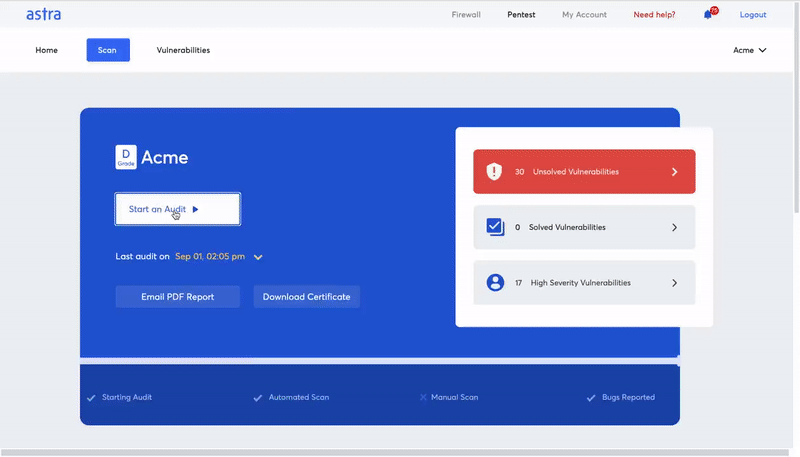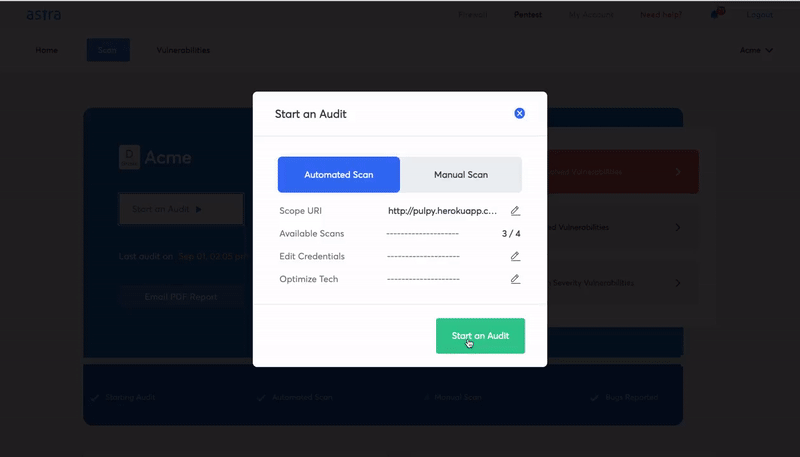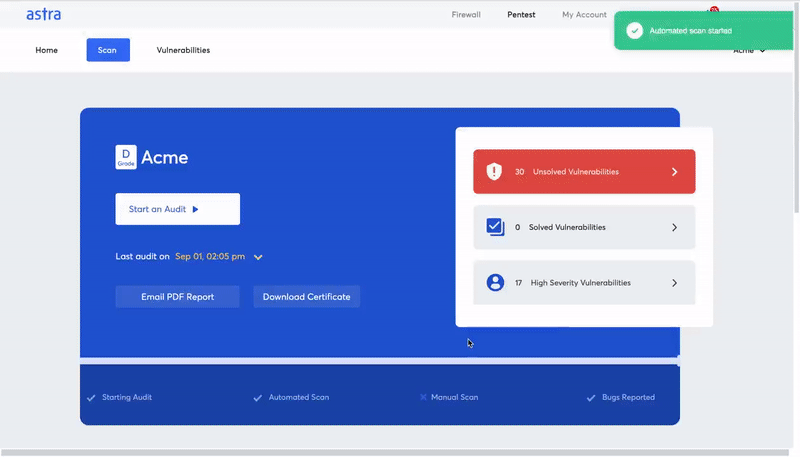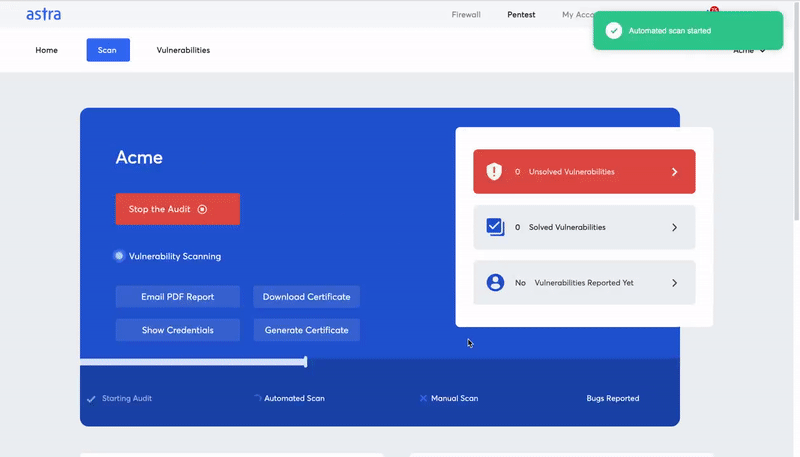
Vulnerability scanning is a process where an automated tool is used to scan IT networks, applications, devices, and other internal or external assets of an organization for known potential security loopholes and vulnerabilities.
At the end of every vulnerability scan, you receive a report that documents the vulnerabilities that were found along with risk scores for each vulnerability and in some cases security recommendations.
Importance of Vulnerability Scanning
You need a vulnerability scanning regime that fits the DevOps environment. It has to be fast, continuous, and accurate. Automated vulnerability scanning with a great vulnerability scanner is your best bet. Here’s what you achieve by conducting frequent scans.
Accurate reports
A machine learning-driven vulnerability scanner gets better at scanning your system with every use. Hence, the reports are increasingly accurate with a decreasing number of false positives. And you do not have to wait for weeks to get the vulnerability report.
Automatic scans
You can automate the vulnerability scanner so as to run a scan whenever there is a code update. Each new edition of an application invites new vulnerabilities. Hence, running an automated scan with every update can be a lifesaver.
Stay compliant and build trust
A lot of industries mandate security audits and vulnerability reports are a huge part of those exercises. So, it plays a significant role in compliance. Moreover, if you stay ahead of security threats, it is easier to build trust and ensure that clients are not spooked away by potential data security threats in your organization.
Vulnerability management also covers IT vulnerability monitoring and strategies and policies you exercise in order to detect and resolve security issues continuously before they are exploited.
Why is Astra Vulnerability Scanner the Best Scanner?
- Runs 8000+ tests with weekly updated scanner rules
- Scans behind the login page
- Scan results are vetted by security experts to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities from one place.
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Integrates with Slack and Jira for better workflow management
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

How does vulnerability scans work?
A vulnerability scanning software checks a network or an application for known vulnerabilities by referencing a database of details about various attack vectors (attack signatures). It is somewhat comparable to diagnosing a patient by symptoms.
Once the scan is done, a report is created that documents the vulnerabilities and assigns risk scores to them. The report may or may not include remediation guidance for the developers.
After the report is produced, the developers can take a shift-left approach to find the code bugs, configuration errors, or other factors that contributed to the vulnerabilities and remediate the issues.
Types of Vulnerability Scans
- Network-based scans scan network security to uncover anomalies on your IT network like open ports, unauthorized remote access servers, and vulnerable applications that may be active on the network.
- Host-based scans scan servers and workstations.
Other than that there are wireless scans, application scans, and database scans.
- An authenticated vulnerability scan can scan behind login pages. For instance, Astra Security has a login recorder extension that keeps the scanner authenticated even if the session times out. It allows the automated scanner to scan logged-in pages while not requiring the user to authenticate the session repeatedly.
- An unauthenticated scan is performed from the outside. It doesn’t require any credentials and doesn’t have trusted access.
Classification of vulnerabilities
The impact and exploitability of a vulnerability are calculated by taking multiple factors into account – the ease of access, authentication, its spread, the availability of mitigation, etc. Then exploitability and impact are concatenated to assign a severity score between 0.0 and 10.0 for each vulnerability. This is called the CVSS score (Common vulnerability scoring system).
The vulnerabilities can be classified into high, medium, and low severity categories depending on their CVSS score.
How is the CVSS calculated?
The CVSS score of a vulnerability is calculated based on three different metric groups – base, temporal and environmental. Firstly the CVSS base score is determined by assessing the intrinsic properties of a vulnerability that do not change with time or the user’s environment. This gives the base score.
The base score is then modified by taking temporal metrics into account that represent such characteristics of a vulnerability that change over time. Finally, the characteristics specific to a user’s environment are considered to get the environmental score. All these scores are applied to calculate the overall CVSS score.
Categories of vulnerabilities based on CVSS score?
- Vulnerabilities with a score between 7 and 10 are considered highly severe.
- Vulnerabilities scoring 4 to 6.9 fall into the medium severity category.
- Those with a score between 0 and 3.9 are put in the low severity category.
These scores allow the developers, and security experts to prioritize the vulnerabilities according to their severity so that the most critical ones are mitigated first.
Let us look at some easily detectable vulnerabilities which can be potentially disastrous for your software if left unchecked.
5 Top Vulnerabilities and Security Risks In Software
There are awareness-building projects and communities like the OWASP and NIST that document the most critical vulnerabilities at a given time. They publish lists of vulnerabilities that pose the most critical and pervasive threats. These lists are usually followed while checking scanning systems for vulnerabilities.
#1 Broken Access Control
Access control refers to the application of constraints on who can perform a certain action or access certain information. In the case of web applications, access control is usually maintained through authentication and session management.
Authentication ensures that the identity of the entity requesting access is true. Session management identifies the HTTP requests made by the user. Access control ensures that the entity is authorized to perform the operation or access the information requested.
#2 Cryptographic Failures
Cryptographic failure is a generalized phrase that describes a situation where sensitive data can be accessed without authorization. It refers to a condition where the data in transit, or at rest, is not secured through encryption.
Successful cryptography ensures access control by employing ciphers along with initialization vectors. Ignored or reused initialization vectors (an arbitrary number required alongside a secret key to encrypt data) increases the chances of information leaks.
#3 Injection
Injection has been on the list of critical vulnerabilities for a long time now. SQL injection (SQLi) and cross site scripting (XSS) are some of the most popular modes of injection attacks.
A malicious code input to the target program is processed as part of the command or query altering the program execution. Interfering with the preexisting parameters using SQL that control the exchange of data between a web app and its database gaining administrative access to the database.
#4 Insecure Design
Insecure design points to those vulnerabilities which come into existence in software owing to the lack of security implementations during its development.
For instance, the lack of input validation can make way for injection attacks. Implementing security in the software development life cycle can be a challenge as it demands a completely different perspective – threat modeling.
#5 Security Misconfiguration
Security misconfigurations are caused by inaccurate configuration or complete abandonment of security controls.
For instance, if a developer writes flexible firewall rules and creates network shares for convenience in a development phase and does not restore the original settings. Similarly, an administrator may authorize configuration changes for troubleshooting or some other purpose, then forget to reset them.
Tips To Manage Vulnerabilities
Here are some important tips to manage vulnerabilities found through vulnerability scans:
1. Set a well-defined scope for vulnerability scanning
Ensure that before the vulnerability scan is conducted, a good comprehensive scope is set in place without missing out on any of the important systems that need to be scanned. This allows the scanning of critical systems for the detection of any vulnerabilities and their remediation.
2. External and internal vulnerability scans
External vulnerability scans aid in the identification of vulnerabilities but also in the maintenance of compliance. This scan looks for any vulnerabilities in the external surface of one’s assets.
Internal scans scan within the assets for any vulnerabilities that could range from weak passwords to broken authorization.
3. Regular vulnerability scans
Carry out regular vulnerability scans rather than limiting them to once over a span of a few months. Continuous scanning of assets ensures that all and any vulnerabilities are detected before they are exploited resulting in heavy damages.
4. Run scans after major updates or changes to the system
Carrying out vulnerability scans after any major updates or changes to the systems allows for the detection of vulnerabilities in the new areas of updates allowing the remediation of vulnerabilities from the get-go.
5. Have an incident response plan in place
Have a plan in place for responding to cyber incidents, including who to contact, how to isolate affected systems, and how to restore systems after an attack. This is crucial for seamless recovery from any incidents that may take place despite best efforts to keep assets secure.
Vulnerability Scanning Challenges
Vulnerability scanning systems alone might not be feasible for larger organizations in the long run. Here are some of the challenges posed by vulnerability scans:
1. Can only identify known vulnerabilities
Vulnerability scans essentially detect vulnerabilities that are already present in a large vulnerability database. However, if there are any recent or new, or undiscovered vulnerabilities, a regular vulnerability scan wouldn’t be able to detect them.
2. Only shows vulnerabilities present during the scan
Vulnerability scans are point-in-time scans i.e. they can only find vulnerabilities that are already present at the time of the scan. However, say if a vulnerability popped up right after the scan, it would go undetected until the next scan. This again can leave the cyber assets vulnerable.
3. Might require access credentials for authenticated scans
Some scanning solutions might just offer unauthenticated scans of the internal vulnerabilities undetected. This would require authenticated scans which can scan behind login with the appropriate credentials through automated integration.
4. Isn’t it extensive enough to find all vulnerabilities
Vulnerability scans are a good cyber security solution for daily cyber health checkups. However, for long-term cybersecurity, comprehensive solutions like penetration tests are much more capacitated to find vulnerabilities through thorough scanning and exploitation.
5. Might require additional manual support
Vulnerability scans in themselves are an automated process. However, once done, the remediation of vulnerabilities based on the report produced might require the aid of a security expert.
How Frequently To Run Vulnerability Scans?
Ideally, vulnerability scans should be done bi-weekly or monthly once at least. Since vulnerability scans are quick and hassle-free, doing so is effortless and goes the additional step of ensuring safety.
At the very minimum, vulnerability scans and subsequent vulnerability detection and remediation of internal and external systems must be done quarterly if not monthly or bi-weekly.
Vulnerability Scanning vs. Penetration Testing
Both vulnerability scanning and penetration testing are important procedures to understand the security posture and resilience of an organization – its network, applications, and devices. They have some fundamental differences.
| Vulnerability Assessment | Penetration Testing |
|---|---|
| Vulnerability assessment is focused on detecting and categorizing vulnerabilities in a system. | Penetration testing involves exploiting vulnerabilities to draw insights about them. |
| It is a mostly automated process involving vulnerability scanning tools. | Penetration testing requires manual intervention on top of automated scanning. |
| It is almost impossible to achieve zero false positives with an automated vulnerability assessment. | Manual penetration testers can ensure zero false positives. |
| Vulnerability assessment often misses critical and complex vulnerabilities. | Thanks to the human element of penetration testing, it detects business logic errors that remain undetected in a vulnerability scan. |
| Automated vulnerability assessment takes significantly less time and money than pen testing. | Penetration testing is a consuming and expensive procedure and for good reason. |
Related: Learn Why Penetration Testing is Important
How to pick a Vulnerability Scanner for your organization?
There are a lot of vulnerability scanners in the market with overlapping features. It is difficult to judge a vulnerability scanner by how many tests it conducts or how fast it reports. Those are all important qualities but are present in a lot of good scanners.
When it comes to vulnerability scanning, the user experience can be improved a lot with small additional features.
Scan behind login: if a vulnerability scanner can scan behind login without repeated authentication, it saves you a lot of time and effort.
Pentest compliance: It helps you visualize in real-time which compliance regulations you might pass or fail according to your vulnerability status.
CI/CD integration: If a vulnerability scanner integrates with your CI/CD pipeline, it can run a scan whenever you push new code.
Features like these make a lot of difference when you are trying to make security a continuous part of your development drives.
The best vulnerability scanning tool – Astra Pentest
Vulnerability scanning is usually an automated process where you just determine the scope of the scan and the rest is done by the tool. That means choosing the right tool for the purpose is important. The automated vulnerability scanner by Astra Security sets the global benchmark in this respect.
The intelligent vulnerability scanner by Astra conducts 8000+ tests to detect a wide range of vulnerabilities including but not limited to those listed by OWASP, SANS, and NIST.
Astra Security has set the bar high by making the entire process incredibly user friendly. Take, for instance, the login recorder which allows the automated scanner to scan behind the login pages without requiring the site owners to authorize it repeatedly.
Your vulnerability scanning experience with Astra is controlled through an interactive dashboard where you can visualize the vulnerability analysis and remediation status. The security experts at Astra also ensure that your vulnerability report does not have false positives.
The Pentest Compliance feature launched by Astra also shows you what all compliance regulations you meet or fail to meet according to the state of vulnerabilities found in your system during the scan.
In fact, you can integrate platforms like GitHub to make your remediation effort independent from the dashboard. You use the most competent vulnerability scanning and pentest tool to detect vulnerabilities in your system without losing any time reinventing the workflow.
To Conclude
Vulnerability scanning is an automated tool based procedure, hence, the importance of choosing the right tool cannot be emphasized enough. The importance of converging DevOps with DevSecOps also needs some extra stress in the context of vulnerability management. It is always easier and less expensive to find and deal with vulnerabilities during the software development life cycle. In fact, you should partner up with a pentesting company that is comfortable with both static analysis of code and dynamic analysis of the application in production. It always helps if your vulnerability scanning report comes with zero false positives.
FAQs
1. What is the cost of vulnerability scanning?
The monthly cost of vulnerability scanning for web applications is between $99 and $399. Check out our pricing.
2. How much time does it take to conduct a vulnerability assessment and penetration testing?
It usually takes 4-7 days to complete the process. After which you can fix the issues identified in the test and run a rescan. The rescan takes half the time needed for the initial test. Get a security audit with 1250+ tests, right now!
3. How often should I conduct vulnerability scans?
The industry best practice is to run vulnerability scans at least once a quarter. However some verticals may require more frequent scans. Scan your website now!
4. Can I have continuous scans for new product versions?
Yes, you can integrate CI/CD platforms with Astra Pentest suite, thus enabling continuous scans for product updates.