Network pentesting is the process of professionally carrying out a hacker-style attack on your network assets to detect and exploit vulnerabilities in network security and to assess the efficacy of the responses to them as it could lead to a compromised cloud or network environment.
For easier reference, imagine it to be a mock drill against known cyber threats. The goal of a network pentest is to detect security vulnerabilities in a network and help the target organization strengthen its defenses against cyber threats.
What Is The Importance Of Network Pentesting?
To understand more about how to secure networks and prevent data breaches, we’ve put some insights into the importance of network penetration testing through this article.
- Internal pentests involve stimulated cyberattacks specific to your business scenario, for example: undetected business logic errors within your payment channel.
- With an external pentest or black box testing service, you get the POV of an outsider i.e. a hacker or a malicious actor looking to exploit the vulnerabilities in your network.
- It can help in the detection of minute vulnerabilities within the firewall and other network security measures through concentrated efforts.
- Vulnerability scans with a pentest allows you to use the risk reports from the scan to apply
Sometimes, organizations who have put their systems through vulnerability scanning doubt the relevance of pen tests since both processes have the same goal. However, an internal or external network pen test is to follow vulnerability assessments. It allows you to cyclically go through a website vulnerability scanner, attain risk reports and the varying levels of danger, and use this information to conduct a pen test before preparing the final assessment and applying fixes.
What is the Purpose of Network Pen test?
1. Protect your data
Single-handedly the most important reason, every organization must guard itself against data breaches. Pen testing networks often function like ethical hacks and simulate cyber attacks as best as possible. A small weakness has the potential to let out sensitive information, affecting your customers’ trust and the more serious violation of various rules and regulations. Here, a helpful way to determine the level of possible intrusion is to identify the different levels of risk that you are exposed to.
2. Ensuring overall security
Be it the structure of your business as a whole, sensitive data, or newly released applications, ensure that no overlooked flaw can compromise your integrity through network pentests. Security assessments and website security scans should be a part and parcel of any new initiatives, especially if there is the management of important data. Some examples of such flaws include SQL injections, weakly configured firewalls, outdated software, and traditional virus or malware.
3. Compliance requirements
Certain regulations insist on penetration testing services, no matter the industry. For example, data security for the payment card industry ensures such tests for the protection of customers’ sensitive information (PCI DSS).
4. Continued maintenance
Network pen tests require multiple runs through a continuous time period to ensure long-term security. Professionals hired for this purpose will also look over the security controls used for the business network such as firewall, layered security, encryption processes, etc. Proper penetration tests, keeping in mind the needs of the system, client, and overall security.
What Are The Steps Involved In Network Penetration Assessments?
Step 1: Reconnaissance
Network penetration testing experts deploy the reconnaissance strategy by taking on the disguise of hackers and analyzing the system to find any potential weaknesses.
- The technical aspect – Expert looks for weaknesses in network ports, peripherals, and any other associated software that could allow hackers to break into the system. Vulnerability assessments become highly useful here, providing an outlook on other issues of the same nature within the system.
- The social aspect – Social engineering loopholes are the typical phishing scams, stealing of login credentials, etc. These kinds of tests could be used to increase employees’ awareness to avoid these scams and gain information about the general security of the entire system.
Step 2: Discovery
In the discovery phase, pentesters use the data from the reconnaissance to run live tests with pre-coded or customized code scripts to identify vulnerabilities. Usually, one script discovers one issue at a time, so multiple scripts may be required for the completion of the entire process. Technical errors like SQL injections and human errors such as divulging sensitive data are given the same weightage.
Step 3: Exploitation
Here, pentesters leverage the discovered information such as possible vulnerabilities and entry points, to test the discovered exploits in your network devices or IT systems. The goal of the exploitation phase is to break into the network environment, avoid detection and identify entry points using a different set of online pentesting tools available.
How Does One Conduct Network Penetration Testing?
Every system has unique requirements, and hence, the below-mentioned tests can be used individually, or in combination.
1. Black Box
A ‘black box’ test is conducted without any prior knowledge of how the network functions or any of its technical characteristics. The test functions by comprehensively exploring the given network to conduct a targeted attack. It is the most realistic attack simulation and is preferred by businesses that deal with sensitive data and want to secure their systems from exploitation. Examples of black-box testing tools include Selenium, Applitools, Microsoft Coded UI, etc.
2. Gray box
The function of a ‘gray box’ test remains between that of black and white. This includes simulated attacks to understand issues that an average system could face such as theft of internal information like login credentials, user privileges, and technical documents, etc.
Highly focused attacks are framed to understand the direction of attack by an average hacker, making them one of the most common network pentests. Some common gray box testing tools are Postman, Burp Suite, JUnit, NUnit, etc.
3. White box
Network professionals collect all possible data about the system, and its possible flaws, and target the specified infrastructure to evoke a response. If black is realistic and gray is moderately intrusive, the ‘white box’ test is like an audit and checks the aftermath of increased security.
This is the version of a final run-through. Businesses usually use it to ensure that the system is impenetrable to the most hardcore hacker, making it the longest in planning but the most important. The top performers in white box testing tools include Veracode, GoogleTest, CPPUnit, RCUNIT, etc.
The most important aspect of a successful network penetration test online is to identify the client’s needs from their systems and plan accordingly while recognizing potential threats. Once the website penetration testing report is provided with recommendations a network pentest fulfills its true purpose.
Tools to conduct Network Penetration Testing:
Here are a few network penetration testing tools you can use to conduct pentesting for your network systems:
- Nessus – vulnerability scanning tool used for vulnerability assessment (VA) process
- Nmap – network discovery and security auditing tool
- NetCat – port scanning and listening tool used to read and write in a network
- Hydra – pentesting tool used for brute-forcing login and obtaining unauthorized access
- Wireshark – packet sniffing and analysis tool used for monitoring network traffic and its behavior
- Nikto – vulnerability scanning tool used for scanning web-servers for security weaknesses
- Metasploit – pentesting tool used for probing vulnerabilities in networks and servers.
- PRET – pentesting toil for checking printer security controls
- Burpsuite – vulnerability assessment and pentesting tool used for discovering vulnerabilities in web apps
At Astra Security, penetration tests are done by certified security professionals who test your network for more than 3000 tests — both automated and manual. Other characteristics of Astra Security’s network penetration testing include:
- Collaborative dashboard and real-time vulnerability reporting
- Detailed reports (with PDF, PoC, selenium scripts)
- Recommendations and quick tips on patching up vulnerabilities
- Security tests for firewalls, routers, switches, wifi, servers, biometrics, UPS, SAN, etc.
- VAPT certificate after completion of the security audit
Here’s what the penetration testing process at Astra looks like:
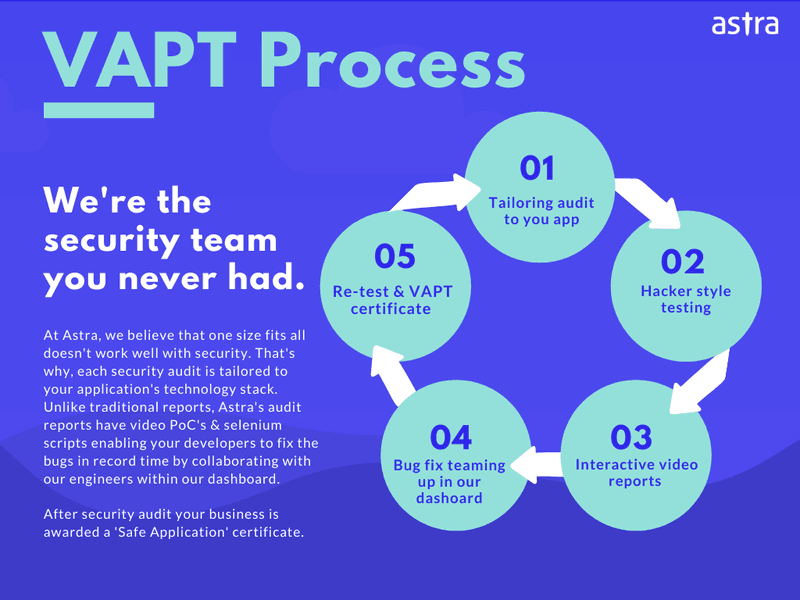
Want to know more about our network penetration testing services? Feel free to talk to us here.
FAQs
What are network penetration assessments?
Network penetration assessments refer to the authorized exploitive testing of identified vulnerabilities in network infrastructures to understand their complete impact on the network’s security.
What are the different network pentesting techniques?
The various network pentesting techniques followed include:
1. External Pentesting: Here external facing web assets (website, emails, DNS) of the company are tested for vulnerabilities to exploit.
2. Internal Testing: Tester has firewall access and simulates the activities of a malicious insider (rogue employee or credential theft).
3. Double Blind Testing: Here, security personnel have no intimation of an attack simulation and as such won’t have time to shore up defenses.
What are some well-known open-source network pentesting tools?
Top open-source network pentesting include Nmap, and Wireshark. Other tools that are commercial include Astra Pentest, Metasploit and Nessus.

















Which network controls would you suggest for an organization’s network security?
Hey Violet, for an organization’s network security, network controls like multifactor authentication, data encryption, role-based access control, regular patch updates, and continuous VAPT testing is suggested. Read more details in our article – best practices for network security.
What is the difference between internal pen testing and external pen testing?
Internal pen testing is the process of assessing one’s security system for loopholes with an in-house security team for the purpose of creating a network baseline. It also determines whether these vulnerabilities can be used to achieve initial access.
External pen testing on the other hand is done by an outside pentest provider and is crucial to meet compliance requirements. It provides a thorough hacker-style examination of one’s security thus finding all vulnerabilities that might escape an internally conducted pentest. Hope this clears it up for you.
What information is required to scope a network penetration test?
Hey Amelia, the information required to scope a network penetration test is as follows:
1. Needs of the customer- All assets to be tested or new features alone, type of tests required, and how far to exploit.
2. Time- The timeframe by which the test needs to be done, and the timings when the exploit can be conducted should be informed prior.
3. Compliances Required- Compliance like ISO 27001 or SOC2 focuses on different areas and so the scope for each will differ.
4. Number of assets- The number of services and IP addresses to be tested is predetermined.