A lot has been said and done about cyber security over decades. Now, if a person who is new to cyber security tries to learn his way in and choose the right security testing software, first there is information, then there is misinformation, and finally there is a cloud of tech jargon, concepts learnt from sci fi movies, and endless discourses to place one security solution above the other, that casts a shadow of confusion over the basics of security. And we are all set to lose around $10.5 trillion annually by 2025.
What is Security Testing?
Security testing is all about finding apparently invisible flaws that could lead to potential hacks, ransomware attacks, data breaches, data theft, cessation of operations, and employment of various automated and manual methods to inspect the security of a website, application, or network.
What makes security testing essential for businesses?
Effective security testing software does not necessarily come cheap. While it is difficult to predict an ROI on your security expenditure, it surely helps to understand what is at stake.
1. Risk Management
More than often, some of the unchecked vulnerabilities and weaknesses have the potential to become actual threats. As such, security testing can help your organization to defend against such vulnerabilities and ward off threats, but this testing needs to be done before cybercriminals get familiar with your application and exploit its weaknesses. Moreover, if you are using third-party applications, outsourced security testing services, or cloud-based services, then it becomes more than crucial to carry out security testing.
2. Cost Reduction
We all have heard the phrase – Prevention is better than cure. Taking this into context, using Security Testing can save a lot on costs associated with recovery and remediation after a breach. The cost may also include the acquisition of tools/technologies like vulnerability scanners etc, which is a fraction of the costs associated with recovery after a breach.
3. Reduced Downtime
These days, time equals money. As such, any chances of network and application downtime can lead to loss of productivity and availability which can cost companies millions of dollars. As such, Security testing becomes very crucial in order to detect bugs in the application and network that can lead to downtime.
4. Regulatory Compliance and Laws
Regulatory standards laid down in HIPPA, GDPR, ISO 27001, PCI-DSS, and others require companies to often do mandatory testing and audits of their security systems. Hefty punitive fines are charged if companies fail to do so. As such, companies must adhere to regulatory compliance and laws around security in order to keep their security tight and avoid hefty fines.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
5. Customer Trust
Another important reason to conduct Security testing is to ensure customer trust. Safeguarding your company’s reputation and holding onto your customer base is very crucial and security testing plays a very essential role in it. Not only is security testing often a requirement to get accredited and certified, but it also ensures that your company has a solid security system that helps gain and maintain customer base, and hence customer trust.
6. Peace of mind
Another important aspect of security testing is that it helps gain peace of mind, knowing that your applications, systems, and infrastructure have been tested for vulnerabilities. Working with a security test team and conducting these tasks can help protect your business and customers’ data.
Also Read: A Complete Guide to Cloud Security Testing | Guide to Cloud Penetration Testing
7 different approaches to Security Testing
- Vulnerability Scanning: This is done through automated software to scan a system against known vulnerability signatures.
- Security Scanning: It involves identifying network and system weaknesses, and later provides solutions for reducing these risks. This scanning can be performed for both Manual and Automated scanning.
- Penetration testing: This kind of testing simulates an attack from a malicious hacker. This testing involves analysis of a particular system to check for potential vulnerabilities to an external hacking attempt.
- Risk Assessment: This testing involves the analysis of security risks observed in the organization. Risks are classified as Low, Medium, and High. This testing recommends controls and measures to reduce the risk.
- Security Auditing: This is an internal inspection of Applications and Operating systems for security flaws. An audit can also be done via line-by-line inspection of the code
- Ethical hacking: It’s hacking an organization’s software systems. Unlike malicious hackers, who steal for their own gains, the intent is to expose security flaws in the system.
- Posture Assessment: This combines Security scanning, Ethical Hacking, and Risk Assessments to show an overall security posture of an organization.
Read also: Penetration Testing for Startups – Importance, Processes, Best Practices
How to choose the right security testing software for your company?
There is no ‘one size fits all’ when it comes to security testing software. You have to take your goals, requirements, and budget into account while choosing the right security testing software for your firm. Now, let’s say you have an internet-facing application that stores a lot of user data, you would want a robust security testing tool that features both regular vulnerability scanning and penetration testing. Here’s what you should expect from a great security testing tool.
1. Do your research
There are a bunch of tools to choose from and each of them comes with some advantages and some disadvantages. For instance, a certain tool may produce reports very quickly but also ring too many false alarms. Another one may come with great features but be very difficult to use. You want to choose a tool that has the right balance of features, speed, accuracy, and user-friendliness for your business.
2. Fewer the false positives the better
A false positive is when an automated vulnerability scanner flags an issue that in reality is not a security threat or doesn’t exist at all. false positives are very cumbersome to deal with as it engages knowledge workers in a wild goose chase for no reason. It causes wastage of time and resources. You need a tool that can put the potential false positives under a different category.
3. A smart tool can save so much of your time
A machine learning-powered security testing software that learns more about your network with every usage and becomes more and more efficient is something you should be looking for. An automated security testing tool should be smart enough to run a scan every time there is an update on the web application you are using it on. There are small features like integration with CI/CD apps or scan behind a log-in that can make a lot of difference in terms of user experience and efficiency.
Also Read: API Penetration Testing: What You Need to Know
4. A truly actionable vulnerability report
You want your vulnerability report to be thorough, detailed, and yet easy to start working on. It should categorize the vulnerabilities accurately according to their severity and CVSS scores. It should come with suggestions for security enhancements. If you are using a pentesting service, the report should have detailed guidelines for developers to reproduce an exploit and remediate it. You should be able to assign the vulnerabilities to developers right from the tool if needed.
5. A verifiable certification
If you are getting a penetration test of your web application done, it should get you a publicly verifiable certificate (of course, after you have removed the vulnerabilities and conducted a rescan). A security testing certificate is a very important document for businesses dealing with customer data or sensitive information. A lot of industry verticals actually mandate such certifications. So you must make sure that the security testing software you are using assigns you a publicly verifiable certificate.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
Astra Security checks all the boxes
Astra Security has created a superb security testing tool, the Astra Pentest suite, and taken user experience to a whole new level. For an intelligent security scanner that conducts 8000+ tests, the Astra Pentest suite is incredibly easy to use.
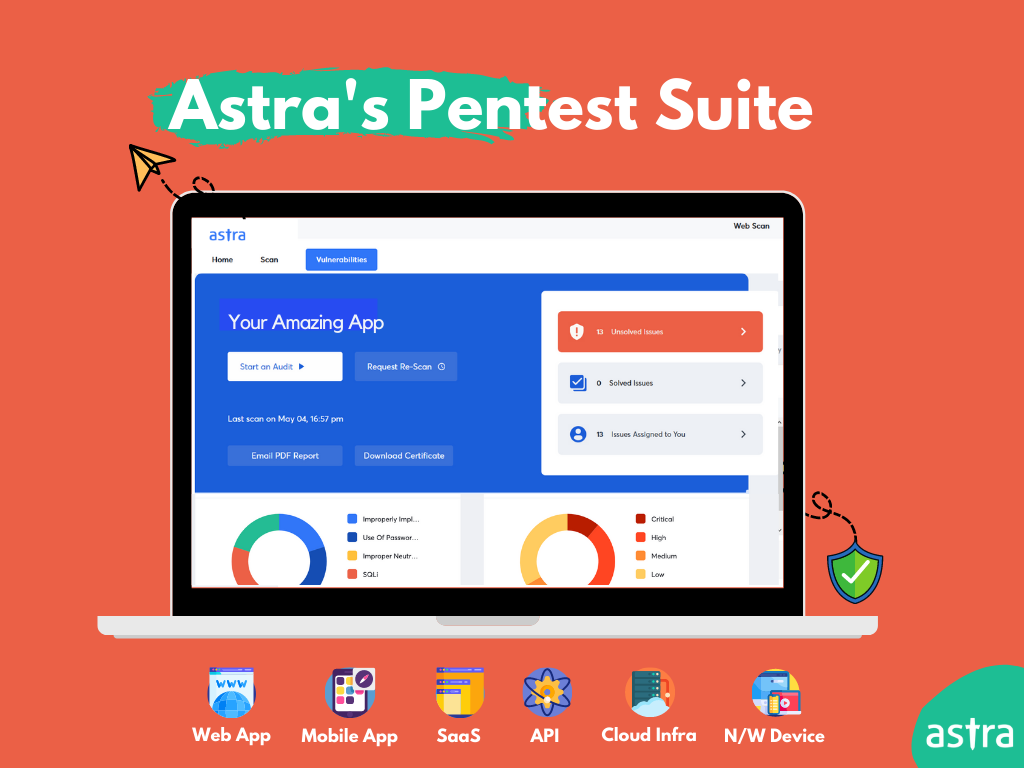
The scanner is machine learning-powered, it gets better with every use. You can automate scans with every code update by integrating GitHub. You can use the in-app dashboard to communicate with your developers or you can take the exchanges to slack by using the integration feature.
With the login recorder feature, Astra’s vulnerability scanner scans behind login pages without requiring you to authenticate it every time a session runs out. There are a bunch of little features like these that just make it easier for developers trying to remediate a security issue.
To conclude
Choosing the right security testing software is about finding the right balance. The aim should be to find a tool that is self-serving, accurate, fast, and easy to use. Look at a bunch of tools and compare the user experience if possible through demo scans. We hope you find the right one for your web application.
FAQs
What is the timeline for penetration testing?
Penetration Testing for web applications usually takes 4-7 days. The time may differ according to the scope of the pentest and other factors.
How much does penetration testing cost?
The cost of penetration testing for web applications is between $99 and $399 per month. The cost may differ significantly for cloud penetration testing or mobile app pentesting.
Do we get free rescans after the remediation?
You get 1-3 free rescans after the initial vulnerability report is produced. You get 30 days to remediate the issues and avail of the rescans.
















