With businesses onboarding the Go Digital campaign, cybersecurity has become a critical aspect of most boardroom discussions. In fact, a recent report by Statista placed the total cybercrime damages in 2022 at a staggering $10.3 billion.
This is where online penetration testing tools take the spotlight in cybersecurity. Today, we hope to guide you through the significance, advantages, and available vendors, offering you a bird’s eye view of how online pentests can effectively fortify your data and safeguard your business.
Best Online Penetration Testing Tools in 2024
Top 8 Online Pentest Tools To Know [Reviewed]
Here are some of the top online penetration test tools to know to make the right choice for your security needs.
1. Astra Pentest
Astra is a leading provider of penetration testing services that assures zero false positive report generation through a comprehensive scan that is capable of running more than 8000 tests. The reports are vetted by expert pentesters who also provide remediation assistance. The website penetration testing tool is capable of testing for compliances like GDPR, HIPAA, PCI-DSS, and ISO 27001.
Besides website pen testing, Astra also provides penetration testing services for firewalls, networks, cloud environments, mobile apps and APIs.
Over the past year, Astra has added names like ICICI, UN, and Dream 11, to their already impressive roster of clients which included Ford, Gillette, and GoDaddy, among others.
Features:
- Scanner Capacity: Unlimited continuous scans
- Manual pentest: Available for web app, mobile app, APIs, and cloud infrastructures
- Accuracy: Zero false positives
- Vulnerability management: Offers a dynamic vulnerability management dashboard
- Compliance: Helps you stay compliant with PCI-DSS, HIPAA, ISO27001, and SOC2
- Price: Starting at $199/month & $1,999/year
Who is it for?
SaaS providers, ECommerce website owners, and public offices, across regions and industries.
Pros
- Provides gap analysis.
- Rescanning is a must after remediation.
- Provides publicly verifiable certificate.
- Ensures zero false positives.
- Detects business logic errors and scans behind the logins.
Cons
- Could have had more integrations.
- Does not provide free trials.
2. Nessus

Nessus is a standard firewall test tool, known for its vulnerability assessments and constant updates which ensure holistic protection and detection of vulnerabilities. It has a free version but this is a bit lacking in features when compared to its commercial product.
Features:
- Scanner capacity: Web applications
- Manual pentest: No
- Accuracy: False positives are possible
- Vulnerability management: Yes (Additional Cost)
- Compliance: HIPAA, ISO, NIST, PCI-DSS
- Price: Starting from $4,236.20 per year
Who is it for?
Cybersecurity professionals, and security teams of enterprises.
Pros
- Quick asset discovery.
- Reduces attack surface and ensures compliance
- Malware detection and sensitive data discovery are also carried out by this tool.
Cons
- Expert remediation is only available at an additional cost.
- Cannot handle large volumes of data while scanning.
3. W3af
W3af is a free online penetration testing framework that enhances any pentesting tool through its guidelines. It is capable of identifying nearly 200 various kinds of flaws within various web applications.
Features:
- Scanner capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possibles
- Vulnerability management: No
- Compliance: No
- Price: Open-source
Who is it for?
Beginners to ethical hacking, and other small to medium-sized organizations.
Pros
- Allows brute-forcing and auditing.
- Can carry out SQL injections and file inclusions
- Comes with a graphical user interface.
Cons
- False positives can occur.
- GUI can be difficult to navigate.
4. Zed Attack Proxy
ZAP is one of the best online pentesting tools available that is open-source and provided by OWASP. It can be used for Linux, Microsoft, and Mac systems to run penetration tests on web apps to detect a variety of flaws.
Features:
- Scanner Capacity: Web application security testing, network ports, and API testing
- Manual pentest: Yes (Used by experts to carry it out)
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: OWASP
- Price: Open-source
Who is it for?
Ethical hackers, cybersecurity professionals
Pros
- Sends automated alerts after crawls and scans
- Perfect for beginners and experts alike.
- Free online penetration testing tool.
Cons
- Can be slow.
- Reports can be cluttered and long.
5. Burp Suite
Burp Suite is a penetration testing tool provided by Port Swigger that provides a variety of services that is essential for any penetration tester. Some of the tools include Spider, Proxy, Repeater Intruder, and more.
It has a free version called the community edition as well as an advanced commercial solution, Professional Edition.
Features:
- Scanner capacity: Web applications
- Manual pentest: Yes
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: PCI-DSS, OWASP Top 10, HIPAA, GDPR
- Price: $449/per user/per year onwards
Who is it for?
Beginners, professional ethical hackers, and also security professionals.
Pros
- Provides advanced automated online pentest.
- Provides step-by-step advice for every vulnerability found.
- Can crawl through complex targets with ease based on URLs and content.
Cons
- Advanced solutions are commercialized and can be expensive.
- Does not provide vetted online pentesting and scanning reports
6. Probely
Probely is one of the leading online penetration testing tools designed for web application scanning and API scanning. It offers partial and incremental scans that automatically prioritize vulnerabilities based on risk and provide proof of legitimacy for each issue.
Features:
- Scanner capacity: Web applications and APIs
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: Yes, patch management and zero-day mitigation are available
- Compliance: PCI-DSS, ISO27001, HIPAA, GDPR
- Price: Free basic plan with professional plans starting at $1,198 / year
Who is it for?
Developers, security teams, and DevOps.
Pros
- Detailed management reports to assist compliance audits
- Interactive dashboard
- Scalable application scanning
Cons
- Limited functionality for detecting vulnerabilities
- Custom vulnerability scoring does not align with general scoring.
7. Intruder
Intruder is an elite online penetration testing software and vulnerability scanner for cost-effective data protection. It ensures continuous monitoring, compliance reporting, and attack surface scanning, with effortless scaling capabilities for businesses of all sizes and industries.
Features:
- Scanner capacity: Websites, servers, and cloud.
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: SOC 2 & ISO 27001/27002
- Price: Essential Plans starting at $1,215 per target/year
Who is it for?
Developers, cybersecurity teams, and DevOps.
Pros
- Offers thorough security assessments
- Automated scans ensure real-time alerts for exposed ports
- Vulnerability risk assessment and prioritization
Cons
- No publicly verifiable certificates
- Lacks assurance of zero false positives
8. Acunetix
Acunetix is a vulnerability scanner that offers effective website penetration testing services online. It promises 90% scan results even halfway through and works on different setups to help you focus on the most important issues.
Features:
- Scanner capacity: Web applications
- Manual pentest: No
- Accuracy: False positives possible
- Vulnerability management: No
- Compliance: OWASP, ISO 27001, PCI-DSS, NIST
- Price: Custom quotes
Who is it for?
Developers and security professionals
Pros
- Reduces false positives with proof of exploit
- Automates regular scans
- Agile testing with detailed reports
Cons
- Lack of transparency with no official pricing plans
- Fails to provide expert remediation assistance with professionals.
What is online penetration testing?
Online penetration testing is a proactive cybersecurity practice that aims to identify vulnerabilities and weaknesses in a computer system, network, application, or infrastructure. Think of it like your digital security guardian. It operates remotely to scrutinize your system’s defenses, by stimulating real cyber intrusions, all conducted via the internet.
Unlike traditional pen testing, which often requires physical access to premises, its online counteragent can span the globe, adapting seamlessly to the dynamic cybersecurity landscape. Its focus is exclusively on safeguarding your digital assets, maximizing efficiency, and providing a lifelike rehearsal for potential cyber threats, all while keeping your budget in check.
7 benefits of using online penetration testing tools
1. Leverage automated security scans
In the fast-paced DevOps environment, security often takes the back seat due to the focus on releasing new features and functional updates. By automating security scans through online penetration testing tools, you can ensure the security of all major updates before they are released.
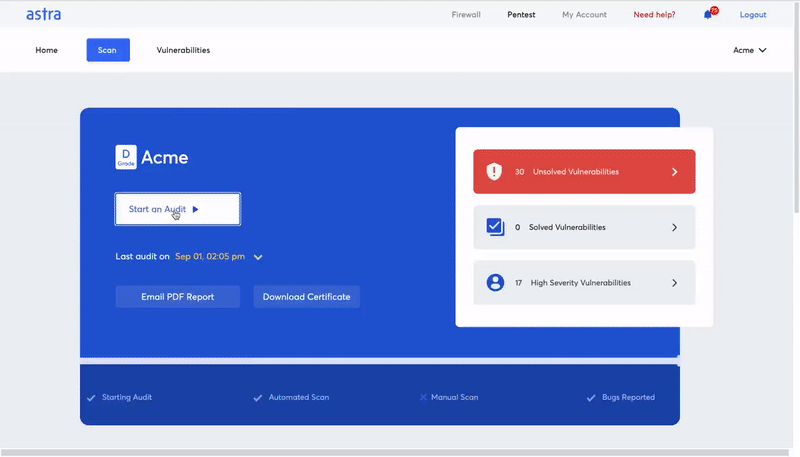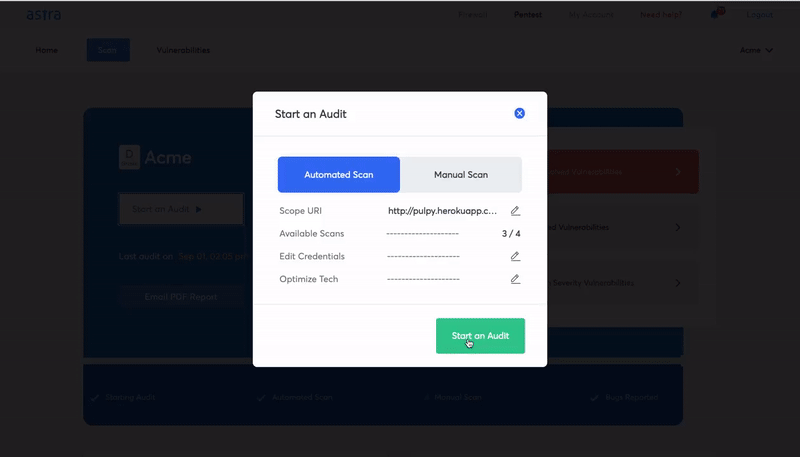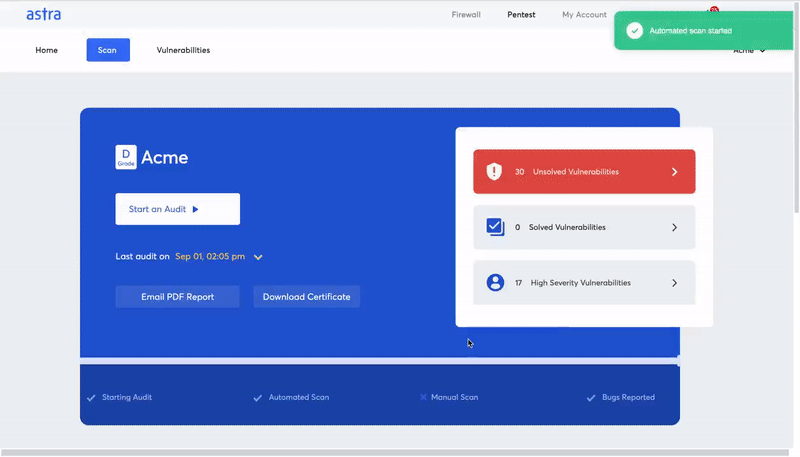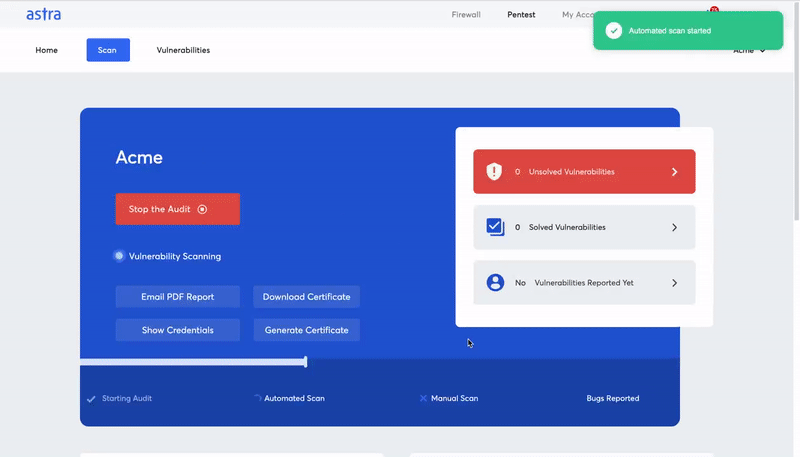
2. Carry regular online pentesting
Regular pentesting is crucial for maintaining strong security. Inconsistent online tests may have several drawbacks:
- Vulnerabilities can slip through between scans conducted months apart
- Your website or application can be subjected to various attacks such as SQLi, cross-site scripting, etc.
- With infrequent online web pentesting, the pressure of remediation can be overwhelming.
3. Monitor and manage vulnerabilities seamlessly
Pentest reports are valuable for risk management and fixing security issues. However, they don’t have the same impact as a dynamic dashboard. A dashboard with graphical representations of vulnerability data allows for better management of their status and the remediation process.
Online penetration test platforms like Astra come with interactive dashboards that make vulnerability scanning and management much easier while also helping you with the remediation process.
4. Get continuous feedback for developers
If you opt for an online pentest tool that can be integrated with your company’s CI/CD pipeline, it can send your developers feedback in terms of the security stature of a certain code update.
It helps you foster a DevSecOps environment where security testing is an integral part of the software development minimizing the gap between the discovery and remediation of a vulnerability.
5. Enhance customer confidence
Security is slowly but surely becoming one of the key factors that influence the choice of vendors among business owners. When you are continuously secured by both defensive and offensive security measures, it inspires trust among the clients.
Integrating security with your regular business functions shows your approach towards the security of your client’s data and their privacy.
6. Facilitate speedy remediations
Online penetration tests are easy, inexpensive, and quick. Thus, allowing you to allocate the resources for prompt remediation of the issues discovered. Some pentest providers such as Astra, offer the option to build collaborative channels between security engineers and your developers to facilitate such patches. This also prevents vulnerabilities from piling up.
7. Compliance readiness
With paperwork, reporting, and minute assessment of security protocols, compliance audits are worrisome events that send cold anxious winds across an enterprise.
A regular online pentest program can reduce this anxiety by identifying vulnerabilities, giving the development team time to address them, and thus improving the company’s attitude and confidence towards audits.
Features you should look for in your Online Pentest Tool
1. Integrates with your CI/CD pipeline:
Your firewall penetration test tool should easily integrate with your CI/CD pipeline so as to enable you to schedule and automate continuous scans with ease.
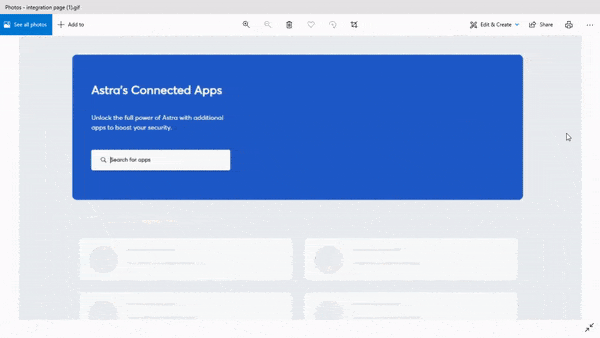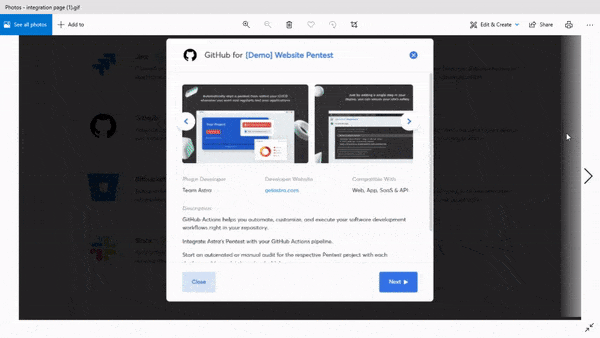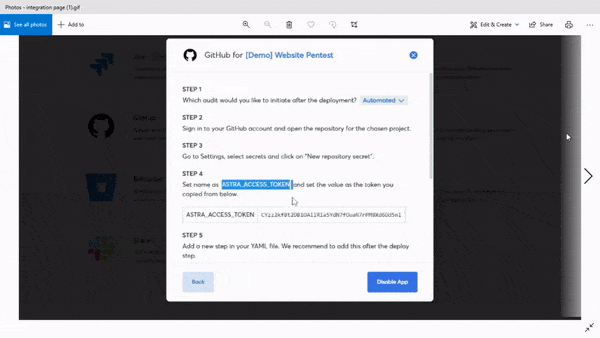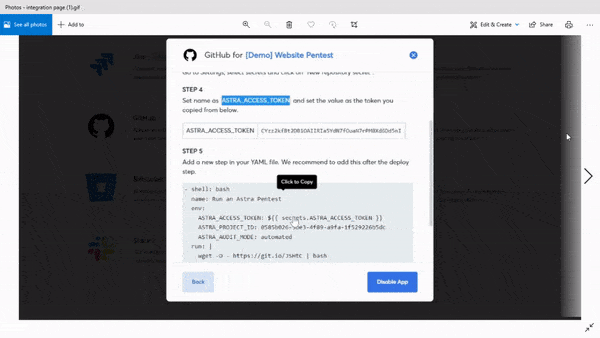
2. Scan behind log-in:
In order to get the full value of external pentesting, you need authenticated scans where the scanner scans seamlessly behind the logged-in pages.
The only problem, once a session runs out, you need to manually re-authenticate the scanner. This issue is tackled by Astra’s login recorder – it uses your credentials once and keeps the scanner running.
3. Optimize for single-page apps:
Your pentest tool should be optimizable for single-page apps and different frameworks, thus increasing efficiency and effectiveness.
4. Offers contextual collaboration:
It helps your developers collaborate easily with security experts by referring to shared resources. This speeds up the remediation process manifold.
What is the process of online pentesting?
The exact process of free and paid online penetration testing can differ quite a bit depending on the provider and the target organization.
A lot of the intricate work around the pentest is performed by the pentest provider with little or no involvement from you, so we will focus on the parts of the process that actually concern you.
Step 1: Determine the scope of the pentest
The first step for you in conducting an online website penetration test is getting on a call with the pentest providers and determining the scope of the pentest. This is the most important step for you since this is where you need to point at asset types that you want to be tested and the ones you want to be left alone.
Step 2: Provide all the necessary information
You share your website or app’s URL for an external scan and authenticate the scanner by providing the information required to run scans behind the logged-in pages.
Scanning behind the login is a prized feature offered by only a handful of pentest providers, and it is something you should definitely look for.
Step 3: Monitor and analyse vulnerabilities
Monitor the vulnerabilities reported in your pentest dashboard. Refer to the pentest report to understand the risk associated with each vulnerability and prioritize the high-risk ones.
Step 4: Remediate the vulnerabilities
Your team of developers should work on the remediation with the assistance of the pentest provider.
Step 5: Re-scan the vulnerabilities
Once the vulnerabilities are taken care of, you can claim your free re-scans to ensure that the issues no longer exist.
Step 6: Integrate the online pentest tool with SDLC
You should integrate your pentest tool with your SDLC (Software Development Lifecycle) to get constant security feedback.
How to secure your business with Astra’s Security Suite?
When it comes to online penetration testing software, Astra security is an unbeatable solution. Astra combines automated vulnerability scanning with pentest led by expert security engineers to create the most comprehensive and the most actionable penetration testing experience.
Astra takes everything offered by its competitors, adds some bonus features, and makes them easier to access. Let us look at some features that make Astra’s pentest platform stand out.
DevSecOps
Astra’s pentest platform helps you achieve DevSecOps through CI/CD integration and contextual collaboration.
Regularly updated scanner rules
Astra’s security engineers update the vulnerability scanner every week. That’s more often than any of its competitors. It is important because it keeps you abreast of the cyber threat landscape.
Compliance-specific scans
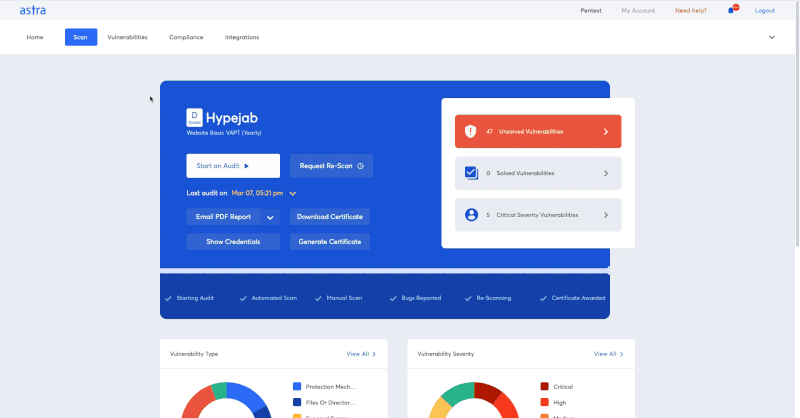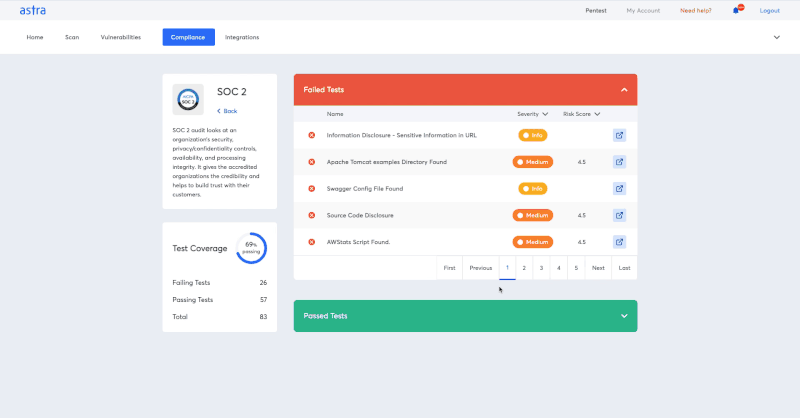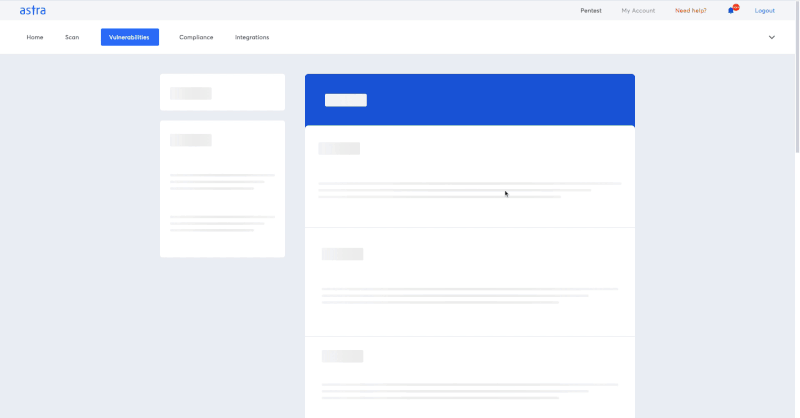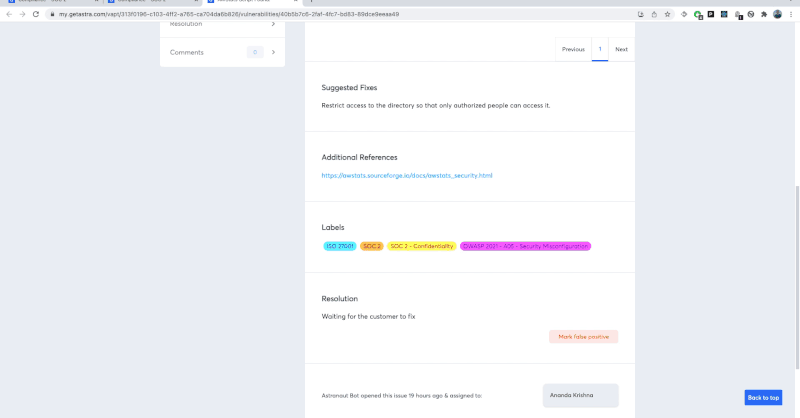
You can use Astra’s pentest dashboard to view the specific compliance regulations that are violated by a certain vulnerability. Thus you can prioritize the remediation of such vulnerabilities.
Scan behind logged-in pages with the login recorder
Share some information to authenticate the scanner once (it takes a few minutes – we’ve added a video to help you with it) and you are done. No need to re-authenticate the scanner every time the session runs out.
Publicly verifiable pentest certificate
Once you have remediated all the vulnerabilities and received the evidence for the same in the free re-scans, Astra offers you a publicly verifiable pentest certificate. It gives you bragging rights – it could make a real difference when your clients try to verify you as a vendor.
On top of all of these Astra maintains an impeccable record of customer assistance, they keep you updated about the cyber security landscape and offer you a number of integrations to strengthen your security with minimum alterations in your regular workflow.
As technology gets better, online risks get worse. Thus, for your business to go digital and remain secure, employing an effective online pentesting tool is a must. Using online pentests makes sure your digital walls stay strong, which helps your clients trust you. It’s like building a strong safety culture into how you work. Going forward, you need to stay watchful, be ready to change, and stay vigilant. And in case you need any further assistance, our team at Astra is always here to light the path!
FAQs
What is the timeline for a comprehensive pentest?
It usually takes somewhere between 4-7 days to complete an in-depth pentest procedure, especially if you are hiring a professional for the same. The re-scans after remediation usually require half as much time, thus 2-3 days for the follow-up scans usually suffice.
What is the cost of online pentesting?
The cost of penetration testing online usually varies between $100 and $5000 per month. Although, the variation in pricing is the result of a variety of facts such as the size of an organization, scope of work, etc. Some select tools also offer free online penetration testing, but the scope, features and customizations are often limited in the same.
What makes Astra the best provider of penetration test online?
The Astra pentesting software is a perfect combination of automated and vetted online testing, giving your business the best of both worlds. It also has a proven track record of zero false positives, competitive pricing, publicly verifiable certificates, integration with the CI/CD pipeline, and so on.
![Top 8 Online Penetration Testing Tools in 2024 [Free and Paid]](https://cdn-blog.getastra.com/2022/08/Featured-Images-32.png)















