Your business is at risk. Every day, cybercriminals are targeting businesses of all sizes with the goal of stealing sensitive data or causing damage. Cybercrime is expected to reach an all-time high of $10.5 trillion by 2025. The good news is that you can protect your business with a cyber security report.
In this article, we will explain what a cyber security report is and why your business needs one. We will also provide tips on how to create a powerful penetration testing report. Finally, we will highlight the key highlights of Astra’s comprehensive cyber security report.

What is a Cyber Security Report?
A cyber security report is an in-depth analysis of a company or organization’s cyber risk posture. This report helps organizations evaluate their cyber security practices and understand the threats they face on a daily basis.
It also provides insight into how well existing cyber defenses are functioning, assesses the technical risks, and identifies any vulnerabilities that need to be addressed.
Importance of Cyber Security Report for Business
A report on cyber security is essential for businesses as it provides important information that helps them protect their data and sensitive customer information from cyber attacks. Here are three key benefits of having a cyber security report:
- Adherence to Security Benchmarks: A cyber security assessment report can help companies adhere to industry standards, such as PCI DSS or NIST. This report can also ensure that cyber security measures are up to date and meet compliance requirements.
- Building trust: A cyber security report can help businesses build trust with their customers by showing that they take cyber security seriously and have taken the necessary steps to protect data and information.
- Comprehensive Evaluation: A cyber security report provides a comprehensive evaluation of a company’s cyber posture and helps identify areas of weakness that need to be addressed. It can also provide insights into the threats they are facing, and what steps need to be taken to protect against them.
Is Cybercrime on the Rise?
- Compared to the third quarter of 2021, global attacks increased by 28% in 2022. On average, 1,130 weekly attacks occurred per organization worldwide.
- According to a recent study, the Education/Research sector was hit the hardest by attacks this past quarter, averaging 2,148 per organization every week. This is an 18% increase compared to last year’s numbers.
- For the third quarter of 2022, ransomware was most commonly targeted towards the Healthcare sector out of all industries, with a 5% year-over-year increase in affected organizations (1 in 42).
Benefits of Cyber Security Reports
- Improved cyber security posture: A cyber security report helps organizations to understand their cyber risk posture and identify areas that need improvement.
- Increased visibility into cyber threats: Reports provide detailed insight into potential cyber threats and how these risks can be managed more effectively.
- Cost savings: By understanding cyber risks, organizations can focus their resources on the most important tasks and reduce costs associated with cyber incidents.
- More informed decision making: Having a thorough understanding of their cyber risk posture enables organizations to make better decisions regarding cyber defense strategies.
- Better communication between IT and business teams: Cyber security reports provide insight into technical issues, which helps bridge the gap between IT teams and business stakeholders when discussing solutions or strategies for mitigating cyber threats.
- Increased cyber preparedness: Reports provide visibility into cyber threats and help organizations develop plans for responding to cyber incidents.
- Improved employee awareness: By sharing cyber security reports with employees, organizations can increase awareness of cyber threats and improve the overall security posture of their company.
- Enhanced regulatory compliance: Cyber security reports can help organizations meet compliance requirements and reduce the risk of penalties or fines associated with non-compliance.
- Comprehensive coverage: Cyber security reports provide an in-depth look at an organization’s cyber risk posture and identify any gaps in its current cyber defenses that need attention.
- Utilize Astra’s comprehensive cyber security report: Astra Security provides a comprehensive cyber security report that helps organizations identify cyber threats, evaluate cyber risk posture, and develop effective cybersecurity strategies.
Cyber security reports are essential for businesses of all sizes. By understanding their cyber risks and identifying potential cyber threats, data protection from malicious actors becomes much more efficient for organizations.
Astra’s cyber security report provides an in-depth analysis of a company or organization’s cyber risk posture to help them stay ahead of the cybercriminals. With this valuable information at your fingertips, you can ensure that your business remains secure in today’s digital world.
How to Create a Powerful Cyber Security Report?
Understandability is key when constructing a cyber security report. Remember to take into account the members’ technical expertise, and avoid delving too deeply into every risk facing the organization security teams need to be able to present why the data matters in a concise way.
To create an effective cyber security report, here are five best practices:
1. Follow cyber security reporting guidelines
According to the Securities and Exchange Commission (SEC), reporting requirements for companies are very important, especially when it comes to cyber-related disclosures. This includes sharing information with shareholders and the board of directors. Back in 2018, the SEC said: “the Commission believes that it is critical that public companies take all required actions to inform investors about the material cybersecurity risks and incidents in a timely fashion.”
2. Determine the organization’s risk tolerance
Organizations can’t be expected to remember every single cyber vulnerability, so it’s important to help them establish a risk tolerance level. This way, everyone will understand what types of vulnerabilities are significant enough to warrant sharing information with the Board. Furthermore, by having this guide, your security team will have a standard by which they can measure their performance.
3. Define the threat environment
Instead of focusing on general security metrics and KPIs that don’t have a bearing on the company, focus on the highest-priority risks to give members an understanding of the threats most likely to compromise business goals or profits. This will help save the Board’s time and energy.
To keep your business secure, stay up-to-date on applicable incidents (e.g., how often they happen and how many people are affected), the preventive measures you have in place and the financial and reputational fallout of possible new threats. In addition, compare your organization’s security level to similar businesses in your industry using data-driven security ratings; this will help you better prioritize which dangers to focus on first.
4. The report should be financially focused
It is vital to communicate the financial implications of cybersecurity risks and initiatives effectively to decision-makers. This includes explaining potential investments for mitigating risk, as well as estimated costs associated with a data breach, such as business loss, legal fees, and reputational damage. By prioritizing cost-based initiatives according to how much risk they pose, you can avoid giving stakeholders too much information or misusing funds.
5. Set realistic expectations for deliverables
Given that security threats are always fluctuating, it’s key for businesses to have active risk mitigation plans. These ought to be revised on a regular basis to anticipate current dangers. It is very important to be grounded when developing these strategies in what can actually be done with the money, time, and manpower readily available so expectations are not set too high.
Templates And Example for Types of Cyber Security Reports
Cyber Security Report Example for Penetration Testing By Astra Security
Here is a cyber security reports template to assist you with making cyber security reports for pentest and vulnerability assessments.
Cyber Security Incident Report Template
Here is a commonly used cyber security incident report example.
How Security Ratings can Help with Cyber Security Reporting
A cyber security rating is a score that reflects an organization’s level of cyber security. By regularly assessing cyber security ratings, organizations can better understand their cyber risk exposure and identify opportunities to take proactive steps in improving their cyber posture. Security ratings provide an easy-to-understand view of cyber security performance, and they can be used as part of a cyber security report to evaluate the effectiveness of current initiatives and determine which areas need more attention.
In summary, creating a cyber security report should involve a detailed outline of uncovered vulnerabilities, executive summary & CVSS score (Common Vulnerability Scoring System), assessment of business impact, insight into exploitation difficulty, technical risks briefing, remediation, strategic recommendations, etc. Moreover, understanding your company’s cyber risk exposure with the help of security ratings can aid cyber security reporting significantly.
Cyber Security Report by Astra
Any business cannot afford to put its security at risk, regardless of size. One security vulnerability could mean the downfall of your company. Astra’s team can help you find all current vulnerabilities and create a plan to make sure they’re patched up. You’ll have extra peace of mind knowing that our experienced professionals are keeping an eye on things for you!
Astra’s cyber security report brings together all these elements in an easy-to-understand format and provides key highlights to help companies evaluate their cyber posture. With the right cyber security report, organizations can gain the confidence needed to make informed decisions and keep up with emerging threats. Ultimately, cyber security reporting ensures that a business is prepared to protect itself and its customers against cyber threats.
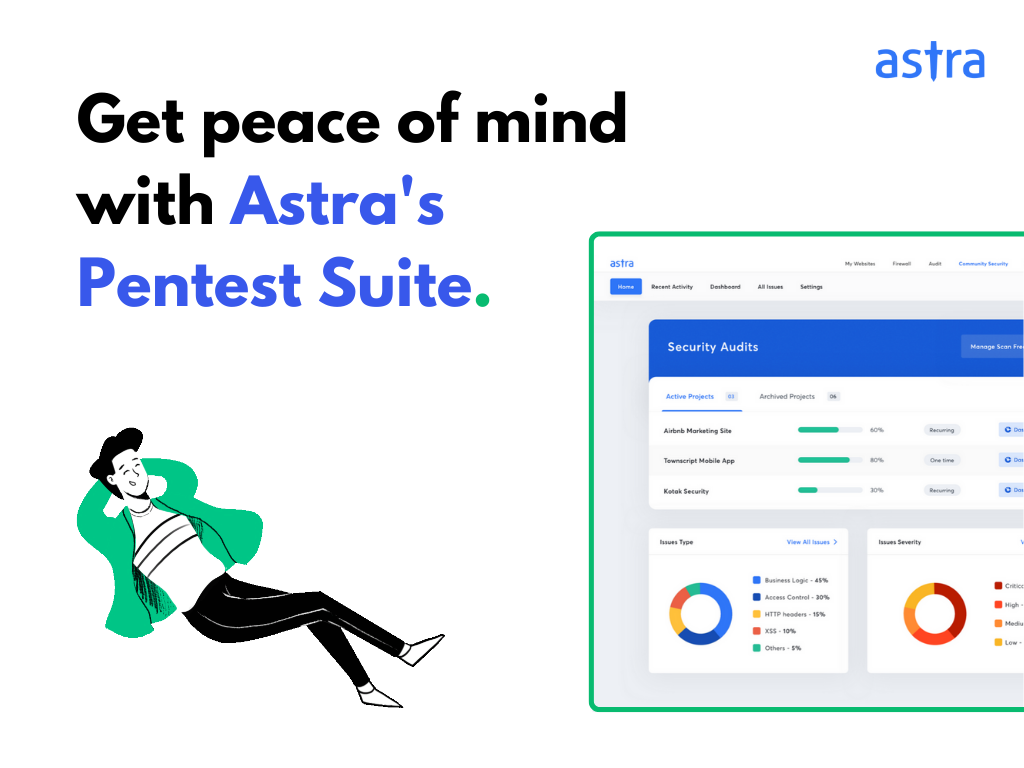
Key Highlights of Astra’s Comprehensive Cyber Security Report
The below shown is a sample cybersecurity pentest report by Astra.
The following are key features of Astra’s cyber security report:
- Industry Standard Security Testing: We at Astra pride ourselves on our ability to provide comprehensive security by running over 8000+ tests that follow OWASP, SANS, ISO, and CREST guidelines. This way, we can be sure that your applications and networks are well-protected.
- Detailed Vulnerability Analysis: Astra Security’s new scanning dashboard and pentest report provide clear insight into vulnerabilities, including their impact, severity levels, CVSS score, and more. You can also integrate your pentest project with GitLab & GitHub for easy tracking, and start automation scans with every new code update!
- Steps to Fix Vulnerabilities: In every security assessment report, we outline both the preventative measures to stop similar vulnerabilities in the future as well as specific steps (remediation) to address each individual flaw. With our pentesting dashboard, you can easily track progress and communicate with whoever is responsible for addressing a particular vulnerability.
- Graphical Representation of the Complete Pentest Scan: At Astra, we understand that one size does not fit all. That’s why we take the time to tailor our cyber security reports to meet the specific needs of each customer. Our goal is to help your dev and security teams quickly and safely address any pentest discoveries.
- Easy to access: You can easily download the cyber security report from Astra’s main dashboard. You can also choose to download the report in PDF or email format.
Test features from the report can be divided into categories according to the identified issue and type of testing Astra carried out, as demonstrated in a sample penetration testing dashboard.
Wrapping Up
A cyber security report is an essential tool for any business looking to protect its digital assets. Astra’s cyber security services provides organizations with the insights needed to close vulnerabilities and identify areas of improvement. With detailed vulnerability analysis, step-by-step instructions for remediation, a graphical representation of the entire scan, and more, Astra helps you stay secure and keep up with the latest cyber threats.
FAQs
How can I access the cyber security report from Astra?
The cyber security report from Astra can easily be downloaded from our main dashboard in PDF or email format. You may also choose to integrate your pentest project with GitLab & GitHub for easy tracking and start automation scans with each new code update.
How often should cyber security reports be updated?
It is recommended that cyber security reports are reviewed and updated regularly to ensure that any newly identified vulnerabilities or threats are addressed quickly. Astra offers automated pentest scans with each new code update, making it easy to stay up-to-date on cyber security health.
How does Astra help businesses achieve the highest levels of cyber security?
Astra helps you stay secure and keep up with the latest cyber threats by providing industry-standard security testing, detailed vulnerability analysis, steps to fix vulnerabilities, graphical representation of the complete pentest with our cyber security report.
















