Software security testing tools are one of the best ways to prevent and analyze network and application layer attacks. They are commonly used to identify vulnerabilities in both applications and networks. Network security testing tools aim to avoid unauthorized access and network-level attacks. Whereas, application security tools are designed to test an application against layer 7 attacks.
List of the top software security testing tools
- Astra Pentest Platform
- NMap
- WireShark
- OpenVAS
- Metasploit
- Nikto
- OWASP ZAP
- Kali Linux
- Rapid7
- Burp Suite
There are certain things that make a software security testing tool better than others. This post is about helping you understand those things so that you can make an educated choice. Of course, we will talk about the top security testing tools in some detail, starting with the following table.
| Security Testing Tools | Key Features |
|---|---|
| Astra Pentest Platform | Continuous pentesting, CI/CD integration, scan behind login, cloud pentest |
NMap | Network exploration, port scanning, network mapping |
| WireShark | Packet analyzer, network troubleshooting, protocol analysis |
| OpenVAS | Vulnerability scanning |
| Metasploit | Helps you write, test, and execute exploit code |
Top 10 software security testing tools
Cybercriminals are constantly working on new ways of breaching network security and stealing valuable information, which is why software security testing tools are becoming common. Also, you need to be thorough in your network security testing and find vulnerabilities in networks before hackers do. There are a lot of tools out there for network security testing, but some of the best are listed below.
1. Astra Security

Features
- Platform: Online
- Scanner Capacity: Unlimited continuous scans
- Manual pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability management: Comes with dynamic vulnerability management dashboard
- Compliance: Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: $199/month
Astra’s Network Security Solution is a unique product of Astra Security, a comprehensive security assessment of your network that can help you find and fix security risks. Astra’s solution is a solution that helps you to identify the security gaps in your network and helps you in plugging the holes.
The Astra Network Security Solution is the most comprehensive solution to perform a complete network security assessment. The solution scans and checks your network to identify the network devices, network ports, and network protocols to find out the vulnerabilities in your network and help you fix the vulnerabilities in a timely manner.
What is best?
- Connects with your CI/CD pipeline
- Offers continuous scanning with regularly updated scanner rules
- Ensures zero false positives
- Helps with rapid prioritization and remediation of vulnerabilities
What could have been better?
- It doesn’t offer a free trial
Verdict
Astra Security essentially replaces 3 services with one platform – a vulnerability scanner, manual pentest, and vulnerability management. On top of that, security experts go the extra mile to help you remediate issues quickly. It is like having a security team of your own. Also, full points for 24/7 chat support and customer service. Overall, it’s an incredible application penetration testing tool in any price range.
2. NMAP
Features
- Platform: Linux, Windows, MacOS
- Scanner Capacity: Usually scans the 1000 most popular ports of each network protocol
- Manual pentest: NMap is actively used for network mapping and port scanning. These are parts of the manual pentest effort.
- Accuracy: Occasionally shows false positives and faulty insights
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
Network Mapper, or Nmap, is an open-source utility for network exploration, security auditing, and network discovery. It was designed to rapidly scan large networks, although it works fine against single hosts.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
While Nmap was developed for UNIX-based operating systems, it also runs on Windows, and there are also versions available for most other major operating systems.
What is best?
- NMAP is a powerful tool
- Capability of mapping a very large network with thousands of ports connected to it.
What could have been better?
- Need extensive knowledge to use.
- Used by malicious hackers as well as security experts.
Verdict
NMap has been around for 26 years and it is still the gold standard when it comes to network penetration testing tools. It is something every ethical hacker needs in their arsenal.
3. Wireshark
Features
- Platform: Unix, Windows. Needs libraries like Qt, GLib, & libpcap to run
- Scanner Capacity: Captures live packet data from a network interface
- Manual pentest: Useful tool for pentesting
- Accuracy: Fairly accurate
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Wireshark can be used to capture and interactively browse the contents of network traffic.
Wireshark is also commonly used to analyze data from a trace file, generally in the form of a pcap (the file format of libpcap). Wireshark has a GUI and comes in both 32-bit and 64-bit versions.
What is best?
- Capture live data packet from network interfaces and analyzes it in real-time
- Available for free
What could have been better?
- It does not run from outside a network
- Cannot perform packet injection
Verdict
The tool is easily one of the gold standards for an open-source network protocol analyzer.
Also Read: Top Penetration Testing Software & Tools Pros Use
4. OpenVAS
Features:
- Scanner Capacity: web applications, network protocols
- Manual Pentests: No
- Accuracy: False positives possible
- Scan Behind Logins: Yes
- Compliance: No
- Expert Remediation: No
- Price: Open-source
OpenVAS is a vulnerability scanner that can perform a complete vulnerability scan of the network infrastructure. OpenVAS is an international project that is used by many organizations all over the world. It is available for free and can be used with commercial products.
OpenVAS tool is owned by Greenbone and the paid solution is called Greenbone Security feed while the free one is called Greenbone Community feed.
What is best?
- Automated vulnerability scanning is quick and efficient
- Freely available network vulnerability scanning tool.
- Constantly updated
What could be better?
- Could be difficult for beginners to make use of.
- Automated causes false positives to appear.
Verdict
The tool is a good start to software security testing and is scalable since if customers want more features, they provide a paid version.
5. Metasploit
Features
- Platform: Unix (including Linux and MacOS), Windows
- Scanner Capacity: N/A
- Manual pentest: Metasploit contains an assortment of tools that can be used for pentesting
- Accuracy: N/A
- Vulnerability management: No
- Compliance: Indirectly relates to compliance reporting
- Price: Free
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is open-source, free, and available to the public.
The project provides information about security vulnerabilities used by penetration testers during security audits and network administrators to ensure the correct configuration of the network’s devices.
What is best?
- It is a powerful framework.
- An assortment of penetration testing capabilities.
What could have been better?
- Has a steep learning curve
- Used by hackers
Verdict
With listeners, encoders, and post-exploit code, Metasploit is a very powerful tool for ethical hacking.
6. Nikto
Features:
- Platform: Linux
- Scanner Capacity: Web applications, servers
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: No
- Price: Open-source
Nikto, an open-source penetration testing software is capable of conducting detailed tests on web servers with a capacity to identify nearly 7000 malicious files and applications.
This includes over 6700 potentially dangerous files/programs, checks for outdated server versions, and version-specific problems on over 270 server versions.
Server versions like Apache, MySQL, FTP, ProFTPd, Courier, Netscape, iPlanet, Lotus, BIND, MyDoom, and more. Key features include scans for 6000+ vulnerabilities and the detection of version-specific problems.
What is best?
- It is freely available to the public for use.
- Available in Kali Linux.
What could have been better?
- Does not have a community platform.
- Does not have a GUI.
Verdict
Yet another open-source penetration testing tool, Nikto is a must-have with its extensive vulnerability detection for various server-specific flaws.
7. Zed Attack Proxy
Features:
- Platform: Windows, Linux, MacOS
- Scanner Capacity: Web application security testing, network ports, and API testing
- Manual pentest: Yes (Used by experts to carry it out)
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: OWASP
- Price: Open-source
Zed Attack Proxy or else known as ZAP is an open-source penetration testing software offered by OWASP that can detect a variety of vulnerabilities within web apps.
It can be used for Linux, Microsoft, and Mac systems to run penetration tests on web apps to detect a variety of flaws.
One of the best open-source penetration testing tools out there, ZAP supports a lot of pentesting activities that make it ideal for users.
What is best?
- Easy-to-navigate user interface
- Maintained by OWASP and is freely available.
- Easy to learn.
- Eligible for beginner and security experts alike.
What could be better?
- Hard to set up the tool.
- Not convenient compared to other tools.
- Some features require extra plugins.
Verdict
ZAP by OWASP was built specifically with web application vulnerability detection in mind. This makes it an excellent choice for open-source web application pentesting.
8. Kali Linux
Features:
- Platform: Linux
- Scanner Capacity: Web applications, networks, APIs
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: No
- Price: Open-source
Kali Linux is a Debian-based platform designed for penetration testing provided by Offensive Security. Kali Linux offers a collection of tools that can be used for penetration testing.
Kali offers multi-language support, allows for the complete customization of Kali ISO, and has over 600 penetration testing tools available within it.
It has a trustworthy operating system, with various accessibility features, and supports various single-board systems like Raspberry Pi.
The platform comes with the latest patches and works with any number of wireless devices. It offers a forensic mode to disable features that can change data in the system that is analyzed.
What is best?
- Open source tool.
- A large collection of online pentest tools.
- High-level stability.
What could be better?
- Not recommended for beginners.
- Installation can be tedious.
- Difficult user-interface.
Verdict
Kali Linux is a perfect and must-have suite for any skilled pentester and its numerous pros certainly outweigh the cons with ease due to the wide, veritable range of tools available with it.
9. Rapid7
Features:
- Platform: Linux, Windows, macOS
- Scanner Capacity: Cloud and Web Applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: Yes
- Compliance: CIS, ISO 27001
- Price: $175/month
Rapid7 is one of the top penetration testing firms with their resources focused on empowering protectors to build solid and sustainable security.
Their pentest services are based on a deep understanding of methods applied by hackers to attack your systems.
They collaborate with the global security community to bring about better, more prolific security solutions, faster. Their services include detection and response, security scanning, and vulnerability management.
What is best?
- Great for finding hidden vulnerabilities
- They maintain top-notch threat intelligence
- Scalable security solution.
What could be better?
- Users have reported issues with functionality and customer support
- The devices that are scanned have to be removed manually
Verdict
Rapid7’s pentesting services are just the icing on the cake along with its vulnerability management services. They have a great threat intelligence program.
10. Burp Suite
Features:
- Platform: Windows, macOS
- Scanner Capacity: Web applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: PCI-DSS, OWASP Top 10, HIPAA, GDPR
- Price: $449/per user/per year
Burp Suite is one of the popular manual penetration testing tools that is very useful for ethical hackers, pentesters, and security engineers. Let us explore some of the tools included in Burp Suite.
- Spider: It is a web crawler used for mapping the target application. You can create an inventory of all the endpoints, monitor their functionalities, and look for vulnerabilities with Spider.
- Proxy: A proxy is placed between the browser and the internet to monitor, and modify the in-transit requests and responses.
- Intruder: It runs a set of values through an input point and lets you analyze the output for success, failure, and content length.
These aside the suite includes Repeater, Sequencer, Decoder, Extender, and some other add-on tools.
Burp Suite has both a free community edition and a commercial edition.
What is best?
- Has both open-source and commercial editions.
- User-friendly interface.
- Best internal penetration testing tools.
What could be better?
- Requires better integrations.
- The commercial product is pricey.
- The free version has lesser features.
Verdict
BurpSuite is undeniably a gold standard in terms of penetration testing tools and it comes in both a free and commercial plan making it very accessible.
16. Acunetix
Also Read: Continuous Penetration Testing: The Best Tool
What is Software Security Testing?
Software Security Testing is an essential part of the security process as it ensures that all systems and resources accessible from outside the organization are safe. It is recommended to do regularly scheduled software security testing to keep up with the latest threats and vulnerabilities.
Software security testing, also known as Software penetration testing, is a process of testing a software application for security loopholes and finding vulnerabilities that malicious actors can exploit.
While there are many types of pentest, such as vulnerability scanning, functional testing, and IDS/IPS testing, most of them focus on finding flaws in the security of the overall infrastructure.
Reading Guide: Network Security Audits
Why is Software Security Testing important?
Software security testing enables organizations to keep abreast of the latest security threats and vulnerabilities. Audited software helps organizations determine their current security posture and plan for the next stage of software security. Software security is a continuous process and not a one-time project.
Software security testing is performed to determine whether a network is vulnerable to attacks from the internet or the internal network. This testing includes a review of all software infrastructure and systems accessible from the internet.
The main goal of software security testing is to determine the level of risk that exists in an organization’s IT network. This testing is crucial because it can prevent the risk of your company’s data and systems being compromised.
Also Read: Top Penetration Testing Software & Tools Pros Use
Benefits of Software Security Testing Tools
Software security testing tools are an essential part of the information security plan. Software security testing tools are used to perform security testing on a network to identify and prevent security risks in the networks.
The results of the tests are analyzed to find any holes in the safety and to point out weaknesses in the existing security system. These security tools have proven to be very helpful in the network testing process.
Also, these security testing tools can increase IT security and keep data safe by identifying the weaknesses in a company’s network and pointing out the necessary improvements. It can also identify potential threats and recommend immediate action to prevent potential problems.
Also Read: A Complete Guide to Cloud Security Testing
5 Different techniques used to perform Software Security Testing
1. Network Scanning
The Network scanner is a potent tool to scan a network and get information about the network. The network scanning tool can monitor the network, identify the hosts connected to the network, and identify the services running on the network like FTP, HTTP, POP3, and SMTP.
The Network scanner also identifies the operating system running on the host and the version of the operating system.
2. Vulnerability Scanning
Vulnerability scanning is a network security process that detects and analyzes flaws in computers and computer systems and reports the information to administrators. This information helps plan security patches or upgrades. It can also help in determining the security status of a network.
Vulnerability scanners have been around for a long time. Still, they have been made more effective by using sophisticated techniques, such as fuzzing, and they are now considered an essential tool in supporting compliance with regulatory standards.
Also Read: Online Website Penetration Testing: A Complete Guide
3. Ethical Hacking
Ethical hacking is the practice of testing a computer system, network, or web application to find security weaknesses (holes) before a malicious hacker does. It is the surface area testing of a system, network, or web application. Ethical hacking aims to find security weaknesses before a malicious hacker does.
4. Password Cracking
Password cracking is of two types:
Dictionary Attack: This method uses a dictionary (a word list) to crack passwords. The word list has all the possible passwords. So the computer compares the password given by the user to the word list to find out the matching password.
Brute Force Attack: This method uses an automatic program to crack passwords. The program tries all possible combinations of characters until it finds the correct password. Brute force attack is a time-consuming process.
5. Penetration Testing
Penetration testing evaluates computer security by simulating an active attack on a computer system or network. Penetration testing is typically performed by ethical hackers, also known as white hat hackers, or by security professionals attempting to determine the extent of damage or risk before an actual attack.
Penetration testing differs from vulnerability scanning and compliance auditing in that the primary aim of penetration testing is to exploit potential vulnerabilities in a given target. In contrast, vulnerability scanning and compliance auditing are more passive tests.
Also Read: What is Automated Penetration Testing? Difference between Automatic & Manual Pentesting Software
How much does a Software Security Testing Tools Cost?
Security testing tools can be costly, and it depends on the tools you are using and the number of apps you are scanning, and a lot more factors that are usually discussed before signing a contract. A security scan should be conducted at least twice a year to check the security and ensure it is secure against threats. On average, the cost usually ranges from $100 to $500 per month.
3 things to know before buying a Software Security Testing Tool
With the number of different network security testing tools available, businesses are faced with a bewildering number of choices when it comes to selecting the best network security testing solution, and keeping that in mind, we have prepared a list of a few things to keep in a while buying a network security testing tool.
1. Ease of use and Friendly UI
One of the critical factors for organizations to choose a network security testing tool is the ease of use. Simple interface and easy-to-follow instructions are always appreciated. Even the most advanced tools are rendered useless when the user does not know how to use them. A good tool will have an easy-to-use interface, step-by-step instructions, and a detailed user guide.
2. Comprehensive scan report
Understanding the threats against your business is crucial when it comes to risk management. A comprehensive security testing report is essential to keeping your business safe. A comprehensive security testing report can uncover high-risk vulnerabilities, help you better understand your network, and help achieve compliance.
3. Updated with Latest Vulnerabilities
No automated security testing tool is perfect. Hackers are constantly finding and releasing new vulnerabilities. An automated network security testing tool should have an updated database of security vulnerabilities so that no vulnerability is left unnoticed.
Also Read: 7 Best API Penetration Testing Tools And Everything Related
Astra’s Pentest Solution: All in one Security Solution
No matter how big or small your company is, hiring a penetration testing company to protect your network and applications is vital. Hiring a good pen testing solution will not only protect your business but your data as well. Astra Security is an excellent solution for your business.
Astra Security has been in the industry for many years now; it offers multiple pen testing solutions, including Network, Web, API, Blockchain, and Cloud penetration testing.
The Astra Penetration Testing Solution is a “Next Generation” Penetration Testing software used by thousands of organizations worldwide. Astra’s pentest solution is well-known for its excellent vulnerability scanner with more than 3000 tests, making it a perfect choice for penetration testing.
Have a sneak peek at Astra’s Dashboard.
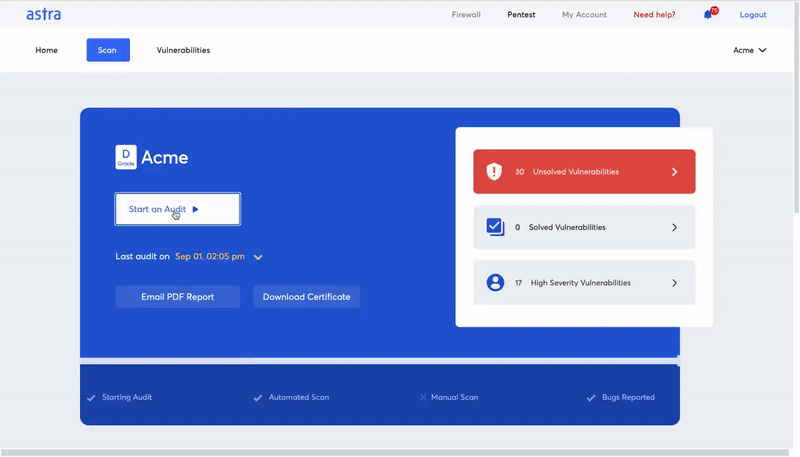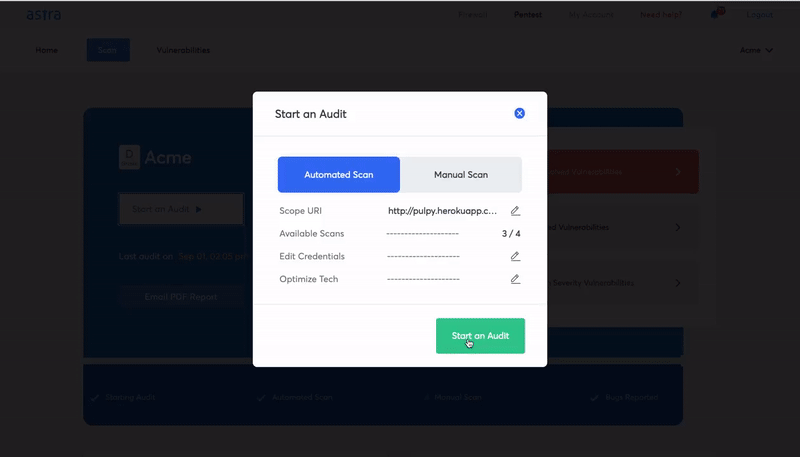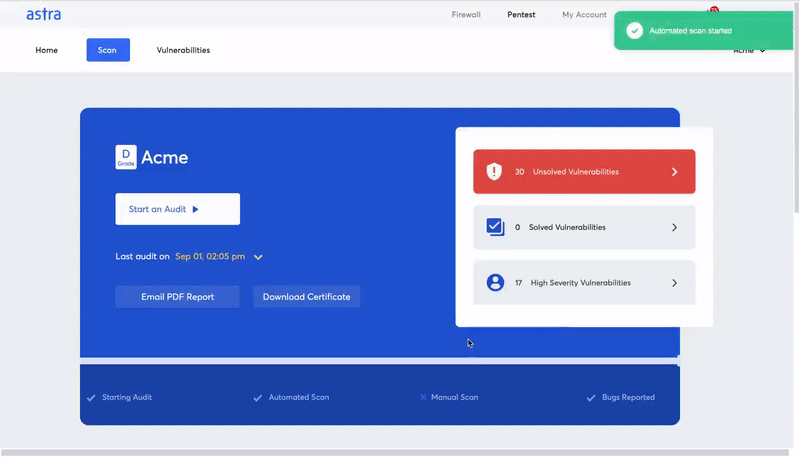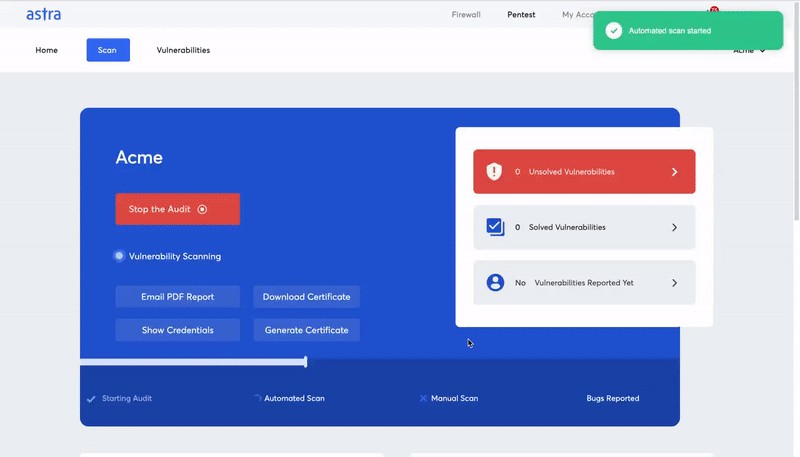
Conclusion
Software security testing is a vital part of the information security management process. It involves testing the security of an organization’s network infrastructure, applications, systems, and services to find vulnerabilities that could be exploited by a malicious individual, hacker, or group. Various organizations use network security testing tools to keep their network secure from hackers. Secure your network too before it’s too late.
FAQ’s
1. What is Software Security Testing?
Software security testing identifies security vulnerabilities in the network by using software applications and tools designed to detect and protect the network from malicious attacks.
2. Is it legal to scan any website Network for security risks?
The question about the legality of port scanning is quite frequent. The law is quite clear about it: you can not scan any network without the owner’s permission legally.
3. Can Astra help me with Software Security Testing?
Astra’s software security testing service is a top-notch way to improve your security, and we can even help you out if you’re just getting started. We have the tools and experience to find vulnerabilities and help you implement security to make sure your network stays safe. It’s time to get proactive and keep your business safe.
![Top 10 Software Security Testing Tools [2024 Reviewed]](https://cdn-blog.getastra.com/2022/01/Software-security-testing-tools.png)















