The number of devices, systems, and assets that are reliant on the internet is increasing by the day. From the POV of an attacker, this is a gold mine.
With each system that is connected to the cyber world comes a wide array of vulnerabilities that can be exploited, no matter how many precautions and security measures are in place.
This article will answer the question “what is vulnerability?” in detail. It included sections on different types of vulnerabilities, categories, major reasons for their arising, and a few examples among other sections. Let’s dive in!
What Is Vulnerability?
A vulnerability is a weakness or a flaw in an IT, network, cloud, web, or mobile application system that can make it susceptible to a successful external attack. Attackers often try to find various types of vulnerability in cybersecurity to combine and exploit a system.
Examples Of Security Vulnerabilities
Some of the most commonly seen vulnerabilities are listed below:
1. SQL Injections
Small codes like SQL queries are injected to manipulate systems and gain access through web applications. Once loopholes are identified, they send malware through vulnerable areas to obtain sensitive information.
2. Cross Site-Scripting
Cross-Site Scripting (XSS) can lead to sensitive information being stolen, such as login credentials, or malicious actions being performed on behalf of the user.
It allows an attacker to inject malicious scripts into web pages viewed by other users.
XSS attacks can occur when user input is not properly sanitized before being displayed on a web page.
3. Misconfigurations
One major vulnerability in cyber security that leads to big data breaches in cloud platforms, web applications, and more. Misconfigurations refer to any glitches or gaps in the security measures adopted that can lead to leaving valuable information virtually unprotected.
These misconfigurations can generally include a lack of proper access management, and even security group misconfigurations. Not having proper access restrictions in place can lead to individuals gaining access to unauthorized sections of data and applications thus putting the entire system in danger.
4. Broken Authentication and Authorization Measures
Broken authentication and authorization measures and reusing old passwords, and writing them down, can all leave the assets vulnerable to exposure.
Wrongful, previous employee authorizations can also lead to breaches occurring. Not having multifactor authentication measures deployed is a major cause of concern regarding vulnerabilities.
5. Cross-Site Request Forgery
Cross-Site Request Forgery (CSRF) allows an attacker to trick a user’s web browser into making unintended actions on a website, such as making purchases or changing account information.
A malicious link or form that looks legitimate to the user is received, but when clicked, it sends a request to the website using the user’s already established session.
Different Types of Vulnerabilities
Different types of vulnerabilities that can be exploited by hackers to gain access include:
1. Flaws
A flaw can be defined as functionality that was placed unintentionally within the system. It results from poor design or mistakes that are made during development.
They can go undetected for quite an extended period of time and most of the vulnerabilities that are discovered nowadays belong to this category.
Such flaws if discovered by the wrong side of people can be sold and brings in hundreds of thousands of pounds.
2. Zero-day Vulnerabilities
Zero-day vulnerability in cybersecurity is any kind that has recently been discovered and is not publicly known. They are used by more experienced attackers to carry out sophisticated attacks on systems.
Once they are publicly known, they immediately become a valuable commodity for carrying out repeated attacks. Thus, zero-day vulnerabilities pose a severe threat to systems like networks and or computers that haven’t had the relevant software patches or software updation applied to them.
The ability of attackers to find and exploit such vulnerabilities depends on the technical complexity of the vulnerability and their prowess in hacking.
What Are Zero-Day Exploits?
These are exploits that make use of a relatively unknown vulnerability in cybersecurity. Until such a vulnerability is patched, people with malicious intent can make use of the vulnerability to exploit the system that is affected by it.
Day zero in this scenario refers to the day invested party learns of the vulnerability and works towards patching it.
3. Features
Features are an intended function that is misused by hackers to gain access to areas they shouldn’t be able to access.
These features may be introduced to improve user experience and may succeed in that, however, they can also be exploited by attackers.
4. User Error
User errors are those that are introduced through the user’s practices, such as setting weak passwords, enabling vulnerable features, failing to fix flaws, or more.
They compromise the integrity of a well-designed system that was intended to reduce vulnerability in cybersecurity.
Such errors are even applicable to cyber-aware individuals who can be persuaded into giving up credentials through social engineering attempts.
Different Categories Of Vulnerabilities
Vulnerabilities detected by managed vulnerability scanning services (MVSS) can also be divided into different categories based on the systems they are present in. It includes:
1. Hardware Vulnerabilities
These are issues that plague the physical infrastructure of the system and they can range from humidity to poor security and everything in between.
Dust, natural disasters, poor encryption, and hardware vulnerabilities are some examples. Hardware security is a part of physical security as it encompasses the assets that need to be protected.
2. Software Vulnerabilities
Vulnerabilities within the software or an application include injections, insufficient testing, flaws in the design, and memory violations among others.
3. Network Vulnerabilities
Vulnerabilities within the network include man-in-the-middle attacks, lack of protection for communication lines, lack of default authentication, or even having a network architecture that isn’t secured properly.
4. Personnel
Personnel vulnerabilities refer to vulnerabilities caused by the personnel aka the users or employees. It includes having no security awareness, not being trained in good security practices, setting weak passwords, or not changing passwords regularly, and also divulging credentials or sensitive information to questionable sources or individuals.
Having a better understanding of the different types and categories of vulnerabilities, let us now jump in and understand what causes such vulnerabilities in the first place.
Major Reasons For Vulnerabilities
A vulnerability in cybersecurity is brought up due to some common yet, reasons that aren’t entirely unavoidable. Some of them include:
- Complex Systems
Systems that are extremely intricate are more prone to vulnerabilities. Vulnerabilities that plague a complex system could be misconfigurations, flaws, or even unintended access.
- Commonality
Multiple systems that have similarities in code, software, OS, and even hardware increase the chances of attackers being able to use publicly known vulnerabilities to try and exploit other systems that share the same traits.
- Connectivity
Connectivity is a blessing and a curse in the extremely cyber-world we live in today.
The more connected a system is to the internet, the higher the chances are that the system, be it a network, computer, phone, application, or cloud infrastructure is more susceptible to vulnerabilities.
- Weak Passwords
Placing weak passwords, or not changing passwords regularly can result in the exposure of assets leaving them vulnerable to data breaches through brute force attacks.
- Software Bugs
These are vulnerabilities or bugs that are left in place intentionally or unintentionally. When discovered patches are released to cover such vulnerabilities, however, if a user fails to update their software, it leaves them vulnerable due to the unpatched bug.
- OS Flaws
Flaws that are present in the operating system are another reason that would allow any malicious user to gain access and easily inject malware, and viruses to obtain data, or even money.
- People
Lastly, one of the biggest reasons for the presence of vulnerabilities is ourselves. People are often tricked by using social engineering techniques that manipulate them into giving up confidential information like credentials. Credentials obtained this way can easily be used to gain access and steal data.
Methods to Find Flaws
Commonly used methods for flaws or vulnerabilities include vulnerability scans and penetration tests. Each has its own merits and demerits as well as different types that can be carried out among them.
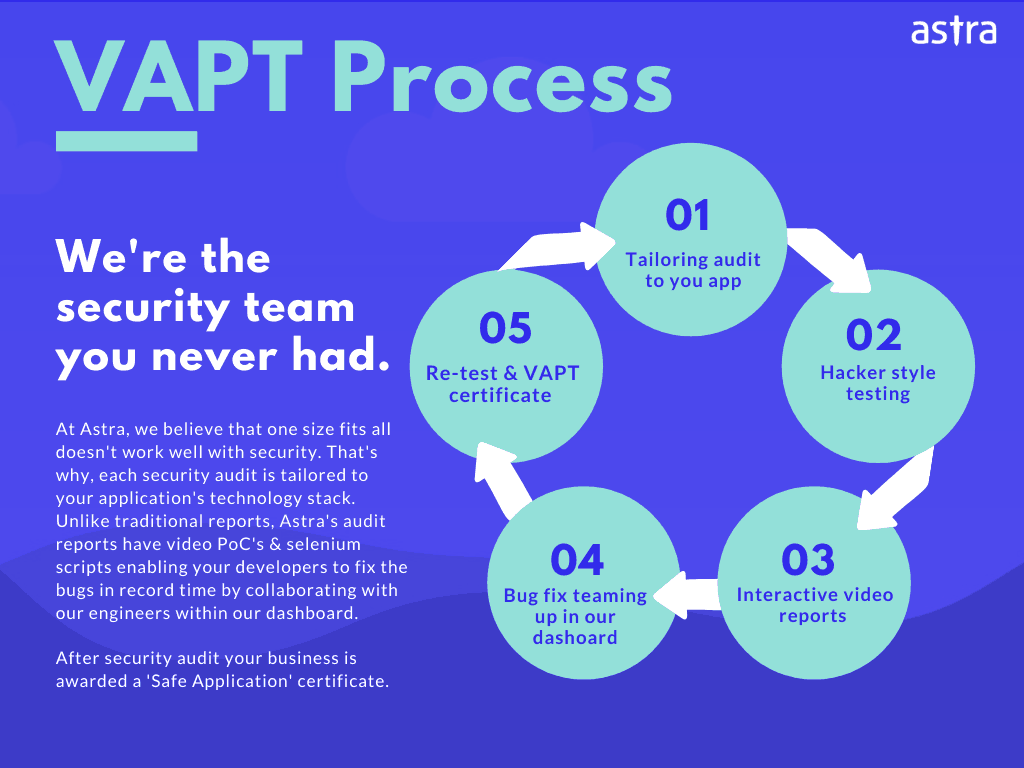
1.Vulnerability Scans
Vulnerability scans refer to the process of analyzing a system’s security using a scanning tool to find any vulnerabilities that may be affecting its security. A vulnerability scan is usually carried out using automated vulnerability scanners.
Its pros are that it can be carried out as many times as one needs as vulnerability scans are generally faster in process. However, it is to be noted that they are not as comprehensive are can be prone to false positives rising.
Generally, vulnerability scans are of types, that is:
- Scans Behind Logins
Scans behind logins are carried out with access to the internal system using credentials. Such a scan is more comprehensive and can indicate the vulnerabilities present in operating systems, installed software, and even security patches that are missing.
- Unauthenticated Scans
Unauthenticated scans imitate the style of a hacker and aim to analyze the exterior security posture of a system. They can result in false positives which can be weeded out by experts who are analyzing the system. Such a scan can also help in the identification of vulnerabilities that could result in a data breach or leak.
2. Pentests
Penetration tests refer to the process of exploiting vulnerabilities that are found using a vulnerability scanner. It is carried out by ethical hackers who are hired to try and break into the target system using any potential vulnerabilities found.
An exploitable vulnerability showcases a compromised security system for the target. Once the penetration test is completed, a report is generated with the findings of the pentest as well as remediation measures.
The boons of a pentest include that it is significantly more comprehensive than a vulnerability scan and provides more details into the impact of vulnerability if it is exploited. However, it is wise to note that penetration tests are more expensive and time taking when compared to vulnerability scans.
Pentest can be carried out manually or using automated tools.
- Manual Pentests
Penetration tests that are carried out by qualified expert ethical hackers are known as manual pentests. These are more comprehensive in terms of vulnerabilities discovered and it has a lesser chance of having false positives.
- Automated Pentest
Automated pentest is carried out using penetration testing tools. Such software is capable of detecting vulnerabilities and attempting to exploit them using known pre-programmed techniques.
Importance Of Vulnerability Management
Here are some of the reasons why efficient management of vulnerabilities is crucial for a secure system.
- Vulnerability Scanning for Vulnerabilities
Making use of a comprehensive vulnerability scanner makes vulnerability management easier and more efficient. Such a scanner should be able to continuously scan and detect even the most minute of vulnerabilities.
A vulnerability scanner with an extensive vulnerability database ensures that all vulnerabilities are rightly detected and assessed. Another important aspect that makes vulnerability management important is behind-the-login scans, detection of logic errors, weeding out any false positives as well as ensuring that are no false negatives.
- Helps in Vulnerability Identification
An important part of vulnerability management comes in the timely identification of vulnerabilities using a capable scanner. Vulnerability identification is one of the first steps in successfully managing a vulnerability through remediation.
- Accurate Prioritization of Vulnerabilities
Yet another crucial step in vulnerability management, the discovered vulnerabilities are prioritized based on risk data and CVSS scores so that the critical vulnerabilities can be fixed by you immediately.
- Remediation Of Vulnerabilities
Once the vulnerabilities are assessed according to the risk they pose, it is now time to respond and fix each flaw found. This is done based on the data from the risk assessment.
Based on the threat level there are 4 general measures that can be opted for to create a viable and healthy security solution for the cloud. This includes patching, shielding, mitigation, and taking no action.
- Rescanning For Vulnerabilities
Once the major steps of identification, evaluation, and remediation are carried out, the final step is to avail of a re-scan. Rescans ensure the security system of the asset is free from all the initially found flaws and that they have been appropriately managed or fixed.
Doing so is akin to going the extra mile in the name of safety and truly ensures the safety of your organization’s service. It also increases your reputation as a safety-conscious provider and increases trustworthiness.
Common Databases for Vulnerabilities
There are several commonly used databases for vulnerabilities:
- Common Vulnerabilities and Exposures (CVE): A standardized, globally recognized database of information security vulnerabilities and exposures.
- National Vulnerability Database (NVD): A comprehensive collection of security vulnerabilities, provided by the National Institute of Standards and Technology (NIST).
- Microsoft Security Updates: Microsoft maintains a database of security vulnerabilities and updates for its products.
- OWASP Top 10: A list of the top 10 most critical web application security risks, maintained by the Open Web Application Security Project (OWASP).
- Common Vulnerabilities Scoring System (CVSS): A framework for scoring and rating the severity of vulnerabilities, based on their impact and ease of exploitation.
These databases provide information about known vulnerabilities and can be used by organizations to assess the risk of their systems and prioritize their remediation efforts.
Are All Vulnerabilities Exploitable?
The likelihood of a vulnerability being exploitable depends on several factors such as the level of access required, the complexity of the attack, and the presence of other security controls.
Not all vulnerabilities are exploitable. Additionally, some vulnerabilities may be considered theoretical and may not have a practical exploit or may be difficult to exploit in practice.
Therefore, it is important to assess the risk of each vulnerability and prioritize their remediation based on the potential impact and likelihood of exploitation.
Differences Between Vulnerabilities and Risks
A vulnerability is a weakness or flaw in a system or application that can be exploited to carry out an attack. They arise from coding errors, misconfigurations, or design flaws.
Risks, on the other hand, refer to the potential for harm or loss associated with a vulnerability. Risks are the likelihood of a vulnerability being exploited and the impact it would have if exploited.
Simply put, vulnerability is the actual issue that affects a system whereas risks refer to the impact and potential consequences that are caused by the vulnerability and the possibility of its exploitation.
Conclusion
This article has elaborately and extensively answered the question of what is a vulnerability. It has mentioned the major reasons that cause vulnerabilities, different types of vulnerabilities as well as their categorization based on the systems they affect.
Now that you’re geared up with all the knowledge regarding vulnerabilities, test your assets to detect and be rid of vulnerabilities with ease like never before.
















