In this era of the internet, nothing comes for free! And if it’s coming, it may probably be a threat in the form of a virus or malware. According to Benjamin Franklin “An ounce of prevention is worth a pound of cure”, and prevention in this digital age can be effectively deemed as knowledge.
In this blog post today, we are going to learn the difference between malware and a virus. Their process of infecting a programmed software and how you can you possibly protect yourself from these.
What is Malware?
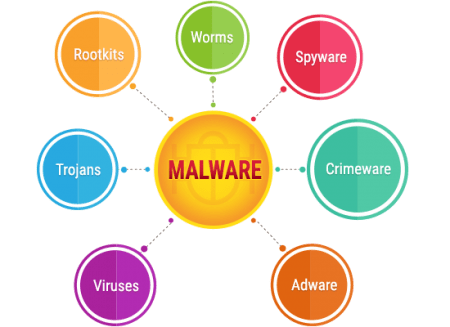
To define in simple words a malware is a software or a computer program that can be leveraged to perform harmful or malicious actions. The term malware is derived from malicious + software and is strategically designed to create a breach and infiltrate the system with viruses, spyware, trojans, worms and more in order to get access to your personal information. The nature of the information may vary broadly. Ranging from personal data such as email, medical records, financial records, personal images or recording to highly sensitive and critical information related to military, development, governments and even national security.
Regardless of the overall purpose, malware is the last thing that you would want on a computer system. The target of a cyber-criminal behind a malware attack is to always gain unauthorized access into the system. Once installed, they may potentially have partial access or complete access in worst-case scenarios, depending upon the strength of your firewall or antivirus.
What is a Virus?
A virus is a specific type of malware, which functions as a parasite and replicates itself until the target is achieved or the entire system is affected, whichever happens, earlier. It is a self-reproducing computer program that executes the functions as instructed by the developer. It basically exhibits 3 main characteristics:
- Replication / Duplication
- Activation / Execution
- Objective / Target achievement
A virus majorly consists of two parts, each responsible for different actions executed by the virus. These are ‘insertion code’ and ‘payload’ where the insertion code inserts a copy of the file into the targeted system and payload instructs the virus to perform the malicious activity. The schema of the virus is a set of detailed instructions defined strategically by the virus developer. The choices of the attack may depend upon various factors such as the location of the victim system, size of the system, durability, and strength of the security or any other customized situation. The basic strategies that are followed by the developer while creating a virus are:
- Spreading conditions
- Infection strategy
- Code placement strategy
- Execution strategy
- Stealth strategy
Spotting the Major Difference
It is often misinterpreted by the users that one is a synonym of the other and are used interchangeably. To define ‘a virus is a specific type of malware’ which can infect anything as programmed. Thus, a virus is a subset of the umbrella ‘malware’ which has a specifically defined objective.
The Scope of the Attack
Users often tend to believe or have a misconception that it’s often the windows based computer systems that are prone to get attacked by the malware. The single reason behind this popular belief is the wide-spread availability of the operating system, including the pirated versions floating over the internet, which makes it an easy target. This is an obsolete fact, due to the interventions of the mobile technology mobile devices are now equally vulnerable to get affected, in fact, according to a Verizon report 94% of malware was delivered by email. The prevalence of malicious software in mobile devices such as smartphones and tablets have been in an accrescent mode.
According to a fresh report by The Register, approximately 620 million accounts from hacked websites were on sale on the TOR network from Dream Market cyber-souk. These websites included 500px, Dubsmash, Armor Games, BookMate and accounts from 12 other sites comprising names, Email IDs and passwords which were up for sale at just USD $20,000. It is believed that the pricing for the stolen data was kept this low as there was no payment information in the stolen data, had it been there, the prices would have been way too steep.
How do these Infections Happen?
Opening email or email attachments to be specific from unknown senders is the most common way to get infected. Also, file sharing through external storage devices without proper scanning or sharing via the internet are easily affected. Strictly refrain from falling victim to ‘You have won USD$ 5000’ or ‘You are our lucky winner to the mega jackpot’ mails. Also, downloading pirated software or installing ‘free’ programs over the web can seriously affect the system.
The best practice that needs to be followed is to never open suspicious emails from unknown sources, especially if there is an attachment. However, if the incoming email is coming from a known source, it’s highly recommended to scan the email with a premium scanning tool. It often happens that you get suspicious emails from your contacts (friends, business contacts or relatives because the chances are quite high that even the sender of the email is unaware of being affected. The most commonly happening occurrence of such an example is of mails with greeting cards or holiday wishes. It is recommended to stay updated with a premium virus protection program.
Infections arising from external storage devices such as floppy, flash drives or CDs can happen at the time when you leave it unscanned. The same thing can also happen while downloading a suspicious or free file from an unknown origin over the internet.
The emergence of the internet has completely disrupted the digital ecosystem and has filled the webspace with ‘freebies’ or ‘shareware’ that can be downloaded, installed and used. These freebies often come with toolbars, games, screensavers and a multitude of other applications that claim to offer ‘helpful’ or ‘entertainment’ resources. Though it’s not necessary that all of these freebies pose a threat or are malicious in nature but a majority of them do. As soon as these freebies are installed on your system, it starts tracking your activity and sends attractive ad popups based on your browsing habits.
Reclaiming the Affected System
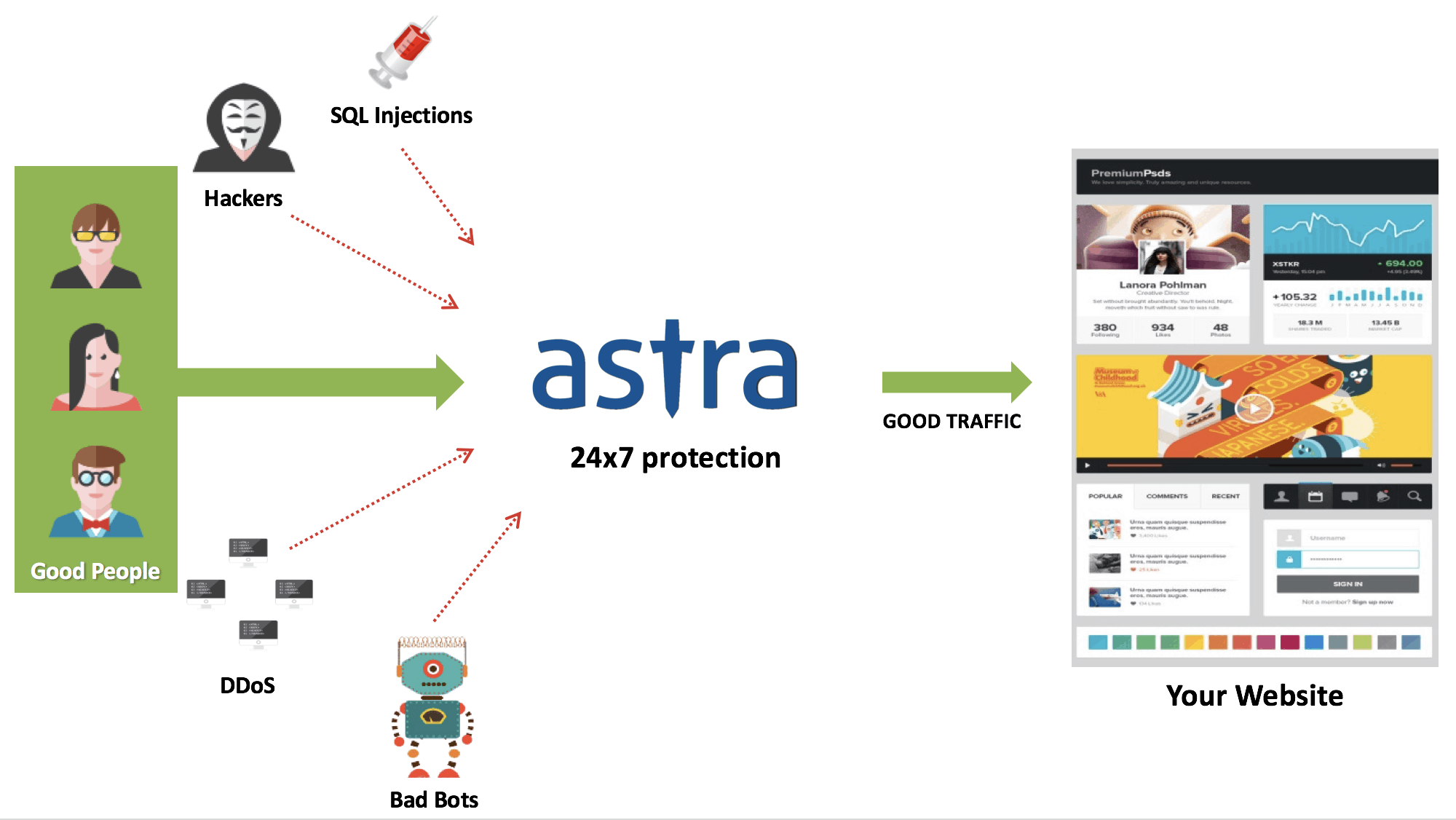
One significant method to reclaim your system is to ensure stringent mobile security and cloud testing services. Which executes effective penetration threats to detect all possible breaches into the system and optimizes the system for digital quality assurance. Also, a trusted web application firewall can be leveraged to ensure maximum security.
For overall protection, it is always recommended to use a licensed version of antivirus or anti-malware to constantly keep the system under check. You can use Astra’s complete site protection to ensure all-round protection of your website.
In case of extreme damage, a detailed security audit of the website & system is recommended. Astra’s Vulnerability Assessment & Penetration Testing shall help you with it. For all other cases staying updated is recommended.