ISO 27001 is a global standard for maintaining a company’s information security management systems (ISMS). Created by the International Organization for Standardization, ISO 27001 provides frameworks, and guidelines for establishing, and maintaining an ISMS. ISO 27001 was created to help organizations protect their critical information assets and meet legal and regulatory requirements.
To achieve ISO 27001 compliance, your company’s ISMS is audited by a third-party ISO 27001 auditor against the ISO standard. One major regulatory requirement of ISO 27001 is penetration testing. In this blog, we will talk about ISO 27001 penetration testing to explore the relationship between ISO 27001 compliance and pentesting.
What is ISO 27001 Penetration Testing?
ISO 27001 penetration test is the process of security testing by simulating a cyberattack to find areas of non-compliance with ISO 27001 regulatory compliance and associated vulnerabilities to exploit them and understand the impact. It is implemented on assets that require ISO 27001 compliance.
ISO 27001 Pentest services are used to evaluate the security of websites, web applications, or networks.
What is ISO 27001 Compliance and Why Is It Important?
ISO 27001 compliance helps organizations establish, maintain, and improve security measures for their information assets. As a whole, it gives you a framework to implement an enterprise-wide Information Security Management System (ISMS) which helps you maintain availability, integrity, the confidentiality of information, and legal compliance.
ISO 27001 is important for any company that wants to run a business around information security to avoid hefty fines and data breaches. ISO, as you may know, stands for International Organization for Standardization.
ISO, together with IEC (International Electrotechnical Commission) published a standard for information security management in 2005 and they revised it in 2013. The European update of the ISO 27001 standard was published in 2017.
What Are The Security Areas Covered By ISO 27001?
ISO 27001 has 14 domains, which cover 6 security areas:
- Company Security Policy
- Asset Management
- Physical and Environmental Security
- Access Control
- Incident Management
- Regulatory Compliance
Does ISO 27001 Require Penetration Testing?
ISO 27001 does not mandate penetration tests but rather recommends the practice as mentioned in the ISO27001 controls A.12.6.1 (Technical Vulnerability Management) which mentions that vulnerabilities should be evaluated and prioritized for mitigation.
What Are the ISO 27001 Penetration Test Requirements?
While ISO 27001 does not mention a penetration testing requirement directly, it is not out of the question when trying to comply with ISO 27001. Let us take a look at ISO control A.12.6.1 of Annex A of ISO 27001:2013 (also known as Technical Vulnerability Management). It states:
“Information about technical vulnerabilities of information systems being used shall be obtained in a timely fashion, the organization’s exposure to such vulnerabilities evaluated, and appropriate measures taken to address the associated risk.”
Now, only a penetration test on top of a vulnerability assessment will give you a complete gap analysis in terms of security. You cannot rely on vulnerability scanning alone when it comes to evaluating the exposure of your organization to a certain vulnerability. And that is why ISO 27001 penetration testing is necessary.
How Frequently Should You Do ISO 27001 Penetration Testing?
The recommended frequency of ISO 27001 penetration testing for a company is 1-2 times a year or at the least, once. It usually depends on the size of the company, the number of employees, and industry requirements.
Another factor that plays a role is the period of the audit, which in the case of ISO 27001 is yearly, meaning a penetration test would be required whenever going for an ISO 27001 audit.
Scope Of ISO 27001 Penetration Test
The scope of a pentest refers to setting and deciding on the assets to be tested, tests and exploits allowed to be carried out, how far the exploits can go, and more. This process is highly comprehensive and covers every aspect of a potential pentest before it is conducted on a system.
Scopes ISO 27001 penetration testing for network security, websites, and more are designed this way to avoid any scope creep and legal liabilities later on.
ISO 27001 Pentest scope usually involves:
- Location details, data assets, employee information, and technologies.
- Taking a count of the internal and external issues of a cyber asset.
- Expectations and requirements of the organization in need of the ISO 27001 pentest.
What Are The Recommended Pentesting Methodologies For ISO 27001?
Since ISO 27001 does not mention penetration testing directly, it also does not mention any recommendations on methodologies to be followed for ISO 27001 penetration testing. This essentially means that the methodology followed is based on the tester’s or your discretion.
A few well-recognized and deployed methodologies for penetration testing however are,
- OWASP Top 10: OWASP top 10 covers major vulnerabilities for web applications, APIs, mobile applications, IoT, and more which can be used to detect those flaws in your assets.
- SANS 25: is not as famed as OWASP Top 10, however, it holds value in terms of identifying software errors.
- NIST: this pentesting methodology is more concerned with reporting styles and legal aspects unlike the other two which focused more on application vulnerabilities.
The Benefits of ISO 27001 Penetration Testing
We have already discussed the necessity of ISO 27001 penetration testing. Let us now understand what is in it for you.
- By conducting a penetration test and fixing the vulnerabilities you nail one of the most difficult parts of the ISO 27001 compliance audit.
- An ISO 27001 certification would help you build trust. It has been seen to have a direct impact on revenue.
- You get rid of dangerous vulnerabilities in the way of preparing for the compliance audit, it is a win-win situation for you.
Average Pricing of ISO 27001 Penetration Testing Services
ISO 27001 penetration test cost for web apps starts from $199 per month. The cost of pentesting for cloud or mobile applications varies depending on the scope of the pentest. Penetration testing for assets on a yearly basis ranges from $5000 to $8000 depending on the features offered along with the required penetration test.
Lower-priced penetration tests may just be automated scans that would not detect niche vulnerabilities within your applications. It is therefore prudent to spend wisely on a reputed pentesting company with relevant experience and qualified pentesters.
How can Astra Security Help You with Penetration Testing Compliance?
Astra Pentest helps you target the issues required for certain compliance, be it HIPAA, PCI-DSS, ISO 27001, or OWASP. They also help you gain end-to-end compliance with SOC2, PCI DSS, and HIPAA with the help of vetted auditors.
Astra’s Pentest has come up with a new pentest compliance feature that allows you real-time visibility of the compliance requirements you pass or fail according to the vulnerability scans from within a pentest dashboard. This feature makes compliance reporting way simpler for you.
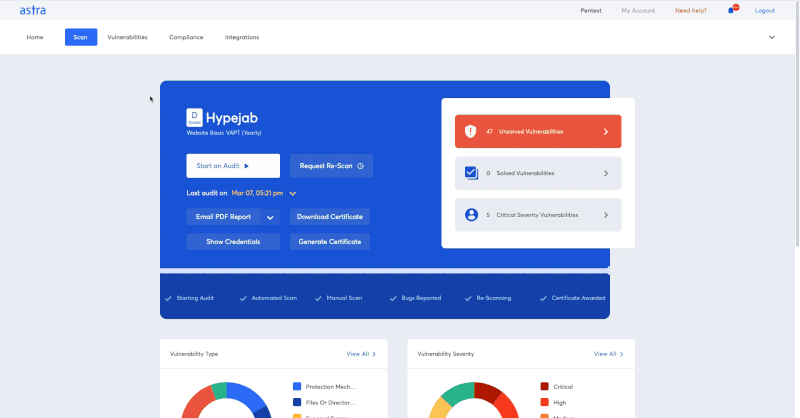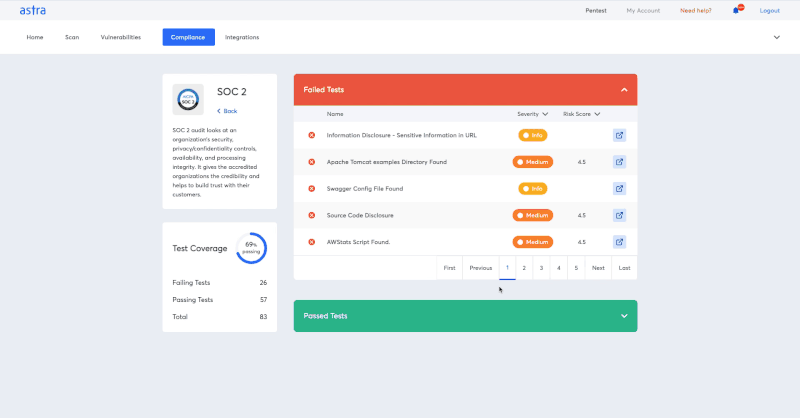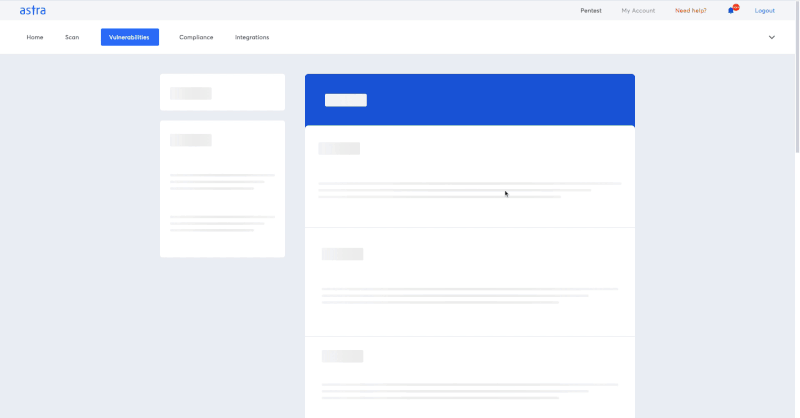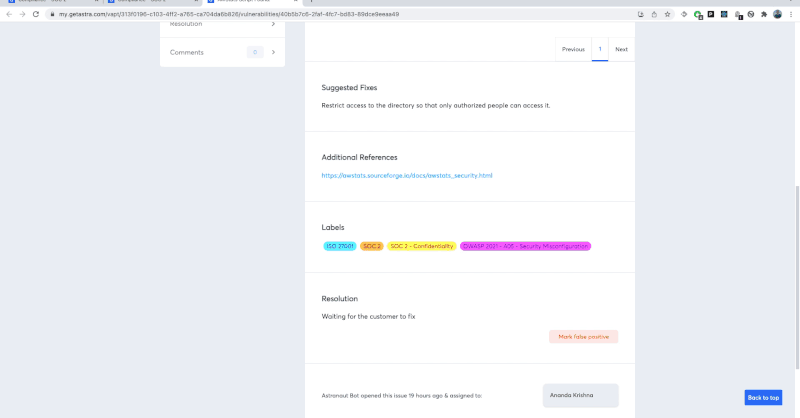
That aside, Astra Pentest ensures that you get the best out of your ISO 27001 penetration testing with 8000+ tests, scan behind logged-in pages, thorough remediation guidance, and support from security experts.
Conclusion
While compliance with security standards is not legally mandated in most cases, it is something you would want to do for the reliability, resilience, and longevity of your organization. Not only does getting an ISO 27001 compliance gives you global recognition as a secure company, but it also ensures that you have treated every security loophole in your systems to achieve a healthier security posture.
FAQs
1. Which are the best ISO 27001 auditors?
ISO 27001 auditors are external auditors who help you achieve ISO 27001 compliance through analysis of data collected, regular monitoring, and reviewing of ISMS. The best ISO 27001 auditors are:
1. Sprinto
2. Drata
3. Secureframe
4. Cyberops
5. QMS International
What is the average duration of ISO 27001 penetration testing?
On average, an ISO 27001 penetration test takes 4-10 days to completely assess an asset for non-compliance and vulnerabilities. Once the pentest vulnerability report is released the critical vulnerabilities are resolved within 1-2 days maximum.
Is ISO 27001 penetration testing enough to gain compliance?
No, penetration testing is a part of the larger process of gaining ISO 27001 compliance.
















