In today’s cyber threat landscape, data is constantly being stolen from companies and organizations, which is why there’s an urgent need to take proactive cybersecurity measures. The data breaches are costing businesses billions of dollars every year, not to mention the negative impact on customer confidence. And security testing is one of the best ways to prevent data breaches. Automated security testing tools have come up as a convenient solution for companies of all shapes and sizes.
If you are looking for a way to stay ahead of the competition and avoid having your data compromised, security testing is a great option to look into. It is something most business owners don’t think about until it’s too late for them. But the sooner they start looking into it, the better it gets for them and their business revenue.
In this article, we’re discussing a trending topic in cybersecurity which is – security testing. We’ll also learn in detail about different types of testing and some security testing tools to carry them out.
What is Security Testing?
Security testing is the process of testing the security of an information system. The process is intended to identify weaknesses in the system that are exploitable for unauthorized access or cause denial of service to authorized users.
Security testing has two main purposes:
- To find security weaknesses in the system before an attacker does,
- To determine if changes to the system have inadvertently created new weaknesses.
Security testing is often performed by a third-party vendor or the same people who develop the system. Still, independent security testing is often required by law or regulation to ensure that systems meet the security requirements of the system’s owner.
In some organizations, security testing is part of a larger process known as penetration testing. Penetration testing is a more formalized and structured approach to security testing, where a team of security experts will attempt to identify flaws and weaknesses in an application’s security.
Security testing is often used to supplement other information security activities, such as penetration and vulnerability assessments, and is frequently conducted by a specialized security team or third-party consultants.
Also Read: What, Why, and How of VAPT (Vulnerability Assessment and Penetration Testing)?
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
Understanding DAST and SAST
Security testing is mainly categorized into two different types. Let’s understand both of them in detail:
1. Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) is a method to find security vulnerabilities in an application while in production.
DAST is conducted in the same way as traditional application security testing, but with the major difference that in DAST, the application is tested in real-time, in production. The testing is conducted using application source code in the same way the application is developed. The application will be tested in the same way customers, or users would use it.
The purpose of DAST is to find security vulnerabilities before the application is released to the public so that the application can be fixed before anyone else can get their hands on it. This means that DAST is a testing tool and a process that uses the results of automated or manual tests to fix security vulnerabilities. This is why DAST is sometimes also called “Dynamic Application Security Fixing” (DASF).
DAST uses various automated security testing tools that help identify any potential security vulnerabilities in an application known as automated security testing tools.
Also Read: A Complete Guide to Cloud Security Testing | 11 Top Penetration Testing Tools/Software of 2022
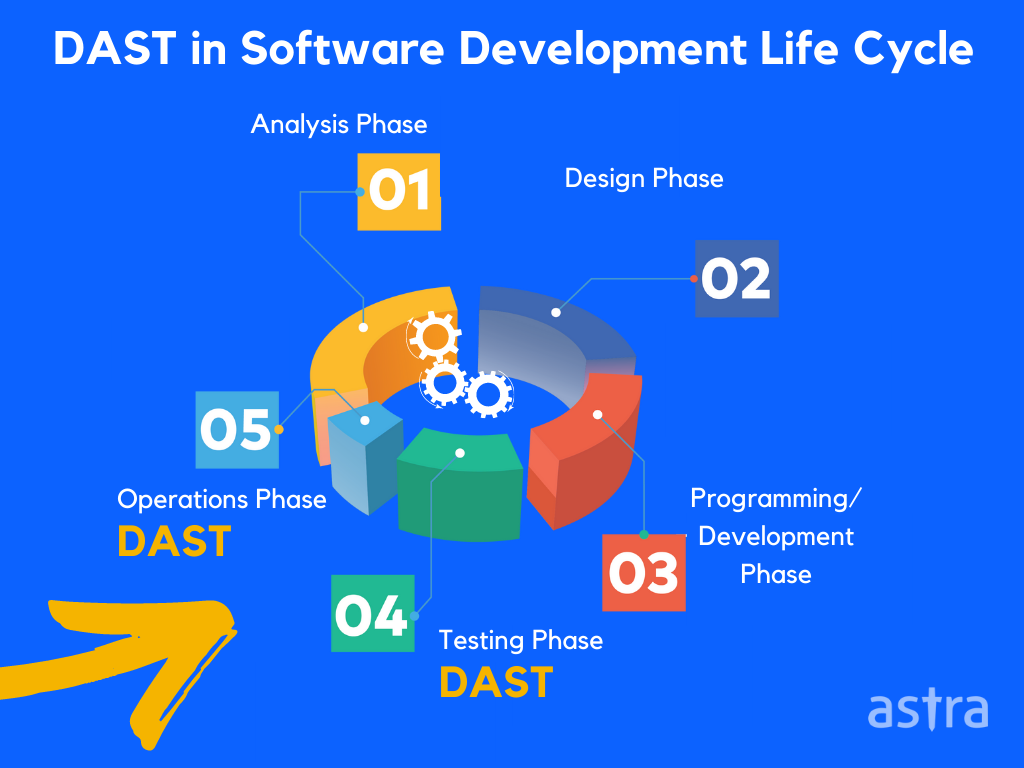
2. Static Application Security Testing
Static application security testing (SAST) is one of the most important security practices a software company can adopt. It uses a source code analyzer to look for common patterns in the application source code.
The term “static” indicates that SAST does not require executing the software’s code to detect vulnerabilities. This is in contrast to dynamic application security testing (DAST), which requires the actual execution of the code to detect vulnerabilities. Static Application Security Testing (SAST) helps manage security risks by using source code analyzers to identify security vulnerabilities in the source code before the software is executed and without executing the program.
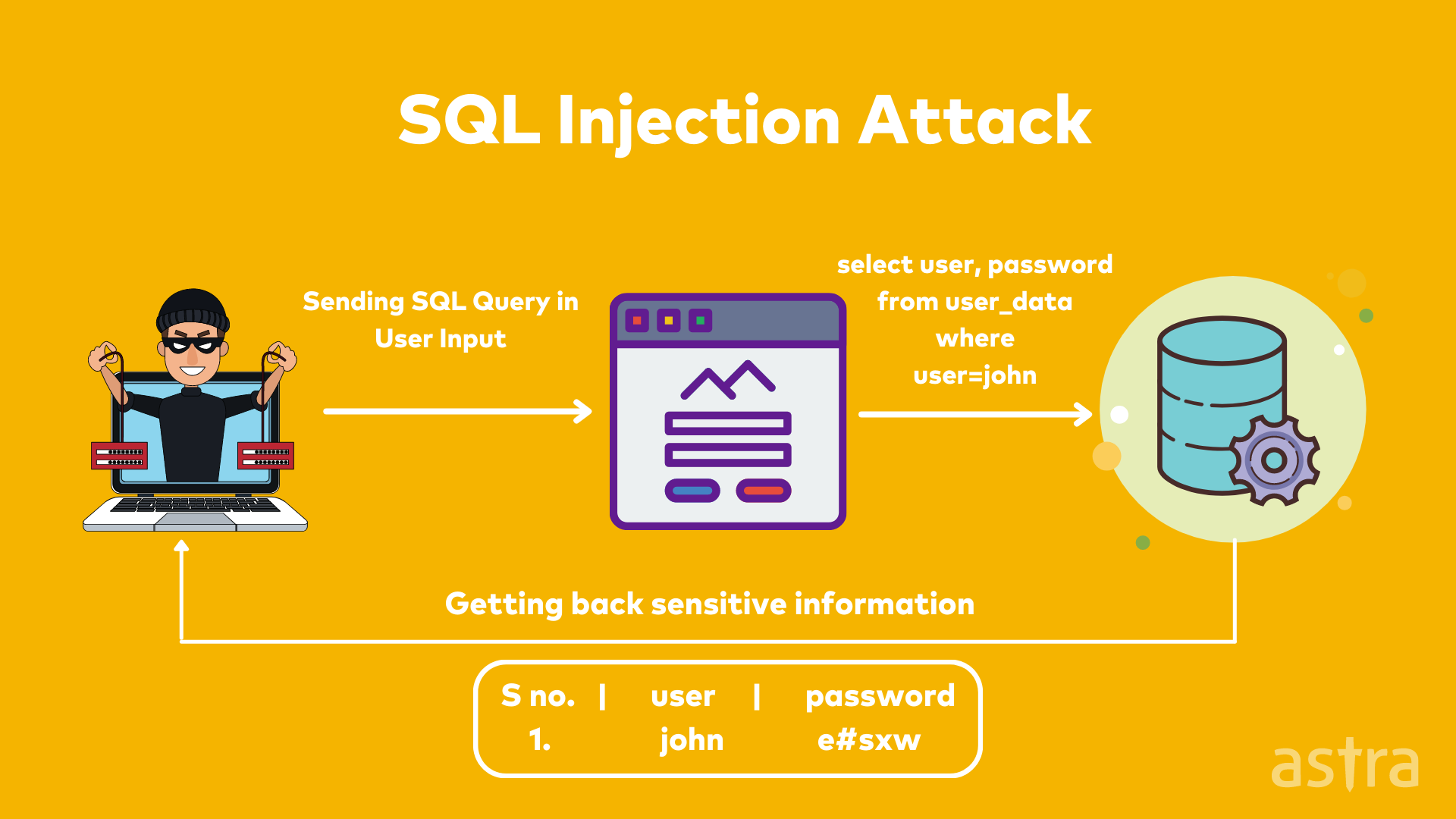
For example, an analyzer can look for common patterns such as cross-site scripting (XSS) and SQL Injection vulnerabilities. Other common patterns include Cross-Site Request Forgery (CSRF).
Types of Security Testing: Manual VS Automated
Manual Security Testing
Manual Security Testing is a security testing technique where a human being (security tester) manually evaluates the system’s security. The tester will manually try to find vulnerabilities in the application or system.
Manual Security Testing is often used as an additional step to automated security testing. The tester will use his skills and experience to find out the vulnerabilities in the application.
Reading Guide: Web Application Security Testing: Methodology, Tests, and Tools | Security Testing Software – 5 Things to Understand Before You Choose One
Automated Security Testing
Automated Security Testing is the process of scanning the application for vulnerabilities using automated tools. This is important because it can help to prevent certain vulnerabilities from being exploited by hackers. With the help of automation scripts or applications, a programmer analyzes the application for potential security holes and fixes these holes automatically.
Automated security testing is the practice of using software/applications to test a system for security vulnerabilities known as automated security testing tools. The automated security testing tools can be run against any application (e.g., web app) and report back to the user with a list of the vulnerabilities found in the application.
Penetration testers and security auditors often use automated security testing tools to find vulnerabilities. Still, the developers and administrators also use them to test applications before release.
Also Read: What is Automated Penetration Testing? Difference between Automatic & Manual Pentesting Software
Deep dive into Automated Security Testing Tools
Security testing of an application is a must these days. The applications are developed with many security vulnerabilities which can be leaked out to the attacker. These vulnerabilities cause a great loss of information or money or both.
The purpose of automation is to reduce the amount of time required to test an application by performing repetitive tasks, overcome the limitations of manual testing, and provide consistent test results. Automated testing has become more important in recent years because it is more cost-effective than manual testing.
Automated security testing tools are used to test any applications for security vulnerabilities. These tools perform several security checks and run various tests to ensure the software is secure and free from any vulnerabilities.
Anyone can use automated security testing tools to scan and test their applications for vulnerabilities. Security testing professionals can also use them to test applications for vulnerabilities during software development. Automated security testing tools are used for various security testing activities, such as penetration testing, vulnerability scanning, source code analysis, and security code review.
The automated security testing tools may include open source applications, commercial applications, or open-source applications offered as a service.
Also Read: Network Security Testing and Best Network Security Tools in 2022 | A Complete Guide to Cloud Penetration Testing
Why are automated security testing tools widely used?
Manual testing is time-consuming and repetitive, and it gives an incomplete picture of your application’s security posture. Automated security testing tools offer a way to test your application quickly and comprehensively.
Security testing aims to find and fix vulnerabilities that can be exploited to breach your application. Using automated security testing tools helps you achieve that goal more quickly. Let’s understand why companies use automated security testing tools widely:
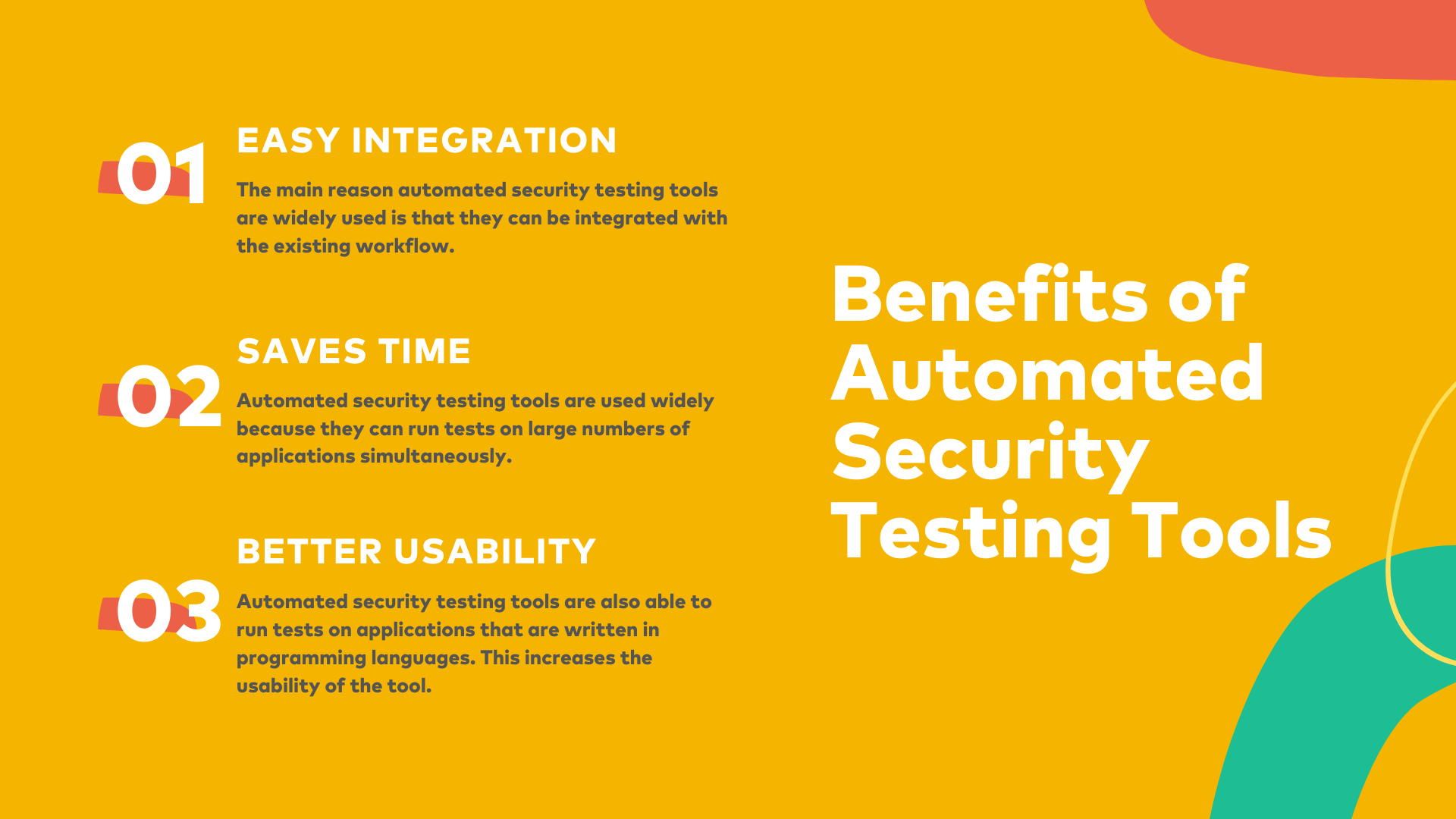
- Easy Integration
The main reason automated security testing tools are widely used is that they can be integrated with the existing workflow. They handle a lot of the tedious work and can even be scheduled to run overnight or while the developers are on a break.
- Saves Time
Automated security testing tools are used widely because they can run tests on large numbers of applications simultaneously. This allows security professionals to save time and resources.
Also Read: A Complete Guide on VAPT Testing | 7 Best API Penetration Testing Tools And Everything Related
- Better Usability and Efficiency
Automated security testing tools are also able to run tests on applications that are written in various programming languages. This increases the usability of the tool. Automated security testing tools can also save time by running tests on the functions of the application. This helps the testing team to concentrate on other functions.
Also Read: Top 5 Software Security Testing Tools You Should Know About
3 Things to Check Before Buying Automated Security Testing Tools
Security testing is not an easy task to do manually. It requires hours of research as well as experience as well as it is quite time-consuming. It needs a lot of effort and patience to do it manually.
However, if you are looking to automate your security testing, then it is time you should seriously think about automated security testing tools. There are a lot of automated security testing tools available in the market, and the choice of selecting the right tool is quite difficult. You may ask: what should we look for when we look for an automated security testing tool? Well, we have prepared a list of things to check before buying an automated security testing tool.
1. Easy to use
Today’s enterprises are adopting security testing tools to ensure that their applications are secure. However, the problem is that the tools are either too complex to use or they are not easy to learn. The automated security testing tools must be easy to use so that everyone can use them easily.
2. Updated with Latest Vulnerabilities
No automated security testing tool is perfect. Hackers are constantly finding and releasing new vulnerabilities. An automated security testing tool should have an updated list of security vulnerabilities so that no vulnerability is left unnoticed.
3. ROI vs. Cost of Tool
The cost of automated security testing tools is one of the main reasons why organizations avoid using such security testing tools. This is because they have a belief that automated security testing tools are expensive and unaffordable. But this is a wrong mindset as the cost of automated security testing tools is not as high as many IT professionals think.
Automated security testing tools don’t have a high cost as their benefits are equally high. This is why it’s important to understand the cost factors behind automated security testing tools.
Top 3 Automated Security Testing Tools
1. Astra Pentest
Astra’s automated security testing tool is an innovative automated tool that provides automated security testing for your applications. It is the best in the market that is capable of testing your application for any security vulnerabilities. It has more than 2600 test cases with high accuracy and fast execution time.
Features of Astra’s automated security testing tool:
1. Comprehensive security testing report
2. Pocket-friendly pricing
3. Compliance friendly (NIST, SOC2, GDPR, etc.)
4. Quick human support available
Learn more about Astra’s automated security testing tool.
2. OWASP ZAP
OWASP ZAP is an easy-to-use integrated automated security testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experiences. As such, it is ideal for developers and functional testers who are new to penetration testing.
Features of OWASP Zap:
1. Open source and free to use
2. Acts as a proxy tool to intercept requests
3. Big community to help with issues
3. Sqlmap
Sqlmap is an open-source automated security testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over databases. Internally it uses the same engine as the commercial tool sqlninja, but its features and syntax are slightly different.
Features of Sqlmap:
1. Supports all kinds of SQL Injection attacks
2. Supports direct connection to the database
3. Supports adding custom headers to requests
Learn more about features of sqlmap
Astra Automated Scanner: What else do you need to know?
Astra’s Automated Scanner is a key security tool that can help you improve the security of your applications. It is a tool for application security testing that automatically scans your applications for vulnerabilities.
By automating the work of a manual tester, Astra’s Automated Scanner can help you save a lot of time and money. Astra Automated Scanner is a highly scalable tool, making it a perfect fit for applications with much traffic.
Astra’s scanner analyzes the entire application and its underlying infrastructure, including all network devices, management systems, and other components. It’s a deep analysis that helps you find security weaknesses, so you can fix them before a hacker does.
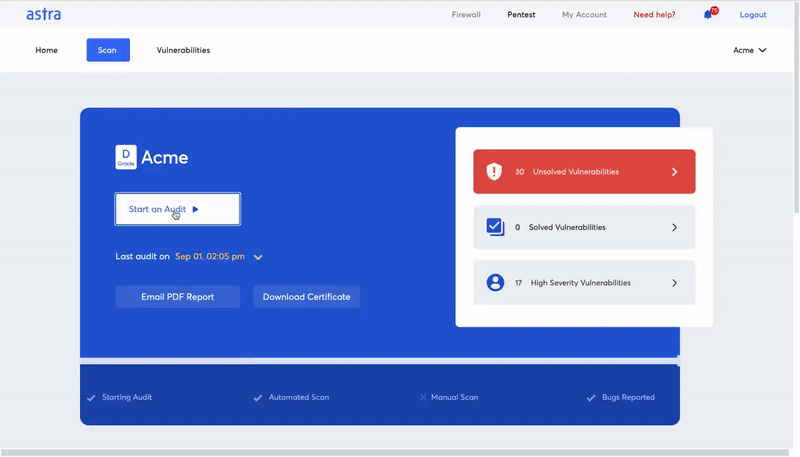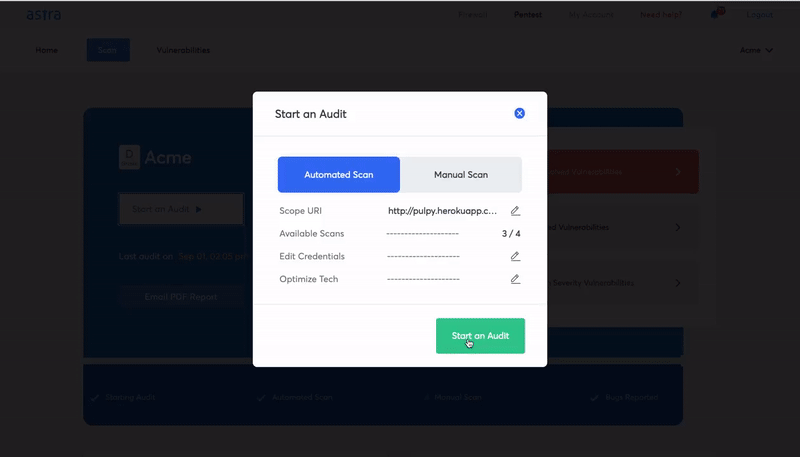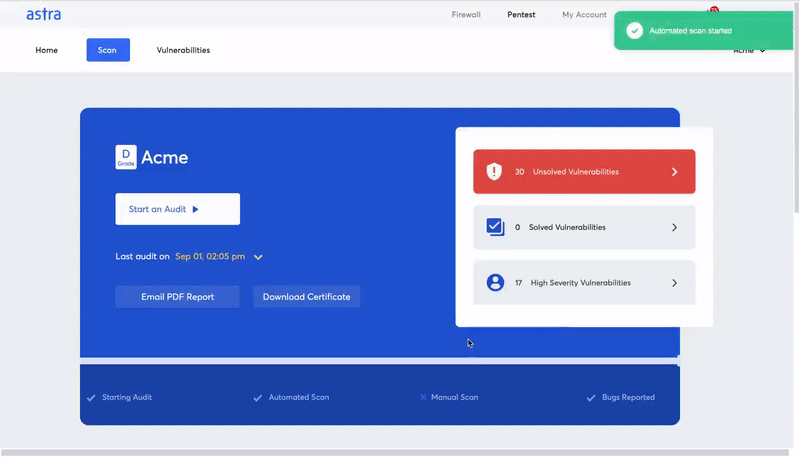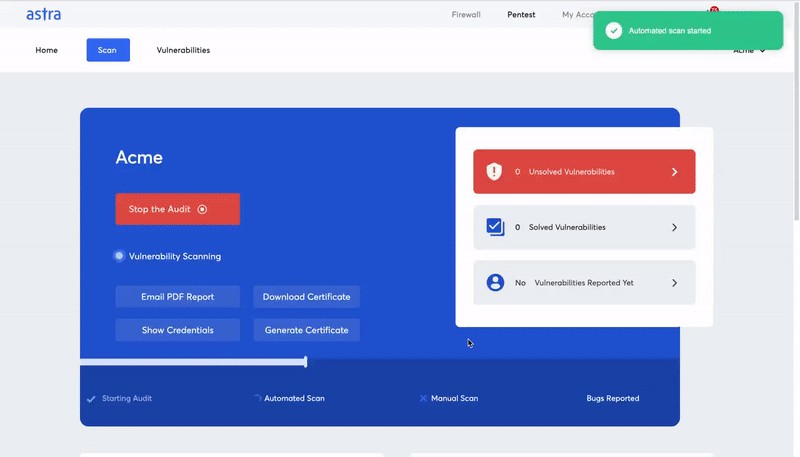
Features of Astra’s VAPT Tool:
- 2600+ tests to keep your infrastructure secure from hackers.
- Easy, accessible reports that you can interpret at a glance with the dashboard.
- Collaborate with developers from within the dashboard.
- Get detailed steps on bug fixing tailored to your issues and know exactly how to reproduce vulnerabilities with video Proof of Concepts (PoCs).
- Why keep your security status private? Showcase Astra’s Publicly verifiable certificate.
- Post pentest, Astra shows a potential loss in $$$ for each vulnerability, making it easier for everyone to understand the impact.
- For each vulnerability, Astra gives an intelligently calculated risk score.
- Pocket-friendly pricing
Conclusion
As the number of cyberattacks targeting businesses and individuals has grown significantly, the need for automated security testing tools has increased. Automated security testing tools are a great way to test any application for security vulnerabilities. It’s not only an efficient way to identify security holes but also a cost-effective method. Any business or individual can use automated security testing tools to test their applications and find out if they have security vulnerabilities.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
FAQ’s
2. Why do companies prefer to use automated security testing tools?
Automated testing tools help businesses to speed up the testing process and provide them with accurate and confirmable results. Automated security testing tools are widely used in penetration testing, vulnerability assessment, and compliance testing. The automated security testing tools provide effective and efficient methods to test the application, servers, and other systems.
What is the average cost of automated security testing tools?
Automated security tools can cost from $500-$10000+ per scan. The cost depends on the type of scan and the number of hosts and services that you want to scan.
Why Astra’s automated security testing tool is a must?
Astra’s automated security testing tool offers more than 2600+ tests with pocket-friendly pricing. To ensure that your website is secure and safe, you need to have a reliable security testing tool. Astra’s automated security testing tool is a must-have for every website owner.
















