A variety of web applications employs database systems for the provision of backend functionality. A widely used language used to query, operate, and administer database systems is Structured Query Language (SQL). Owing to its rampant use in web applications globally, SQL-powered databases are easy and frequent targets for cyber-criminal acts, the severity of which depends solely on the intricacies of each system being targeted.
SQL injection attack explained
An SQL injection attack is one of the most frequently occurring web hacks prevalent today, wherein an attacker uses web page inputs to insert a malicious code in SQL statements. It usually occurs when a web page asks for user input like username/userid. The attacker uses this opportunity to insert a SQL statement which ends up running on your database without your knowledge.
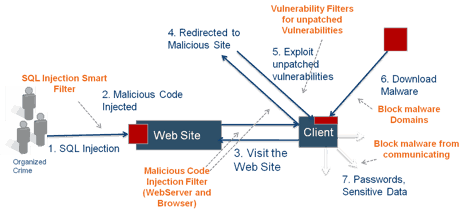
A SQL Injection Attack Workflow
The implications of such an attack can only be dependent on the web application, and how it processes the attacker-supplied data prior to building a SQL statement. Possible security ramifications vary from authentication bypass to information disclosure to extending malicious code to other application users. The risk factor extends to a large number of websites since SQL (Structured query language) database is supported by various web platforms like WordPress, PHP, Joomla etc.
Ramifications of a successful SQL attack
An SQL injection is considered as a high severity vulnerability. The extent of to which the damage can be caused can solely be left to the attacker’s skill and imagination, and the existence of countermeasures, like low privilege connections to the database server, to brace such an attack.
Once compromised, a hoard of sensitive information once concealed by the database now becomes at the mercy of the attacker. Consequentially, the attacker can now steal sensitive data from the database, execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases gain control of the operating system.
Typically, the following kind of attacks are possible once an SQL injection occurs:
- The attacker can bypass the authentication to log onto the application, potentially with administrative privileges, without supplying any of the required credentials.
- The attackers can comprise data integrity by altering contents of the database, deface a web page or insert malicious content into other innocuous websites
- The attacker can compromise the availability of data by deleting log or audit information in a database
- The attacker can jeopardize the operations of the host operating system via command execution through database
Safeguarding your site from SQL injection attacks
Although an SQL injection attack is amongst the most common application layer attacks affecting web applications globally, it is extremely simple to avoid SQL Injection vulnerabilities in your code.
The primary approach is to validate user-supplied data, which can be done by whitelisting or blacklisting. Moreover, another approach to defending your site against SQL attacks is to construct SQL statements such that any form of user input cannot alter the meaning logic of the SQL commands.
-
Input validation
Input validation incorporates the use of two approaches to defend against an SQL injection: blacklisting and whitelisting. Blacklisting involves removal or replacement of known malicious characters from user input. Although this method is widely used, it is not as effective as whitelisting. An attacker can circumvent the filter and inject malicious SQL statements. On the other hand, whitelisting examines every character in the user input for malicious content and only allows inputs containing all characters which conform to the permitted list.
2. Secured SQL statements
In addition to stringent input validation, it is imperative to employ parameterized queries in ASP.NET, prepared statements in Java, or similar techniques in other languages making up the web application. Fortifying the SQL statement in this way would ensure escaping of perilous characters before the SQL statement is passed to the underlying database system.
3. Routine Audit
Routinely test your applications using both static and dynamic testing for any potential SQLi vulnerabilities.
How Astra can guard you against SQL Injection
Astra’s Web Application firewall scans in real time to mitigate against commonly occurring web application flaws, including SQL injection. It’s cloud-based security platform enables you to manage your application security program, effortlessly track progress, and educate your company’s employees on avoiding and repairing SQL injection and other security flaws through e-learning materials.

















[…] Injection: Even if the best defense mechanisms are in place to prevent injection attacks, information obtained through the query logic code (snippet from server error messages) might […]
[…] 7 database API abstraction layer became vulnerable to an SQL Injection attack. The vulnerability SA-CORE-2014-005 impacts all Drupal core 7.x versions prior to 7.32. This […]
[…] Joomla 3.7 became victim to an SQL Injection Vulnerability: CVE-2017-8917. Easily exploited, the vulnerability stems from a new component, com_fields, […]
[…] Ajaxcart, EM (Extreme Magento) Quickshop, MD Quickview, SmartWave QuickView were discovered having SQL injection vulnerability. These are some of the most widely used extensions and are used in several different themes, […]
[…] Not Trust Those Inputs: Vulnerabilities like SQL Injection and Cross Site Scripting are one of the most exploited on web apps. Be it WordPress, Magento or […]
[…] the source of the webpage causing the redirect/pop-ups. In the case of Opencart it is caused due to SQL injection vulnerabilities in the store, allowing the hacker to add the malicious code to the database. In the case of […]
[…] execution flaws – an attacker injects malicious codes to gain administrator privilege. While SQL Injection attacks form 40% of total vulnerabilities encountered by Joomla, Drupal and WordPress are equipped […]
[…] página da Web, causando o redirecionamento / pop-ups. No caso do Opencart, ele é causado devido a vulnerabilidades de injeção de SQL na loja, permitindo que o hacker adicione o código malicioso ao banco de dados. No caso do […]
[…] code. This is an easy way to get entry inside the website without doing much. Attacks like XSS and SQL injection are direct consequences of the lack of input sanitization. Recently, Joomla patched an either […]