The rise of data breaches and cyber-attacks worldwide has been a growing concern for businesses and their customers. Firms and people constantly fall prey to cyber-attacks and data breaches, while security agencies and organizations always attempt to combat the same.
The data breaches are increasing, but what can you do to avoid data breaches? The short answer: conduct OWASP security testing regularly. This blog will understand how OWASP security testing can help you prevent data breaches and protect your customer data in your web application or website.
What are OWASP and OWASP Top 10?
As the Web grows, so does its attack surface. Web applications are developed in a greater variety of languages and frameworks and deployed to more diverse environments than ever before.
The Open Web Application Security Project (OWASP) is a worldwide, community-supported organization that focuses on improving software security. OWASP’s free-to-use, open-source software tools, training material, and articles are used by organizations worldwide.
The Open Web Application Security Project (OWASP) mission is to make web applications more secure. The project is open to anyone interested in improving the security of web applications or any application like Mobile, Cloud, etc.
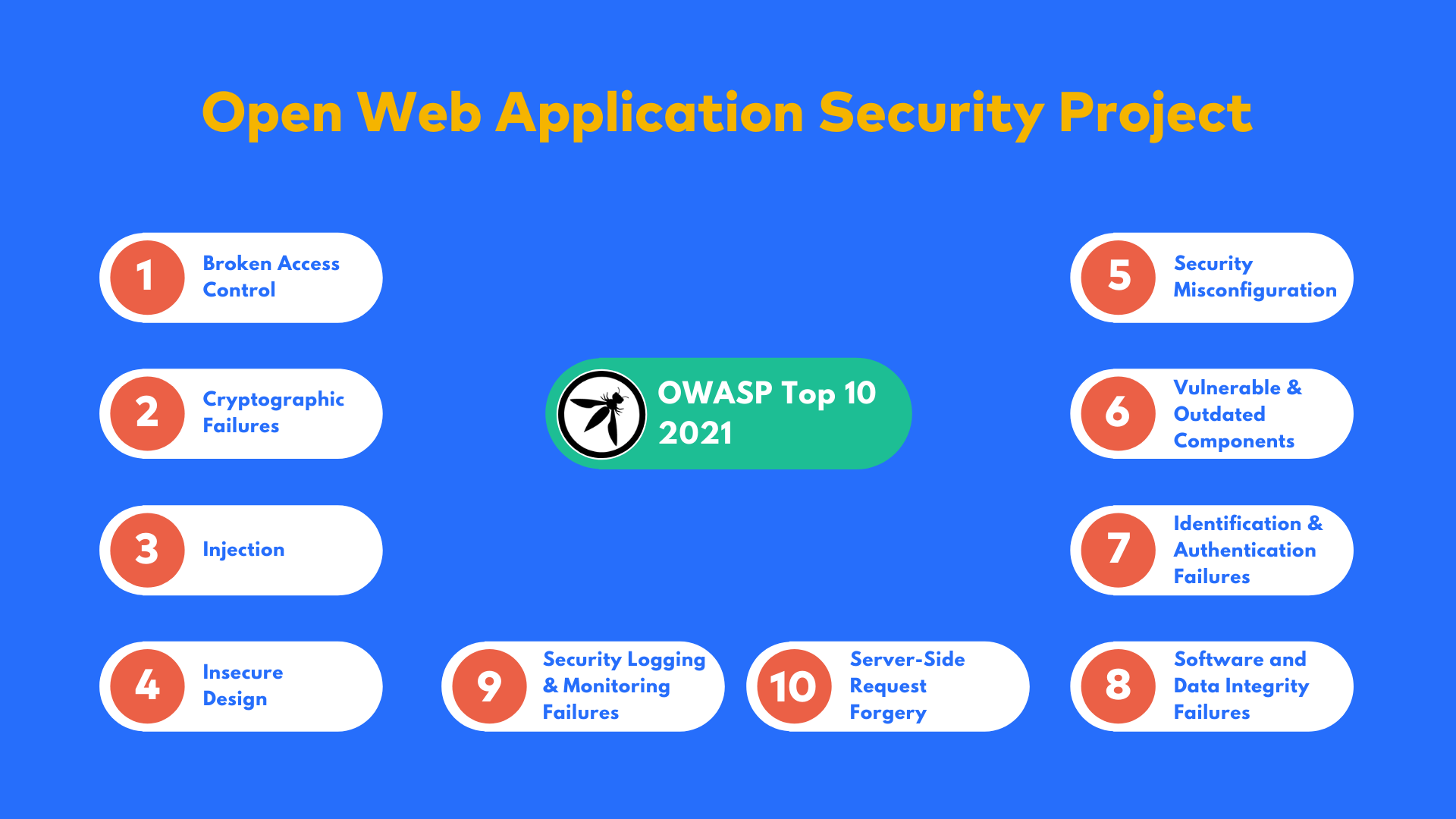
The OWASP Top 10 is an awareness document produced by the Open Web Application Security Project (OWASP) for software developers. The goal is to help software developers create more secure web applications.
Developers use OWASP Ten 10 to understand the most common security risks in web applications and avoid them. The OWASP Top 10 list is the most well-known list of its kind and is used by many organizations to guide their security efforts.
Understand OWASP Top 10 Risks and Vulnerabilities
1. Broken Access Control
Broken access control is the failure of enforcing or implementing the security policy. Missing or inadequate access controls may grant unauthorized users access to sensitive data or give authorized users access to unauthorized data.
A commonly used method to enforce access control is to define a set of access rights for users and then grant only those rights to users. This is often called discretionary access control. Access control can also be enforced by limiting hardware or software configuration to a specific set of approved values.
2. Cryptographic Failures
Cryptographic failures can happen in any cryptosystem. To be precise, a cryptosystem includes a cryptographic algorithm and a cryptosystem environment. The cryptosystem environment includes all the information necessary to use the algorithm.
Cryptographic failures can be divided into design failures and implementation failures. A design failure is a flaw in the cryptosystem design that causes a cryptosystem to be insecure even if all implementations of it are secure. In contrast, an implementation failure is a flaw in the way a particular implementation of a cryptosystem is written.
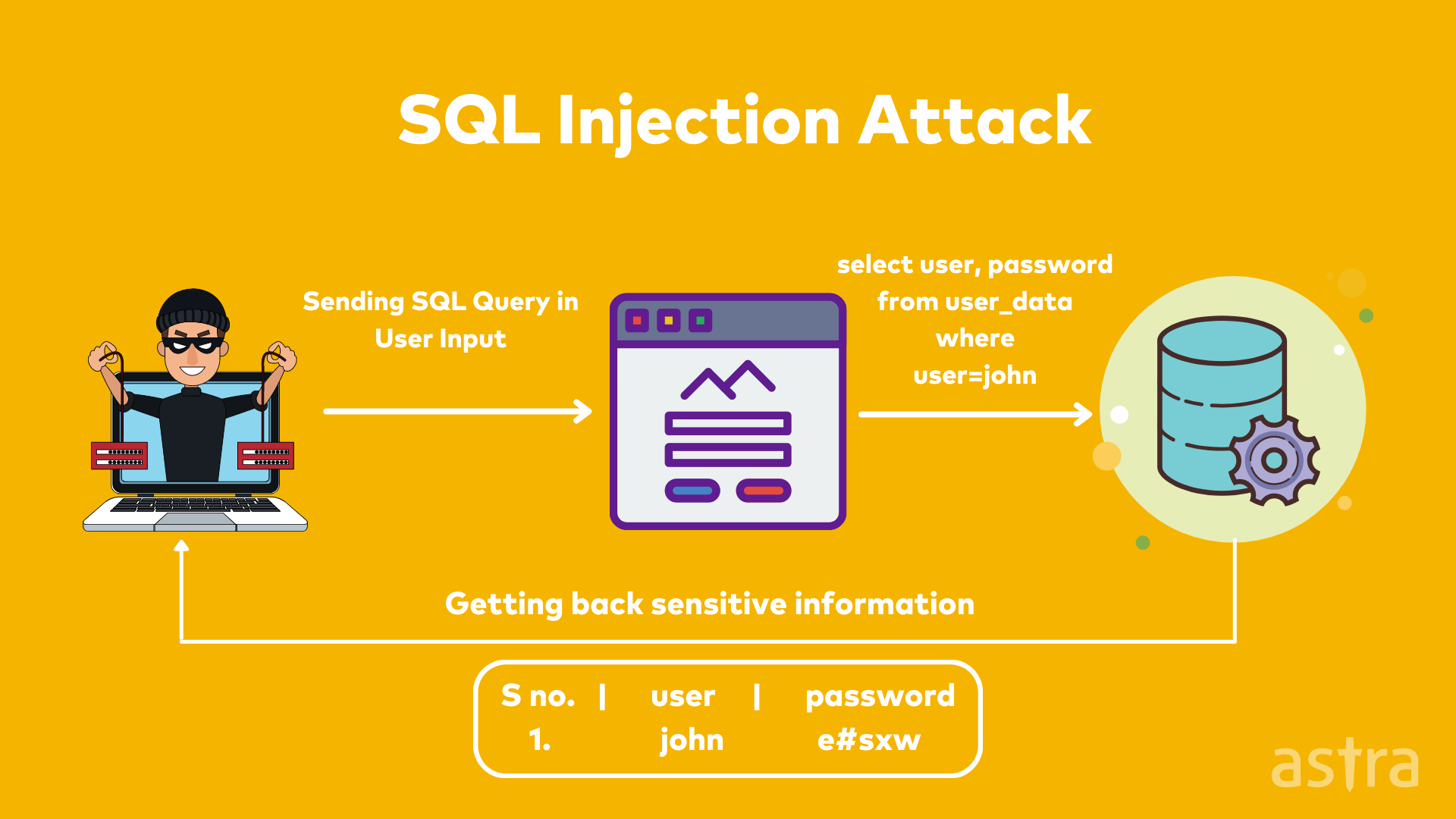
3. Injection
Injection attacks (also known as injection flaws, injection vulnerabilities, and injection exposures) are a type of security vulnerability that arises when an application takes user input and uses that input in an unsafe way.
This is particularly prevalent in web applications where the application receives input from a user and then passes it on to a database (for instance). An attacker can manipulate the user input such that it forces the application to execute some other command (in addition to the one initially intended).
Also Read: Security Testing Software – 5 Things to Understand Before You Choose One
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
4. Insecure Design
Insecure design is a broad category representing weaknesses, expressed as “missing or ineffective control design.” If a system or product design is not secure, it can be considered an insecure design.
In the context of web applications, it usually means that the website owner has not taken enough care to make sure the application is not vulnerable to security attacks. Still, it can also mean that the application has not been designed in a way that helps the user avoid insecure behavior.
5. Security Misconfiguration
Security misconfiguration is a common problem affecting many organizations. It results from inattention to security, lack of understanding of security best practices, or both. It is not uncommon for organizations to “set it and forget it” when it comes to security, allowing their systems to be installed with default settings that are either too permissive or too restrictive or leaving security settings that are no longer in use in place.
Security misconfiguration is often viewed as a security control problem, but it is a control weakness that can lead to security incidents, data breaches, and other issues. It is also one of the most prevalent problems in organizations, with potentially damaging consequences.
6. Vulnerable and Outdated Components
The term “vulnerable” or “outdated” components is used to describe software susceptible to being breached, hacked, or otherwise compromised. An attacker may exploit vulnerabilities for several reasons, such as to gain access to unauthorized information, modify data, or cause a denial of service (DoS).
7. Identification and Authentication Failures
Improper authentication, access, and session management are critical to protecting users from various security attacks. Some common vulnerabilities are:
- Improper session management
- Weak password policy
- Missing brute force protection
8. Software and Data Integrity Failures
Software and data integrity failures are a growing concern as the impact of data breaches and security vulnerabilities grows. Software and data maintain integrity when they are in their expected state. This means that the data is securely stored, the application is working correctly, and functioning as expected.
Maintaining software and data integrity can be difficult due to the complexity of the software, the variety of data, and the processes in place to maintain integrity. When software or data is not in its expected state, it is called a failure of integrity.
9. Security Logging and Monitoring Failures
Every company, even the best-run company, faces the possibility of a security incident. A large part of preventing such an event is having a solid security monitoring and logging system in place. But even the most sophisticated of such systems have some possibility of failure.
Security logs contain forensic information such as the source and destination addresses, files accessed, and other security-related information. Therefore, it is essential to analyze security logs regularly.
10. Server-Side Request Forgery
Server-Side Request Forgery (SSRF) is a vulnerability when an application makes a request to an unauthenticated, remote host and does not validate the request correctly. This allows the attacker to forge requests from the vulnerable server to any valid host on the internet. Hackers can use this to retrieve information from internal networks, access restricted information, or exploit vulnerabilities of the remote host.
Securing Applications against OWASP top 10 with Security Testing
Security testing is a type of software testing that uncovers vulnerabilities in a software application and prevents them from being exploited by hackers.
Security testing is one of the most crucial steps in the Software Development Life Cycle. Comprehensive security testing ensures that the software is free of vulnerabilities that hackers could violate. Security Testing aims to provide that the application does not contain any vulnerability that the attackers can exploit.
OWASP security testing is the best way to protect your system against OWASP Top Ten vulnerabilities. It will teach developers how to prevent these vulnerabilities and write secure code.
Security testing is not limited to penetration testing, which is mainly used to validate the system’s security. It also includes other types of testing like vulnerability scanning, source code analysis, authentication testing, etc.
What is OWASP Security Testing?
OWASP Security testing is a specialized security testing that focuses on attack vectors and vulnerabilities listed in OWASP Top 10. The OWASP Top 10 is a list of the most critical web application security risks.
The idea behind OWASP security testing is to see how easily hackers can attack a web application and whether the web application can be exploited using a known attack vector. The scope of this type of testing is pretty broad. The main goal is to test a web application for security vulnerabilities so that security engineers can detect them before a real hacker finds and uses them.
Also Read: OWASP Penetration Testing
Why is OWASP Security Testing important?
There is a lot of focus on software vulnerabilities and security breaches today. Big companies like GoDaddy and Clubhouse have been hacked and had to deal with the consequences of the hacks. The risk of getting hacked is real and is not going away. It’s essential to take OWASP security testing seriously.
The OWASP security testing methodology is a risk-based methodology designed to enable organizations to find and fix security issues in software. The OWASP security testing methodology is a set of guidelines that provides a structured approach to testing for security vulnerabilities.
OWASP security testing is a step in the software development process that ensures that a product is free from vulnerabilities listed in OWASP Top 10. This process ensures that all the required security controls are implemented and that the application is free from vulnerabilities. In other words, OWASP security testing is a process of identifying security flaws in an application before the product is deployed in the market.
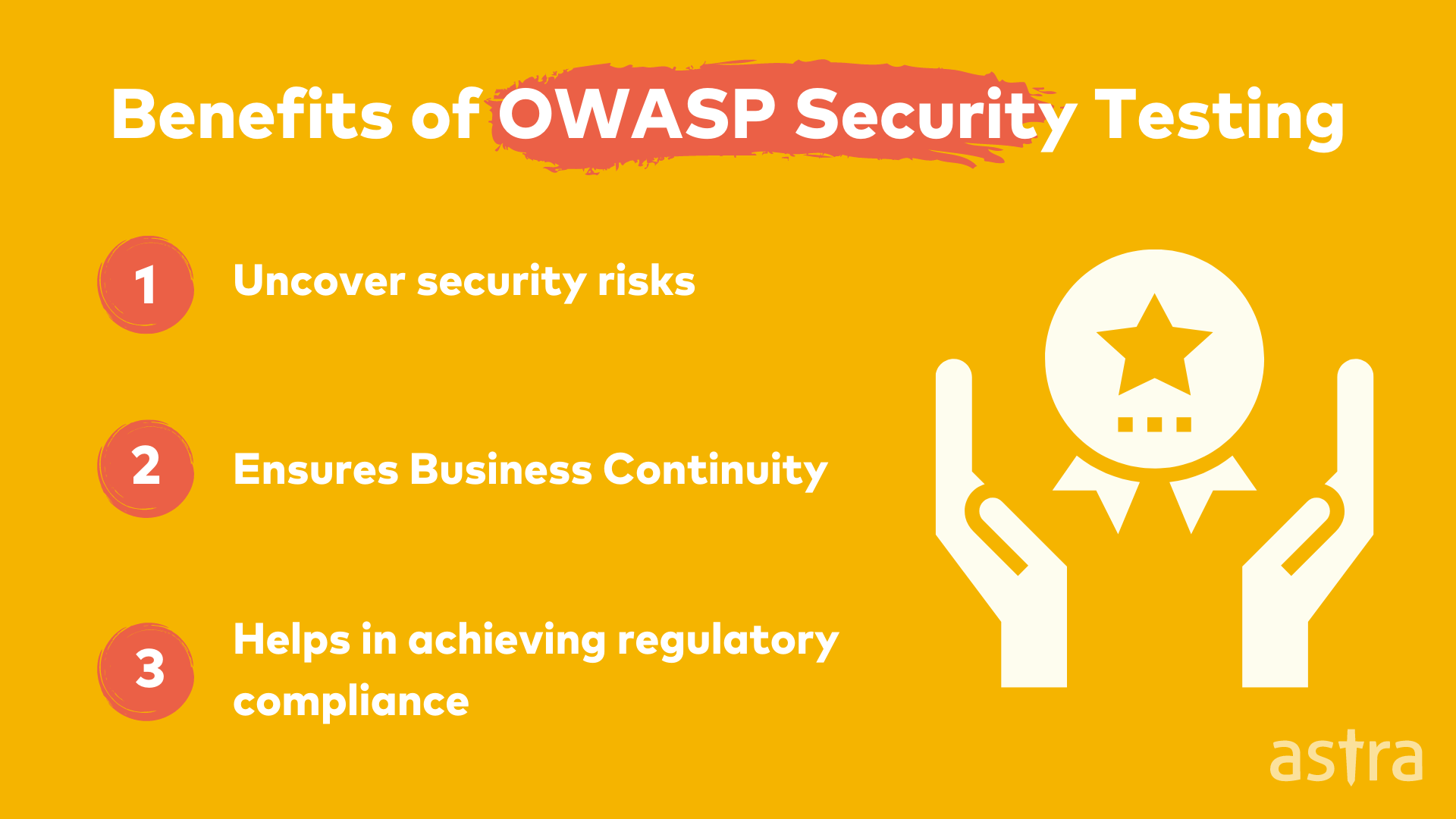
OWASP security testing is widely used in organizations. Some benefits of OWASP Security Testing are as follows:
- OWASP Top 10 is a list of the most common security vulnerabilities. OWASP security testing on that list helps companies uncover security risks.
- Regularly conducted OWASP security testing helps in ensuring the systems are durable and helps in protecting against hackers and ensure business continuity.
- OWASP security testing helps in achieving regulatory compliance such as NIST, PCI DSS, etc.
Also Read: How to Achieve Security Compliance with NIST Penetration Testing?
OWASP Security Testing Checklist
The OWASP Testing Project has released a list of controls to be tested when performing OWASP security testing. Testing for all of the rules on the list is not required, but it is recommended. The list is by no means complete, but it is a good starting point for OWASP security testing and a good framework for the security testing process.
1. Session Management
- Session puzzling
- Session Timeout
- Invalidate session after logout/password change
- Cookies with security flags (httpOnly and secure)
2. Data Validation
- Reflected XSS
- Stored and DOM-based XSS
- HTML Injection
- Text Injection or Content Spoofing
- Expression Language Injection
- Open Redirection
3. File Uploads
- Safelists file extension
- Maximum file size
- Insecure file name (leads to XSS)
- File content checking with the file extension
- Server-side file type (extension) match
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed]
Why choose Astra for OWASP Security Testing?
As companies of all sizes become more dependent on software, the security of these applications becomes critical. The challenge for teams that are tasked with securing their software becomes how to manage it all. Astra’s goals are to make security testing simple yet powerful.
Security Testing Made Simple: Astra aims to make security testing easy for teams of all sizes. Astra provides top-notch cyber security solutions, including web application security testing, cloud pentesting , API testing, and a lot more. Astra enables companies to gain a competitive edge in the marketplace.

Conclusion
With so many risks present online, OWASP security testing represents a way to ensure that your business is protected. This guide has been an excellent resource for companies that want to understand OWASP security testing and why it is essential. If you want to learn more about this topic, we encourage you to get in touch with an Astra-Naut today, and we can answer all of your questions and provide personalized support to make sure you’re using OWASP Security Testing for your next security project.
FAQ’s
1. What is OWASP Top 10?
The OWASP Top 10 is an awareness document produced by the Open Web Application Security Project (OWASP) for software developers. The goal is to help software developers create more secure web applications.
2. What is OWASP Security Testing?
The OWASP Top 10 is a list of the most critical web application security risks. OWASP Security testing is a specialized security testing that focuses on attack vectors and vulnerabilities listed in OWASP Top 10.
3. How often is list of vulnerabilities in OWASP Top 10 updated?
The OWASP Top 10 list is compiled and published every three to four years, including the most critical security vulnerabilities and keeping web developers up-to-date on the latest threats. The list is widely recognized and adopted by developers and security professionals alike.
4. Can I trust Astra for OWASP Security Testing?
Astra is one of the leading providers in the industry when it comes to security testing. Astra is trusted by the world’s leading financial, retail, technology, and education industries. Astra’s security suite has helped them in different ways, offering the best in class security audit, vulnerability management, vulnerability assessment, and penetration testing solutions.