With the growing dependence on the cyber world, newer threats have emerged to the data and applications that are stored and accessed via cyber platforms. This is why security has gained utmost priority over all else and is taken seriously by most companies.
Audits offered by security audit services are most often relied upon by such companies to ensure that their services, applications, and data are compliant and free from any security vulnerabilities that could threaten to compromise them.
Security audits refer to the thorough assessment of a company’s posture with regard to information security and how well it follows the set of rules and regulations put forth by its specific industry.
Security audit services are providers that offer such audits to companies, networks, and more. They offer a variety of services within the security audit category that a company can choose from to assess its security posture. This helps in determining any vulnerabilities and fixing them.
This article will discuss the importance of security audit services, the different processes under them, and the types of their applications. The article will also mention the top 3 security audit services in detail.
Importance of Security Audit Services
Making use of security audit solutions is relevant for the following reasons:
- Identification of Vulnerabilities: Vulnerability scanning as a part of a security audit can help with the identification of vulnerabilities or loopholes present within the system. This is important as it can help in fixing them before any harmful attacks take place.
- Establishment of Baseline: Audits can establish a healthy outline for security based on which future audits and their results can be compared. This can help improve the systems in place making them more secure and less prone to attacks.
- External Compliance: These are mandates or rules and regulations set forth externally by the government for any industry and are enforced by the authorities, for example, PCI-DSS and HIPAA. They need to be followed meticulously to avoid penalties and the smooth running of businesses.
- Internal Compliance: These are internally established controls for policies and procedures that will help the business go as smoothly as possible. It is set and enforced by members of the company itself.
- Security Training: Security audits are important in the sense they can help assess all safety aspects of a company including the methods and security procedures followed by employees to ensure the safety of records and data. If any areas of lacking are found appropriate training can be given to remedy the situation.
Processes In Security Audit Services
Application security audit and compliance services aren’t a single process, but rather a holistic umbrella term with different processes underneath it.
1. Vulnerability Assessments
Vulnerability assessments are one the most important processes in a security audit. This involves scanning your security system thoroughly to find any loopholes, vulnerabilities, or weak points in the security by carrying out a comprehensive scan.
Once the assessment of the systems in place is complete, a detailed report is generated with information regarding the vulnerabilities, their severity level, and the harm they pose to the organization. Additionally, measures to remediate these problems are also given by the security audit services so that the company’s development team can make the appropriate fixes.
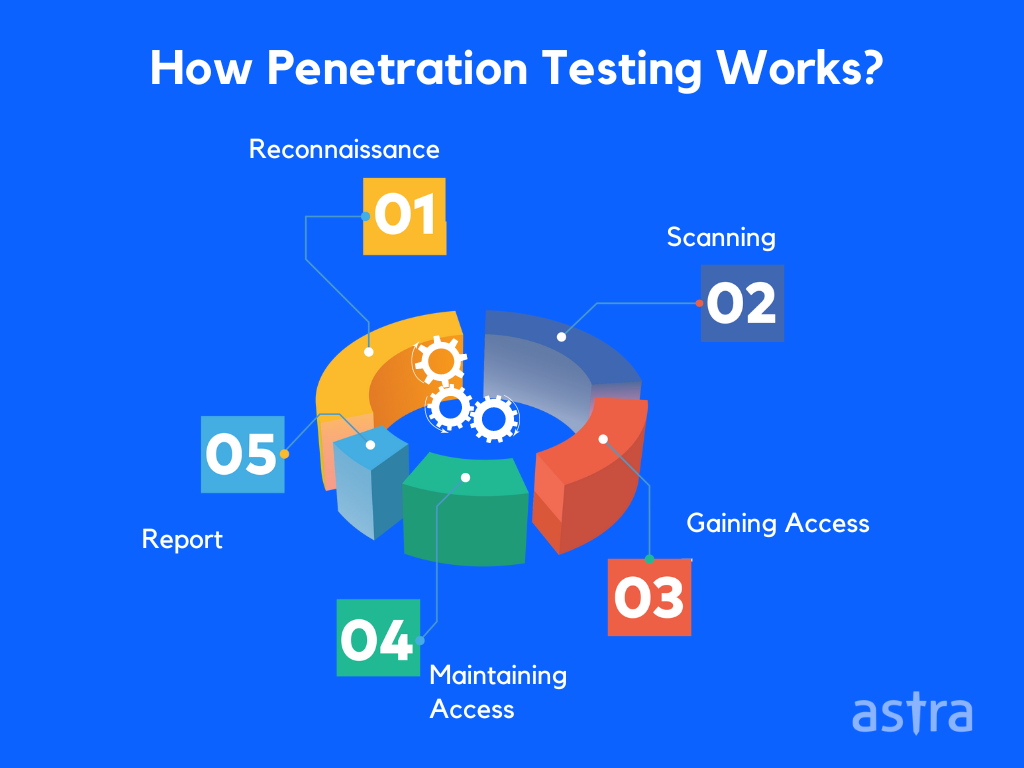
2. Penetration Tests
Penetration Test are similar to vulnerability assessments in the sense that a company’s security system is thoroughly scanned and scrutinized to find vulnerabilities. However, penetration tests go a step further and attempt to exploit these vulnerabilities with the help of ethical hackers.
This is done to understand the full extent of damage that could be caused by the identified vulnerabilities. Similar to vulnerability assessment reports, the list of vulnerabilities, their CVSS scores, and their effects are discussed in detail while also providing information on which attacks proved successful and what mitigative measures can be taken against them.
3. Risk Assessments
Risk assessments are a more generalized version of vulnerability assessment where any potential risks to a company’s security are assessed and reported. This can include identifying non-compliance risks, security risks, the possibility of breaches, and more.
As mentioned above, risk assessments are generally carried out to ensure continued compliance with industry standards, thereby helping to avoid any hefty penalties or even criminal charges. They are carried out by following a strict risk assessment checklist.
4. Compliance Audits
These are security audits done specifically from a compliance point of view to assess whether an organization’s every aspect is compliant with the standards and laws set by their industry. These are called external compliance audits.
However, there is another kind of audit, which is all about auditing the internal compliance of a company known as internal compliance audits. These audits check for any issues with compliance with standards and rules for procedures set by the company themselves. As the name suggests, internal security audits can be carried out by the company itself or by a hired third party.
Top 3 Security Audit Companies
1. Astra’s Security
Astra’s Pentest is a suite of tools put forth by Astra Security since 2013. Their products aim to make cybersecurity hassle-free and to ensure the same through comprehensive hacker-style pentests. Below mentioned are the detailed features of Astra’s Pentest:
- Security audit solutions provided by Astra’s Pentest include comprehensive vulnerability scanning and assessments, penetration tests, and website protection.
- Penetration tests are available for mobile and web applications, APIs and web services, cloud infrastructure, and networks.
- Astra’s Pentest can conduct more than 3000 tests that can help in identifying and exploiting vulnerabilities.
- Astra’s Pentest offers a highly comprehensive vulnerability scanner that is capable of detecting vulnerabilities based on intel, known CVEs, SANS 25, and OWASP Top 10.
- Astra’s Pentest Suite provides both manual and automated pentesting services thereby assuring zero false positives. It can also find out business logic errors.
- Helps ensure compliance with ISO 27001, GDPR, HIPAA, SOC2, and PCI-DSS.
- Expert and professional team of pentesters with years of knowledge that makes them the best in the field. They provide 24*7 support to customers to clear up doubts and queries.
- Highly intuitive and easy-to-navigate dashboard that provides all the details of vulnerabilities with CVSS scores, measures for remediations, and a comment box to interact with pentesters directly to clarify any doubts.
- Team members from an organization’s development team can be added to work alongside Astra pentesters to resolve vulnerabilities found during audits.
- Astra’s Pentest provides detailed reports after vulnerability assessment and penetration tests with a list of vulnerabilities, attacks carried out, CVSS scores, and patching recommendations. POC videos are also provided to make the vulnerability fixing process easier.
- Once the vulnerabilities found are fixed, rescans are provided to make sure that there aren’t any further vulnerabilities.
- Astra’s pentest can be integrated into your company’s CI/CD pipeline thus ensuring that all projects are secure throughout their development. This helps make the shift from DevOps to DevSecOps.
- Publicly verifiable certificates are provided once the pentests and rescans are done to ensure that all vulnerabilities have been appropriately fixed. These certificates are valid for 180 days and can boost customer confidence in one’s organization since it shows that they are security conscious.
2. Cyberops
Founded in India, Cyberops aims to shield the digital space with its products and services to reduce the exposure to malicious attacks faced by businesses. Features of Cyberops include:
- Cyberop provides security audit services like VAPT for networks, mobile and web applications, servers, and cloud as well as IoT devices.
- Their VAPT services help maintain compliance with various industry standards like ISO 27001, ISO 27701, and GDPR.
- They provide a safe-to-host certificate once testing is completed and the systems are secured.
- Their assessment reports are concise and mention the vulnerability details, impact, and measures to fix the vulnerabilities.
- Cyberops provides consultations by experts who utilize the latest testing tools as well as carry out manual testing.
- Provides risk and compliance management as well as vulnerability patch management.
- Provides cybercrime consultations for incident responses.
- Conducts assessments for UI/ UX to help organizations optimize and increase their customer satisfaction and revenue.
3. Intruder
Intruder is a cybersecurity provider that was established in 2015 to help organizations reduce their exposure to risks and any cyber-attacks. Their features include:
- Intruder provides security testing services like internal and external vulnerability scanning, cloud and web application vulnerability scanning, as well as continuous penetration testing services.
- Their services help with continuous vulnerability management through constant surveillance, comprehensive security checks, and immediate response to threat alerts.
- It helps protect and discover your cloud assets so you can keep them safe from exposure as well as synchronize the tool with the cloud to integrate scanning.
- Ensures compliance to various industry standards through easily carried out vulnerability scans.
- Provides timelines to understand how long fixing certain vulnerabilities will take thereby ensuring that the organization’s compliance isn’t jeopardized with the remediation timeline.
- Provides a free thirty-day trial for all services provided.
- Commonly used by SMEs, enterprises, and developers to ensure safety.

Types Of Security Audits
| Security Audit Type | Key Features |
|---|---|
| Web Security Audit | All aspects of a website including themes and extensions are tested. CVEs as well as business logic errors are taken into account. |
| Mobile Security Audit | These audits are integrated in the mobile app development process to protect the data from theft and deletion. |
| Cloud Security Audit | Cloud security audits ensure that the cloud infrastructure as well as the data in the cloud is secure. |
| Network Security Audit | Systematically goes through all devices, and software running on a network. |
| API Security Audit | It's currently considered just as important as we audits in terms of securing apps. |
| Security Compliance Audit | Compliance audits are specifically designed to check certain regulations. |
These are the different types of security audits provided by various companies. They include cybersecurity audit services for mobile and applications, cloud infrastructure and networks, API or web service audits, and lastly, security audit solutions for maintaining compliance with industry or company standards.
- Web Security Audits
Security testing provided for web applications helps identify vulnerabilities and loopholes within them before they are exploited. This can help stave off various kinds of threats like DDoS attacks, and even help find business logic errors. It’s not just the front end of a website that gets tested, rather all aspects of it including extensions and themes are assessed too.
- Mobile Security Audits
This refers to auditing applications that are built specifically for mobile devices. This is crucial since nearly everyone everywhere makes use of phones and has a lot of data stored in them. It, therefore, becomes a responsibility to measure to integrate security audits into the development pipeline of an application thus ensuring its safety from data theft or deletion.
- Cloud Security Audits
Cloud security audits are carried out on the cloud servers where copious amounts of data and applications are stored nowadays. It is therefore vital to ensure that the cloud server providers carry out regular audits and make sure that all vulnerabilities have been found and fixed. This ensures that the server clients do not face data or application theft and or loss as well as prevents loss of business and revenue.
- Network Security Audits
Network security forms a crucial cog in the wheel of IT security. Auditing refers to systematically going through all the devices, connections, and systems accessed through the internet. Such security audits carry relevance as networks usually see high activity in terms of data transfers and storage.
- API Security Audits
API security audits refer to auditing, pentesting, or assessing APIs for any vulnerabilities. Web services are also a type of API that can be audited. API security audits are vital, but they have been considered secondary in terms of protection where the primary importance always went to web applications. However, recent developments have shown that insecure APIs make for excellent targets for hackers which ultimately brought out the relevance of carrying out security audits on APIs.
- Security Compliance Audits
This particular security audit service aims to ensure and enforce an organization’s continuous compliance with industry-standard or even the company’s own set of rules and regulations. The former is called external compliance while the latter is known as internal compliance. Internal compliance security audits can be done by the company itself or by hiring external security audit services. External audits ensure that organizations are PCI-DSS, HIPAA, or SOC2 and ISO 27001 compliant depending on whichever is applicable to the organization.
Conclusion
This article has discussed all things security audit related that every organization should be aware of. This included the four processes under it, namely vulnerability and risk assessments, penetration tests, and compliance audits. Beyond this, the relevance of security audits and the top three security audit services were discussed in detail. Lastly, the article mentions the different types of security audits provided by companies for a variety of applications and even compliance.
FAQs
1. What are security audit services?
Security audit services refer to companies that provide various security audit processes like vulnerability and risk assessments, penetration tests, and compliance audits to organizations.
2. What are IT Security Audits?
IT security audit refers to the comprehensive analysis of an organization’s IT infrastructure. This includes penetration tests and vulnerability assessments of online infrastructure and assessments of the on-premise security infrastructure as well.
3. Top security audit companies in India?
The top security audit companies in India include Astra Security, Cyberops and Hicube.
















