The security of applications is being called into question daily for the protection they offer to their customers and also for themselves. With hackers looking for any minute opportunity to steal data, it is best to safeguard and test your applications regularly. This is where DAST comes in.
What Is DAST (Dynamic Application Security Testing)?
Dynamic application security testing (DAST) is the process of finding security vulnerabilities while the application is in the production phase which includes both manual and automation testing using various kinds of testing tools.
DAST is a black box testing
It is a type of black-box testing service (with no knowledge of infrastructure, network, or code) that tests your application from a malicious person’s perspective, also known as an Attacker or Hacker. Applications depend on inputs and outputs to operate, which means that if there is suspicion in the user-based input, something similar might also reflect the response.
DAST testing can help you find vulnerabilities in your software, even before any input is given. It is not designed to work on specific software but on the application layer, where the actual applications are vulnerable.
Why is DAST Important?
The importance of DAST lies in its following features:
- Detection of minor security misconfigurations from the developers such as improper validation of user input, server version disclosure, and using vulnerable software libraries that could lead to major security issues.
- The difference is that DAST is dynamic. That means the tests are run in real-time, simulating real-world application behavior. Dynamic testing is usually conducted on the live system, also known as Production Environments.
According to a study by CNBC, more than 75% of applications are vulnerable in some way or another, there is simply no way that security vulnerabilities in applications are going away anytime soon; that’s where DAST Security Testing comes in.
DAST scanning, you might wonder how it is different from traditional penetration testing or static application security testing is slow, static, and very time-consuming.

Pros And Cons Of DAST
Here are some of the advantages of DAST scanning:
- Dynamic testing: DAST scans are carried out on real-time production environments that mimic real-world behavior.
- Less False Positives: Dynamic scans provide accurate results and comprehensive test coverage for your applications. If any false positives are present they are detected by the DAST scanners.
- Early Identification: DAST automated tests help with the early identification of vulnerabilities since the application mimics live-world behavior.
- Black-Box Level: Since dynamic application security testing works on a black box level with no prior information sharing, it can find problems missed in earlier testing such as authentication or configuration issues.
Some of the limitations of DAST testing include:
- False positives are not avoidable, with manual review however they be cross-checked and removed.
- Relies heavily on security experts for the creation of the right testing procedures for any applications.
- Dynamic scanning can only detect the problems in the live environment and not within the code itself.
- Dynamic scans can are time taking to complete, and remediation and fixing of vulnerabilities take additional time thus delaying set timelines.
What are various types of DAST?
Most people consider DAST as an Automated approach, but it’s not. Dynamic Application Security Testing is widely divided into two types:
- Manual DAST: Software vulnerability scanners and penetration testing tools can be a great help when it comes to securing an application. However, they are no match for a human mind, which makes mistakes of its own. This is where manual DAST comes into play, who can use their experience and knowledge of the field to find vulnerabilities that automated scanners would miss. Manual testing includes the team of security professionals testing the application for bugs that are usually missed by automated vulnerability scanners.
- Automated DAST: Automated Dynamic testing includes testing applications using software and feeding them required data. This type of testing includes using Crawlers, Fuzzers, and Regex to find and replace essential keywords, which results in different kinds of vulnerabilities such as SQL Injection, Cross-Site Scripting, and Server Side Request Forgery, etc.
How does DAST work?
DAST works by simulating external attacks on an application to identify outcomes that are not part of a typical user experience. DAST scanning requires no prior knowledge of the programming language being used, due to which the application is tested end to end without getting into the source code.
DAST tests all kinds of endpoints including hidden endpoints and stimulates different kinds of attacks to find security vulnerabilities. The automated testing tool for dynamic application security testing simulates malicious attacks on an application to identify outcomes not part of an everyday user experience.
One example of DAST security is a SQL injection flaw. By sending a large string of characters, a DAST attack can help identify a SQL injection flaw.
Other application security testing methodologies do not cover a wide range of vulnerability testing. However, DAST looks for vulnerabilities in the source code at runtime, which means that DAST does not require an application to be rebuilt to test for vulnerabilities.
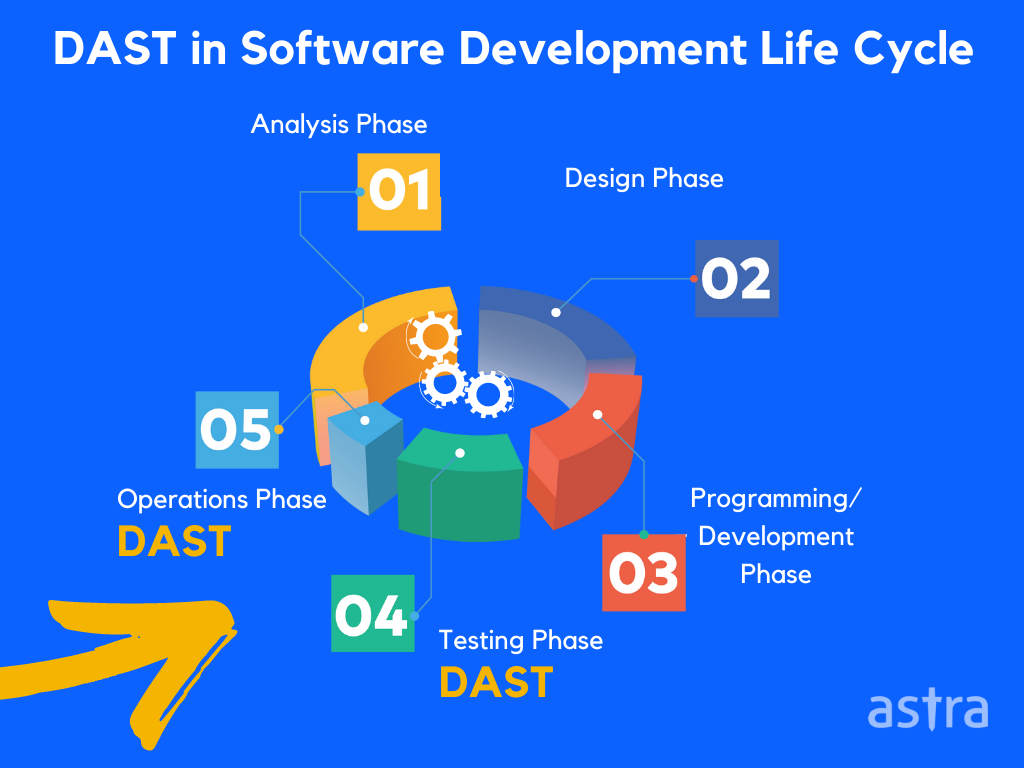
Integration of DAST in SDLC
Software development life cycle (SDLC) is one of the essential terms in software development because it is the framework that unifies the entire process of the development of the software or the application. The integration of DAST tools, with SDLC, is the key to building secure applications.
DAST enables development teams to identify and resolve issues before they become more significant problems. DAST scanning was introduced to the software development lifecycle (SDLC) to provide developers with an opportunity to identify vulnerabilities in an application before hackers exploit it.
However, before the emergence of DAST solutions, it was difficult for teams to integrate scan results into the development lifecycle. Organizations that integrate DAST into their SDLC processes have a competitive advantage over those that don’t.
Why DAST is Important for Your Application?
DAST is a relatively new testing practice that focuses on assessing the security of software applications at runtime. It allows us to perform testing on the production environment, thereby offering several otherwise unavailable benefits.
So what are these benefits? Let’s have a look at them in more detail:
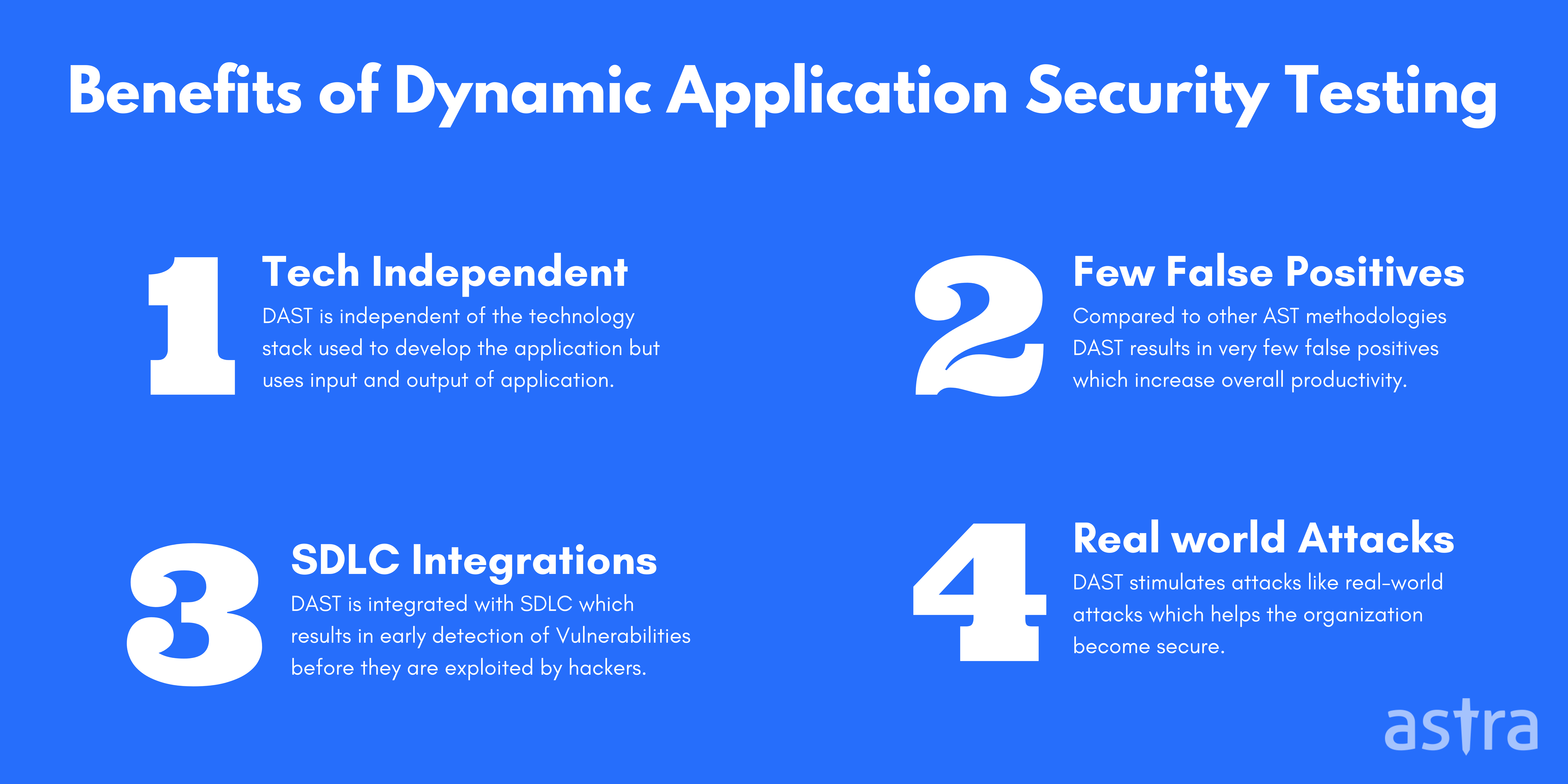
1. No syntactic knowledge of application:
DAST is adaptable to whatever programming languages are being used since it requires little to no knowledge of programming language and isn’t language-specific making it more agile. Automated scanners test the application based on the input and output, no matter what the language is.
2. Very few false positives:
DAST scanners result in very few false positives compared to other AST methodologies because of end-to-end testing irrespective of components, language, and platform.
3. Scan what matters:
Since DAST exercises applications and services using their web interfaces, it tests the result of all components and systems interacting with each other and highlights real-world vulnerabilities without the need for much insight into each component.
4. Real-world scenarios:
DAST scanners aren’t designed to work within internal intranets, so their methodology is consistent with typical external attacks. It stimulates attacks like real-world attack that helps applications become secure before a hacker tries to attack them.
5. Integration with SDLC:
Organizations implement DAST into the SDLC to reduce the vulnerabilities and security risks in their applications in the CI/CD pipelining phase, resulting in a higher chance of successfully mitigating vulnerabilities.
6. Easy and continuous setup:
DAST is easy to set up and is a continuous scanner that keeps on checking for security vulnerabilities making it easy for the development and management teams.
Differences Between SAST and DAST
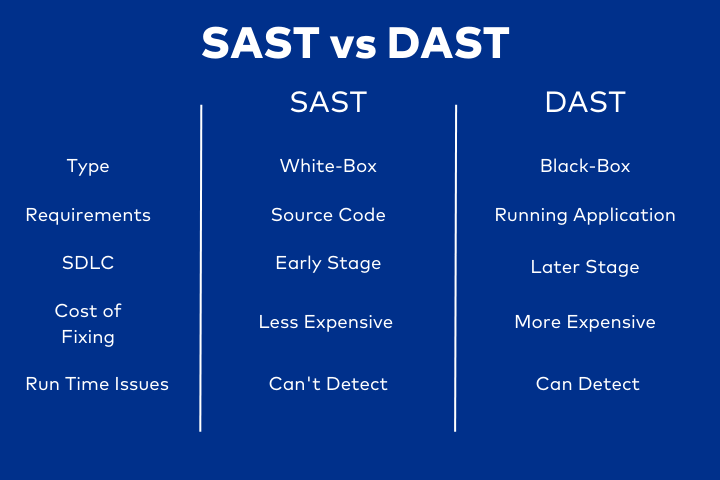
This section highlights the differences between SAST and DAST tools.
Static Application Security Testing (SAST)
- Static Application Security Testing (SAST) is a specialized application testing that analyzes an application’s source code without executing it.
- SAST is also known as code review, source code analysis, or white box testing.
- The testing is performed on the static source code (hence the term “static”) to ensure that it doesn’t allow for any vulnerabilities.
- The weaknesses can include missing security checks, unsafe usage of cryptographic functions, and poor input validation.
Dynamic Application Security Testing (DAST)
- Dynamic Application Security Testing (DAST) involves the inspection of the functionality of an application.
- DAST evaluates the security of the application, particularly in response to malicious attacks.
- DAST is used from a black-box perspective, meaning it tests from the outside in, not from the inside out.
- This allows for a more significant number of vulnerabilities to be detected and more applications to be tested.
How Does Astra’s DAST Tool Help?
Automated scanners are great at picking up vulnerabilities that are obvious to software. These are the low-hanging fruit. The more complicated part of testing is the unnoticed vulnerabilities that are usually left in automated scans.
Astra’s vulnerability scanner is equipped with natural hacker intelligence gathered from 1000+ vulnerability assessments and penetration tests (VAPT) done by our security experts on varied applications.
Astra’s Pentest is the only solution that gives you the manual and automated DAST. It is an end-to-end solution for all security problems.
Benefits of using Astra’s Pentest:
- Automated and Manual tests to make sure no vulnerability is left behind.
- 8000+ tests to keep your application safe.
- Easy, accessible reports that you can interpret at a glance with the dashboard.
- Collaborate with developers from within the dashboard.
- Get detailed steps on bug fixing tailored to your issues and know exactly how to reproduce vulnerabilities with video Proof of Concepts (PoCs).
- Why keep your security status private? Showcase Astra’s Publicly verifiable certificate.
- Post pentest, Astra shows a potential loss in $$$ for each vulnerability, making it easier for everyone to understand the impact.
- For each vulnerability, Astra gives an intelligently calculated risk score.

Conclusion
When it comes to security, no aspect is more critical than testing. Dynamic application security testing can help you find and fix vulnerabilities in your code before they become a problem. At Astra Security, we test software applications for bugs and vulnerabilities in the runtime environment providing you with proper steps to reproduce and fix the issue. As automated and manual dynamic security testing has its benefits, Astra’s solution includes both manual and automatic DAST, keeping our applications secure.
FAQs
What is the purpose of dynamic application security testing (dast)?
The purpose of dynamic application security testing or DAST is to scan for vulnerabilities within an application in its production environment. Apps in this stage mimic real-world behavior and as such helps in the detection of issues that may have been previously missed.
















