Internal penetration testing is a type of ethical hacking in which testers with initial access to a network attempt to compromise it from the inside to intrude and gain further access. The insider or tester with network access simulates the actions of a real attack.
Types of Pentest: Internal vs External penetration testing
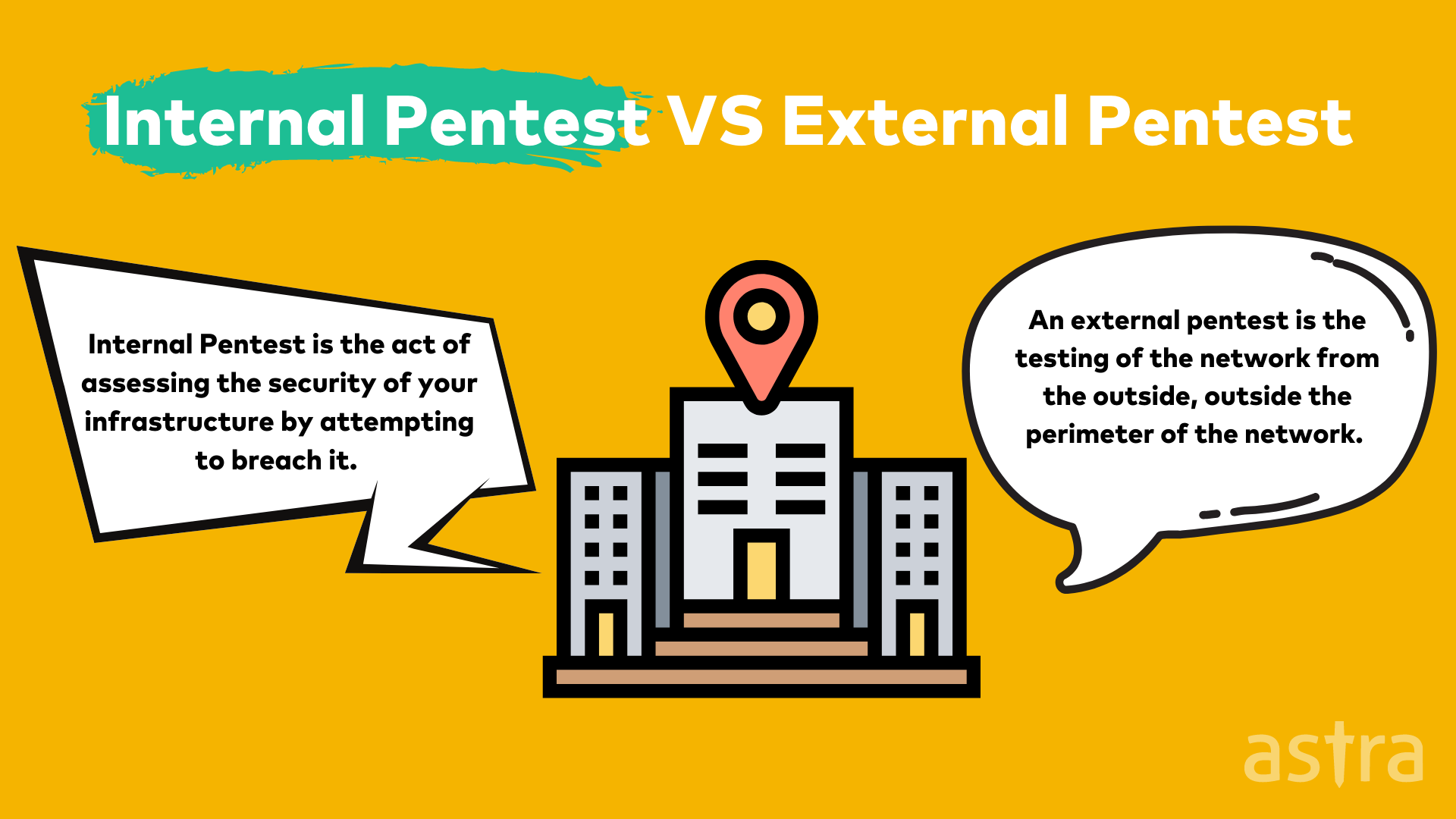
Internal Pentest is the act of assessing the security of your infrastructure by attempting to breach it. This can be done by an external party or by an internal party.
An internal party will typically be someone who is already working for your company. An external party may be hired through an external company.
The reason for performing an Internal pentest is to determine what an attacker could achieve with initial access to your network. Typically, an external party obtains this first access and then uses it to gain access to your internal network. The results of your internal penetration test will be used to create a baseline of your network.
An external pentest is the testing of the network from the outside, outside the perimeter of the network. This is usually termed External Penetration Testing. The external penetration test determines the network’s security from the outside and tests the external security controls such as network devices, network ports and firewalls, and web applications.
External Pentest is an advanced level of penetration testing that involves testing the effectiveness of perimeter security controls to prevent and detect attacks.
External penetration testing is performed by third-party security professionals who are not involved in designing, implementing, or maintaining the organization’s network infrastructure or systems.
Internal Penetration Testing: A Detailed Guide
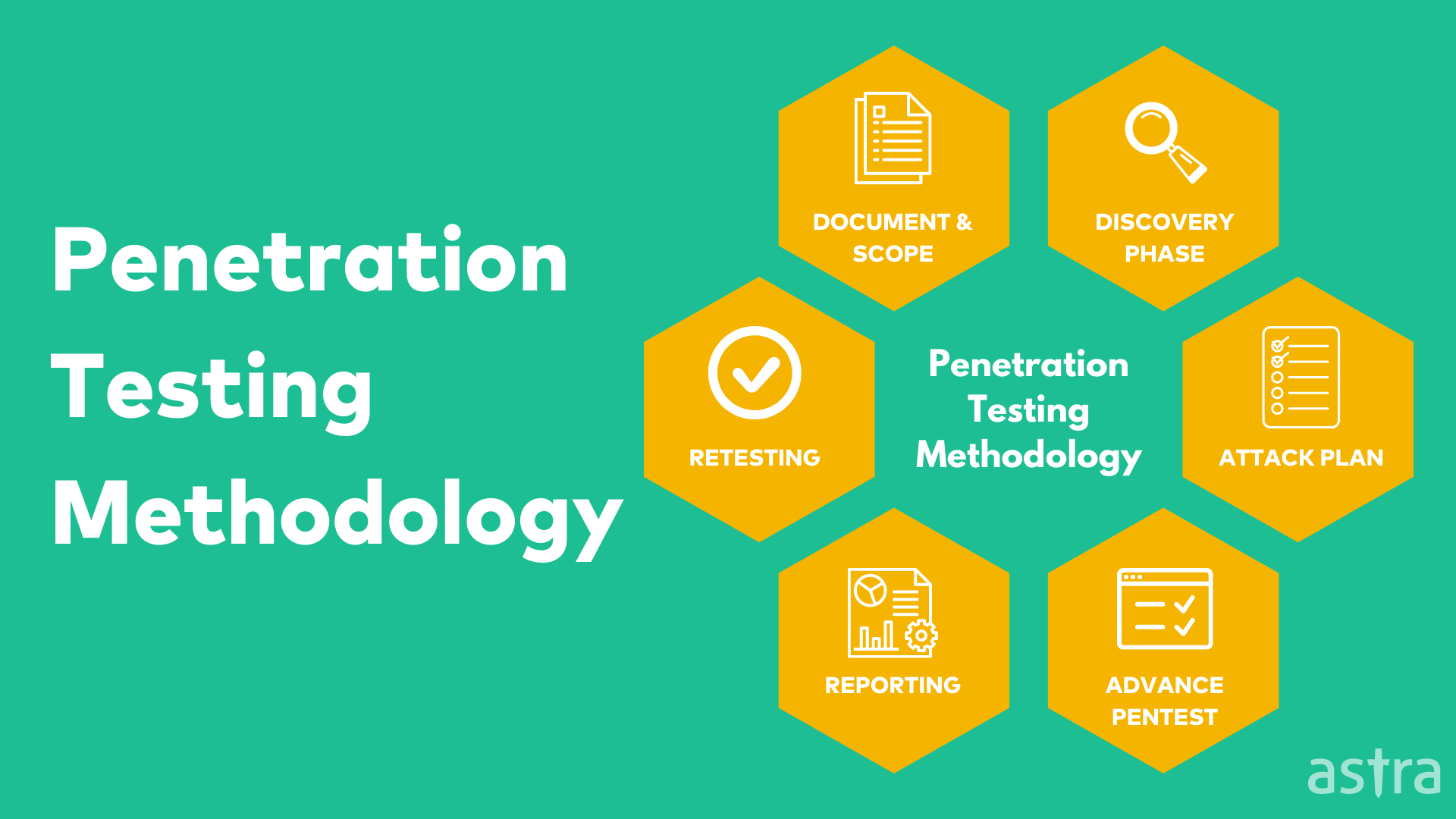
Let’s start with the components of an internal penetration test in brief:
- Information Gathering: Collect as much information about target systems or networks to perform further penetration tests.
- Discovery Phase: Information gathered to discover vulnerabilities on the target using automated scanning tools.
- Exploitation: This is where the hacker uses any vulnerabilities previously identified during the reconnaissance phase.
- Reporting: The report is usually presented to the management or the IT department of the company to take mitigative action for the vulnerabilities found and exploited.
An internal pentest is designed to simulate the actions of a real attack. It’s an attack performed by an insider or someone who has initial access to the network. This attack is often referred to as an Advanced Persistent Threat (APT) attack.
An internal pentest, however, isn’t limited to APT testing. There are many other reasons why you might want to do an internal penetration test. For example, if you have a malicious insider or an employee leaves the company, you should be prepared for them to take company data with them.
The purpose is to find the security gaps in your network before an attacker can discover them, giving you time to develop a plan to fix the problem before you are compromised.
Several companies have internal teams known as red and blue teams. These teams can include both software developers and security specialists. The Red Team will attempt to find security flaws and weaknesses in the system, and the Blue Team will guard the system and protect it from attacks. Both teams will work together to improve the system and provide better security against attacks.
Benefits of Internal Pentest
Today, most businesses are improving their defenses against outside threats, but they forget that 49% of cyber attacks come from within.
An internal breach into your business can be much more devastating than an outside threat because users don’t expect the people they trust to do them harm. This is why internal penetration testing is becoming more popular.
Internal penetration testing involves simulating an attack from an insider. It consists in analyzing the network infrastructure for vulnerabilities, evaluating access controls within the infrastructure, and testing the security controls of applications and databases.
Some other benefits of performing internal pentest are:
- Find Internal vulnerabilities
- Uncover internal or insider threats
- Thorough & Extensive testing
- Save the cost of a data breach
- Helps in achieving compliance
Internal Penetration Testing Steps
Internal pentest or Internal Penetration testing can be broken down into three main steps:
1. Information Gathering
Information Gathering is the first phase of penetration testing; it’s about collecting as much information about target systems or networks to perform further penetration tests.
Information Gathering is an important phase of penetration testing. If the information gathering is not done correctly, it can lead to information loss, which will result in the penetration tester performing the penetration testing again.
2. Discovery Phase
In the Discovery phase, the Penetration Tester uses the information gathered in Reconnaissance to discover vulnerabilities on the target. Penetration testers use various automation tools to perform automated scans.
The information gathered in the Reconnaissance phase is the foundation of any subsequent attacks and is used as a starting point for the Discovery phase.
3. Exploitation
The third phase in the hacking process is the exploitation phase. This is where the hacker makes use of any vulnerabilities that were previously identified during the reconnaissance phase.
The goal of this phase is to gain access to the target system. If the hacker can gain access to the target system, they can then take control of the system and use it for their purposes.
4. Reporting
The reporting phase of penetration testing is an essential step in the entire penetration testing process, which helps you understand your network’s security posture.
The report is usually presented to the management or the IT department of the company. Its main goal is to help the company (or the IT department) make the right decisions to fix the security problems detected during the penetration testing, improve the overall security of the assets, and better the company’s cyber security posture.
Common Internal Pentest Methodology
It’s important to follow industry standards for internal penetration testing due to how it pertains directly to your organization.
Though you can customize processes and procedures on top of industry methods, make sure that you don’t stray too far away from the elements that make up the standard in the first place!
Checkout most commonly used internal pentest methodologies:
1. OWASP Penetration Testing Guide
2. PCI Penetration Testing Guide
3. NIST 800-115
7 Best Internal Penetration Testing Tools
When it comes to performing an internal penetration test, there are several ways that you can go about it. You can employ someone to complete the test for you, or you could go the DIY route and do it yourself.
The DIY route can be a lot of work, especially if you are not familiar with the tools used in the process. Fortunately, there are tools that you can use to perform an internal penetration test for you.
Let’s take a look at the different tools that you can use for this process –
1. Metasploit
2. Nmap
3. Wireshark
4. Burp Suite
5. Hashcat
6. Sqlmap
7. OWASP Zap
How can Astra help you enhance your Internal Pentest Plan?
Internal Pentest is a complex task that needs a team of professionals like security engineers to carry out. Companies often don’t utilize this service, as they think it’s expensive and not very effective. However, internal pentest is still considered an essential part of any security plan.
The primary reason why companies don’t use internal pentest is that they think it’s expensive and time-consuming. But, with the right team of security engineers, it is possible to carry out an effective internal pentest.
Astra is a team of expert and skilled security engineers. The security engineer at Astra is always up to date with the latest technology and knows how to handle cyber attacks. The Astra team of security engineers is cost-effective and delivers the best penetration testing services in a limited time.
Checkout Astra’s Pricing
Conclusion
To make the business secure from cyber attacks, there is a need for an internal pentest. Internal pentest is used to find loopholes in the infrastructure of the company. It’s like a security audit for your company. Security engineers carry out internal pentest to find vulnerabilities in the company’s infrastructure, which is why you need Astra. Schedule a call today with us and let us secure your organization.