Undoubtedly, blockchain technology has seen a widespread adaption in recent years. Apart from initial adaption into cryptocurrencies, today it is being used in healthcare, real estate, smart contacts, etc. However, improper implementation of the technology has also been the cause of many blockchain security issues. This can make the blockchain vulnerable, allowing attackers to perform several malicious activities. Such as delaying the working of the chain, reversing the transactions done on the blockchain, stealing the private keys of users, and much more.
For instance, recently the price of ‘Safedollar’ (a type of stablecoin cryptocurrency) which was always meant to be of fixed value against the dollar dropped to zero because of a cyberattack. The preliminary reports show that hackers exploited a flaw in the algorithm of the coin. Moreover, blockchain security issues can have wider repercussions for the applications that this technology is used.
According to IBM,
While blockchain technology produces a tamper-proof ledger of transactions, blockchain networks are not immune to cyberattacks and fraud. Those with ill intent can manipulate known vulnerabilities in blockchain infrastructure and have succeeded in various hacks and frauds over the years.
This article explains, what is a blockchain and some major blockchain security issues. Also mentioned are means to prevent those issues.
If you want to learn in-depth about blockchain technology and different aspects of blockchain security, check out our article – An Introduction to Blockchain Security.
What is a Blockchain?
Merriam-Webster dictionary defines blockchain as,
A digital database containing information (such as records of financial transactions) that can be simultaneously used and shared within a large decentralized, publicly accessible network.
To put it into simple terms, consider it as a giant distributed database. A database that grows over time with transactions and in which the previous records are immutable.
Since the database is distributed, different nodes may have different opinions about the records inside it. This could have raised serious issues in a blockchain so much so that the technology may not have even survived.
But this problem was solved by the use of cryptography, more specifically, the hash functions which ensure a unique signature for each block on the chain. So every user on the blockchain can now independently verify and agree upon the same records.
While the above issue was fundamental in nature, other blockchain security issues may crop up in a functioning blockchain.
Working of Blockchain Technology
Often the terms ‘blockchain’ and ‘cryptocurrency’ are used synonymously but the two things are quite different. Cryptocurrencies are the most popular applications of blockchain technology. This technology has slowly found its applications in other sectors too.
So, in order to explain how blockchain works, the example of cryptocurrencies is given here.
Let us say, Elon wants to send Jeff one coin called Astra coin over the blockchain. So the first thing that you need to understand is public-key cryptography. If you are not familiar with it, read about it and return to this article.
To put it in simple terms, owning a crypto coin is basically having a key pair associated with that coin. Now, to perform the transaction, Elon will need the following things:
- The private key associated with the Astra coin that Elon holds
- Elon’s address on the blockchain (his public key)
- Jeff’s address on the blockchain (his public key)
- and of course, the amount should be present with Elon that he wishes to send.
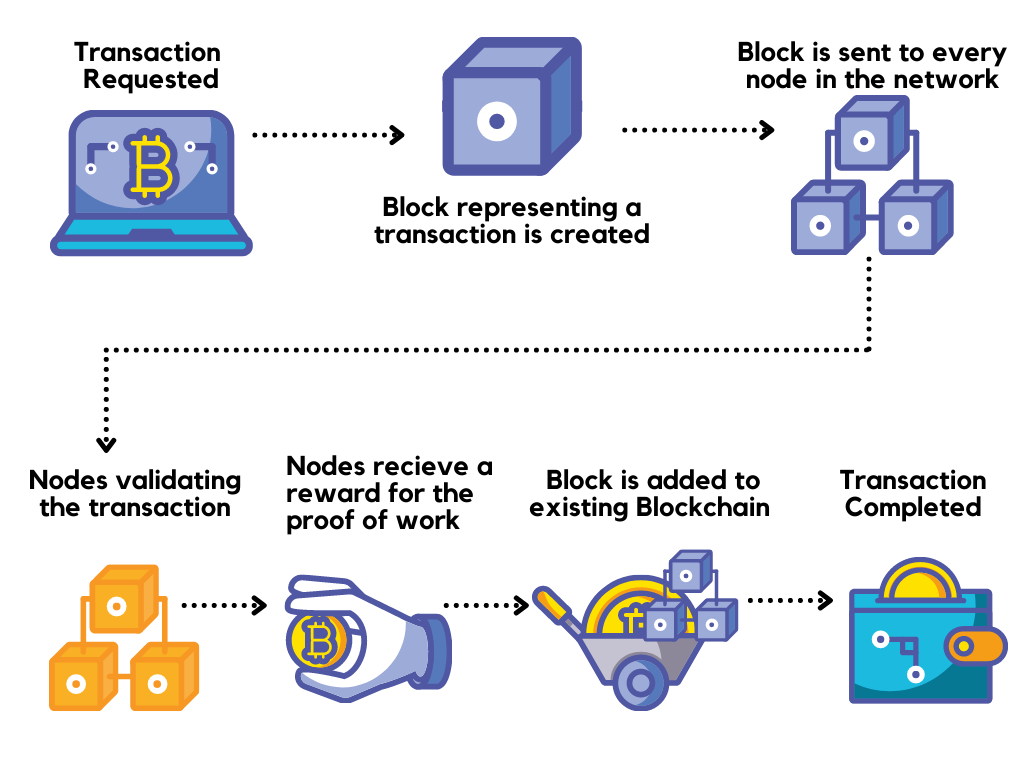
A Simple Example
In order to send one Astra coin, Elon will authorize the transaction by signing it with his private key. Afterward, this message will be broadcasted over the network.
Now, nodes on the network will see this message and verify it by Elon’s public key (that’s how key-pair works). After verifying the authenticity of the message, the nodes will also see if one coin is present at the sender’s address to avoid basic blockchain security issues. It will be then grouped with a bunch of other transactions.
Now comes into the picture, ‘Miners’. They would be working to find the valid cryptographic hash for this bunch of transactions which would make it into a block.
For example, in the case of the Astra coin, a valid block is one whose hash ends with the alphabet ‘a’. So, miners would be adding a random number called nonce to the bunch of transactions. They would keep changing the nonce until the hash of the whole bunch ends with the alphabet ‘a’ (it’s a hit and trial). Once found, it would be called a valid block and propagated over the network. Thus that block would be added to the blockchain and the transaction would be complete.
Now the same process would repeat over and over, adding newer blocks to the chain. Of course, there are other nuances to it like, miner’s fee, wallet splits, etc which can be ignored as of now to understand the basic working of a blockchain.
Now if you think objectively outside of the cryptocurrency framework, a blockchain works via the consensus of its participants. Proof of work defines what records go into blockchain and at its core lies cryptography which is responsible for trust in the blockchain.
6 Types of Attacks on Blockchain
While blockchain technology uses an immutable ledger, there are some blockchain security issues that can threaten even the basic nature of the technology. Let us now take a look at some prominent among them one by one.
1. 51% Attacks
Like we discussed above, miners play a key role in validating transactions on the blockchain and thus help it grow further. Blockchain technology makes decisions based on popular support. For instance, sometimes two blocks are mined at the same time with conflicting transactions. In that case, the block which gets majority approval on the network is kept in the chain and the other becomes stale.
Now, if a group of malicious hackers manages to obtain control over 51 % or more of the mining power, the results can be disastrous. The hackers can then, use their position of the majority to cancel transactions and perform fraudulent transactions. They may even be able to re-write some of the blocks but re-writing the whole blockchain (although theoretically possible) would be practically impossible.
Blockchain security issues like the 51% attack are more likely to happen at the early stages of the chain. At a time when very few miners are present on the network, it would be possible to get hold of 51% of mining power.
Sybil Attacks
Named after a famous book character, in this type of attack, an attacker creates multiple fake nodes on the network. Using those nodes the attacker can obtain majority consensus and hamper the transactions on the chain. So, a large-scale Sybil attack is nothing but the 51% attack.
For blockchain security issues like Sybil attacks, many blockchains use proof of work and proof of stake algorithms. While these algorithms do not entirely prevent such attacks but simply make it infeasible for the attacker to perform them.
2. Double Spending Attacks
One prominent feature of physical cash is that you cannot pay using the same bill at two different places (unless you are a magician or a fraudster). On the contrary, digital assets can easily be replicated, after all, it’s all just bits of 1s and 0s.
So, in the example above, Elon can try to send the same Astra coin to two different wallet addresses, that is of Jeff and Mark respectively. This type of attack would be called a double-spending attack.
Generally, there are mechanisms built in the blockchain to prevent such types of attacks. For instance, if the coin is sent to Jeff in the first block, the transaction to Mark will be ignored in the subsequent blocks.
But in case both the transactions made it to two different blocks mined at the same time, the block with the highest number of confirmations from the nodes on the network will be kept and the other will be ignored after some time. However, this mitigation to blockchain security issues like the double-spending attacks comes with its own disadvantages.
For example, Mark would still be expecting one Astra coin in his wallet. As a result, generally, users wait for at least 6 more blocks to be mined (as suggested by Satoshi Nakamoto in his white paper) before being really sure about getting the coin. Moreover, if a motivated attacker is able to perform a 51% percent attack as mentioned above, they can easily perform the double-spending attack afterward.
3. Routing Attacks
One thing that we can easily see by now is that blockchain technology requires a robust network to function. The ISPs connect to each other and share route information via the BGP (Border Gateway Protocol). This protocol is old and has some vulnerabilities that an attacker can exploit.
For instance, an attacker controlling an ISP can publish a false route and thereby deny transactions for some nodes or even partition the blockchain network in half!
Suppose, in the example above, Elon’s node is located at 100.0.0.0/16 (/16 is the IP prefix). Now, if an attacker propagates a route to 100.0.0.0/17 via the BGP, soon this info will be updated in all the routers (that’s how BGP works by sharing route info with neighbors). As a result, the data meant for Elon will be diverted to the entry specified by the attacker.
This is because when BGP is presented with two conflicting routes (100.0.0.0/16 by Elon vs 100.0.0.0/17 by the attacker), it selects the one with a longer prefix.
Blockchain security issues related to routing can have serious implications as in 2014 a hacker managed to perform the routing attack. This allowed the hacker to prevent the blocks mined by miners from propagating over the network. Instead, he/she used the info to claim the work done as his/her own and thus was rewarded with mining fees.
4. Private Key Security Attacks
As mentioned earlier, public-key cryptography is at the core of blockchain technology. Therefore, improper implementation or handling of public-key cryptography can cause some serious blockchain security issues.
If the key signing is poorly implemented in your blockchain (for instance using the same key for multiple signing instead of a Merkle tree), it can allow an attacker to obtain your private key from the public key. Having control of your private key basically means owning all the data associated with you in a blockchain.
In the case of cryptocurrencies, owning all your coins. Although, the chances of this happening are very less unless you use really buggy code for your blockchain. The major issue is the improper handling of your private key. For example, storing it in infected computers, public pastes, etc. In 2020 around $300k worth of cryptocurrency was hacked because the user left the public key in Evernote.
5. Selfish Mining Attacks
A selfish mining attack is exactly what it sounds like.
Suppose Jeff is sending few Astra coins to Mark with a delay in such a way that the separate transactions make into multiple different blocks (with a bunch of other transactions from people sending coins to each other). Meanwhile, Elon and Bill are competing as miners to validate these transactions.
Now suppose Elon discovers the valid block for the first transaction but instead of propagating it over the network, he starts to work to find the second valid block for the next transactions. He continues to make his secret chain of blocks until the main blockchain is one block behind his secret chain. It is then that he strategically reveals his chain to the network.
As some blockchain protocols are designed, in the case of two conflicting forks the longest chain is kept. Hence, Elon can now claim a higher mining fee.
In contrast, if Elon would have published the valid block as soon as he found it, he and Bill would have started competing from the same level for the next block.
Thus, in the selfish mining attack, an attacker uses his advantage position to hold for longer to maximize profits. However, this strategy is also risky. If Bill or some other miner would have found the next block before Elon and published it, all his work would be useless.
This seems risky and non-profitable at first glance but an analysis using Markov chains has shown that selfish mining indeed works!
6. Vulnerable Smart Contacts
Smart contacts are basically agreements written in code that use blockchain for record-keeping.
For example, in real life, if you loan someone some money, you get a periodical interest until the borrowing period is over after which you get back your principal amount.
Now, this can be translated into code and using cryptocurrency in place of real money. The good thing is that you require no intermediary like a bank. Once the contract is in place there is no means to change it.
However, sometimes these contacts are poorly coded. This allows an attacker to find potential flaws in the code and exploit them. This was seen in the case of DAO when an attacker was able to find such a flaw and steal $50 million worth of cryptocurrency.
Preventing Blockchain Security Issues
- Using Proof of Stake instead of Proof of Work can help prevent the 51% attacks. As the decision will be made by users who are already in control of the majority of coins.
- There are a number of algorithms to prevent Sybil attacks. One of which called Proof of Work is implemented in the majority of cryptocurrencies.
- It is important to keep a check on the mining pools of your blockchain. Ensure that any pool that breaches a limit of 40%, gets some of its miners diverted to other pools.
- The use of secure routing protocols (one with certificates) can help prevent routing attacks on the blockchain.
- Smart contacts need to be thoroughly vetted for any bugs by experts before implementation.
- Build a robust community of your blockchain users and update them via emails, newsletters, etc regarding safe private key storage practices.
Conclusion
Finally, it can be said that blockchain is indeed a very revolutionary technology that has merged the whole exercise of consensus-building with the rigor of code. A blockchain is as secure as its underlying code. Therefore, before going public with your blockchain, run thorough tests and audits for any blockchain security issues. As the financial value of your blockchain increases, so does the attacks on it. While a blockchain security services may seem costly, it’s nothing compared to the losses you may face if an unfortunate attack happens on your blockchain-based app. Regular in-depth security audits and pentesting will prevent your blockchain from going defunct in the future.
















