Article Summary
Penetration testing is the process of testing a computer system, network, or Web application to find vulnerabilities that an attacker could exploit. The point of a penetration test is to identify potential vulnerabilities that a malicious user could exploit. The idea is to test for weaknesses that a malicious user could exploit, not a system administrator. Penetration testing is not a one-and-done activity. Instead, it is a process that an organization must undertake regularly. The frequency of the tests depends on risk assessments and the organizational structure of the company.
With the growing trend of cyberattacks in the last few years, it is essential that companies are aware of this threat and can identify vulnerabilities in their systems. Cyber threats are not only becoming more frequent but also more sophisticated. The most cost-effective way to reduce your risk of cyber-attacks is through penetration testing.
Introduction to Penetration Testing
As the frequency and severity of attacks increase, the need for cyber security testing dramatically increases. Penetration testing is an invaluable process that can identify vulnerabilities and issues that traditional IT security tools may not pick up, but what exactly is penetration testing and why is it important for businesses?
Penetration testing include testing of a computer system, network, or web application to find vulnerabilities that an attacker could exploit. The point of a penetration test is to identify potential vulnerabilities that a malicious user could exploit.
The idea of a pentest is to test for weaknesses that a malicious user could exploit, not a system administrator. Penetration testing is not a one-and-done activity. Instead, it is a process that an organization must undertake regularly. The frequency of the tests depends on risk assessments and the organizational structure of the company.
Penetration testing is an effective and proven method for finding and fixing security weaknesses before being exploited by cybercriminals and hackers. It allows your security team to discover weaknesses in your defenses before a cyberattack occurs.
Why is Penetration Testing necessary?
Penetration testing is an essential part of any cyber security strategy.
Penetration testing helps in validating the security of an organization’s systems, applications, and networks. It is used to find security weaknesses before criminals do. Penetration testers (or “pentesters”) launch simulated attacks to find security holes. This process helps an organization find and fix flaws before a criminal can exploit them.
Penetration testing provides a way to test the effectiveness of the system’s security controls. It helps organizations design their security processes and security controls to be more effective.
Also Read: Top Penetration Testing Services & Providers – Comparison with Reviews
3 Reasons why penetration testing is important
1. Secure Infrastructure
Secure infrastructure is extremely important for any organization. There are many ways to test a security infrastructure and one of the most common ways is Penetration testing.
Penetration testing helps in finding out the weak spots in the application or the network which can be easily exploited by a cyber criminal.
2. Customer Trust and Company Reputation
Reputation is everything. It’s what makes the world go around, and it’s the main focus of most businesses. A business’s reputation can make or break it. Simple news about a company’s data leak can destroy all the reputations you have built over ages.
3. Efficient Security Measures and Security Awareness
The security of the organization’s data is of paramount importance. However, it is at risk of being attacked, whether by an employee who accepts a bribe to leak confidential information or by hackers, so it’s important to be prepared. A penetration test is a non-destructive way to map out potential security gaps before an attack occurs.
Also Read: A Complete Guide to Cloud Security Testing | 11 Top Penetration Testing Tools/Software of 2022
How much can a data breach cost you?
A data breach can be a big problem for a company, and the consequences might be enormous and affect the whole organization. There are financial, legal, and reputational consequences involved. In addition, the direct economic consequences will also come from the costs and the implications of the data breach.
The financial costs of a data breach are essential to quantify, but they’re just part of the cost. The more insidious impact is the direct losses that occur because of the violation, such as decreased consumer confidence, lost business, regulatory fines, penalties, fraudulent transactions, and more.
There are many costs associated with a data breach. The most direct of these are the costs related to the breach’s investigation, notification, and remediation. These are the costs that are often incurred by the company directly. As the IBM study found, these costs continue to rise; Data breach costs rose from USD 3.86 million to USD 4.24 million, the highest average total price in the 17-year history of this report. Regular penetration tests reduces chances of data breaches by keeping the applications secure.
How often should you conduct a pentest?
You may be wondering how often you should perform penetration testing. The answer is dependent on your company’s risk level. An organization with no sensitive data on its network might test once a month, while an e-commerce site that carries a high-risk group of information theft may need to try on a weekly or daily basis. Some even test their security continuously.
The important thing is to find what works best for your organization. If you are unsure of the level of risk your company faces, it is best to consult with a security professional.
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
How does penetration testing help with Regulations?
Regulatory compliance is one of the most important things that must be considered when starting a new business. The regulatory aspect is one of the top concerns for any business to be successful. Every industry has its own set of rules and regulations.
Penetration testing (aka pen testing) is an application security assessment technique designed to identify vulnerabilities in target applications. Businesses and organizations often employ it to comply with governmental regulations such as Sarbanes-Oxley (SOX), HIPAA, and FISMA.
Penetration tests may be performed on various systems and devices, including computers, laptops, web servers, firewalls, and routers. They are executed by independent contractors and may be used by organizations to demonstrate compliance with industry regulations. Penetration tests will contain a report of the findings and will often recommend how to fix or mitigate the identified vulnerabilities.
How is Penetration Testing different from Vulnerability Assessment?
There are a lot of misconceptions about penetration testing and vulnerability scanning. Penetration testing and vulnerability scanning are both essential aspects of network security, but they serve different purposes. Penetration testing is used to test a network’s defenses against a real-world attack. At the same time, a vulnerability assessment is a non-intrusive scan that looks for potential vulnerabilities in a network.
Penetration testing is usually done for:
Penetration tests are an essential part of any security strategy. They involve a team of experts who simulate a real-world cyber-attack on a company’s systems and applications to see the vulnerabilities of its network.
A penetration test is a broad term that can be broken down into 5 categories:
- Web application and API penetration testing
- Mobile application penetration testing
- Cloud penetration testing (AWS, GCP, and Azure)
- Blockchain and Smart Contracts penetration testing
- Network penetration testing
How to conduct penetration testing??
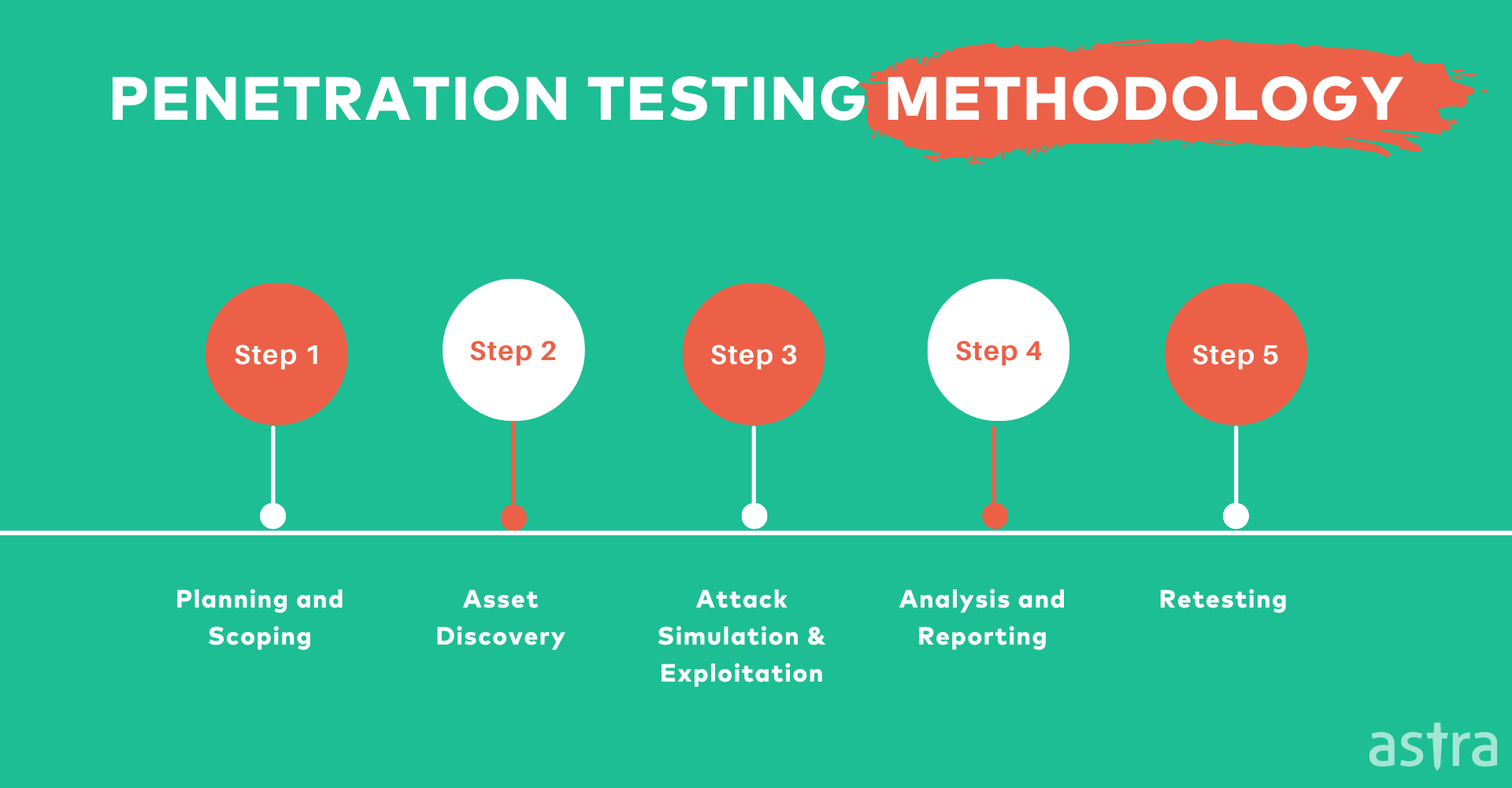
Penetration Testing can be conducted in 5 different steps. Let’s understand all of them in detail:
STEP 1: Planning and Scoping
Many things go into planning a pen test, but the scope, timeline, and limitations are the most important things. What are you testing? Who is carrying out the tests? What are the assets involved in testing? How long will the testing take? What are the attack surface boundaries? What are the limitations of the test? Which tools will you be using for the testing?
The limitations are the essential part of the planning phase. Limitations are parameters that are set in place so that testers can focus on the most important things. This includes things like: What are you not testing? What is the scope of the test? What are the goals of the test? These are the things that you will need to define upfront before moving forward with your trial.
STEP 2: Asset Discovery
At the beginning of the penetration test, the penetration testing company will perform a reconnaissance of the target system. The team will identify the IP addresses, domain names, and other information the target system uses. The team will also identify the type of devices used by the target to determine what kind of firewall the target has.
Reconnaissance helps the pentest team to identify the type of firewall and the connection the target has between the client and the server. Some common steps involved while performing reconnaissance are:
- Email reconnaissance
- Network reconnaissance
- DNS and whois reconnaissance
- Application reconnaissance
- Social engineering
The steps involved while performing reconnaissance are not limited to these above mentioned steps.
Some of the common tools to perform reconnaissance are:
- Google: Google is a library of information. Pentesters use google dorks to find sensitive endpoints or files such as logs or config files.
- Shodan: Shodan is a search engine used to find various kinds of servers over the globe. Pentesters use different shodan dorks to find origin ip addresses behind load balancers and servers having specific version or config.
- Nmap or Genmap: Nmap is a port scanner which is used to scan ports of any host or ip address. Nmap is a CLI based tool whereas Genmap is a GUI based port scanner tool.
- Aquatone: Aquatone is used to take screenshots of hosts which helps to save a lot of time. It takes in a list of hosts or routable ip addresses and returns a screenshot of every host.
- Nuclei: Nuclei is a tool which contains a set of templates which scans a list of URLs for publicly available exploits or CVEs
STEP 3. Attack simulation and exploitation
After the discovery phase, now the penetration testers have complete knowledge of the target system. In the attack simulation and exploitation phase, the pentesters start stimulating real-world attacks. Various kinds of automatic scanners are also beginning to keep checking for vulnerabilities. The penetration testing is not limited to automatic scanners, manual tests are also performed to find security risks that are usually missed by automated scanners. Some common risks that automated scanners miss are Business logic, Zero day exploits, Bypasses of issues such as SSRF, XSS, etc.
Based on the information from the discovery phase, the team starts finding CVE’s and attacking the software/application based on the technologies being used.
STEP 4. Analysis and Reporting
Once the penetration testing is complete, the pentest team starts generating penetration testing reports. A pentest report is a written document that describes the findings and results of an investigation or research. A well-written report has information about all the findings, a list of targets, exploits used, how to fix and remediate the issues.
Check out this article: Penetration Testing Report OR VAPT Report by Astra
STEP 5. Retesting
Retesting is an essential but optional part of the penetration testing methodology. After the organization patches the vulnerabilities, the penetration testers start testing again, known as retesting, to confirm if the issues have been fixed properly.
The retesting phase usually results in a bypass of the patch that the organization has applied.
What are three different types of penetration testing approaches?
There are three main types of penetration testing. Black, White, and Gray. Not to be confused with the hacker colors of black, white, and grey (used to identify an attacker’s skill level).
1. Black Box Testing
Black box testing is when the tester has no prior knowledge of the environment that is being tested. This is the most common kind of pen-testing. Information is typically gained through public resources, such as the Internet.
2. White Box Testing
White box testing is when the tester has complete knowledge of the environment that is being tested. Information is typically gained through access to the internal network or other confidential resources.
3. Gray Box Testing
Gray box testing is a combination of white and black box testing. Information is typically gained through partial knowledge of the environment.
What are Internal and External Penetration tests?
External Penetration Testing
External Penetration Testing is a form of penetration testing performed against non-production targets, such as service providers and business partners, and against external to the organization network and infrastructure. The basic goal of external penetration testing is to identify and exploit vulnerabilities and gain access to the internal network.
External Penetration Testing is not only used for testing your business partners and suppliers, but can also help to identify weaknesses in your defenses that an attacker could leverage to gain access to your internal network. It is also commonly referred to as Outside-In testing.
Internal Penetration Testing
Internal penetration testing is one of the best ways to ensure that an organization is protected from insider threats. The reason for this is that it allows the penetration tester to gain the same level of access as an insider. This means that the tester can use the same privileges as the insider. This allows the tester to use the same tools as the insider.
The penetration tester can move about the network in the same way as the insider. The tester essentially becomes the insider. This is not possible with external testing. External testing is great for finding vulnerabilities but it does not allow the tester to move freely about the network.
How is Penetration Testing Different from Vulnerability Assessment?
There are a lot of misconceptions about penetration testing and vulnerability scanning. Penetration testing and vulnerability scanning are both important aspects of network security, but they serve different purposes. Let’s understand both of them in detail.
Penetration testing is used to test a network’s defenses against a real-world attack. Penetration tests are most often performed by IT professionals, or security consultants. The goal of a penetration test is to determine the security posture of a system. Penetration testing is an excellent method for validating the security of your system. It’s also a great way to find security vulnerabilities before they are exploited. Penetration testing is different from vulnerability scanning, which is a method of identifying known vulnerabilities. Here are three examples of penetration testing techniques.
On the other hand, Vulnerability scanning is a network security analysis tool that probes a network, system, or application in search of vulnerabilities. Vulnerability scanning may also refer to a vulnerability management process. Vulnerability Scanning can be done on a single or a group of network/applications.
Vulnerability scanners examine weak points in a system’s defenses. The most common reason for a vulnerability scan is to find a way to hack a system or network.
What are different types of tools used for penetration testing?
1) Web penetration testing: Some common tools used to perform web application penetration testing are Astra, OWASP ZAP, Nmap, Nuclei, Dirbuster etc.
2) Cloud penetration testing: Some common tools used to perform penetration testing are Astra, Pacu, Prowler, Cloudjack etc.
3) Network penetration testing: Some common tools used to perform network penetration testing are Nmap, Wireshark, httpsniff etc.
4) Mobile penetration testing: MobeSF, Astra Security Scan, Cydia, apktool are some of the most common tools used to perform mobile application penetration testing.
5) Blockchain penetration testing: BitcoinJ, Truffle and Astra security scanner are one of the best blockchain penetration testing tools available.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
What is the average cost of a pentest ?
Cost a penetration test depends on a lot of factors. Some of the following factors include:
- Scope of work
- Size of organization
- Type of penetration test to be performed
- Approach of pentest
- Experience of Pentesters
- Consultation and Remediation
Read more about How Much Does a Penetration Testing Cost on Average?
Why do you need Astra’s Pentest Suite?
Astra has been in business for over 6 years providing security to companies of all sizes. Astra has a team of professional security engineers whose only goal is to keep your organization secure.
Astra knows that security is their only goal, and we deliver the best services to our clients. We Don’t care about taking up all your time with long meetings and other non-value-based activities. Astra comes with a user-friendly dashboard with collaborative support, easy-to-read reports, and much more.
Astra’s Pentest is the best penetration testing solution available in the market. Astra offers penetration testing services in various fields such as API, Web, Mobile, Blockchain, and Network.
Some features of Astra’s penetration testing suite are:
1. Collaborative Dashboard
No more back and forth with long email threads. Astra’s vulnerability management dashboard gives you a bird-eye view of your VAPT progress.
2. Payment Hack Analysis
Astra tests your checkout flows to ensure hackers cannot steal credit card information or buy products for free.
3. Server Infrastructure Testing
Astra’s scanners audit your server configuration to ensure that your server is secure & hardened from all types of server-level attacks.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
4. VAPT Security Certificate
Get a safe-to-host certificate after fixing the vulnerabilities. Share the certificate with your growing customers to showcase how secure your applications are.
5. Consultation Call
Get on a call with your account manager and Astra’s security experts for an in detail consultation session about your application’s security.

Conclusion
Penetration Testing is the most demanding and complicated task among all the cyber challenges. Penetration Testing is a way of attacking a company’s systems and infrastructure to test the security and vulnerability. Penetration testing is an excellent way to validate the security of your website. Look no further than us at Astra when you are looking for an ethical hacker who can help you with this task. We have skilled security professionals at our disposal who are ready to help you with your penetration testing needs.
FAQs
1. What is Penetration Testing?
Penetration testing refers to the process of evaluating a system’s security posture by finding and exploiting vulnerabilities present in the said system.
2. Why Perform Penetration Testing?
Penetration testing is essential for some compliance regulations. That aside, you should perform frequent pentests to evaluate and strengthen your security measures against cyberattacks.
3. What is the average cost of a pentest ?
The average cost of pentesting for web apps is between $99 and $399 per month.
















