In recent years, the global landscape of commerce has undergone a significant transformation. Traditional brick-and-mortar stores have given way to online platforms as consumers turn to the internet to fulfill their shopping needs.
This transformation has made e-commerce a central player in the global economy. To put this into perspective, according to a recent report, cybercrime is predicted to cost $8 trillion by 2023 and will grow to $10.5 trillion by 2025.
This is where e-commerce penetration testing service steps in.
Action Points
- E-commerce penetration testing is a vital cybersecurity technique for identifying and addressing vulnerabilities in online businesses.
- E-commerce penetration testing offers benefits such as early vulnerability detection, improved security, and compliance adherence.
- The penetration testing process involves six phases: Pre-engagement, Information Gathering, Vulnerability Analysis, Exploitation, Post-Exploitation, and Reporting.
- Common tools for E-commerce penetration testing include Astra Pentest, SQLmap, and OWASP Zed Attack Proxy (ZAP), each serving different aspects of security assessment.
What is E-commerce Penetration Testing?
E-commerce penetration testing, also known as pen testing or ethical hacking, is a cybersecurity technique that organizations use to identify, test, and highlight vulnerabilities in their e-commerce systems, networks, or web applications.
Its purpose is to identify and evaluate vulnerabilities, weaknesses, and security gaps in an e-commerce website or application that can be exploited by real-world adversaries. Some key objectives include:
- Identifying vulnerabilities:
One of its primary objectives is to uncover potential security vulnerabilities within the e-commerce system. These may include weaknesses in the website’s code, misconfigured security settings, or other issues that could be exploited by attackers.
- Evaluating security controls:
Pentesters assess the effectiveness of existing security controls and measures in place such as the strength of access controls, encryption methods, and intrusion detection systems to ensure they are up to industry standards.
- Ensuring compliance with industry standards:
E-commerce platforms often need to comply with various industry regulations and standards, such as PCI DSS (Payment Card Industry Data Security Standard). Penetration testing helps verify that these compliance requirements are met and maintained.



What is the Importance of E-commerce Penetration Testing?
E-commerce penetration testing is an essential aspect of cybersecurity for businesses that operate online as outlined under:
1. Protecting Customer Data
E-commerce businesses handle sensitive customer data, including personal information and payment details. Penetration testing helps identify vulnerabilities in the system that could be exploited by cybercriminals, leading to data breaches, legal fallout, and loss of customer trust.
2. Safeguarding Financial Transactions
E-commerce platforms rely on payment gateways to process financial transactions. A breach in these systems can result in financial loss for both the business and its customers. Penetration testing helps ensure that payment data remains confidential and transactions are processed securely., saving costs of legal action as well as non-compliance.
3. Business Reputation
Security breaches can have a devastating impact on an e-commerce business’s reputation. When customer data is compromised, it erodes trust and can lead to negative publicity. Penetration testing helps prevent such breaches, safeguarding the brand’s reputation and customer loyalty.
What Are the Benefits of E-commerce Pentesting?
1. Early Identification of Vulnerabilities:
E-commerce websites are prime targets for cyberattacks due to the sensitive customer data they handle, such as credit card information and personal details.
By simulating various attack scenarios, security professionals can uncover weaknesses in the website’s code, infrastructure, and configuration proactively addressing them, and reducing the likelihood of data breaches, financial losses, and damage to your reputation.
2. Improved Security Posture:
Once vulnerabilities are identified, the testing team can work with the business to prioritize and remediate them. This process enhances the overall security posture of the e-commerce platform.
Moreover, regular testing also encourages a culture of security awareness within the organization, as it promotes the continuous improvement of security measures.
3. Compliance and Regulation Adherence:
Many industries, including e-commerce, are subject to various data protection regulations and compliance standards such as HIPAA and ISO 27001.
By identifying and addressing vulnerabilities, businesses can demonstrate their commitment to data security and compliance. This not only helps avoid legal consequences and fines but also instills trust in customers who want to know that their data is handled in accordance with the law.
What is The Penetration Testing Process?
The E-commerce pentesting process can be divided into 5 phases as explained under:
Phase 1: Pre-engagement Phase
During this phase, the pentesting team and client establish a clear understanding of the objectives and scope of the engagement, ensuring that both parties are aligned in their expectations. This phase includes the following steps:
Step 1: Defining Objectives and Scope:
In this step, the client outlines what they want to achieve through the penetration test. This may involve specific goals, such as identifying vulnerabilities in their e-commerce system or testing the effectiveness of their security controls. Defining the scope is crucial to determine which parts of the system will be tested and what should be off-limits.
Step 2: Contractual Agreements:
Once the objectives and scope are defined, the next step is to establish the terms of the engagement through contractual agreements. This includes legal considerations, project timelines, and any other essential details to ensure a smooth and legally compliant testing process.
Phase 2: Information Gathering
The information-gathering phase involves collecting crucial data about the e-commerce system to understand its architecture, potential vulnerabilities, and attack surfaces. This helps in planning and conducting a successful penetration test and consists of the following steps:
Step 1: Collecting Data about the E-commerce System:
Penetration testers gather information about the target system, such as domain names, IP addresses, server configurations, and network topology. This information is crucial for identifying potential entry points and attack vectors.
Step 2: Enumeration of Assets and Potential Vulnerabilities:
In this step, the testers enumerate assets within the e-commerce system and start identifying potential vulnerabilities, such as open ports, services, and software versions to build a profile of the target system and understand its weak points.
Phase 3: Vulnerability Analysis
The vulnerability analysis phase is focused on identifying weaknesses within the e-commerce system and assessing the potential attack vectors that could be exploited. This phase includes the following steps:
Step 1:Identifying Weaknesses in the System:
The penetration testers use various tools and techniques to actively scan and probe the target system for vulnerabilities. This may involve automated vulnerability scanning and manual testing to identify security flaws like misconfigurations, software vulnerabilities, or weak authentication mechanisms.
Step 2: Assessing Potential Attack Vectors:
Once vulnerabilities are identified, testers assess how they can be leveraged to gain unauthorized access to the system. They prioritize the vulnerabilities based on their severity and exploitability, focusing on those that pose the greatest risk.
Phase 4: Exploitation
In the exploitation phase, the penetration testers attempt to exploit the identified vulnerabilities, simulating real-world cyberattacks. This phase includes the following steps:
Step 1: Attempting to Exploit Vulnerabilities:
Testers actively try to exploit the vulnerabilities they’ve discovered, using various techniques such as code injection, privilege escalation, or brute force attacks. The goal is to gain access or control over the target system.
If successful, the testers work to gain unauthorized access to the system, mimicking the actions of a malicious attacker. This access may include gaining control of servers, databases, or other sensitive assets.
Phase 5: Post-Exploitation
The post-exploitation phase involves documenting the findings and the impact of the penetration test, as well as preparing for the final reporting phase. This phase includes the following steps:
Step 1: Documenting Findings and Impact:
Penetration testers carefully document their actions, including the vulnerabilities exploited, the data accessed, and the potential damage caused. This documentation is crucial for the client to understand the impact of the vulnerabilities.
Step 2: Reporting and Remediation Recommendations:
Testers prepare detailed reports that outline their findings with the risks identified and provide recommendations for remediation. These recommendations are essential for the client to improve their security posture and mitigate the identified vulnerabilities.
What are Some Common Tools for E-commerce Penetration Testing?
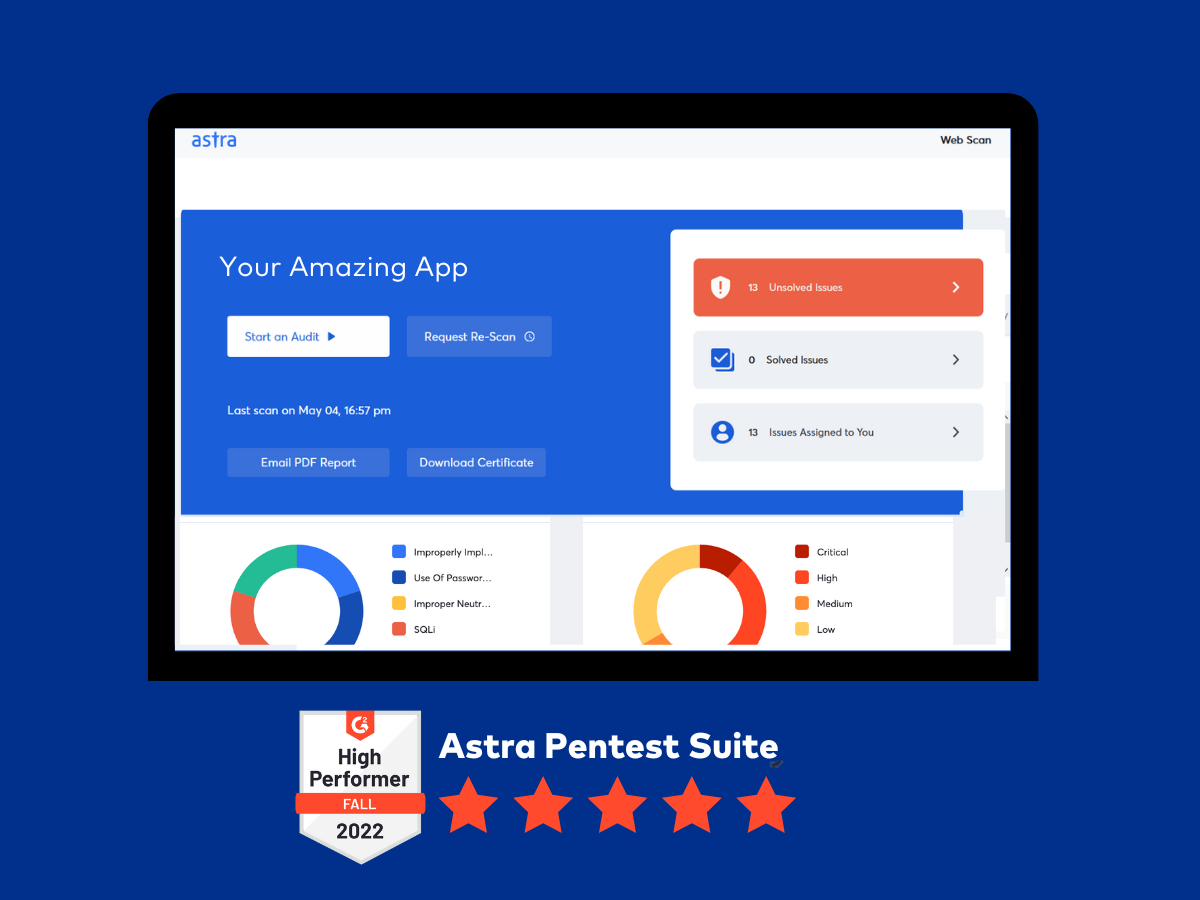
1. Astra Pentest
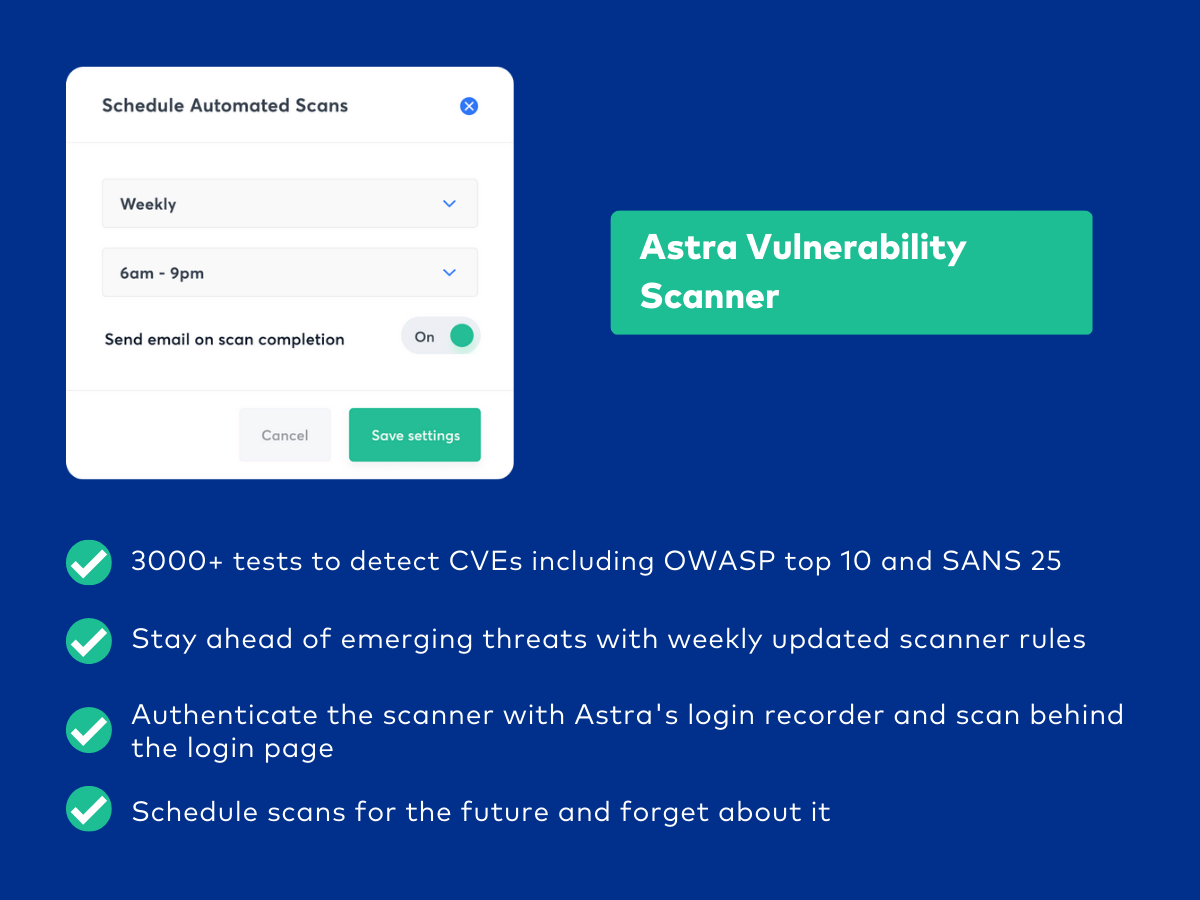
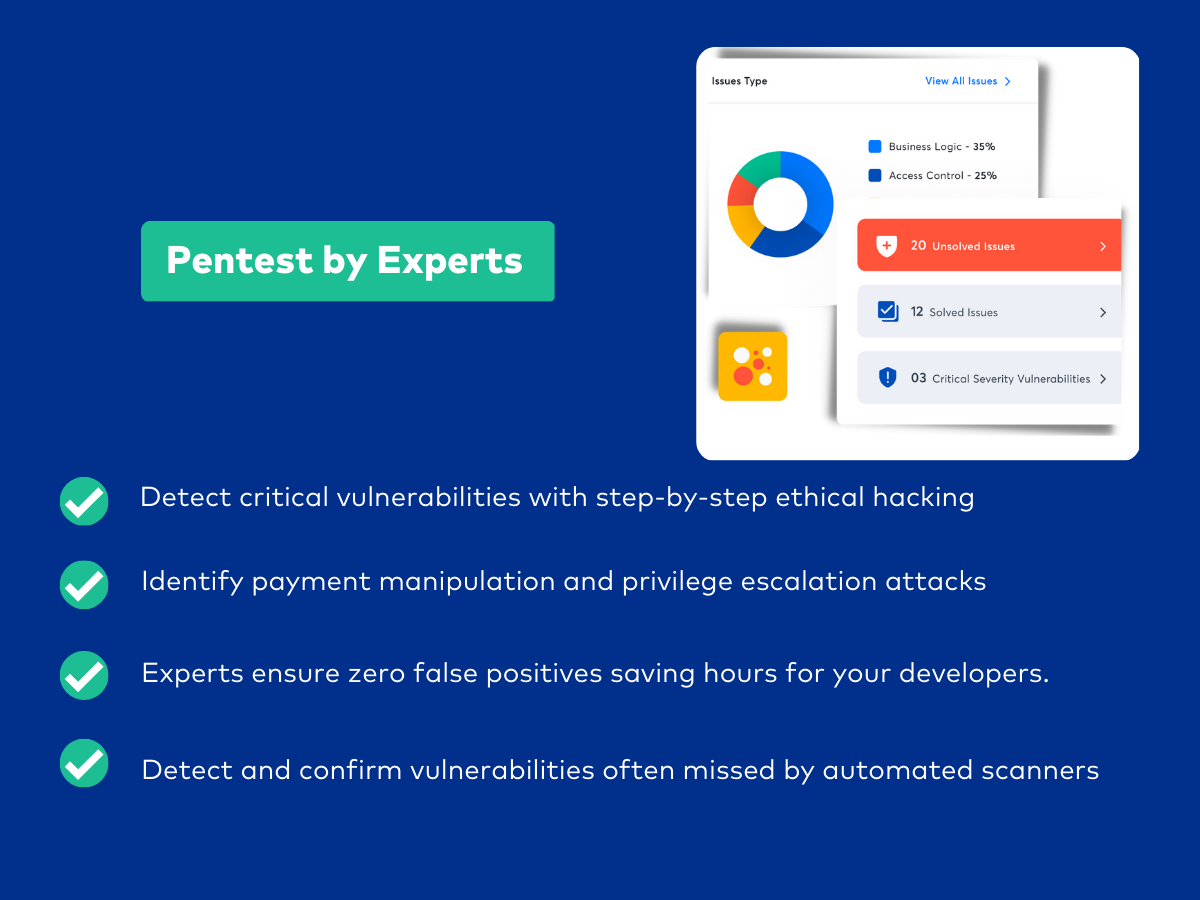
Astra is a leading provider of E-commerce penetration testing services that assures zero false positive report generation through a comprehensive scan that is capable of running more than 3000 tests. The reports are vetted by expert pentesters who also provide remediation assistance. The shopping web store pentesting tool is capable of testing for compliances like GDPR, HIPAA, PCI-DSS, and ISO 27001.
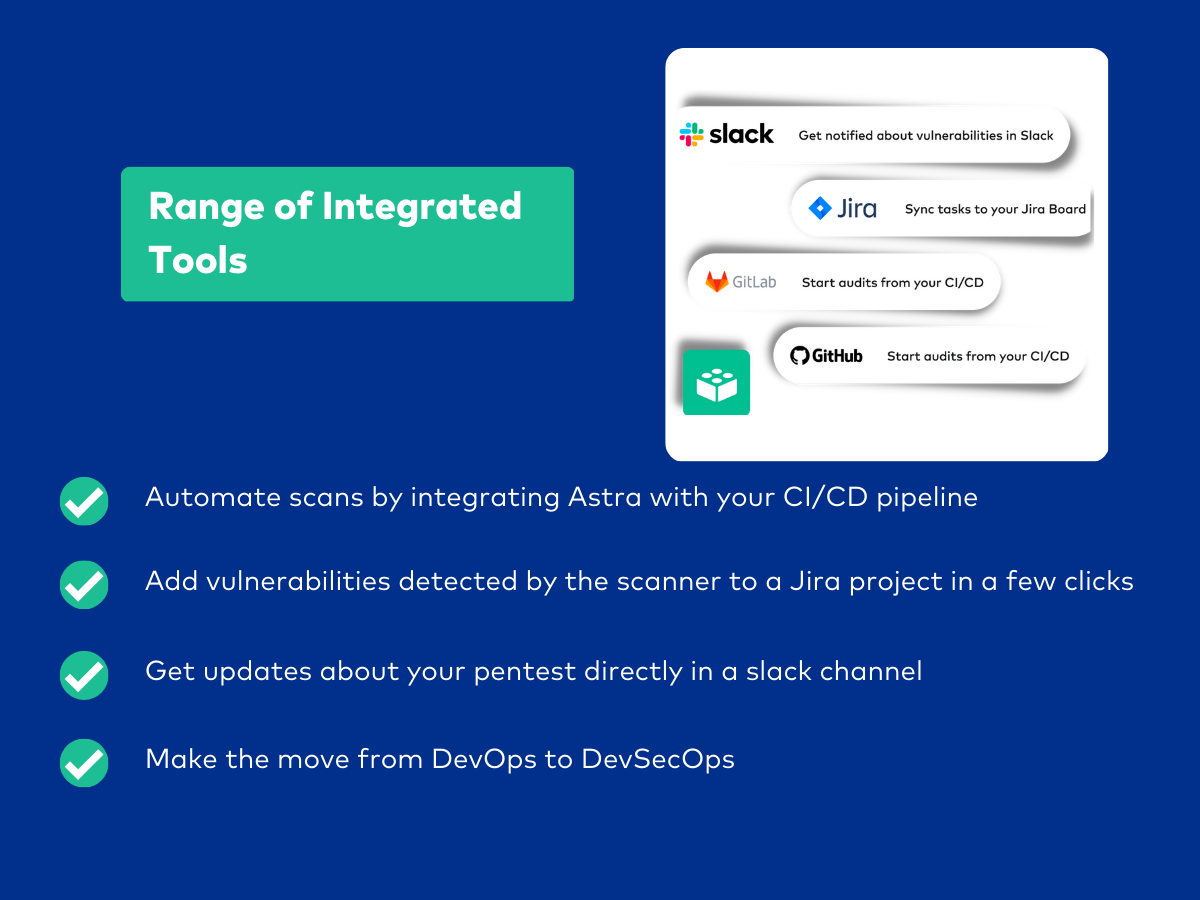
Besides pen testing your web store, Astra also provides penetration testing services for firewalls, networks, cloud environments, mobile apps, and APIs.
Features:
- Platform: Online
- Scanner Capacity: Unlimited continuous scans
- Manual pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability management: Comes with dynamic vulnerability management dashboard
- Compliance: Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: Starting with $199/month & $1,999/yr
Pros
- Provides gap analysis.
- Rescanning is a must after remediation.
- Provides publicly verifiable certificate.
- Ensures zero false positives.
- Detects business logic errors and scans behind the logins.
Cons
- Could have had more integrations.
- Does not provide free trials.
2. SQLmap
SQLmap is yet another important open-source tool for penetration testing E-commerce websites. It is the best tool for finding SQL injection vulnerabilities through thorough scans of web applications of your digital stores. The found SQL injections are exploited automatically and are popular for various database servers like Microsoft, MySQL, IBM, Oracle, and more.
Features:
- Platform: Windows, Linux
- Scanner Capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: No
- Price: Open source
Pros
- Open-source online website penetration testing tool
- Supports servers like MySQL, and Microsoft Access.
- Automated methods of finding various types of SQLs.
Cons
- No graphical user interface.
3. OWASP Zed Attack Proxy
ZAP is one of the best online E-commerce pentesting tools available that is open-source and provided by OWASP. It can be used for Linux, Microsoft, and Mac systems to run penetration tests on web apps of e-commerce stores to detect a variety of flaws.
Features:
- Platform: Windows, Linux, MacOS
- Scanner Capacity: Web application security testing, network ports, and API testing
- Manual pentest: Yes (Used by experts to carry it out)
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: OWASP
- Price: Open-source
Pros
- Sends automated alerts after crawls and scans
- Perfect for beginners and experts alike.
- Free online penetration testing tool.
Cons
- Can be slow.
- Reports can be cluttered and long.
Conclusion
Thus, penetration testing bolsters an organization’s reputation by proactively preventing security breaches, enhancing overall security posture, protecting financial transactions, and fostering a culture of security awareness. Moreover, by identifying vulnerabilities proactively, E-commerce penetration testing helps prevent data breaches and maintains compliance with industry and geographical regulations
As the E-commerce landscape continues to thrive, pentesting remains an essential strategy for securing this dynamic and invaluable digital ecosystem.
FAQs
How much does E-commerce penetration testing cost?
In 2023, the average cost of E-commerce penetration testing ranges from $2,500 to $50,000. However, the specific price can vary significantly depending on the complexity of the website, its size, and the depth of testing required.
How long does an E-commerce pentest take?
The duration of an e-commerce penetration test can vary significantly depending on the complexity of the platform and specific goals. Typically, it can take anywhere from a few days to a few weeks to thoroughly assess and secure an e-commerce website or application.
















