A CERT-IN Certificate is awarded to a company after a successful Vulnerability Assessment & Penetration Test (VAPT) by a CERT-IN empanelled cyber security organization like Astra. The VAPT should be performed per the guidelines set by CERT-IN.
Often viewed as a simple qualification, it is an exhaustive process overseen by the Indian Computer Emergency Response Team (CERT-IN). The primary aim is to verify adherence to established cybersecurity standards through a security audit of your IT infrastructure.
Although it also offers a variety of benefits, before moving forward, let’s delve deeper into what CERT-IN certification entails.
What Does CERT-IN Certification Entail?
CERT-IN, the Indian Computer Emergency Response Team, is a government body under the Ministry of Electronics and Information Technology (MEITY). It is the national nodal agency for cyber security incidents; its primary aim is to strengthen India’s cyber defenses.
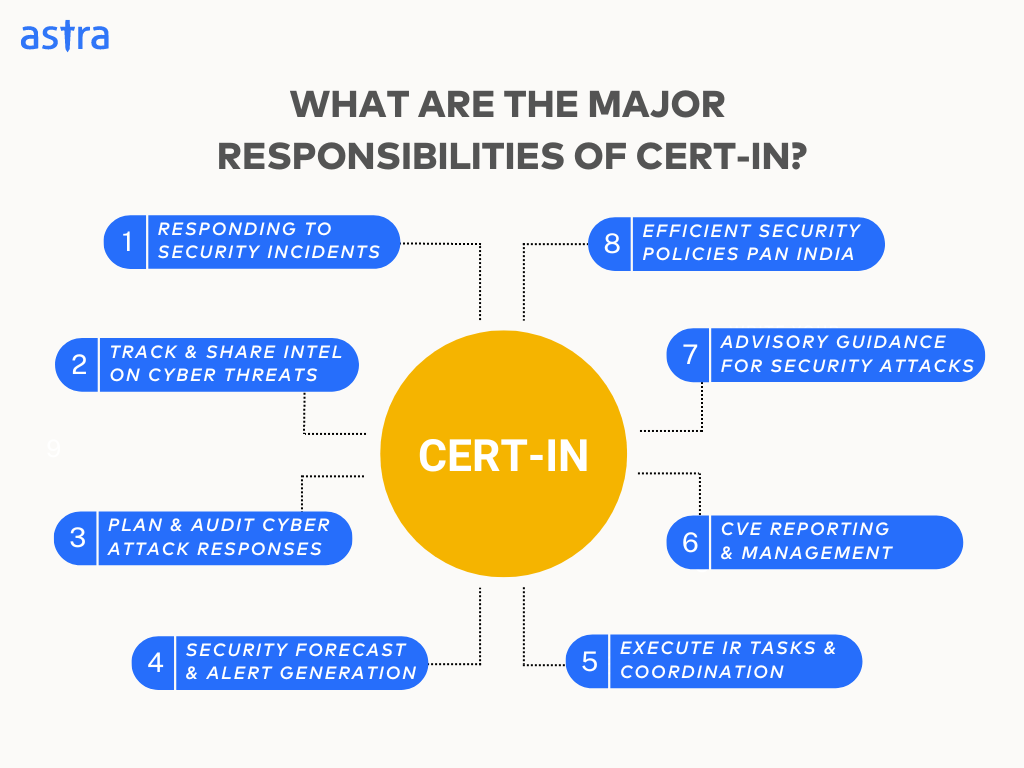
Contrary to its name, CERT-IN doesn’t directly award compliance certificates but oversees the process. It empanels security auditors to conduct a comprehensive security assessment of your organization’s IT infrastructure according to specific guidelines.
This often includes websites, systems, applications, and any network or digital infrastructure your company uses. Upon completing and meeting all requirements, the auditor awards a certificate, demonstrating compliance with CERT-IN standards.
The certification fee varies depending on various factors, such as the size and complexity of your organization’s IT infrastructure, the scope of the audit, and your chosen auditor.
What is The CERT-IN VAPT Certification Process?
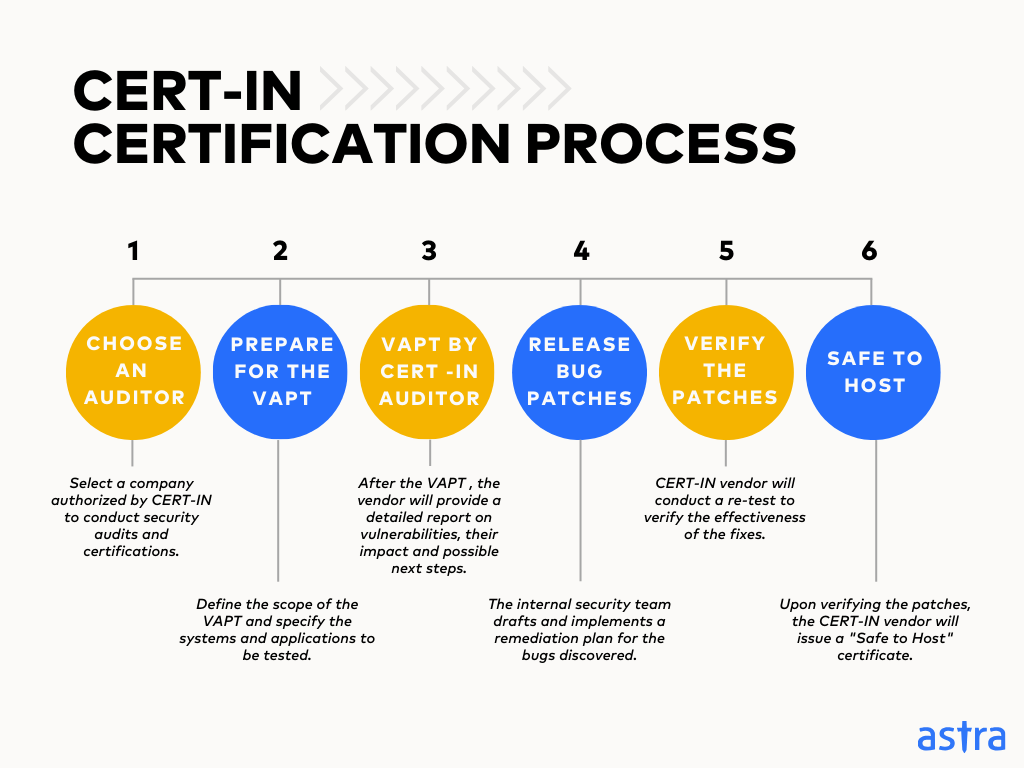
1. Choose a CERT-IN Empaneled Cybersecurity Company
The CERT-IN process begins by selecting a company authorized by CERT-IN to conduct security audits and certifications. Research the company’s experience, expertise, and reputation to ensure it fits your organization’s needs well.
Pro Tip: Establish clear communication channels and discuss project timelines and costs to facilitate a smooth audit process.
2. Prepare for a Vulnerability Assessment and Penetration Testing (VAPT):
Define the scope of the VAPT, specify the systems and applications to be tested, and provide the depth of analysis. Set up a dedicated test environment to replicate your production systems without impacting fundamental operations.
Pro Tip: Prepare with your engineering team to understand the testing process and potential disruptions. Ensure that they are available for quick response if necessary.
3. VAPT by CERT-IN Empaneled Security Vendor
Your CERT-IN vendor will conduct a comprehensive VAPT, simulating real-world attack scenarios. They will attempt to exploit vulnerabilities in your systems to identify potential security weaknesses, the possible impact, and potential losses.
Once the VAPT is complete, the vendor will provide a detailed report outlining the identified vulnerabilities, their severity levels, and suggested remediation steps.
4. Release Patches Against Vulnerabilities
Based on the above report, your internal security team can draft a remediation plan, preferably prioritizing the vulnerabilities based on severity. This often involves patching software, updating configurations, and implementing additional security controls.
5. Verify Your Patches
After addressing the vulnerabilities internally, the CERT-IN vendor will conduct a re-test to verify whether the fixes effectively mitigated any potential security risks.
6. Achieve a “Safe to Host” Certificate:
Upon verifying the patches, the CERT-IN vendor will issue a “Safe to Host” certificate. This certificate demonstrates your adherence to CERT-IN guidelines and commitment to cybersecurity best practices.
What Makes Astra the Best VAPT Solution?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- The Astra Vulnerability Scanner Runs 8000+ tests to uncover every single vulnerability
- Vetted scans to ensure zero false positives
- Integrates with your CI/CD tools to help you establish DevSecOps
- A dynamic vulnerability management dashboard to manage, monitor, assign, and update vulnerabilities
- Astra pentest detects business logic errors and payment gateway hacks
- Helps you stay compliant with SOC2, ISO27001, PCI-DSS, HIPAA, etc.
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

What are CERT-IN Guidelines?
The CERT-IN Security Audit Baseline Requirements (SABR) outline and establish a standardized framework for conducting security audits, ensuring a comprehensive evaluation of IT infrastructure and practices.
It focuses on core security areas through the five distinct control categories explained below:
1. Management Controls
Security audits of your management controls assess your organization’s security policies, procedures, and risk management programs. This includes reviewing documented strategies and how you identify, manage, and prioritize risks for effective mitigation.
2. Protective Controls
Such control audits assess an organization’s defenses, from network firewalls to application coding practices. They ensure data is protected at rest, in transit, and in use while considering the physical security of data storage and devices.
3. Detection Controls:
Detection control audits focus on your Intrusion Detection System (IDS), log monitoring, and vulnerability management. This includes examining your ability to detect threats, gather relevant security logs, and effectively patch vulnerabilities.
4. Response Controls
Under such controls, the auditors determine the clarity and adaptability of your incident response plan, outlining the strategy for security incidents. They also focus on communication checks to ensure clear instructions have been provided for everyone in case of an incident.
5. Recovery Controls
Here, the auditor evaluates the organization’s preparedness for data loss and system disruptions, including the efficacy of the data backup strategy and the feasibility of the disaster recovery plan. This helps minimize downtime and ensures swift recovery.
Which Types of Organizations Require CERT-IN Certification?
CERT-IN certifications are one of the efficient ways to attest to the security of Indian organizations and, hence, are beneficial to most Indian organizations. Here’s a non-exhaustive list of organizations mandated by various laws to comply with this certification:
1. Financial Institutions:
A. RBI Regulated Entities:
- Banks adhering to the “Cybersecurity Framework for Banks” and “Cybersecurity Framework for Urban Cooperative Banks.”
- Companies complying with the “RBI Guidelines for Cybersecurity in the NBFC Sector.”
- Companies and software under the “RBI Guidelines for Payment Aggregators and Payment Gateways.”
B. Insurance Companies:
- Companies and software complying with the “IRDA mandate for ISNP Security Audit.”
Note: The ISNP Security Audit applies to insurance companies establishing online platforms for their services, as mandated by the Insurance Regulatory and Development Authority of India (IRDAI).
2. Government and Public Sector:
- Companies conducting business related to IT services with the Government of India.
- Companies hosting applications or portals on the National Informatics Center (NIC) infrastructure.
3. Other Regulated Sectors:
- Companies and software falling under the “SEBI Cybersecurity and Cyber Resilience Framework.”
- Companies or those using software adhering to “UIDAI – AUA KUA Compliance.”
- Organizations are designated critical infrastructure providers (CIPs) in critical sectors like power, telecommunications, and transportation.
Benefits of CERT-IN Certification
1. Enhance Your Security Posture:
CERT-IN audits comprehensively assess your IT infrastructure, identifying bugs and zero days such as broken authentication, cross-site scripting, and privilege escalation. This proactive approach allows you to minimize the risk of cyberattacks and data breaches.
2. Improve Your Brand Reputation and Customer Trust:
With the rising number of cyberattacks, CERT-IN certification demonstrates your organization’s commitment to robust cybersecurity practices, fostering trust and confidence among customers, partners, and stakeholders, giving you a competitive advantage.
3. Demonstrate Regulatory Compliance:
For specific sectors, such as government entities, critical infrastructure providers, and financial institutions, complying with CERT-IN guidelines and undergoing security audits are mandatory by law, as are the latest amendments of the IT Act.
The certificate provides tangible proof of compliance and helps you avoid potential penalties associated with non-compliance.
What are the Components of a CERT-IN VAPT Report?
Although the components and structure of a VAPT Report for CERT-IN certification may vary based on the vendor, these are some key components that form the foundation of an acceptable report:
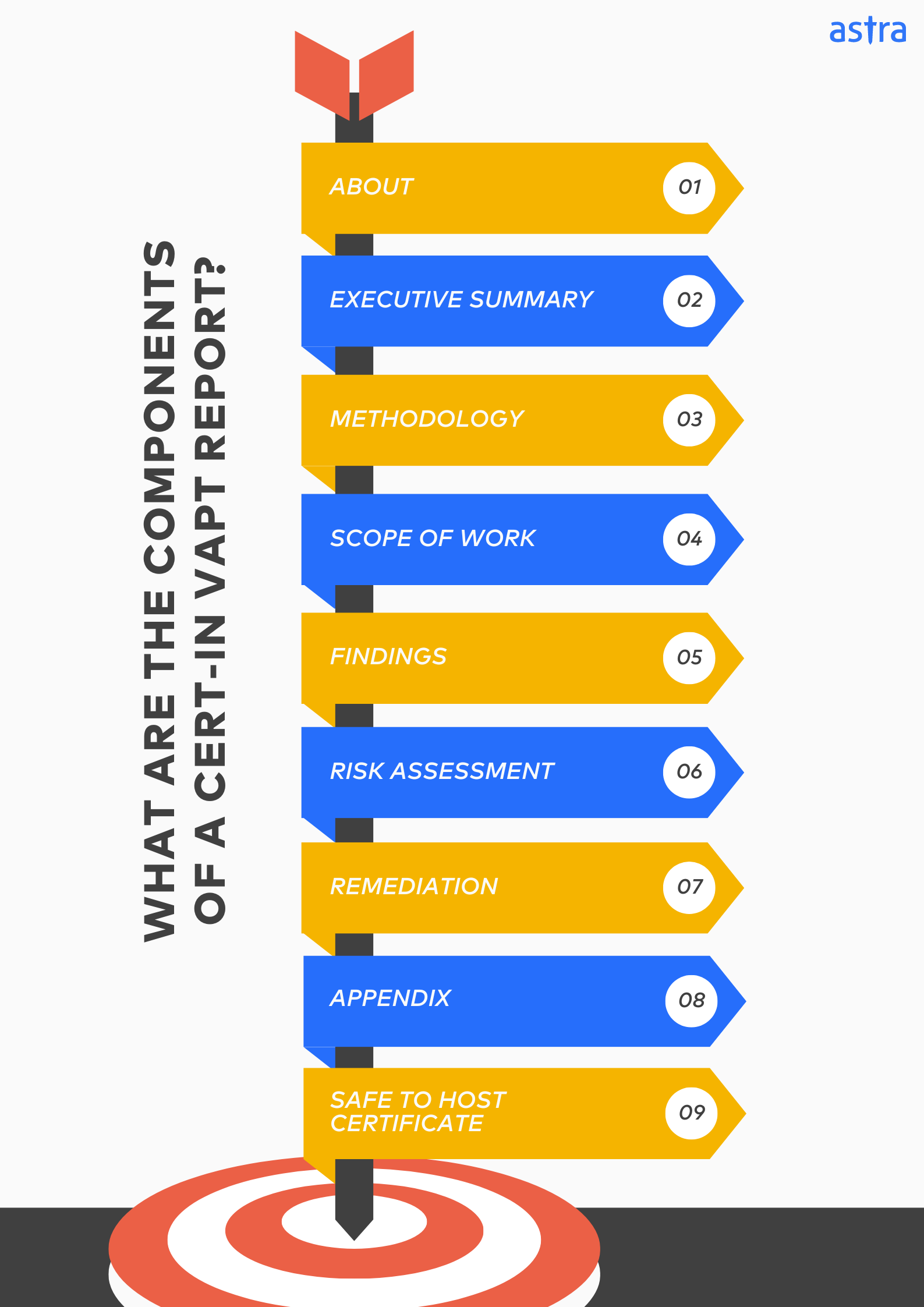
- About: Short intro about the pentesters, reviewers, and any other members, as well as their experience
- Executive Summary: Briefly summarizes the date, time taken, and findings to highlight critical vulnerabilities and recommends actions.
- Methodology: Explains how the VAPT was conducted, including testing types, tools, and adherence to CERT-IN guidelines.
- Scope: Defines which systems and applications were assessed, setting the context for vulnerabilities.
- Findings: Details each identified vulnerability, including description, severity, CVSS score, CVE reference, and potential impact (with redacted PoCs, if applicable).
- Risk Assessment: Analyzes each vulnerability based on severity, exploitability, and business impact, prioritizing critical issues with steps to reproduce.
- Remediation: Offers specific recommendations and timeframes for addressing each vulnerability, referencing mitigation strategies.
- Appendix: Provides additional technical details for further analysis.
- “Safe to Host” Certificate (if applicable): Demonstrates successful remediation and adherence to CERT-IN standards.
How Can Astra Help?
Astra is a leading SaaS company specializing in innovative penetration testing and security auditing solutions. Our VAPT techniques blend automation, AI, and manual expertise to run 9300+ tests to deliver penetration testing solutions tailored to your needs.
Astra is empanelled by a CERT-IN for providing Information Security Auditing services.
Final Thoughts
As such, By offering a robust framework for cybersecurity, CERT-IN certification empowers organizations to improve their security posture and demonstrate their commitment to data protection.
This, in turn, not only builds trust with customers and partners but also shields them from hefty non-compliance penalties. Thus, as lengthy as the process might initially seem, the benefits of the CERT-IN certification significantly outweigh the inconveniences!
FAQs
What is CERT-IN?
CERT-IN, or the Indian Computer Emergency Response Team, is a government-approved organization established in 2004 by the Department of Information Technology to uphold information technology (IT) security and implement the provisions of the 2008 Information Technology Amendment Act.
What is CERT-In empanelled?
CERT-IN empanels IT security auditing organizations. These approved auditors can then conduct security assessments and pentests on computer systems, networks, and applications for businesses and government institutions across India.

















Do Astra security helps other organization to obtain CERT-IN Empanellment?