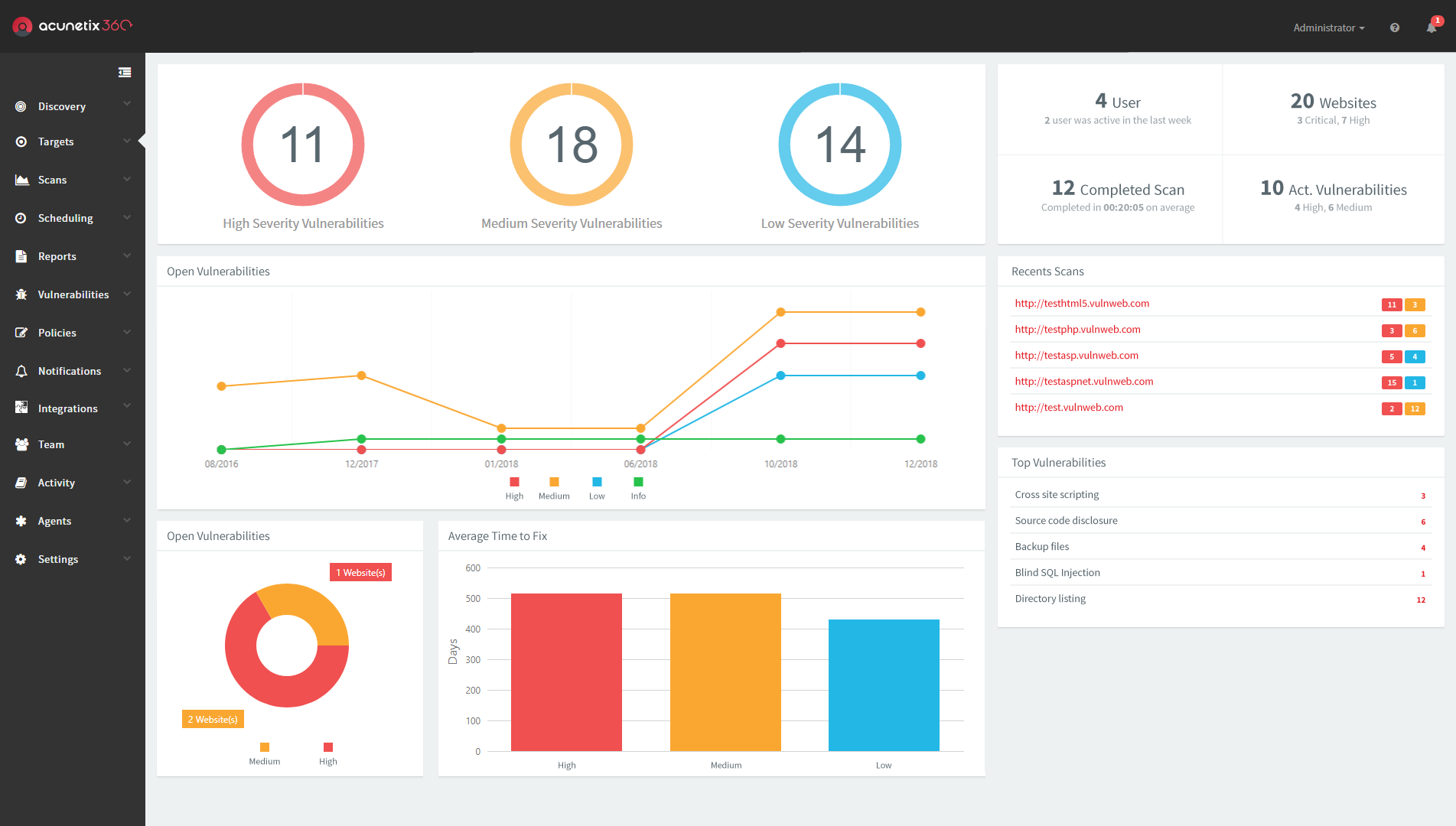
5. Acunetix
Key Features:
- Platform: Windows, macOS
- Pentest Capabilities: Continuous automated scanning for web applications
- Accuracy: False positives possible
- Compliance Scanning: OWASP, SOC2, NIST, HIPAA, and ISO 27001
- Expert Remediation Assistance: No
- Workflow Integration: GitHub, JIRA, and Atlassian
- Price: Available on quote
- Best Suited For: Automated VAPT
As a popular VAPT tool, Acunetix automates web vulnerability scanning and efficiently detects over 4,500 vulnerabilities, including SQL injection and XSS scripting variants. It seamlessly integrates with your firm’s IDEs, CI/CD pipelines, and GRC platforms, streamlining workflows.
Further, detailed scan reports by Accunetix empower developers with proof-of-concept examples and clear remediation guidance to address identified security risks swiftly.
Pros:
- Easy to optimize for various platforms
- Simple to navigate and learn
Limitations:
- Vulnerability PoCs can be complex for beginners
- Can generate false positives
Top 3 VAPT Tools for Security Analysts:
| Features | Astra | ZAP | Nmap |
|---|---|---|---|
| Target | Web apps, API, mobile, cloud, & network infrastructures | Web applications | Network infrastructure, IoT devices, limited cloud instances |
| Pentest Capabilities | Unlimited continuous automated scans with regular manual tests | Automated and manual pentests | Unlimited scans for network discovery, vulnerability scanning, service identification, and OS fingerprinting |
| Deployment Capabilities | SaaS/Cloud | Manual installation from source code pre-built packages and Docker | Flexible deployment through the command line, scripting, and graphical interface |
| Accuracy | Zero false positives | False positives are possible | False positives are possible |
| Price | Starting at $199/month | Open-source tool | Open-source tool |
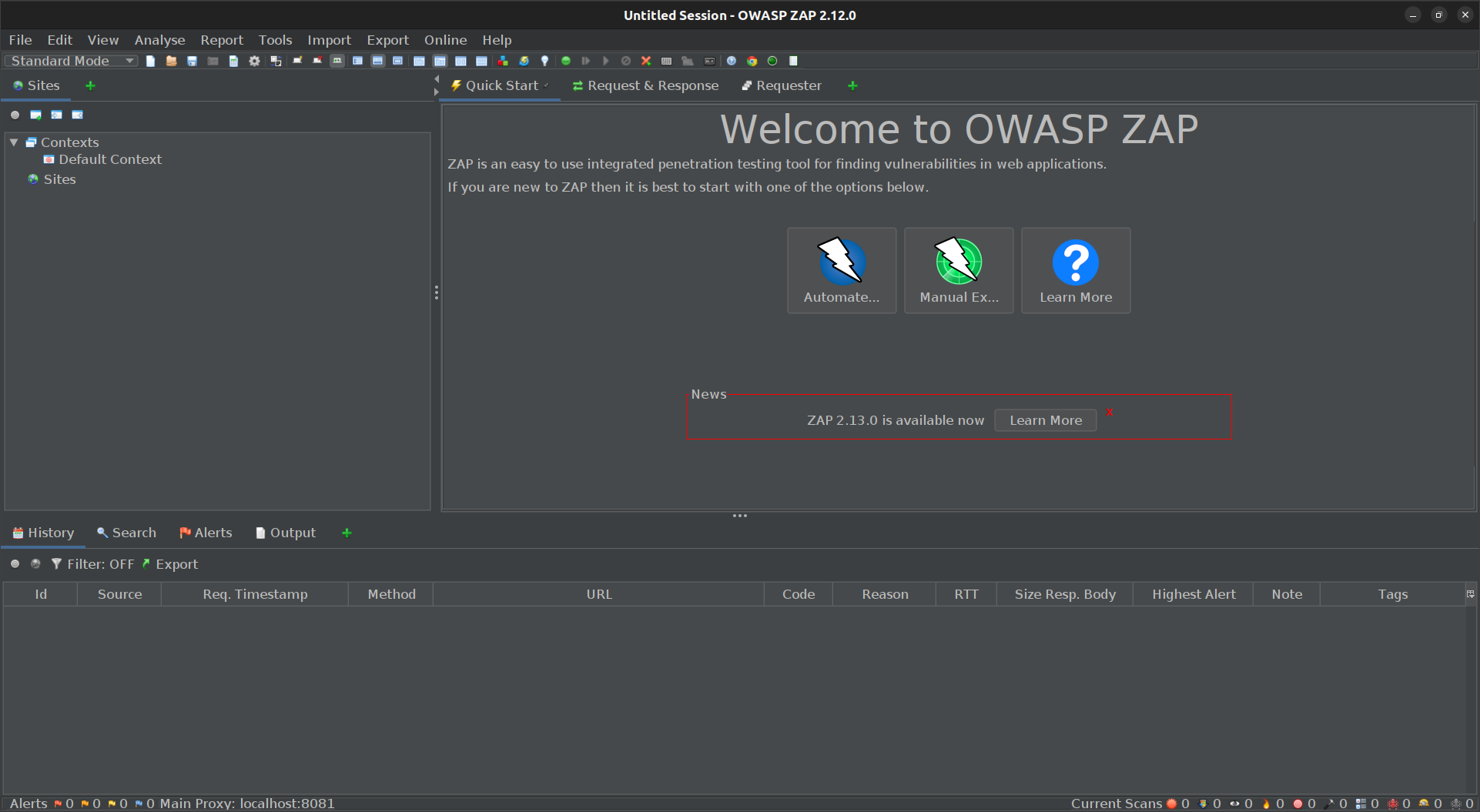
1. ZAP
Key Features:
- Target: Web applications
- Pentest Capabilities: Automated and manual pentests
- Deployment Capabilities: Manual installation from source code pre-built packages and Docker
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: OWASP Top 10
ZAP, or Zed Attack Proxy, is a powerful VAPT tool designed to help security analysts pentest web applications. It functions as a Man-in-the-Middle (MitM) proxy, empowering you to intercept, analyze, and even modify web traffic flowing between a browser and a web application.
ZAP offers grants analysts a comprehensive toolkit for in-depth security assessments, including session manipulation, fuzzing for vulnerabilities, and launching brute-force attacks.
Pros:
- User-friendly interface, especially for beginners
- Designed to scan for OWASP Top 10
Cons:
- Some features require extra plugins
- False positives are possible
2. Nmap
Key Features:
- Target: Network infrastructure, IoT devices, limited cloud instances
- Pentest Capabilities: Unlimited scans for network discovery, vulnerability scanning, service identification, and OS fingerprinting
- Deployment Capabilities: Flexible deployment through the command line, scripting, and graphical interfaces
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Network VAPT
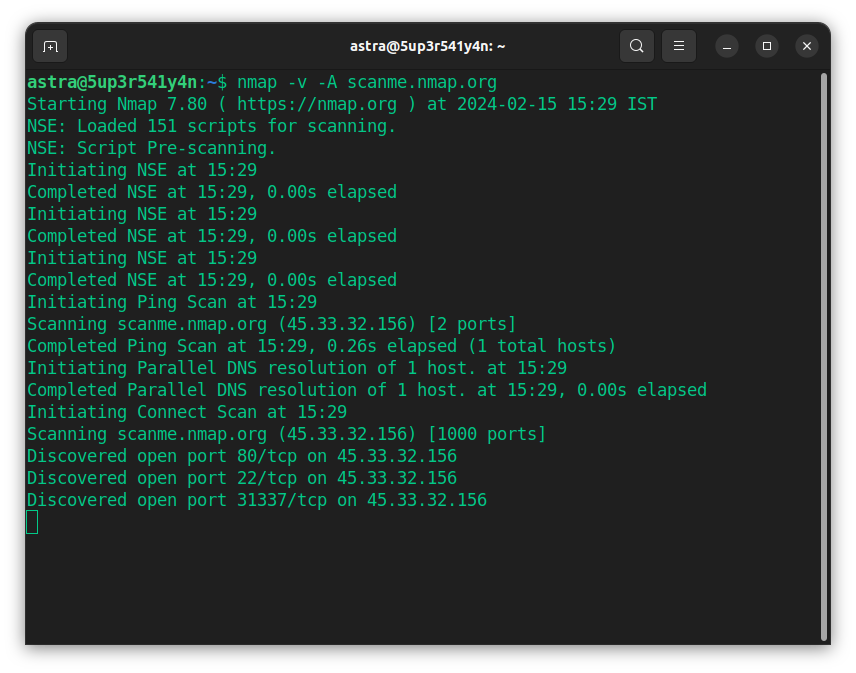
Nmap is a free and open-source network scanning and VAPT tool that helps pinpoint potential entry points and identify running services on connected systems. This translates to improved efficiency and deeper network insights.
Nmap’s version detection capabilities and scripting engine, NSE, empower security professionals to automate tasks, enhance scans, and even create custom scripts to tackle specific network vulnerabilities.
Pros:
- Offers an advanced GUI and results viewer
- Designed to map large networks
Cons:
- Intrusive scanning techniques
- Has a steep learning curve for beginners
3. Vega
Key Features:
- Target: Web applications
- Pentest Capabilities: Website crawling and automated scanning
- Deployment Capabilities: Manual installation from source code and pre-built packages with JRE
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Custom VAPT for web apps
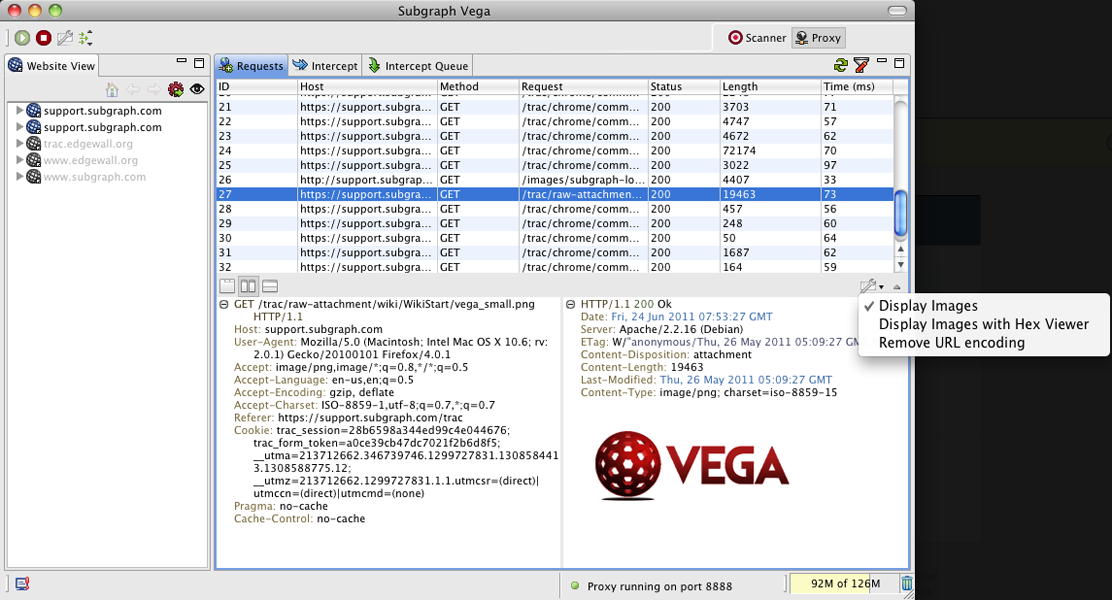
As an open-source VAPT testing tool, Vega offers a comprehensive suite of functionalities to intercept and analyze web traffic, efficiently crawl web applications, and pinpoint vulnerabilities like misconfigured SSL/TLS certificates.
Vega’s extensibility through JavaScript allows security professionals to tailor the pentesting experience to their needs.
Pros:
- Offers extensive customization through scripting support
- Offers active community support
Limitations:
- The interface is a little dated
4. Wireshark
Key Features:
- Target: Network
- Pentest Capabilities: Vulnerability detection, deep packet inspection, and traffic analysis
- Deployment Capabilities: Installer packages for traditional and portable versions
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Network traffic centered VAPT
Beyond a network packet analyzer, Wireshark is a versatile VAPT tool for internal penetration testing. Its ability to dissect real-time and historical traffic enables the reconstruction of attack timelines, identification of vectors, and a deeper understanding of the attacker’s behavior.
Thus, analysts can leverage Wireshark’s deep inspection capabilities to uncover vulnerabilities in network protocols, configurations, and applications.
Pros:
- Analyzes real-time and historical data
- Offers a variety of in-built filters for customization
Limitations:
- Large packets of data can lead to performance degradation
- Cannot perform packet injection
5. Nikto
Key Features:
- Target: Web applications and servers
- Pentest Capabilities: Vulnerability and misconfiguration identification
- Deployment Capabilities: Manual installation from source code
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Open-source VAPT for web apps and servers
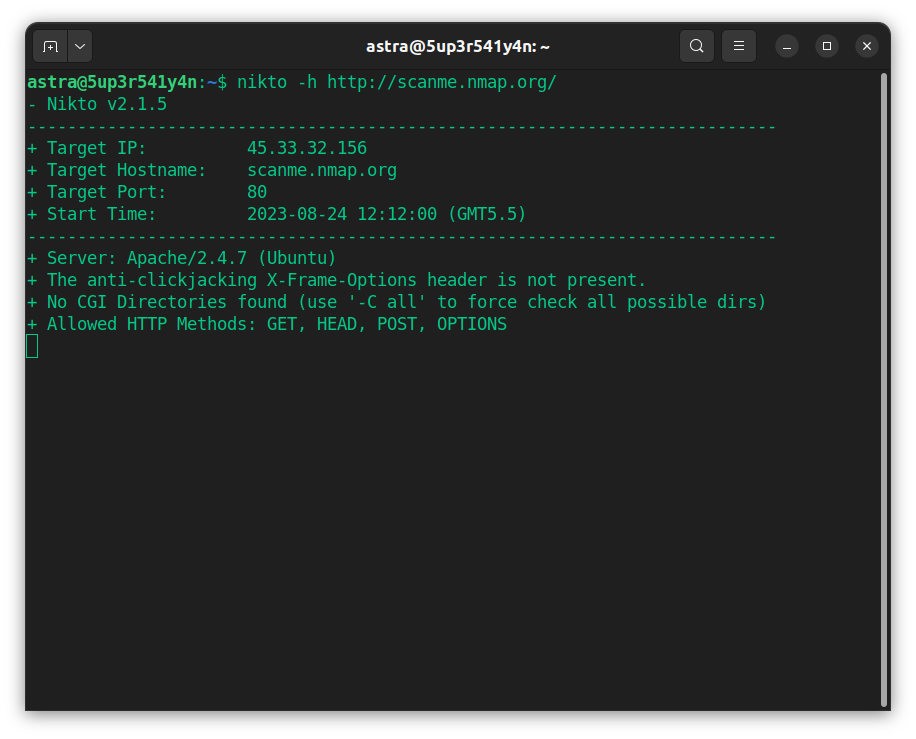
Nikto is a powerful open-source vulnerability assessment and penetration testing tool that scans for over 6,700 vulnerabilities, including outdated software, misconfigurations, and common exploits.
It allows analysts to customize tests through plugin support, helping them identify issues such as open directories, insecure file permissions, and weak HTTP headers.
Pros:
- Easy for beginners to use
- Tests for 6700+ bugs and CVEs
Limitations:
- Does not have a community support platform.
- Results require manual vetting to avoid false positives
6. W3af
Key Features:
- Target: Web applications
- Pentest Capabilities: Vulnerability scanning, threat exploitation, and attack simulation
- Deployment Capabilities: Manual installation from source code and pre-built packages
- Accuracy: False positives are possible
- Price: Open-source tool
- Best Suited For: Evaluation of the security posture of a web application
The Web Application Attack and Audit Framework (W3af) is a common open-source VAPT testing tool that identifies vulnerabilities and helps assess their impact and severity. This provides a more complete picture of your security posture.
It helps integrate seamlessly with DevSecOps practices and supports multiple operating systems, along with manual exploit customization for advanced testing needs
Pros:
- Helps automate repetitive tasks
- Can also scan session-protected pages
Limitations:
- UI can be complex to navigate
- False positives are possible
How to Choose The Best VAPT Tool?
1. Define Your Needs:
Before starting your search for the best tool, determine the purpose of the pentest (e.g., security posture check, compliance requirement), budget, and timeline. This clarifies your non-negotiables and helps identify the ideal pentesting partner.
2. Do Your Research:
Don’t rely solely on company-promoted information and marketing collaterals. Read independent reviews and check if the company has a strong reputation in your industry, especially with your specific type of asset.
3. Understand the Deliverables:
Get access to sample reports to ensure they provide actionable insights into vulnerabilities, including how to recreate them and how to fix them. Consider requesting an “executive summary” for easier communication with non-technical stakeholders.
4. Choose a Responsive Partner:
Choose the VAPT tool that offers active customer support. Effective communication and responsive support teams help resolve identified vulnerabilities and streamline remediation, especially in complex environments.
Final Thoughts
The above guide highlights the top VAPT tools available in the industry. These tools equip firms and security analysts with key considerations such as scanning capabilities, a CXO-friendly dashboard, compliance-specific scans, custom pentest reports, and workflow integrations.
Understanding and evaluating your specific needs against available options can help you select the right tool to enhance your overall security posture. While various tools cater to specific needs, platforms like Astra Pentest offer a comprehensive approach with PtaaS VAPT solutions that are ideal for both parties.
Ultimately, investing in an effective VAPT solution empowers you to address security risks and build a robust security posture proactively.
FAQs
What is a VAPT tool?
A VAPT tool is a security program that scans for weaknesses in your systems (vulnerability assessment) and then ethically tries to exploit them (penetration testing) to expose areas for improvement.
How much does a VAPT cost?
The cost of a VAPT varies depending on a variety of factors such as complexity, scope, and vendor. However, it can fluctuate anywhere within a range of $1,500 to $25,000+ per engagement.
What is the difference between VAPT and Pentest?
VAPT (Vulnerability Assessment and Penetration Testing) combines vulnerability scanning with manual testing to assess security posture. Pentesting, on the other hand, solely focuses on exploiting vulnerabilities to identify security weaknesses.
![11 Top VAPT Tools [Compared & Reviewed]](https://cdn-blog.getastra.com/2024/03/452a01aa-11-best-vapt-tools-of-all-time.png)















