More than 55% of all the attacks WordPress suffers can be attributed to vulnerable plugin exploits. Statistics show that over 70 million WordPress websites are using vulnerable plugins & themes, thus becoming easy targets for hackers.
Faulty plugins and modules have been a nagging problem not only for WordPress, but for every major CMS out there. The wide spread user base and the panoramic diversity of plugins make them lucrative targets for attackers, and they have been quite relentless in their efforts to exploit plugins.
There are certain security practices plugin and theme developers must follow to avoid becoming easy targets. One such vital security measure is to test your plugin for vulnerabilities while developing it i.e. conducting a plugin security audit, aka plugin security assessment during various stages of the plugin development or before its launch.
Get the ultimate WordPress security checklist with 300+ test parameters
What is Plugin Security audit or Plugin VAPT?
A plugin security audit is a process to identify exploitable vulnerabilities, security loopholes, misconfiguration issues, and potential entry points in a plugin via automated and manual tests.
In a plugin security audit (or plugin VAPT), security professionals try to attack the target plugin with a hacker-like approach in a simulated hack scenario.
Why is WordPress Plugin Security Audit Important?
More than 52% of WordPress vulnerabilities relate to WordPress plugins, risking sensitive data in a website.
By exploiting a vulnerable plugin, hackers can:
- Encrypt all the website data and ask for ransom.
- Steal the data of your website or users and sell it on the dark web.
- Inject malicious code into a WordPress site that can lead to website blacklist, spam redirection, SEO spam, or hosting account suspension.
- Steal the credit card info of WordPress site users which may land lawsuits and hefty fines against website owners.
- Trick website visitors into phishing
- Use your hacked website to infect the systems of website visitors and so on.
For these reasons, reviewing WordPress plugins for security vulnerabilities becomes non-negotiable.
You May Like to Read: Cloud Security Audit: Everything You Need to Know
A WordPress security audit can help developers identify and fix plugin vulnerabilities present in their software.
Here’s what you get out of a WP plugin security audit:
- It can give you a holistic view of misconfigured integrations implemented within your code and offer you a chance to do a secure code review.
- It also helps in preparing your plugin dev/security team to cope up with active vulnerability exploitation.
In addition, If a WP plugin has vulnerabilities and hackers are actively exploiting it then WordPress can temporarily disable that plugin and make it unavailable to the users until the vulnerability is patched in a given time. Here’s an example message shown on the unpatched plugin download page:
What are the common vulnerabilities in WordPress Plugins?
While there are many different techniques hackers use to discover vulnerable WP plugins, there are some commonly seen security vulnerabilities in WP plugins hackers often exploit and break into the site.
Here are some common vulnerabilities in WordPress plugins:
- SQL Injection (SQLi)
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Code Execution
- Privilege Escalation
- Arbitrary File Upload
You can follow the prevention guidelines mentioned here if your plugin is still under development: link
How to Do WordPress plugin security audit (developers perspective)
A plugin security audit comprises three steps: Information Gathering (i.e. Reconnaissance), Exploitation, and Remediation.
The purpose of a plugin security audit varies with different plugins and developers’ needs. Having said that, almost all plugin security audits tend to encompass the following things:
- Testing all input areas on the plugin
- Checking requests made by the plugin
- Checking the source code
- Checking permissions and data storage on the plugin
- Checking data validation and sanitization
- Checking data escaping / secure output
- Analysis of code to check security issues in early SDLC (Using SAST)
- Checking plugin security in run-time by doing Dynamic Application Security Testing (DAST)
Here is more detailed information on steps to perform while testing your Plugin for security:
Step 1: Setting up the testing environment
- Configure a WP instance on your machine or setup a local environment using this tool
- Install the plugin you want to test
- Activate/configure the plugin
- Configure your browser to route all traffic through Burp tool and enable live scanning
- Add all the widgets/elements on a page
- Navigate through the front-end page where all these elements are there
You may like to read: Choosing The Right Security Audit Company Made Easy
Step 2: Use code scanners to look through vulnerabilities
- You can use this open source tool to do that: link
Step 3: Run plugin security test cases
- You can use this open source checklist to do that: link
Step 4: Run a coding standard test to find security gaps
- You can follow the steps mentioned in this open-source guide to do that: link
(Note: The WordPress Coding Standards require PHP 5.4 or higher and PHP_CodeSniffer version 3.3.1 or higher)
Related blog – Penetration testing Company
How to Pentest your WordPress plugin?
1) Gathering Information
The first step in plugin penetration testing is to gather information about your plugin. This information shall help you in prioritizing security areas you need to test first on your plugin.
Common security areas that are tested in a plugin pentesting are — user data input and related checks (validation, sanitization, escaping), files & directories permissions, configurations, data storage, encryption, web servers, database, and more.
Now, you can use automated tools to find out vulnerabilities in each of these security areas. Tools like Nikto, Nmap, Testssl, etc can accelerate the process for you.
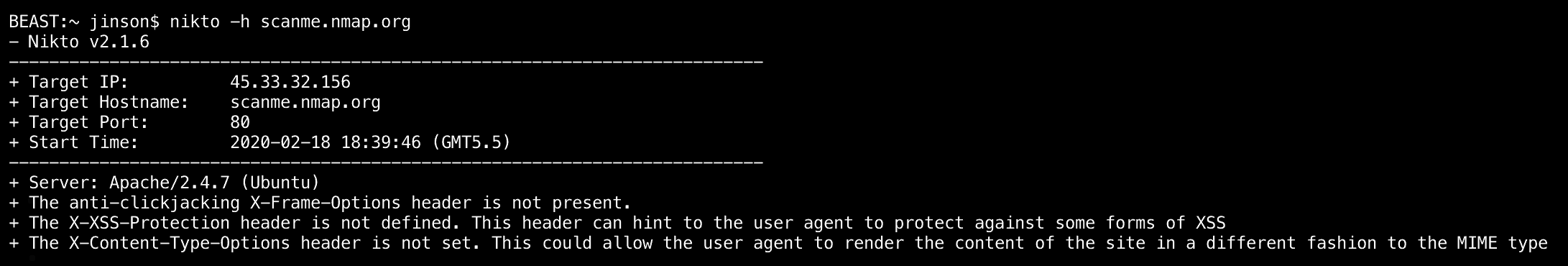
- Nikto: Nikto is a Kali Linux pentest tool. It is extensively used to find out information such as — server, hostname, port, IP, security headers, etc. of an application.
To use this tool on Kali Linux, run the following command:# nikto –h [examplewebserverurl]
Where [examplewebserverurl] is your web server’s IP or FQDN.
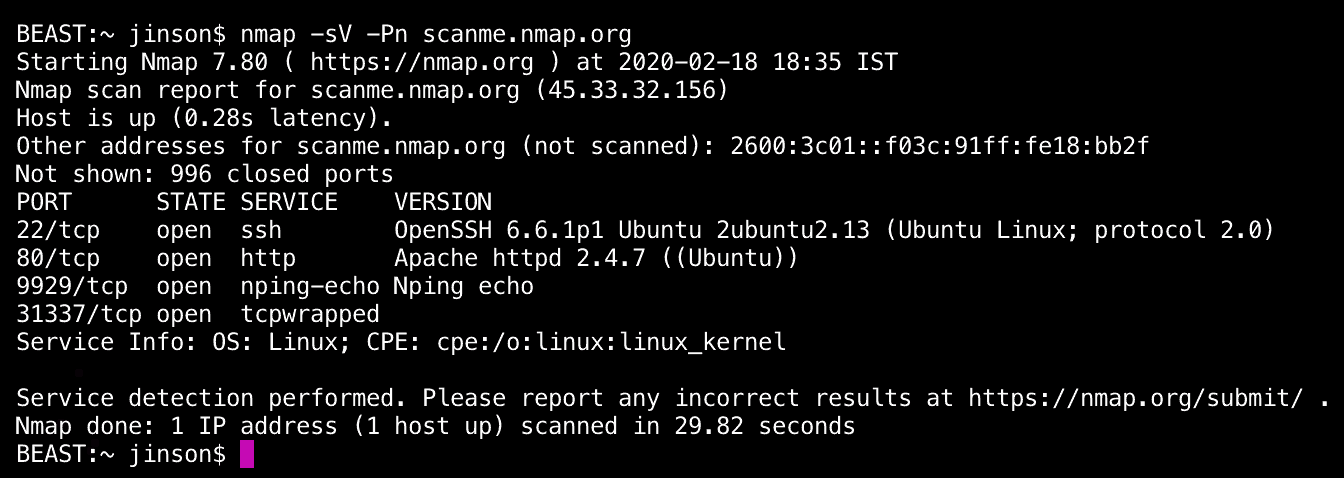
- Nmap: Nmap, short for Network Mapper, is a pen-testing tool used for network inventory, managing service upgrade schedules, and monitoring host or service uptime. In other words, Nmap is a tool that tells you all about the hosting service of that application; from the name of the hosting service, version, operating system to what firewalls or security systems they have, Nmap tells you about all.
To run Nmap on Kali-Linux, run the following command:
nmap -sV -Pn [examplewebserverurl]
2) Exploitation
By now, you have an idea of all vulnerabilities that are present in your plugin. Next, you need to exploit them. This will help you learn how easily each vulnerability can be exploited and the level of damage it can cause.
There are tools available for this as well. For example, SQLmap, Burp Suite, etc.
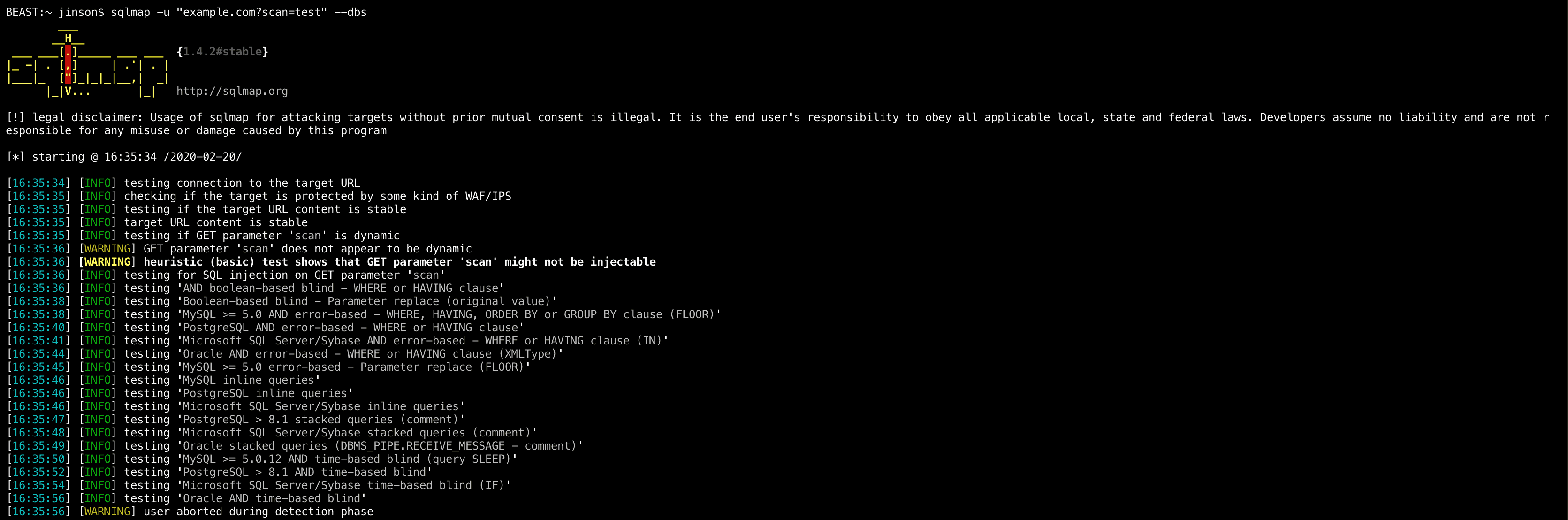
- SQLmap: SQLmap is a tool to exploit database vulnerabilities. This tool is basically used to crack open the database by executing malicious queries into the plugin’s input fields.
To use this tool, run the following command in your SQL database:
sqlmap -u “example.com?scan=test” –dbs
- Burp Suite: Burp Suite comprises a range of pen-testing tools. The Burp Suite tools can be used in any stage of a plugin security audit. It caters to both — security assessment and vulnerability exploitation. Tools included in Burp Suite are: HTTP Proxy, Scanner, Intruder, Spider, Repeater, Decoder, Comparer, Extender & Sequencer.
Now that you’re equipped with adequate information about vulnerabilities, you can easily resolve them individually. However, it really does seem like a lot of work.
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed]
Get Professional Support
The above process (as simply as I have tried to put it) can be tiring for many. Moreover, if you aren’t a security-savvy person, you cannot be completely sure you executed the plugin VAPT flawlessly. Therefore, we recommend that you get a professional VAPT or security audit for your WordPress plugin to get better results.
Astra’s security experts will thoroughly go through the plugin’s source code, configurations, permissions, and run over 1250 tests to spot vulnerabilities in the plugin or any software and help you resolve them.

VAPT by Astra comes at a very reasonable price and has various other features.
Further, Astra’s VAPT process can be broken down into these five pointers:
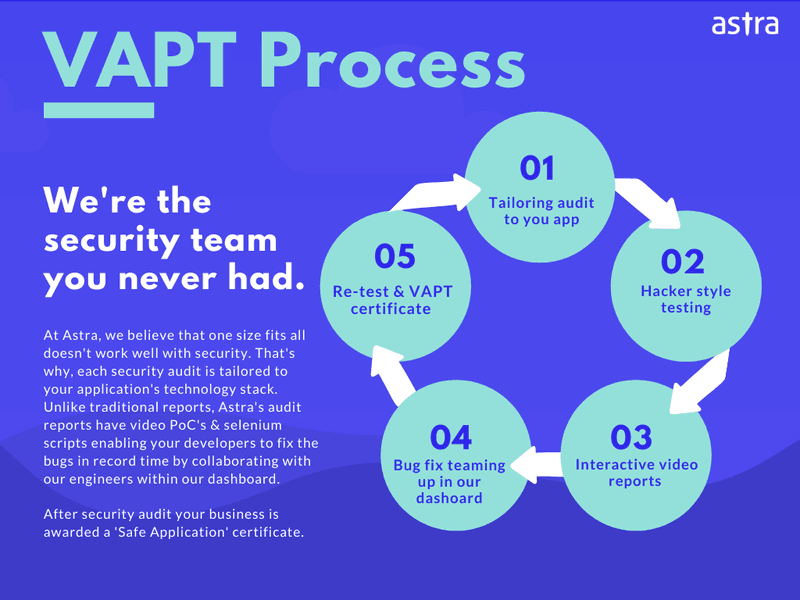
Conclusion
All it takes is one vulnerable plugin to ruin a website.
Plugin exploits affect thousands of websites and businesses daily. Several of which never recover from the aftereffects of a cyberattack and eventually shut down. Cyberattacks negatively affect your business’s reputation and affect customers’ trust.
Hence, to save yourself and your plugin from this adversity, it is necessary that you conduct a detailed plugin security audit or plugin security assessment regularly to identify and resolve security flaws in your plugin.
If you’re looking for external in-depth penetration testing for your plugin, Astra Security has you covered. Check out Pentest Suite today!
















