An average website faces 94 attacks every day, and only 26% of all data breaches are attributed to web application hacks. The cyber threat landscape has worsened over the last couple of years, and keeping a continuous tap on all aspects of cyber security can be overwhelming. It is an established fact that frequent penetration testing is the best way to counter this, regardless of the industry you are operating in. But then there is the debate around automated and manual penetration testing slowing the decision down for you.
You need a combination of automated and manual penetration testing to get a complete picture of your organization’s security posture along with actionable insights to fix and prevent the issues.
Now that we have picked an answer and put the debate aside, let us understand why a company needs both manual and automated penetration testing. In the course of this article, you will learn what a penetration test is, what are the different approaches to it, how automated and penetration testing serve your purpose, and how you can choose the perfect pentest partner.
What is Penetration Testing?
Penetration testing is the process of evaluating the security of a system by finding and exploiting vulnerabilities with the help of hacker-like tactics.
It is analogous to finding the ways of breaking into a house, then assessing how many rooms were accessible from each break-in point, how easy it was to break, and how much worth of valuables could be stolen in course of the operation.
The main difference between a hack and a penetration test is that hackers break in to steal actually cause harm, and penetration testers make you aware of the exploitable flaws in your security and help you fix them.
What is Manual Penetration Testing?
Manual penetration testing is the process where security engineers manually perform penetration testing to assess the security posture of a system. They use hacker-style techniques to find ways to break into your system, evaluate the vulnerabilities in terms of impact and exploitability, and prepare a report documenting the vulnerabilities and the way to reproduce and fix them.
This is what a manual penetration testing process looks like
- The secuirity experts prepare a running profile of attack methods that can be used against a target system.
- They prepare test cases and execute them in a way that detects software vulnerabilities without affecting the business functionalities that might be active on the target system.
- After that they customize attack payloads for specific applications and execute them while taking note of the environment.
- They perform an analysis of the data captured through the operation to attain vulnerability patterns, interpret the results, and prepare a plan for remediating the issues.
Also Read: Top 6 Web Pentest Tools You Should Not Miss in 2022 | Top 5 Software Security Testing Tools in 2022 [Reviewed]
What is an Automated Penetration Testing?
Automated penetration testing refers to the scanning of your systems for common vulnerabilities with the help of automated tools and processes. It is a faster, and comparatively cheap process that can give you a quick analysis of your website’s or network’s vulnerability status.
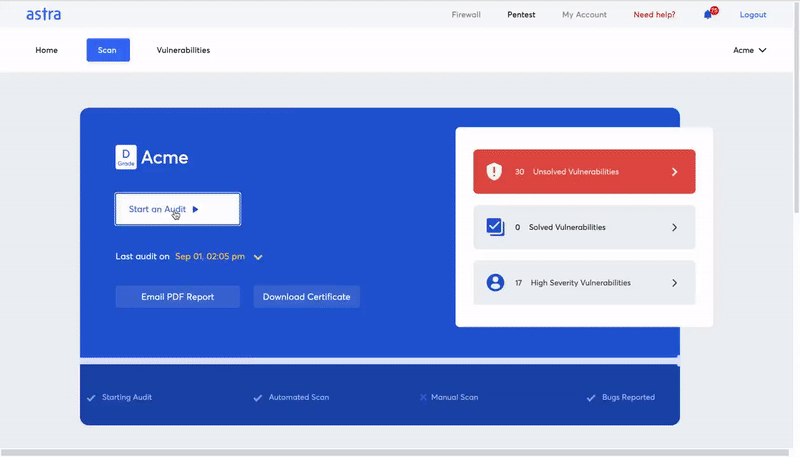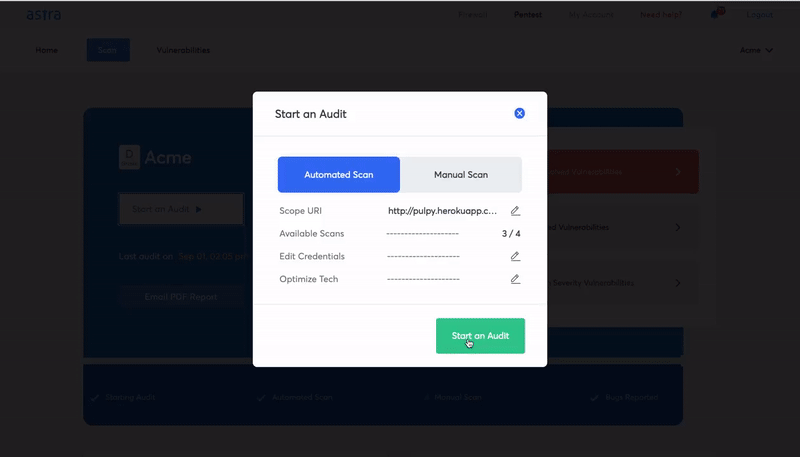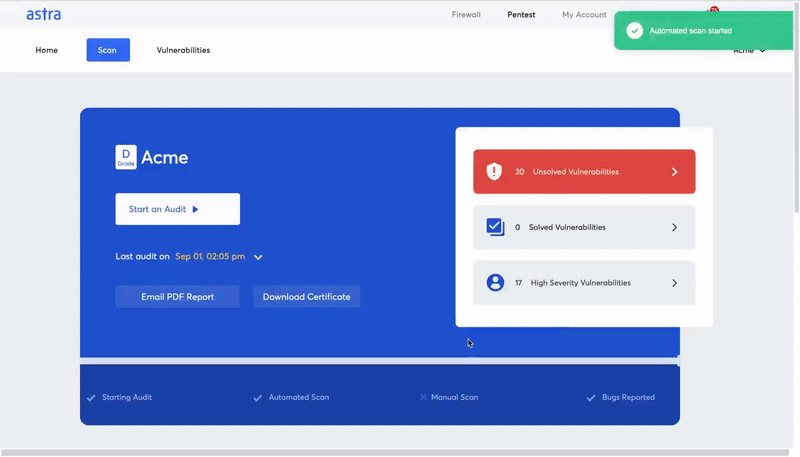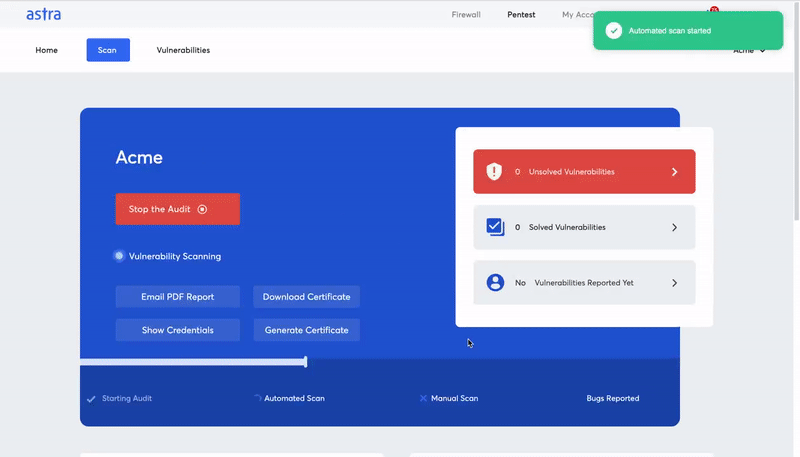
An automated penetration test or vulnerability scan produces results in minutes by checking your system for vulnerabilities by referencing a vulnerability database. It is perfect for a small business that does not deal with too much sensitive data and runs a simple application.
Read also: Penetration Testing – What, Why & How [A Complete Guide] | API Penetration Testing: What You Need to Know
What are the advantages of manual penetration testing?
Manual penetration testing comes with a significant edge over vulnerability scanning or automated pentest. The foremost advantage is that it involves both automated tools and human intelligence increasing the depth of the penetration testing naturally. Let us look at some specific advantages.
- Zero False Positives: If you have dealt with vulnerability scanners, or if you are a security aware person in general, you would know how big a deal false positives can be. The real pain of false positives is felt by the developers wasting hours trying to fix an issue that does not exist.
Manual pentesters exploit each vulnerability to ensure that they are genuine issues. This saves you a lot of time and effort. This is one of the most important advantages of manual penetration testing.
- Deep and Exhaustive Testing: Automated vulnerability scanners have become really smart over the last decade with regularly expanding test cases. But let’s face the fact, they still miss vulnerabilities. You cannot have a definitive vulnerability report without a manual pentest. There are security errors like business logic errors that cannot be detected by an automated scanner. We will talk more about it later.
- A Thorough Pentest Report: Security engineers who have run a manual penetration testing of your systems can produce a detailed report with step-by-step guidelines for you to reproduce and fix vulnerabilities. Moreover, you get their assistance while trying to fix the issues. Reading, interpreting and acting upon a pentest report is a pretty tenuous task even for the IT professionals, a little human assistance goes a long way in making the process fruitful.
Also Read: Continuous Penetration Testing: The Best Tool You’ll Find in 2022
- Compliance: Some compliance regulations like the PCI-DSS require manual penetration testing. What Are Some Key Differences Between Automated and Manual Penetration Testing?
| Automated Penetration Testing | Manual Penetration Testing |
|---|---|
| Automated penetration testing or Vulnerability Scanning is an automated process of detecting vulnerabilities performed with penetration testing tools. | Manual penetration testing or simply penetration testing is a meticulous assessment of your security infrastructure, performed by competent security researchers. |
| It is quick to execute and saves a ton of time. | Manual pentests can take days on end to complete. |
| It is a low-effort & efficient method of scanning your networks for vulnerabilities. | It requires proper planning and preparation to conduct a full-blown manual penetration test. |
| It does not provide deeper insights into the vulnerabilities. | It provides detailed & deeper insights into the vulnerabilities. |
| It discovers common security misses like a lacking update, flawed permission rules, configuration flaws, with amazing efficiency. | It detects acute flaws that are often missed by a scanner like business logic errors, loopholes, coding flaws, etc. It also involves exploiting these vulnerabilities to gauge the impact on the system. |
| It can be done frequently without much preparation & planning. | It requires effort & time, thus can't be done frequently. |
What Are Some Flaws that Require Manual Penetration Testing to Detect?
While automated penetration testing tools have come a long way in terms of speeding up the process there are certain areas that still require human attention to detail. When it comes to rooting out complex vulnerabilities that do not necessarily show up on vulnerability scans and ensuring zero false positives, manual penetration is irreplaceable.
Here are some vulnerabilities that require manual pentesting to detect
- DOM-based cross-site scripting
- Blind SQL injection
- Business logic errors
- Cross-site request forgery
- Template injection
- Broken access control
An experienced security expert can catch anomalies that may appear to be legitimate to an automated scanner. A lot of difficult vulnerabilities may be found when pentesters follow their instinct and use creative ways to examine in an unexpected direction.
On top of everything, the support you get from manual pentesters in terms of reviewing and remediating vulnerabilities is quite indispensable.
Read also: Comprehensive Guide on Website Penetration Testing
The Advantages of Using Astra’s Pentest
The pentest suite by Astra Security is a complete and elegant solution to your penetration testing needs. The security team at Astra ensures zero false positives by manually exploiting the vulnerabilities. The pentest report produced by them is as thorough as it gets but at the same time, it is easy to follow, thanks to the step-by-step guides, and video POCs. You get best-in-class human support, in case the developers hit a roadblock while remediating the issues. The scope of collaboration between your team and the security experts is ample and smooth.
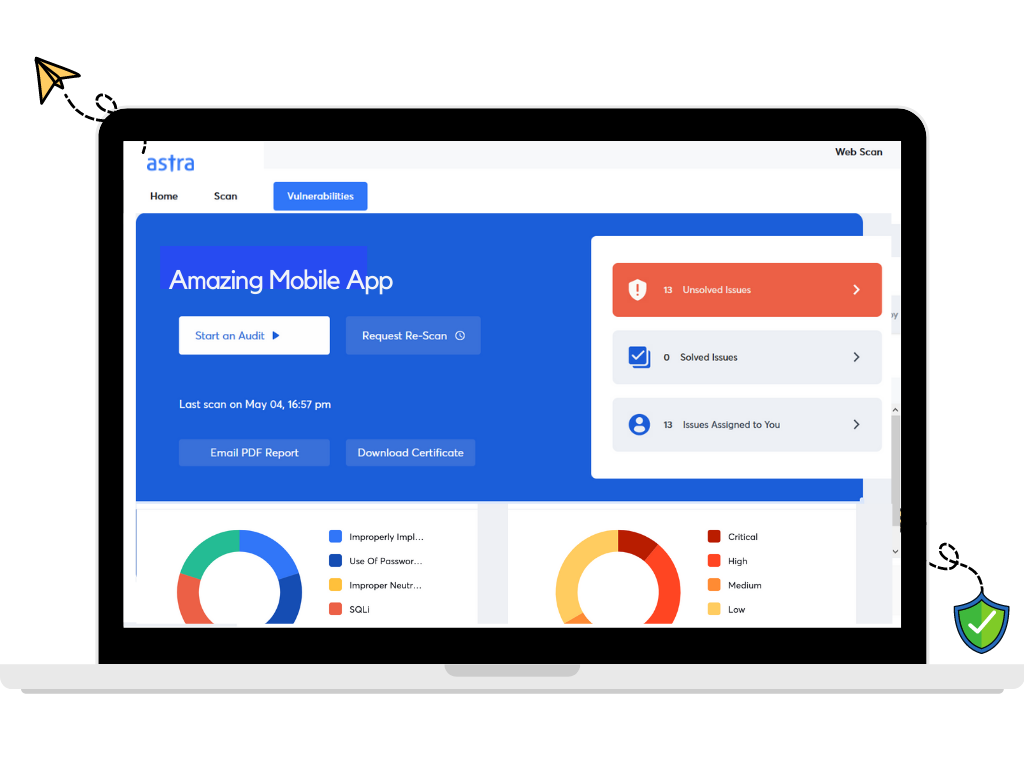
Here are some key features that set Astra’s Pentest apart
- 8000+ tests to ensure no vulnerability is left unchecked.
- Zero false positives ensured by manual penetration testing.
- Interactive dashboard to visualize vulnerability analysis, assign vulnerabilities to team members, and comminicate with security experts.
- Continuous Scanning with the help of CI/CD integration. You do not have to visit the pentest dashboard to start scans after product updates. You can just automate it.
- Scan behind logged-in pages without manually authenticating the scanner every time the session times out.
- Pentest compliance reporting helps you understand the position of your company in terms of compliance requirements, in real-time.
- A thorough pentest report eases up the process of remediation.
- Best-in-class support from security experts to help the developers interpret and act on the report.
- A publicly verifiable certificate helps you build trust among customers.
A combination of automated and manual penetration testing is a necessity for companies with internet-facing assets and sensitive information. Astra’s pentest makes it super simple for you to evaluate the security posture of your website, applications, or network.
Conclusion
The depth and effectiveness of manual penetration testing cannot be matched by an automated pentest, then again, the speed and scalability of automated tests are incredible. A combination of both received from a perfect pentest partner is what you need.
Your systems are most likely vulnerable to attacks, the sooner you get a pentest, the better your chances are of avoiding the nuisance of getting hacked. Find the right pentest firm to collaborate with and get secure.
















