DAST tools help you dynamically test the production-ready application for critical security vulnerabilities proactively, eventually contributing to your shift from DevOps to DevSecOps.
Our security experts have handpicked the top 13 DAST tools, which focus on your non-negotiables, such as security test coverage, pricing, functionality, compliance testing, deployment, integrations, and continuous pentest capabilities.
13 Best DAST Tools in 2024
- Astra Pentest
- Invicti
- Nessus
- Acunetix
- IndusfaceWAS
- BurpSuite
- StackHawk
- ZAP
- Kali Linux
- W3af
- Nikto
- Ettercap
- Vega
Why Do You Need a DAST Tool?
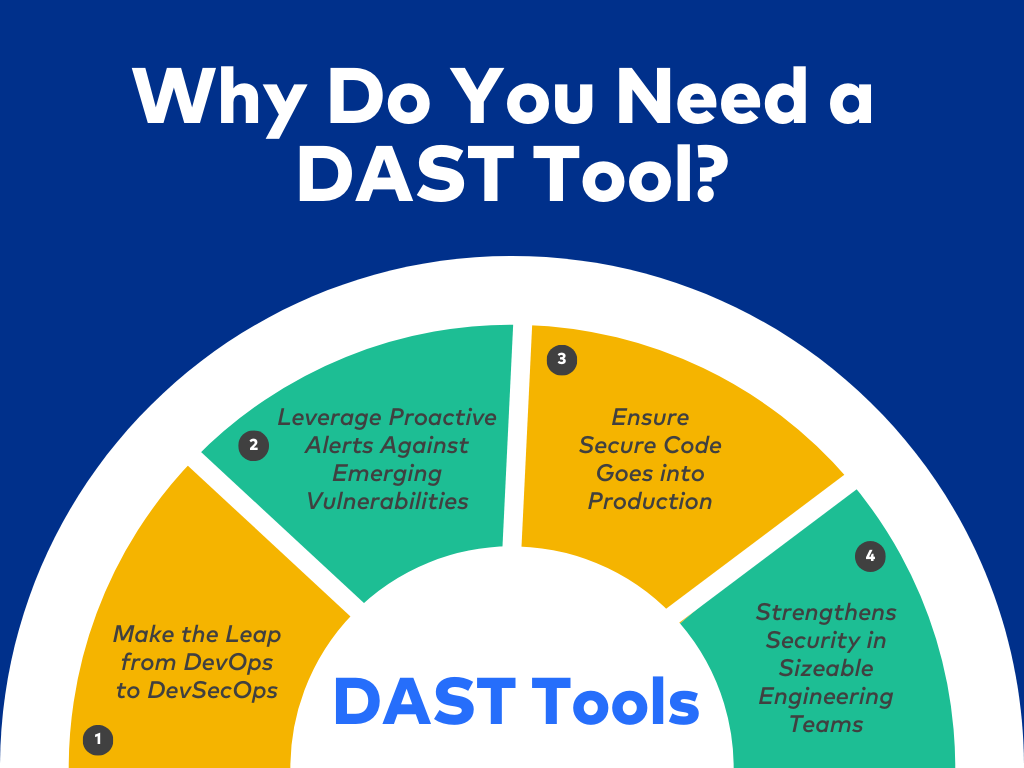
Make the Leap from DevOps to DevSecOps
Traditionally, security testing happens when a feature is in production or just about to reach production. This leads to several bottlenecks, delays, and duplication of work if critical vulnerabilities are found, which require major code factoring.
By automating security testing in all stages of development, DAST scanning tools enable your developers to identify vulnerabilities during the early phase of development.
Besides facilitating early detection and remediation, this fosters collaboration between your development and security teams. This helps you transition smoothly into a DevSecOps culture where security is prioritized throughout the SDLC pipeline.
Leverage Proactive Alerts Against Emerging Vulnerabilities
With the ever-rising volume of new CVEs discovered daily (nearly 80 a day in 2023), frequent scans are essential for avoiding potential threats. DAST scanners automate this process, systematically probing your web applications for security flaws and generating proactive alerts.
This allows developers and security teams to swiftly address these issues before attackers can exploit them.
Ensure Secure Code Goes into Production
By mimicking real-world attacks, DAST scanners help identify vulnerabilities like SQL injection or XSS flaws early on. Such early detection ensures that only secure code goes into production, saving time and resources compared to fixing a security breach after deployment.
Thus, besides fostering a secure code approach from the get-go, DAST scanners also play a crucial role in your company’s “shift left” security culture.
Strengthens Security in Sizeable Engineering Teams
In sizeable engineering teams, individual developers might write secure code, but unforeseen vulnerabilities can emerge when these components are integrated into a complex web application. This is where dynamic application security testing tools step in.
Integrating DAST scanning in your SDLC empowers you to address such weaknesses before they become critical issues, ultimately strengthening the overall application security posture and minimizing the wastage of resources.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Our automated scanner scans for 9300+ vulnerabilities
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Key Features to Look for While Choosing a DAST Tool
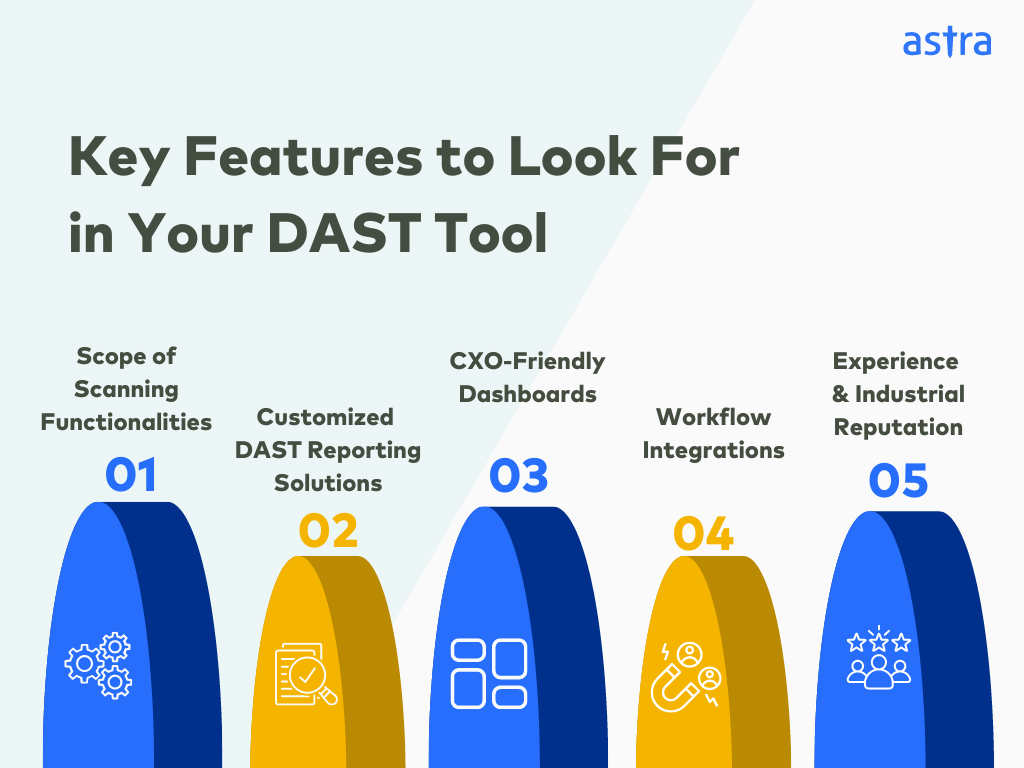
While companies and security developers leverage dynamic assessments, their specific considerations when choosing a DAST software provider differ significantly.
Simply put, while an enterprise favors a wide variety of test cases, CXO-friendly dashboards, workflow integrations, intuitive UX, and custom reports, security researchers and developers look for customization capabilities, depth of analysis, and exhaustive reports.
Top 3 DAST Tools For Enterprises Compared
| Features | Astra Pentest | Invicti | Nessus |
|---|---|---|---|
| Platform | Online | Online | Windows, macOS |
| Vulnerability Tests | 9300+ | 1400+ | Checks for 84000+ CVEs |
| SDLC/ Workflow Integration | Slack, JIRA, GitHub, GitLab, and Jenkins | JIRA, GitHub, GitLab, Kenna, and Bitbucket | IBM Security, Splunk, GitHub, and GitLab |
| Accuracy | Zero False Positives via Vetted Scans | False positives possible | False positives possible |
| Scan Behind Login | Yes | No | No |
| Compliance Scanning | PCI-DSS, HIPAA, ISO27001, & SOC2 | PCI-DSS, HIPAA, and ISO 27001 | HIPAA, ISO, NIST, and PCI-DSS |
| Custom Reports | Yes | Yes | Yes |
| Price | Starting at $199/m | Available on quote | Starting at $4,236/yr |
13 Best Dynamic Application Security Testing Tools [Reviewed]
1. Astra Pentest
Key Features
- Platform: Online
- SDLC/ Workflow Integration: Slack, JIRA, GitHub, GitLab, and Jenkins
- Accuracy: Zero false positives
- Scan Behind Login: Yes
- Compliance Scanning: PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: Starting at $1999/yr
Astra emulates hacker behavior to scan applications for 9300+ security tests. While expert-vetted scans ensure zero false positives, the convenient login recording Chrome extension enables authenticated DAST scans behind login pages without redundant reauthentication.
CTOs & CISOs love Astra Pentest because it helps them fix vulnerabilities quickly and move from DevOps to DevSecOps with seamless CI/CD integrations. Last year, Astra uncovered 2,000,000+ vulnerabilities for its customers, saving $69M+ in potential losses due to security vulnerabilities.
Pros
- Integrate effortlessly with your CI/CD pipeline
- Scan round-the-clock for vulnerabilities
- Leverage regularly updated scanner rules
- Collaborate with security experts with OSCP, CEH & CVEs under their name
- Generate custom executive and developer-friendly reports
Limitations
- Only a 1-week free trial is available
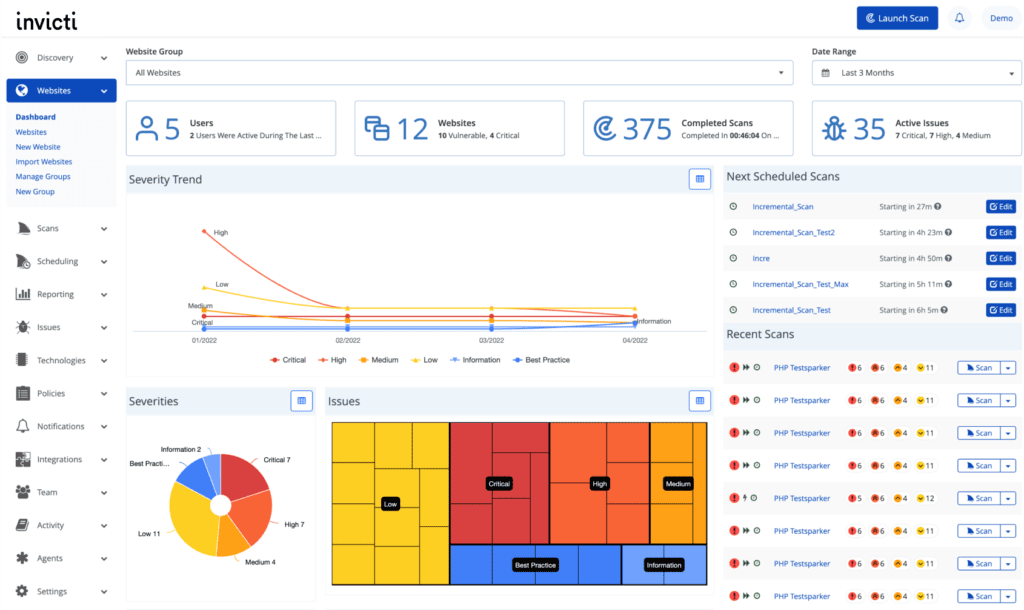
2. Invicti
Key Features
- Platform: Online
- SDLC/ Workflow Integration: JIRA, GitHub, GitLab, Kenna, and Bitbucket
- Accuracy: False positives possible
- Scan Behind Login: No
- Compliance Scanning: PCI-DSS, HIPAA, and ISO 27001
- Price: Available on quote
Better known for its web app security solutions, Invicti offers advanced crawling and vulnerability detection functionalities for first and third-party (open source) code with its mature DAST and IAST scanning tools.
Following a proof-based approach, its intuitive interface provides graphical representations of 250+ vulnerability test cases, making it easy for your team to understand and prioritize risks. Moreover, Invicti’s compliance readiness features help maintain security throughout the year.
Pros
- User-friendly and easy to set up
- Active support team
Limitations:
- GUI scan bugs have been observed at times
- Slows down while scanning large applications
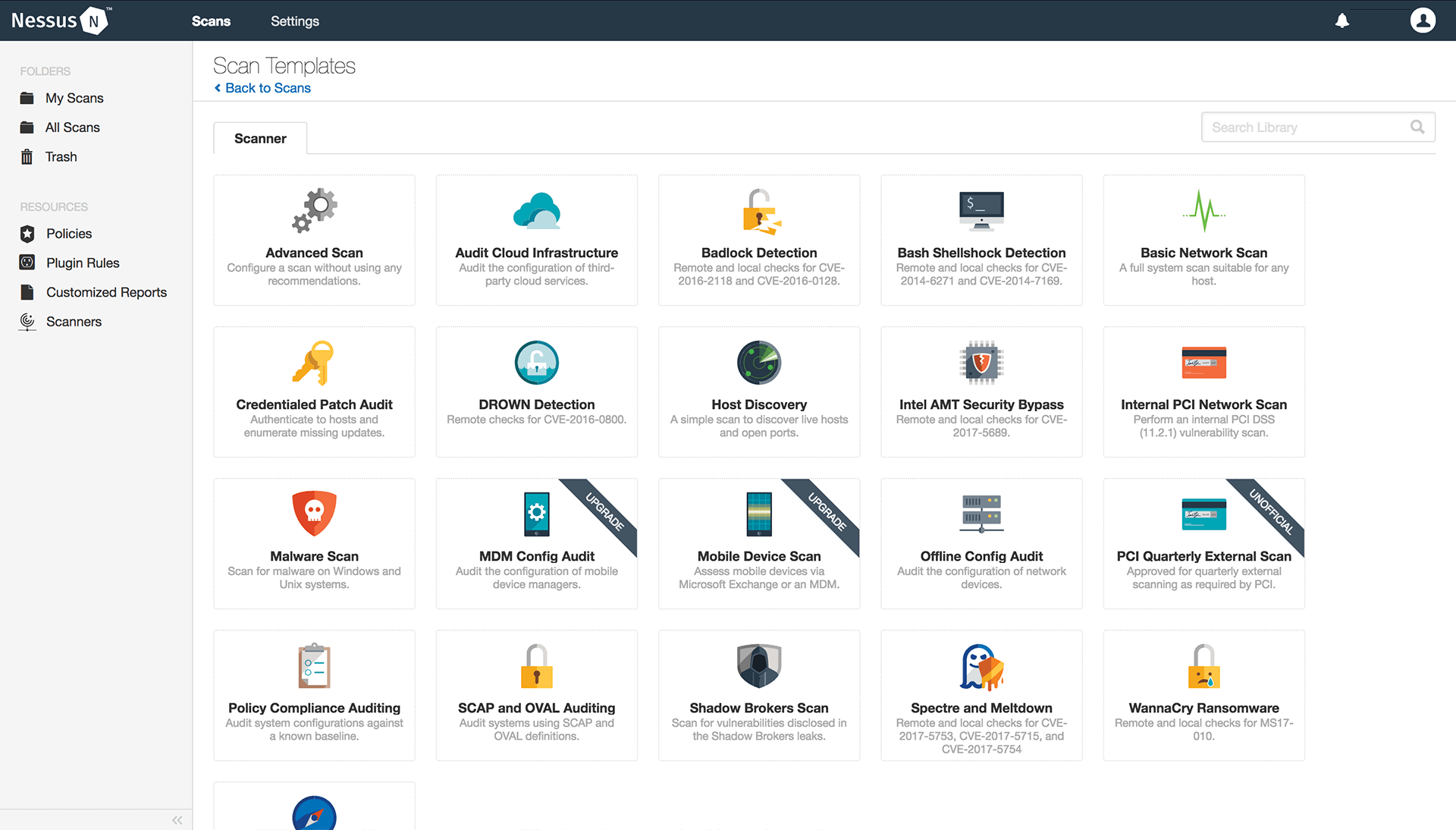
3. Nessus
Key Features:
- Platform: Windows, macOS
- SDLC/ Workflow Integration: IBM Security, Splunk, GitHub, and GitLab
- Accuracy: False positives possible
- Scan Behind Login: No
- Compliance Scanning: HIPAA, ISO, NIST, and PCI-DSS
- Price: Starting at $4,236/yr
Nessus goes beyond essential DAST testing tools by leveraging Tenable’s extensive vulnerability database to identify a vast range of web application vulnerabilities. With 500 prebuilt scanning policies, it helps automate the DAST process, saving you time and resources.
Further, Nessus supports various industry standards like PCI DSS, HIPAA, and ISO, ensuring compliance with regulatory requirements around the year.
Pros:
- Intuitive interface for simple navigation
- Automated Workflows for streamlined audits
Limitations:
- Scan durations can vary significantly
- Standard automation might not work with custom asset tags
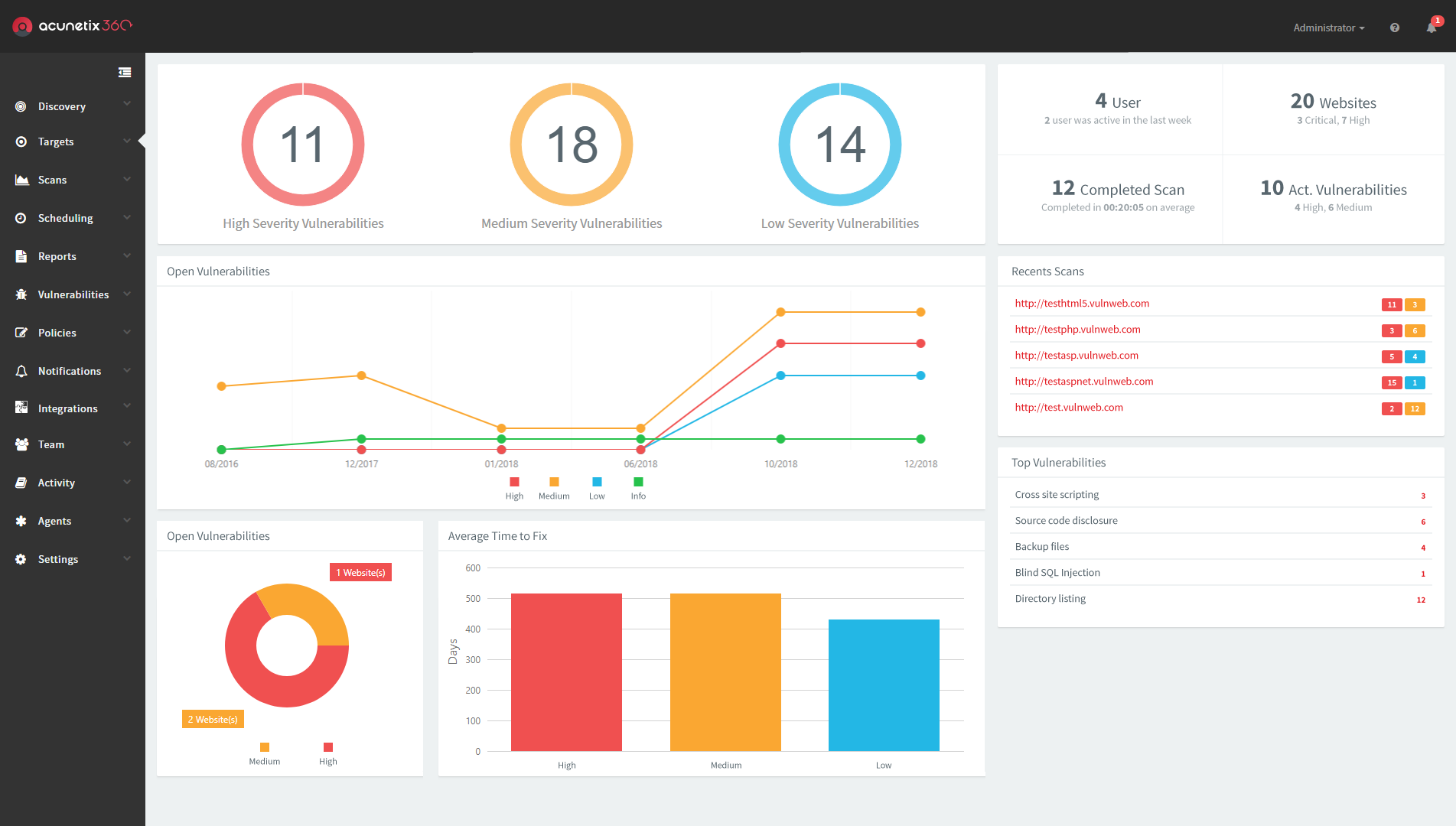
4. Acunetix
Key Features:
- Platform: Windows, macOS
- SDLC/ Workflow Integration: GitHub, JIRA, and Atlassian
- Accuracy: False positives possible
- Scan Behind Login: Yes
- Compliance Scanning: HIPAA, SOC2, NIST, and ISO 27001
- Price: Available on quote
Acunetix is a DAST scanner designed to run 900+ tests to scan for an extensive list of over 4,500 vulnerabilities, including widespread threats like SQL injection and XSS attacks. It integrates effortlessly with IDEs, CI/CD pipelines, and GRC platforms to streamline workflows.
Acunetix also provides detailed reports with exploit examples and proof of concepts to help developers fix vulnerabilities efficiently with clear remediation guidance.
Pros:
- Shallow learning curve
- Intelligent automated scanning tool
Limitations:
- False positives possible
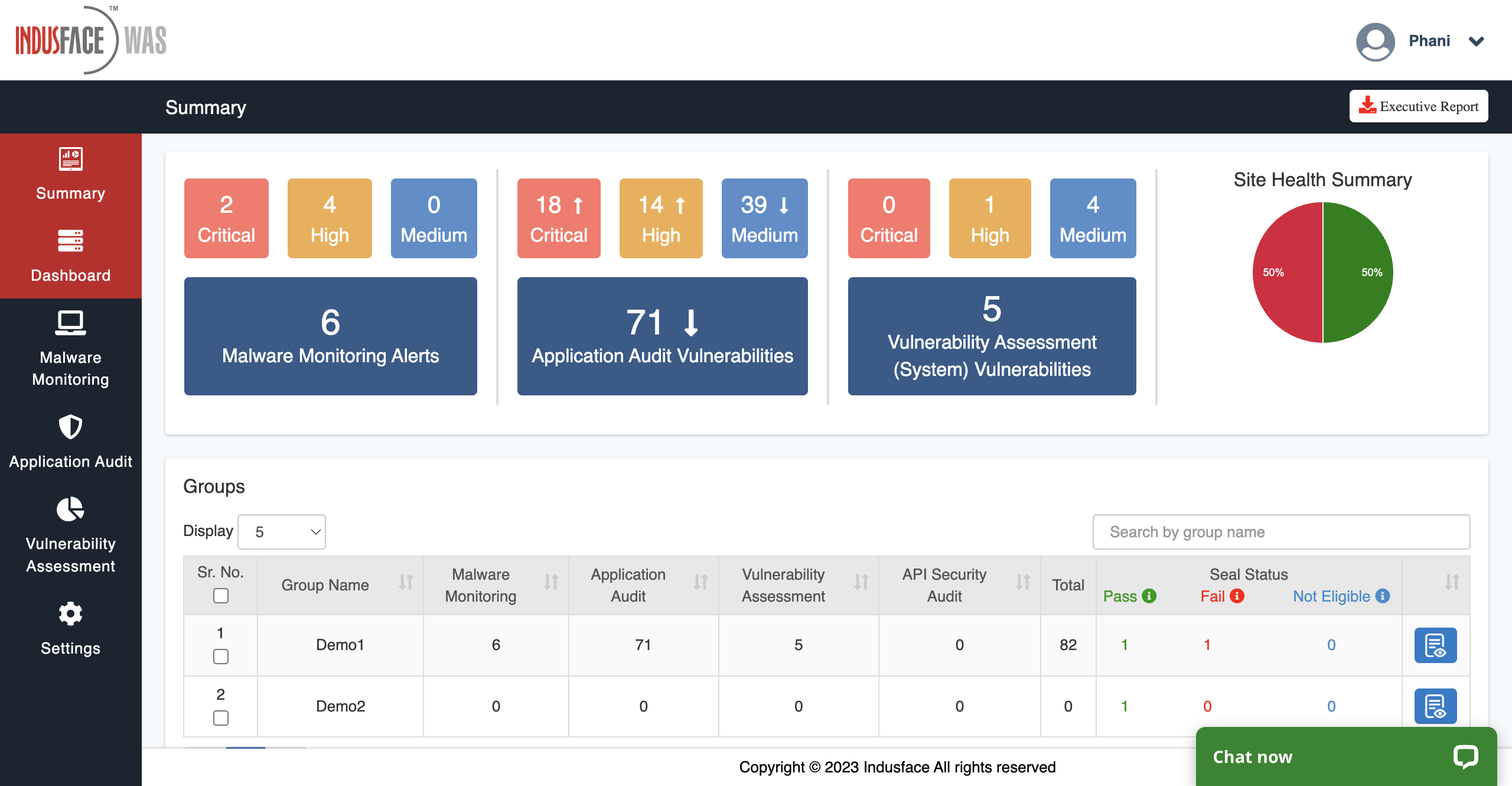
5. IndusfaceWAS
Key Features:
- Platform: Online
- SDLC/ Workflow Integration: JIRA, GitHub, Slack, and Microsoft Teams
- Accuracy: False positives possible
- Scan Behind Login: Yes
- Compliance Scanning: SOC2, ISO and OWASP
- Price: Starting at $199/app/month
IndusfaceWAS offers a comprehensive DAST solution that combines real-time monitoring with automated vulnerability assessments. It provides detailed reports with proof-of-concept documentation to improve the remediation turnaround.
Moreover, IndusfaceWAS also scans for vulnerabilities to support compliance testing across various industry standards, including SOC2 and ISO.
Pros:
- Quick support turnaround
- Intelligent automated scanning tool
Limitations:
- The interface could be more intuitive for first-time users
- Constant scan update notifications can clutter your inbox
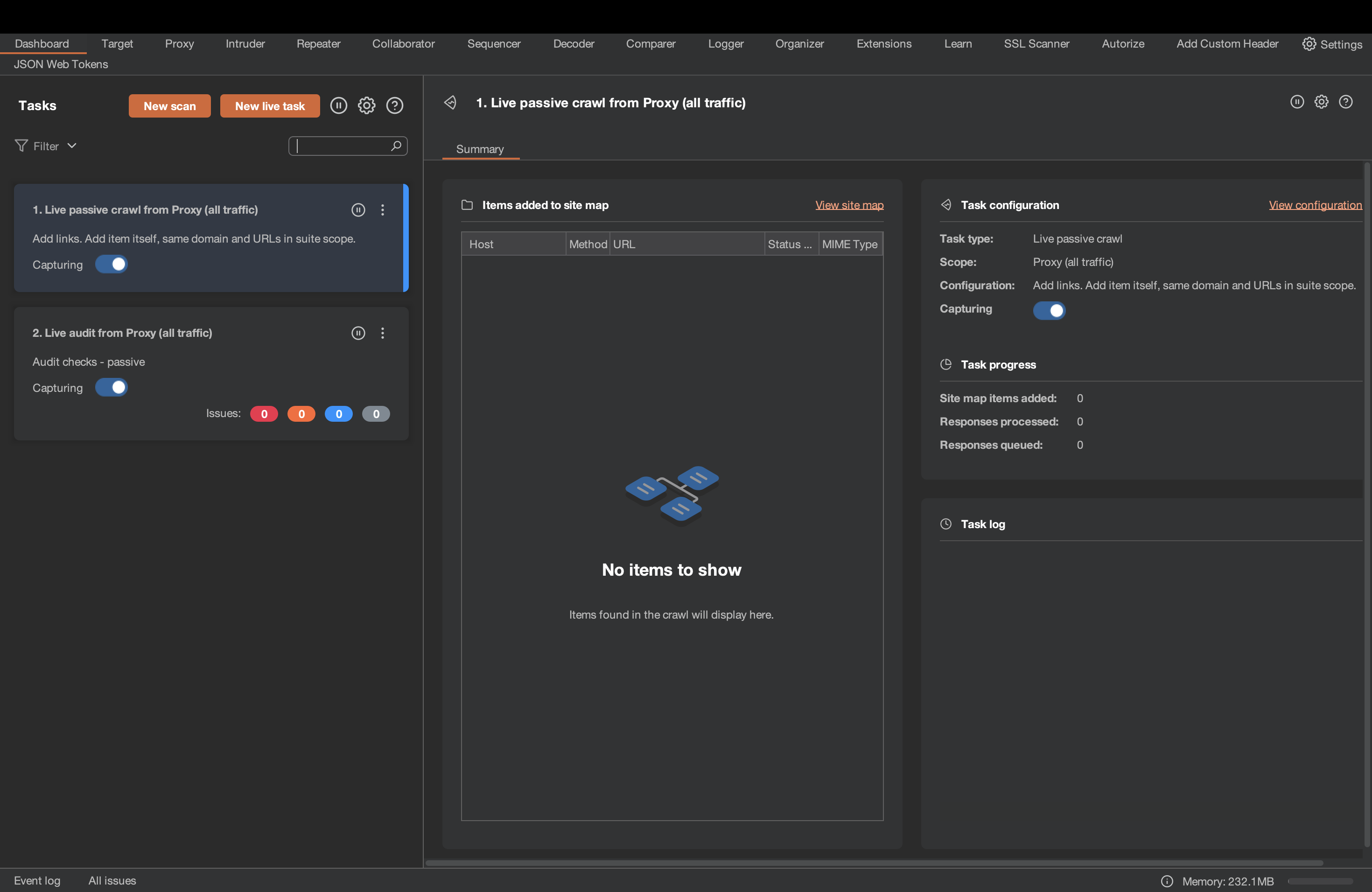
6. Burp Suite
Key Features:
- Platform: Online
- SDLC/ Workflow Integration: Slack, JIRA, Jenkins, and GitLab
- Accuracy: False positives possible
- Scan Behind Login: Yes
- Compliance Scanning: PCI-DSS, HIPAA, and GDPR
- Price: $449/yr/user
Burp Suite stands out as a DAST scanner that empowers you with a comprehensive toolkit for automated testing. It equips you to intercept and manipulate web traffic, automate repetitive tasks, fuzz parameters, and even brute-force logins.
With 2500+ test cases, Burp Suite also helps identify a wide range of vulnerabilities, including common ones like SQL injection and XSS. It facilitates various industry standards like SOC2 and ISO, ensuring compliance.
7. StackHawk (Open-Source Option Available)
Key Features:
- Platform: Online
- SDLC/ Workflow Integration: Slack, Snyk, GitHub, AWS, Atlassian, and Microsoft
- Accuracy: False positives possible
- Scan Behind Login: Yes
- Compliance Scanning: Soc2
- Price: $59/contributor/month
StackHawk is a dynamic code scanning tool explicitly built to automate security testing within your CI/CD pipeline. Focused on runtime and pre-production application security testing, find security bugs earlier in your development process.
StackHawk offers a free plan with unlimited DAST scans, which are automatable in your CI/CD for a single application. However, certain features, like customized scanning with expanded coverage, are only available in the paid versions.
Pros:
- Easy to integrate with CI/CD Tools
- Quality support team
Limitations:
- False positives are possible
- Scans can be time-taking
Top 3 DAST Tools For Engineers Compared
| Features | Astra Pentest | ZAP | Kali Linux |
|---|---|---|---|
| Target | Web apps, Mobile, API, Cloud and Network Infrastructure | Web applications | Online and physical systems, web applications, and networks |
| Pentest Capabilities | Automated, AI, and manual dynamic scanning | Automated and manual dynamic scanning | Unlimited scans for CVE scanning, exploitation, and post-exploitation |
| Deployment Capabilities | Online | Manual installation from source code pre-built packages and Docker | Installer packages for live boot and disk installation |
| Accuracy | Zero False Positives | False positives are possible | False positives are possible |
| Price | Starting at $1999/yr | Open-source tool | Open-source tool |
8. ZAP (Best Open-Source DAST tool)
Key Features:
- Target: Web applications
- Pentest Capabilities: Automated and manual dynamic scanning
- Deployment Capabilities: Manual installation from source code pre-built packages and Docker
- Accuracy: False positives are possible
- Price: Open-source tool
ZAP is a community-driven dynamic application security testing tool. It empowers security professionals to identify vulnerabilities by acting as a MiTM proxy, giving them granular control to intercept, analyze, and modify traffic between your browser and the target.
Beyond pre-built scanners, it also allows you to manipulate sessions, fuzz parameters, and launch brute-force attacks. ZAP also enables you to work alongside tools in your CI/CD pipelines and various bug-tracking systems
Pros:
- Streamlined user experience
- Advanced security testing capabilities
Limitations:
- Direct support options may be limited
9. Kali Linux
Key Features:
- Target: Online and physical systems, web applications, and networks
- Pentest Capabilities: Unlimited scans for vulnerability scanning, exploitation, privilege escalation, and post-exploitation
- Deployment Capabilities: Installer packages for live boot and disk installation
- Accuracy: False positives are possible
- Price: Open-source OS
While Kali Linux itself is a VAPT OS, it functions as a powerful platform for DAST tasks. Encompassing 600+ security tools, Kali offers a comprehensive toolkit for developers and security researchers, including ZAP, W3af, Nikto, and Ettercap.
Even beyond its pre-installed options, Kali provides extensive resources for customization, including documentation, tutorials, and community support to enhance the learning process and address troubleshooting needs
Pros:
- Offers advanced capabilities for in-depth application testing
- Consistent security updates and enhancements
Limitations:
- The initial learning process can be challenging
- CI/CD integrations might require additional scripting
10. W3af
Key Features:
- Target: Web applications
- Pentest Capabilities: Vulnerability scanning, threat exploitation, and attack simulation
- Deployment Capabilities: Manual installation from source code and pre-built packages
- Accuracy: False positives are possible
- Price: Open-source tool
The Web Application Attack and Audit Framework, or W3af, is a common open-source DAST tool software that helps you pinpoint CVEs in your web applications and assess their impact and severity.
It integrates seamlessly in your DevSecOps pipeline and allows you to leverage its multi-platform support to customize manual exploits for advanced testing needs.
Pros:
- Reduces manual effort through automation
- Scans authenticated sessions for deeper testing
Limitations:
- Interface can be challenging to use
11. Nikto
Key Features:
- Target: Web applications and servers
- Pentest Capabilities: Vulnerability and misconfiguration identification
- Deployment Capabilities: Manual installation from source code
- Accuracy: False positives are possible
- Price: Open-source tool
Nikto is a powerful open-source DAST tool provider that leverages its exhaustive vulnerability database of 6,700+ entries to scan web apps for vulnerabilities such as outdated software and setting misconfigurations.
By analyzing dynamic responses, Nikto can identify issues like open directories, insecure file permissions, and weak HTTP headers by analyzing dynamic responses. Moreover, its plugin support allows for customization to target specific vulnerabilities.
Pros:
- Simple and intuitive interface
- Free and open-source
Limitations:
- May need to manually ver=t results to ensure accuracy
12. Ettercap
Key Features:
- Target: Network infrastructure and web applications
- Pentest Capabilities: Passive network sniffing, active attacks, and network analysis
- Deployment Capabilities: Manual installation from source code and pre-built packages
- Accuracy: False positives are possible
- Price: Open-source tool
While Ettercap isn’t a traditional dynamic application security testing tool, it can be leveraged for the respective security analysis tasks. It allows analysts to simulate real-world attacks, such as MitM and session hijacking, to expose vulnerabilities in web applications.
Ettercap’s scripting and plugin support empowers you to automate repetitive tasks during these simulations and tailor the testing process to their specific application environment.
Pros:
- Collaborative community fuels innovative plugins
Limitations:
- Not compatible with Windows 10
- The interface could be clearer and more intuitive
13. Vega
Key Features:
- Target: Web applications
- Pentest Capabilities: Website crawling and automated dynamic scanning
- Deployment Capabilities: Manual installation from source code and pre-built packages with JRE
- Accuracy: False positives are possible
- Price: Open-source tool
Vega is a free and open-source DAST tool that functions as an intercepting proxy. It allows for deep traffic analysis while its web crawler scans the application to identify vulnerabilities, including SSL/TLS configurations.
Vega also supports various JavaScript extensions to help tailor the scans to your needs, making them customization-friendly.
Pros:
- Offers multiple testing modes
- Allows you to create custom attack modules to target specific vulnerabilities
Limitations:
- Has a limited number of elements it can crawl and analyze
How to Choose The DAST Software For Your Web Application?
Scope of Scanning Functionalities:
As an enterprise, focus on the breadth of scanning tests a DAST tool provides. Look for tools designed to address the OWASP Top 10 and SANS 25 vulnerabilities that offer a high accuracy rate to minimize false positives.
On the other hand, as a security engineer, leverage tools that help automate repetitive tasks and allow regression scanning. Focus on DAST software based on their strengths against specific asset types and ease of use for advanced dynamic scanning.
Customized DAST Reporting Solutions:
As an enterprise, look for tools that offer tailor-fitted DAST reporting solutions. This translates to generating executive reports for your management, simplifying complex security findings into concise summaries, and exhaustive reports for your engineering teams.
As a security researcher, focus on tools that generate detailed, exhaustive reports with vulnerability specifics, CVSS scores, and clear steps for replicating and patching identified vulnerabilities and attack vectors.
CXO-Friendly Dashboards:
As an enterprise, prioritize tools that offer a CXO-friendly dashboard with an intuitive interface. Look for tools that provide easy triggers, real-time scanning capabilities, key vulnerability reports, and simplify team collaboration.
Conversely, an easy-to-navigate DAST software with access to exhaustive vulnerability databases, asset specialization, custom views, and enhanced filters is a must for developers.
Workflow Integrations:
To eliminate communication roadblocks, companies usually prioritize dynamic application security testing tools that integrate effortlessly with your existing workflow tools like Slack and JIRA, as well as CI/CD pipelines, including GitHub, GitLab, and Jenkins. This fosters a smooth workflow and eliminates data silos.
Since developers and security researchers usually work individually, quality CI/CD integration is a bonus, but their primary focus remains on the functionalities that a DAST software offers.
Experience and Industrial Reputation:
As an enterprise, look for scanners with experience in scanning and pinpointing vulnerabilities in applications belonging to your industry. In addition to company-promoted information, independent reviews on sites like G2 and Capterra should be focused on to verify the above.
On the other hand, as a development engineer, focus on tools that have earned a reputation in the cybersecurity space for event-triggered, continuous, and ad-hoc scans for specific assessments.
Final Thoughts
While this list isn’t all-encompassing, it showcases some of the leading DAST scanners catering to the distinct needs of both enterprises and security analysts.
On one side, enterprises often prioritize comprehensive DAST tools for DevSecOps, like Acunetix and Invicti, with broad functionalities, detailed reporting, and seamless integrations. Meanwhile, developers usually favor tools like ZAP to prioritize specific capabilities, ease of use, and in-depth analysis.
With that said, platforms like Astra combine these benefits, offering a comprehensive solution ideal for both parties. A well-chosen DAST tool is critical to your journey to DevSecOps when combined with secure coding practices and proactive alerts.
FAQ’s
1. What is the purpose of the DAST tool?
DAST tools act like security guards for your web applications. They mimic hacker attacks to find weaknesses that could be exploited. By scanning running applications, they identify vulnerabilities like SQL injection before they cause problems.
2. What is the difference between SAST and DAST tools?
Static Application Security Testing (SAST) analyzes source code for vulnerabilities early in development (white-box). DAST attacks the running application like an outsider (black-box) to find exploitable weaknesses later in the lifecycle.

















Good job Ankit, It is a good list. I’ve missed some of these tools on my dast tool list, but of course Astra Security is in there 🙂