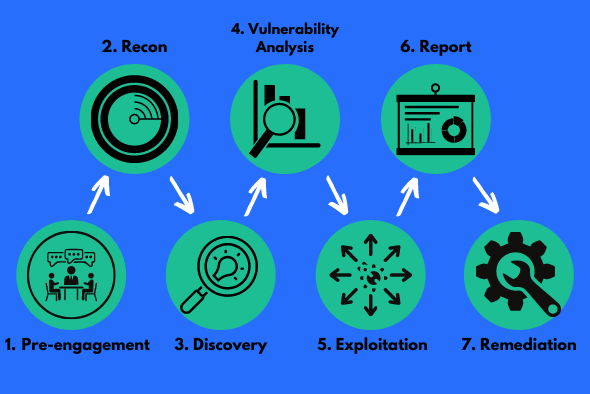
There are seven penetration testing phases: Pre-engagement phase of Pentesting, reconnaissance, discovery, vulnerability analysis, exploitation and post-exploitation, reporting and recommendations, and Remediation and Rescan. Let’s take a detailed look at each of these phases.
7 Phases of Penetration Testing are:
- Phase I: Pre-engagement phase of Pentesting
- Phase II : Reconnaissance
- Phase III: Discovery
- Phase IV: Vulnerability Analysis
- Phase V: Exploitation and Post Exploitation
- Phase VI: Reporting and Recommendations
- Phase VII: Remediation and Rescan
When you opt for an external pentesting solution or service provider, the entire pentesting process requires collaboration between your organization and the external security testing team. The terms of this collaboration are agreed upon in a pre-engagement phase. Let us see what it covers.
Penetration Testing Phase I: Pre-engagement phase
This is the stage where the logistics and the rules of engagement of the test are discussed.
The VAPT providers and the target organization can discuss the legal implications of the exercise. The objective of the test is determined and the goals of the pentest are aligned with the specific requirements of a business. You may want to keep certain areas off-limits for the pentesting team, this is the phase to clarify all of that.
This is also the time when the scope of the penetration test is defined.
Determining the scope of the penetration test ensures that both the target and the tester know what to expect from the test. There are certain assets that the pentesters are allowed to test, those are within the scope of the pentest, and others are not. Similarly, the target organization’s security posture is tested for a predetermined set of vulnerabilities, anything out of that set is out of scope for the pentest. The scope of the pentest greatly influences all the subsequent penetration testing phases.
Penetration Testing Phase II: Reconnaissance
In order to simulate a cyber attack on an application or a network, the pentester needs access to information about the target. They gather this information in the reconnaissance stage.
Whether a hacker wants to target an entire network or a single web application, they need to know as much as they can. That is exactly how a pentester approaches the target. The scoping done in the previous phase helps the pentester narrow down the recon to increase efficiency.
There are two kinds of reconnaissance –
1. Active reconnaissance
The pentesters engage directly with the target system to gather information. While this is a more accurate approach to reconnaissance, it makes more noise since the intruder interacts with the system.
2. Passive reconnaissance
In this mode, the intruder does not interact with the target system and applies different passive strategies instead to gather information. They can try to eavesdrop on network traffic, and trace OS footprinting or internet footprinting.
When it comes to attacking a web application, mapping is an important part of the recon operation. This step helps the attacker to look at all the pieces of the application in one place and form an understanding of how the app works. An application has many implemented functionalities and understanding them is crucial for the success of the subsequent penetration testing phases.
Penetration Testing Phase III: Discovery
The discovery phase can be divided into two parts:
- Further information gathering
- Vulnerability scan
The first part involves gathering more information about the target network using a bunch of different techniques. Let us talk about a few of them.
- Hackers can uncover host-names and IP information using techniques like DNS interrogation, InterNIC queries, and network sniffing.
- Banner grabbing can be used to uncover application and service information.
- During an internal test, the tester can uncover system information such as names and shares using NetBIOS enumeration.
The second part consists of testing the application or the operating system for known vulnerabilities. You can get an automated scan where the system is tested against a vulnerability database. Or you can go for a manual scan where security engineers manually scan the systems. The latter is more suitable for uncovering new and hidden vulnerabilities whereas the former is faster.
Penetration Testing Phase IV: Vulnerability Analysis
You will discover various threat sources during a security scan. It is important to tie each of those threat sources to a vulnerability and then prioritize it depending on the risk it poses to the system.
You need a well-defined and consistent process of analyzing the vulnerabilities in terms of severity and risk. It is the job of a VAPT provider to analyze the vulnerabilities and create a clear picture for you to understand and act upon.
While it is difficult to assign an exact number to a vulnerability, a lot of VAPT companies use a semi-quantitative method of rating the vulnerabilities. The Common Vulnerability Scoring System (CVSS) is a globally accepted method of producing a numerical score based on the severity of a vulnerability.
The CVSS score helps you rate a vulnerability as low, medium, or high in terms of severity. You can prioritize one vulnerability over others depending on these factors, when it comes to remediation, the last one of the Penetration testing phases.
The assessment of vulnerabilities is usually performed in line with various security and risk assessment standards such as the Risk Assessment Guide for Information Technology Systems by the National Institute of Standards and Technology (NIST), ISO 27001, HIPAA, and more.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
Penetration Testing Phase V: Exploitation and Post-Exploitation
The previous phases prepare the stage for the exploitation phase. The goal here is to establish access to a system using the loopholes uncovered in the earlier phases of Pen testing. The pentester tries to identify an entry point and then looks for assets that can be accessed through that.
The pentesters have to be very careful while conducting this phase to ensure that the business functionalities are not compromised or hindered. Nevertheless, system crashes during penetration testing are very rare.
The post-exploitation phase
After the pentester has exploited a vulnerability and identified an entry point to the system the next job is to determine the value of that entry point. The questions they ponder are
- How much access does the entry point yield?
- How easy is it to maintain access?
- How much time may pass before the breach is spotted?
- What is the degree of harm that the vulnerability may cause?
The exploitation and post-exploitation phases help the tester gain access, locate sensitive data, identify communication channels, etc. They can also try and exploit the connection between different systems within the network and expand the breach.
The extent to which a pentester may exploit a certain vulnerability is determined by the rules of engagement agreed upon in the pre-engagement stage.
Penetration Testing Phase VI: Reporting and Recommendations
All the previous penetration testing phases contribute to this phase where a VAPT report is created and shared with the client. In the reporting phase, the pen-testers provide detailed information about the vulnerabilities such as,
- The description of the vulnerabilities.
- Ratings according to a common vulnerability scoring system.
- Severity and impact of vulnerability.
- Risk assessment report.
- Video POCs.
- Recommendations for fixing the vulnerabilities.
The quality of a VAPT report determines how quickly and efficiently you will reproduce and remove the vulnerabilities from your system.
Penetration Testing Phase VII: Remediation and Rescan
The VAPT report consists of step-by-step recommendations for fixing the vulnerabilities. Your developers can follow those recommendations to close the gaps in your application security. The VAPT company you are partnering with for the security testing should help you at every step of this process.
An ideal remediation phase looks something like this:
- Vulnerabilities are reported with detailed remediation steps.
- There is video-based assistance from the security engineers.
- Developers get on a call to discuss the remediation steps when needed.
Once the vulnerabilities are fixed, the VAPT company should offer rescans to identify any security loopholes that might have been left unattended.
How much time does it take to complete all the phases of penetration testing?
The first six penetration test phases, that is from conducting reconnaissance to producing a VAPT report, should not take more than 10 days. The timeline may vary a little bit based on the scope of the test.
The timeline for the remediation phase depends upon how quickly your development team can work on the fixes recommended by the pentesting team. However, there is usually a stipulated time to avail of the free rescan offered by a VAPT company.
What happens after all seven penetration testing phases are covered?
After the vulnerabilities are found and fixed, the VAPT company runs rescans of your application. If no more vulnerabilities are found in the rescans, the VAPT company may offer you a successful VAPT certificate. You can use this certificate to achieve the minimum requirements of pentesting for achieving regulatory compliances such as ISO, SOC2, HIPAA, FISMA, and many more.
Some popular tools you can use for pentesting
- Astra vulnerability scanner: This tool lets you test your web application with 8000+ tests and helps you fix them. The entire scan takes 4-7 days to complete.
- Zed Attack Proxy: This tool lets you check your web app for vulnerabilities during the construction or testing phases of development.
- W3af: It is a Python-based tool that can find up to 200 different security vulnerabilities.
- Arachni: Arachni is an open-source security scanner for web pages.
Astra Pentest: The Security Suite that does not test your patience
Astra Pentest is as simple a security product as you can find and yet it offers unmatched functionality, independence, efficiency, and value.

- Every user is assigned a dedicated VAPT dashboard where they can visualize the thorough analysis of vulnerabilities.
- Although the entire vulnerability assessment and penetration testing may take up to 10 days, you start seeing vulnerabilities along with CVSS scores and remediation steps 2 days into the manual scan.
- You can also run automated vulnerability scans and get the scan results very quickly.
- Astra Pentest also offers security scans behind the admin login (with its newly-introduced Google Chrome extension).
- The VAPT report is complete with video PoCs making it extremely easy for the developers to reproduce and fix the vulnerabilities.
- You get 2-3 free rescans after the vulnerabilities are fixed.
- You get a publicly verifiable Pentest certificate.
Astra strives to make all the pen testing phases as smooth for the users as possible.
To sum it all up
We have discussed seven different Penetration testing phases from gathering information to analysis and removal of vulnerabilities.
All these phases are interdependent and deserve ample attention. The important part for you is to ensure that none of the phases is jumped or ignored.
Remember, a vulnerability analysis without exhaustive reconnaissance is hardly reliable. Put your trust in the right place, choose a VAPT provider that has proven records of excellence and get ready to fix those vulnerabilities.
FAQs
What is the timeline for Penetration Testing?
Web app penetration testing takes between 7-10 days. The vulnerabilities start showing up in Astra’s pen test dashboard from the 3rd day so that you can get a head start with the remediation. The timeline may vary with the pen test scope.
How much does Pentesting for a Web App cost?
Web app Pentesting costs $99 to $399 per month to perform web application penetration testing depending on your choice of plan.
Why should you trust Astra with Pentesting?
With 8000+ tests according to global security standards, Astra ensures that all security loopholes are identified. Astra’s Pentest dashboard offers dynamic visualization of the impact and severity of threats. It helps you prioritize the remediation. Security engineers at Astra assists you in fixing the vulnerabilities and certifies your web app. It helps you through all the Penetration testing phases.
Do you get rescans after the vulnerabilities are fixed?
Yes, you get 2-3 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















