Security audits essentially refer to the thorough assessment of a company’s security posture, which includes:
- The physical posture of the company’s security.
- Applications, software, and security patches that are in place.
- Network security measures that ensure the safety of data in transit.
- Information handling procedures and practices made use of by employees.
Assessing these aspects of security against an extensive security audit checklist can reap numerous benefits. It is well-established that every company ensures its continued compliance by carrying out audits with the help of a security audit company at least twice a year. This is also subject to a variety of factors like the size of the organization, its employee strength, and the intricacies of its security system.
A security audit company helps make this whole process easier by aiding your organization in defining the parameters, audits, and tests to be conducted, evaluating risks, and giving a detailed report based on its findings. Thus, essentially helping your organization to dot the I’s and cross the T’s when it comes to its security.
This article will detail the benefits of carrying out a security audit and explain in detail which sectors should particularly carry them out. We will also list out the factors in choosing the right security audit firms and mention the features of the best security audit company there is.
Why Are Security Audits Important?
Security audits are essential for maintaining compliance with international security regulations and standards like HIPAA, PCI-DSS, SOX, NIST, and ISO 27001. Such audits can help you understand whether your organization is meeting all the initially set requirements and if there are any gaps in meeting them.
Security audits identify areas of the security systems that can be improved on by your company. This helps in finding and fixing any vulnerabilities before they can be preyed on by malicious attackers thus mitigating potential crises.
It is important in the development of risk mitigation strategies and assessment plans in case of any disasters or breaches taking place to ensure the protection of sensitive client information. Finally, a thorough audit can help you analyze and build a good security posture with standardized protocols in place.
How Often Do Security Audits Need To Be Done?
Companies that deal with a lot of sensitive information like healthcare, banking, and governmental organizations frequent security audits more than other organizations. They also have regulatory bodies and standards to abide by for a seamless security experience, to avoid non-compliance-related penalties, loss of reputation, and even criminal charges.
Such companies opt to do security audits at least bi-annually. This can also be done on a quarterly or even monthly basis however this takes up a lot of time and resources. At the very least it is recommended for organizations to carry out security audits once a year to find any loopholes in the systems within the organization.
Also Read: Security Audit Services: Importance, Types, Top 3 Companies | 5 Best Cloud Security Companies: Features Offered And Factors To Consider
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
Regardless of what sector your company is in, be it telecommunications, finance, healthcare, or governmental, it is becoming increasingly necessary to conduct security audits with a regularity.
The frequency with which security audits are conducted depends on various internal factors like:
- Size of the organization and employee strength.
- Complexity and structuring of the organization.
- Demands of the organization.
- Amount and importance of sensitive data that the company deals with.
- The number of systems and applications that need to be audited.
- Addition of any new systems or features.
- Growth of the organization
Additionally, if there are any updates or changes to the compliance standards, companies will be required to undergo security audits to ensure compliance with the updated model. It is also highly advisable to conduct security audits after a data breach or migration to ensure that the new security measures in place are solid.
Factors In Choosing The Right Security Audit Company
Decided on doing periodic security audits to safeguard your enterprise? That’s great. Now you must be wondering how to find the right security audit company for your needs. Well in order to make the right decision, it is always beneficial to have a list of factors that you can look for in companies providing security audit solutions.
This way, if a company from your shortlist of candidates fits the profile and requirements, you can choose them without hesitation. Some of the important factors that the right security audit services would have are:
- Reputation
Ensure that the security audit company you choose has an excellent reputation when it comes to customer service, integrity, and quality services. The company should be known for its comprehensiveness, multiple client references, and experience with the sort of security audit services you are looking for. Client references can give you in-depth information about the quality of the services provided by security consulting firms.
- Qualification
The companies you have shortlisted should have highly qualified and trained employees. It is important to make sure the company provides audit compliance to the regulations your organization requires like ISO 27001, HIPAA, SOC2, and more. The auditors should also have the relevant qualifications that make them trustworthy and reliable options.
Also Read: 10 Best Cyber Security Audit Companies: Features and Services Explained
- Processes
Make sure that the processes and tools used for testing by the security audit company are compatible with your organization’s needs, systems, and infrastructure. The companies providing security audit services should provide demos of the same so that you have a better understanding of how their audit for your organization’s infrastructure will look like.
- Duration
Generally, the relationship established between an organization and its security audit company can range from 3 months to anywhere around a year or more. Therefore it is crucial to ensure that they will be reliable for this longstanding duration. It is also wise to opt for security audit packages with a yearly span as it leads to lesser work and documentation with every security audit, thus saving you precious time, resources and expenditure.
- Transparency
When interacting with potential options for security audit services, thoroughly assess their credentials and understand their working environment and process. Be sure to enquire about how flexible they would be in accommodating your organization’s unique needs into the scope of auditing. Ensure that the team is responsive and transparent in explaining their procedures and clarifying your doubts as it is important to ensure a durable working relationship.
Also Read: Cloud Security Audit: Everything You Need to Know
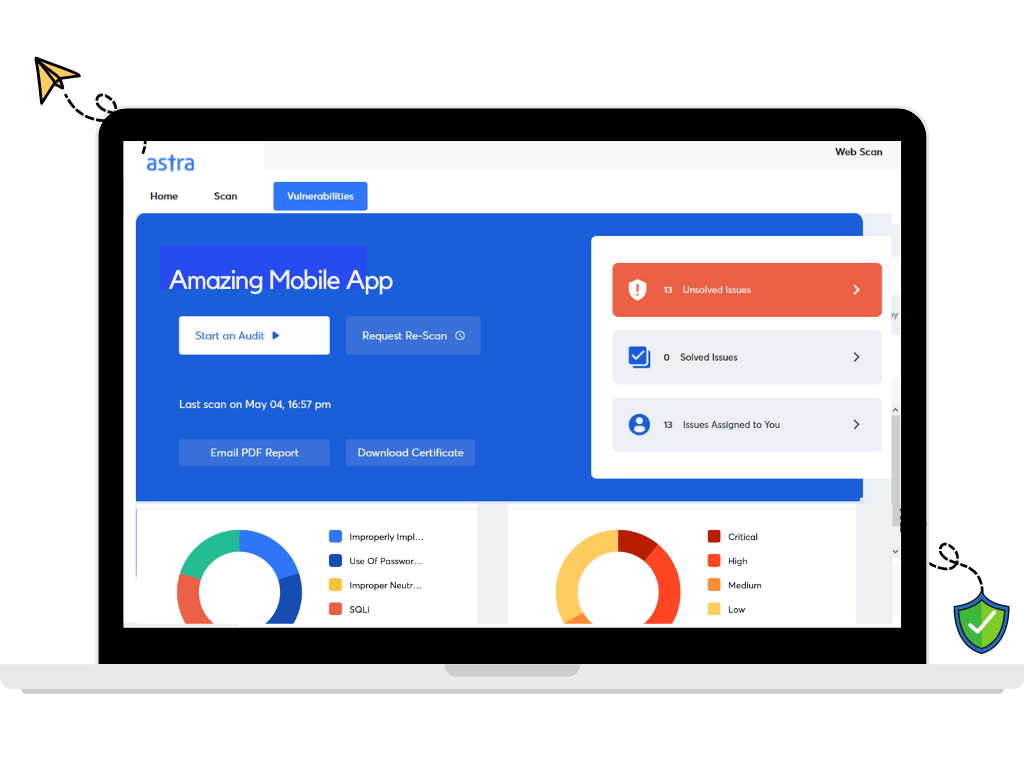
The Best Security Audit Company- Astra
Astra Security is the perfect security audit company for your organization. All the above-mentioned factors are already met by Astra’s security team, and it offers additional features that make them one of the best options to cater to all your security audit needs. The next section provides information on Astra Security’s most distinguishing features.
Features Of Astra
- Comprehensive Vulnerability Scanner
Astra Security’s Pentest Suite has a powerful vulnerability scanner that is capable of running more than 3000 tests that can find vulnerabilities from known CVEs, OWASP Top 10, and even SANS 25.
It is also capable of conducting behind-the-login scans with a browser extension to ensure the seamless record-keeping of your login activities to rule out foul play. It also provides scans for PWAs and SPAs (Progressive Web Apps and Single Page Apps) regardless of what their tech stack is, thus ensuring that your web application is fully secured.
The vulnerability scanning reports provided are detailed and articulate with every vulnerability, its severity level, and remediation steps being mentioned in detail. This makes it easier for the developers in your organization to fix the found loopholes.
- Manual and Automated-VAPT
Astra Pentest Suite’s hacker-style tests can find and exploit vulnerabilities within your system to understand the extent of damage and breach that could occur from them. This is done by making use of CREST, NIST, and OWASP testing methodologies to test for compliance, business logic errors, and more.
The dedicated approach of using both automated and manual pen testing methods ensures that there are no false positives to worry about as they’re vetted out using manual testing methods.
Besides this, they also provide business logic testing to find the areas within your organization’s procedures that necessarily don’t have vulnerabilities but have to be streamlined for further efficiency and growth.
Related Read: Astra’s Pentest Suite for VAPT
- Compliance Check
Astra’s security audits ensure that all the parameters of your organization fall well within the regulations and standard laws that it must be compliant with like SOC2, ISO27001, HIPAA, GDPR, and PCI-DSS.
Astra Security’s auditing finds the areas within your organization’s infrastructures that fail to meet the criteria for maintaining compliance thereby allowing you to take the necessary steps to achieve compliance. Not being compliant can lead to receiving heft penalties and fines that can disrupt your business.
It is also important to check the compliance status of your organization every time a new feature or addition is made to your services to make sure that it is safe for use. These factors make compliance checks with Astra Security audits important for your security needs.
- Interactive Dashboard
Astra Pentest Suite’s dashboard is extremely user-friendly, interactive, and intuitive. This ease of use makes Astra a top choice for your security audit needs. The dashboard shows the list of vulnerabilities found, their CVSS risk scores, and remediation measures to be taken.
Along with this, the organization can post their queries under each vulnerability which will be answered by the auditing team directly. It also provides a detailed auditing report for your to view or download as a PDF and video POCs with suggestions to fix vulnerabilities.
The dashboard also provides the option to add members from your organizations developing team to collaborate with the Astra Security auditors to fix and patch any vulnerabilities or loopholes found. Therefore Astra Security’s dashboard makes the journey from the documentation of the auditing to remedying of the vulnerabilities found as seamless as possible.
- Integrations
Choosing Astra as the security audit solution to fulfill the security audit needs of your organization also allows for integrative possibilities with your CI/CD pipeline thus smoothly transitioning your organization’s practicing methodology from DevOps to DevSecOps.
The integrations can be made with Jira, GitLab, GitHub, Jenkins, Bitbucket, Azure, and Slack where the security posture of your projects can be assessed throughout its development stage to deployment. This ensures that all your applications are vulnerability free and reduces the patches that need to be done.
- 24×7 Astra Team Support
Astra Security’s expert team of auditors is always available to guide you and clarify your doubts. This communication is made easy with the interactive dashboard where auditors can quickly reply to any queries raised by your organization. Engineers from the testing team are also available for chats if the need arises.
Additionally, the members of the auditing team hold all necessary qualifications ranging from bachelor’s in information security to CEH certification and Policy Compliance Certification from Qualys. Alongside this, effective communication and collaborative skills make the customer support at Astra friendly and quick.
- Verifiable Certificate
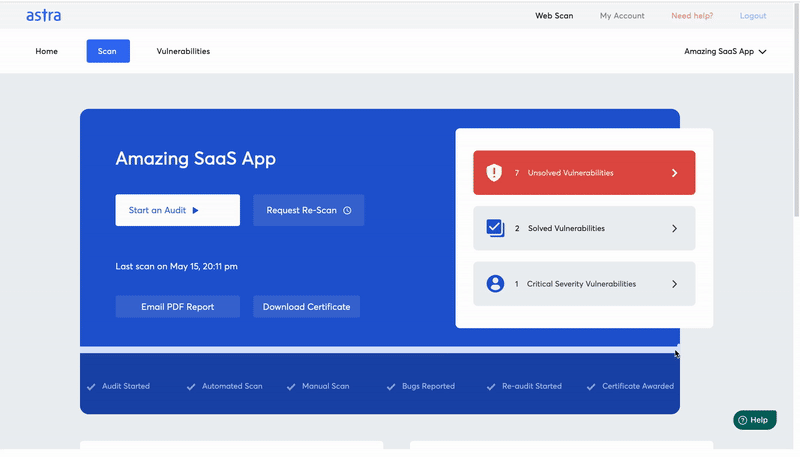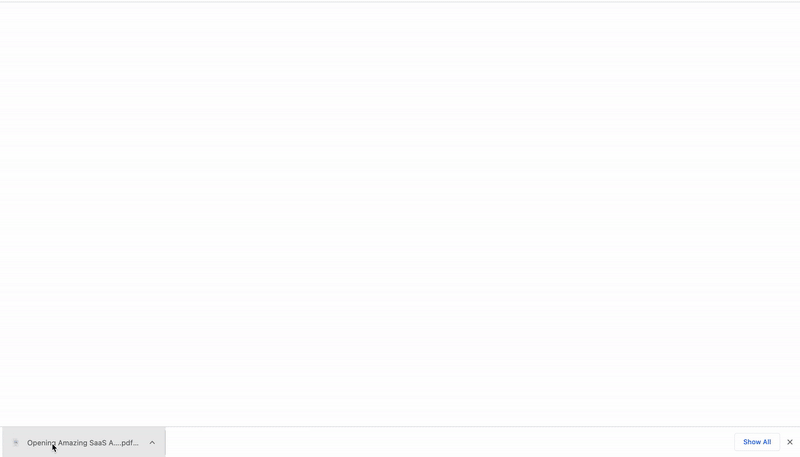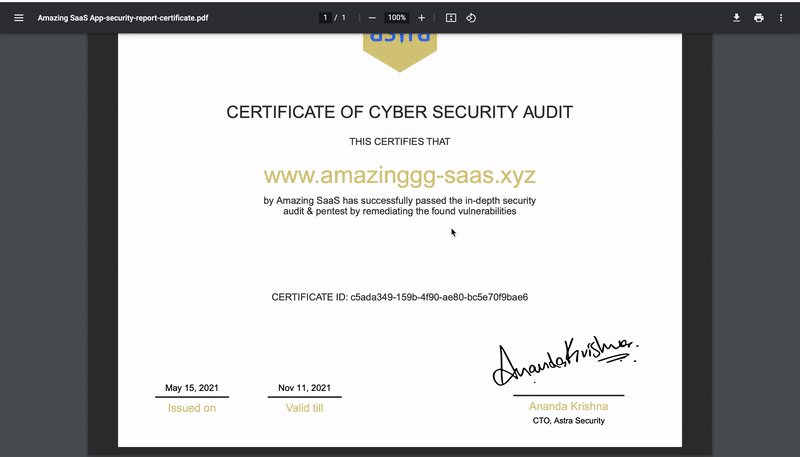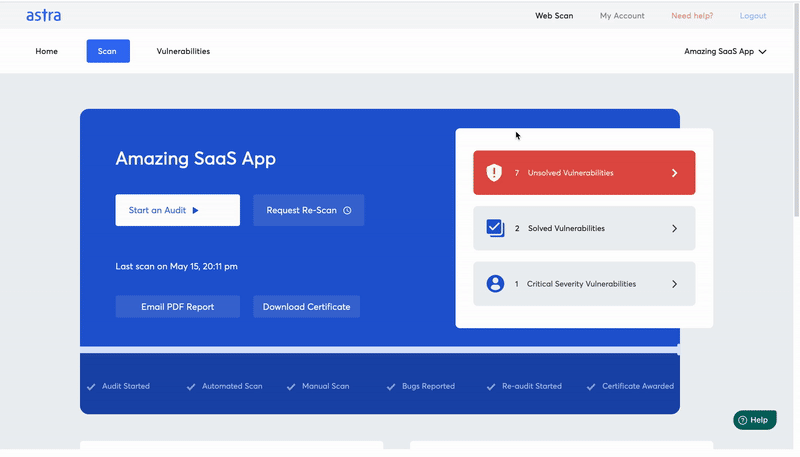
Yet another enticing feature of Astra comes in the form of an Astra Security Audit Certificate. This certificate is provided to the organizations that carry out security audits, fix the vulnerabilities found, and does a re-scan to ensure its safety. Once these steps are done the downloadable certificate is provided through the dashboard. It is a publicly verifiable certificate that can be displayed on your website.
The Astra security audit certificate increases the trustworthiness and reputation of your organization with the existing clientele and also helps bring in additional clients owning to the attested security conscious, and standard-compliant nature of your organization.
- Affordable Packages
Security audits at Astra are also provided at extremely competitive budget-friendly prices that can be opted for as monthly or yearly plans. These packaging and pricing go as followed:
- Scanner: A basic package costing $99 monthly or $1,188 yearly.
- Expert: A detailed package costing $199 per month or $2388 annually.
- Pentest: A completely comprehensive package with all the expert plan features and more at an expense of $4500 per year.
One factor to be kept in mind is that these prices vary based on the number of target URLs to be tested.
Related: Astra Security Pricing
Types Of Security Audits Provided By Astra
- IT Security Audits
IT security audits refer to carrying out a systemic assessment of a company’s information technology posture and infrastructure. An IT security audit company helps organizations in the sector find exploitable vulnerabilities before any malicious attacks occur and fix them in time.
An IT security audit comprises both physical and virtual checking of systems to ensure their security. It can help find the gaps in your compliance and staff’s security training thereby giving the organization areas to improve on.
Read More: API Security Audit Checklist
- Web Security Audits
Web Security Audits aim to assess websites and all their related components such as extensions and themes for any loopholes. It generally involves a thorough static and dynamic analysis of codes, testing for business logic errors, and more.
Checkout Astra’s Web Security Audit Checklist
- Network Security Audits
Also a crucial part of IT infrastructure safety, network security audits refer to the evaluation of all the network devices, connections, and systems that are accessible through the internet. Ensuring the security of a network is vital to maintaining the security of information stored and passed by an enterprise.
Checkout Astra’s Network Security Audit Checklist
- Cloud Security Audits
In cloud security audits, the assessment is carried out to check for any vulnerabilities within a cloud server that could compromise application security and customer information through hacking. Fixing these vulnerabilities can make the cloud server provider more trustworthy and reliable thus attracting more customers.
Also Read: Complete Guide To Cloud Security Testing
Conclusion
This article detailed the need, benefits, and timeline of an audit with the help of a security audit firm. It also mentions the factors to look for in the perfect security audit solution for your needs. Astra Security, with its numerous features, stands out as the prime candidate for all your organization’s security audit requirements thus saving you a lot of hassle. The features that have been mentioned and the types of security audits provided by Astra are a few of the reasons why you should opt for Astra Security as the security audit company for you!
1. What is the difference between a security assessment and a security audit?
Security Assessments refer to methodically going through the security protocols in place to see if there are any gaps and subsequent vulnerabilities. A security audit, on the other hand, is a systemic analysis of an organization’s entire information handling procedure which includes security assessments, physical infrastructure analysis, network, and application security.
2. How long does a security audit take?
This depends on the size and manpower of the client organization, the resources allocated and the compliances to be achieved. Usually, it takes around 1-3 months.
3. What are the two types of security audits?
The two categories of security audits are external audits and internal audits. External audits are carried out by a hired professional security audit company. Whereas internal audits are done by the in-house development team of an organization.
![Security Audit Company and Services [Top rated]: How to Pick](https://cdn-blog.getastra.com/2022/05/Featured-Images-6.png)















