One of the things that Mr. Robot taught us is that a big scale cybersecurity breach isn’t far from reality. The internet is such a vast place, hiding dangers can put your business at risk at any moment. Despite the technological advancements in the field of cybersecurity, no-one can guarantee that a data breach won’t happen to you.
Numbers can also be frightening as data breaches in the U.S. reached 1.47 billion in 2019 from 157 million it was back in 2005. If a data breach happens to you, you need to be prepared and know which steps you need to take to minimize the damage.
To give you and your business a helping hand during that unfortunate event, we’ve collected 6 ways to help you respond to the cyber-crisis.
So, read on to find out how to deal with a data breach.
How to Respond to a Cybersecurity Breach?
I’m sure you’ve heard that “prevention is better than cure.” With this in mind, you should always be prepared for a cybersecurity breach regardless of how secure your systems are.
The main principles you should follow are to prepare yourself, respond accordingly, and plan for any future threat by learning from these unfortunate events. To give you a visual idea, here’s what you need to keep in mind when you deal with a cybersecurity breach:
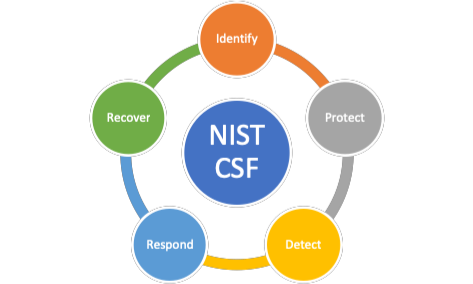
Now, let’s see what these steps entail!
1. Report the Cybersecurity Incident
With the emergence of privacy protection laws like the GDPR, companies have adopted stricter data privacy rules. Especially for businesses targeting European audiences, you should make sure that your marketing automation software complies with the regulations. Not only that, but GDPR also dictates that notifying the public is necessary in case of a breach.
Keep in mind, that if the data breach has the potential to cause social damage to your customers and result in financial losses, reporting the incident is the safest way to address it. Dealing with a cybersecurity breach requires you to communicate with several people. From senior management to the press, you have to know who to contact to avoid any possible problems from delaying to make the public aware. Addressing the situation will help your users understand the problem and take individual measures.
2. Call Your Security Response Team
To successfully deal with the incident, you need to call your security response team, assess the situation, and come up with an effective solution. Whether you have an eCommerce business, an agency, or a SaaS company, having a security response team on hand will allow you to fight the threat faster.
Your team will help you execute your data breach plan and make sure that every step is meticulously followed. Here are some of the things that your response team will handle for you:
- Collect the incident reports and conduct the analysis.
- Communicate with the individuals affected by the breach.
- Choose the right tools to respond to the threat and recover the data.
While your response team might be able to respond to the incident if the threat is beyond your team’s power, you should also consider getting professional help as well.
3. Find the Source of the Breach
With your response team ready, it’s time to find the source of the data breach. In this step, you’ll have to discover the possible weaknesses that the cybercriminal leveraged to bypass your security. While systems and networks are often responsible for data breaches, your employees can also be the cause – sometimes without even knowing.
Among others, stolen credentials, lost devices, and weak passwords are the most common causes of a cybersecurity breach.
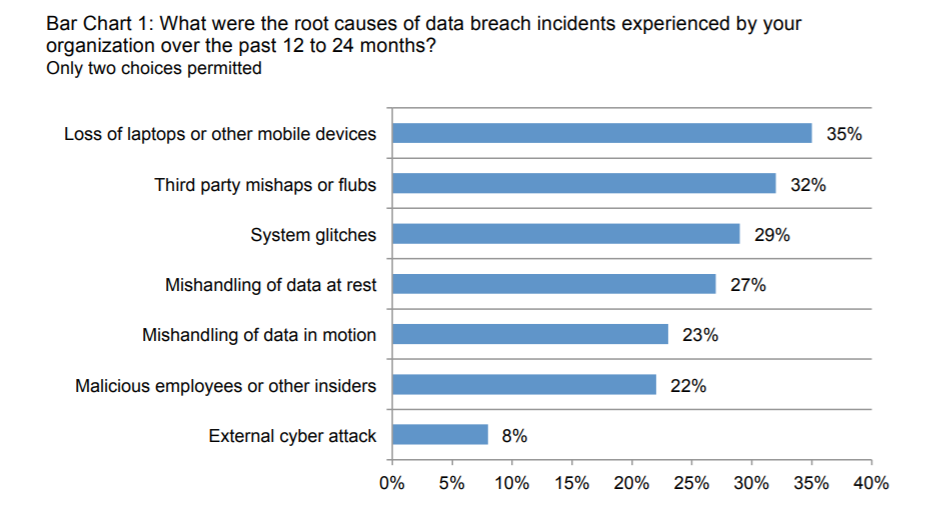
What’s more, an inside error can also lead to a breach within a few minutes. If that’s the case, you and your team should be careful about how to handle the employee responsible for the mistake. However, don’t forget to cross out the possibility of malicious intent as well. Learning more about the potential source of a data breach will help you respond faster.
4. Contain the Cybersecurity Breach
Once you identify the source of the breach, you need to take the necessary steps to contain it within 48 hours. For this, your team needs to see if it can stop the unauthorized access to the compromised systems. If necessary, you need to take offline the infected devices to minimize the communication between them and the cybercriminal.
Furthermore, you need to make sure that auditing is up and running before proceeding. A security audit will help you assess the data you have and who has access to it. By looking at the flow of the information you can determine whether you have successfully contained the data breach or not.
5. Eliminate the Cause of the Breach
If you followed your incident response plan and managed to contain the threat, it’s time to eliminate the cause of the problem. To eradicate the cause, you can utilize some of the best security tools like Astra to help you secure your data and remove malicious software. As you can see below, 51% of breaches had to do with malware.

So, if you are dealing with a malware attack, you can use your tools to remove the threat and run malware scans to determine the extent of the infection.
While deleting malicious software is the starting point to restore your system, the leaked data is what might cause you and your users problems in the future. For this, you should make sure that the people affected are aware of the leak to prevent any future financial fraud or identity theft.
6. Restoring Your System
Restoring your system to its previous glory after a breach will take time. However, this time you need to be careful and use what you learned to ensure that another breach doesn’t happen. Identifying your weaknesses and implementing further improvements on every part of your system will minimize the chances of another data breach.
Fighting a security breach is a major challenge for every company. As cybercriminals find new ways to exploit systems, you need to be alert and monitor your data flow for any abnormalities. Of course, you can also help your company by educating your employees on cybersecurity threats. This way, you’ll have one less thing to worry about.
Conclusion
Security incidents are bound to happen to every business regardless of security level. To respond to the threat, you need an experienced team that will handle the breach, minimize the damage, and prevents further loss.
So, if it happens to you, make sure to have an incident response plan in place, ask for help, if necessary, and use the right tools to eliminate the threat. Educating your company about security issues and training them is also essential to prevent such incidents. Now, you are ready to successfully deal with any cybersecurity breach.
















