Statistics reveal that 77% of companies are woefully ill-prepared and planned when it comes to thwarting an attack or a data breach. Such staggering statistics reveal the state of security in organizations, it is important to ensure that any attack surfaces presented by your organization in cyberspace are protected. One such attack surface is your company’s website.
Websites often have vulnerabilities such as XSS, and SQL injections that can be exploited for malicious intent. It is therefore important to carry out routine checks on your website’s security. This can be done through website penetration tests or vulnerability scans. Further in this article, we will go deeper into website penetration testing and take a closer look at the complete methodology involved in Website Penetration Testing (tools + checklist).
What Is Website Penetration Testing?
Website penetration testing is a simulated hacker-style attack on a website aimed at identifying and gauging the gravity of existing vulnerabilities to protect the website from malicious attacks. It focuses more on how each of these vulnerabilities could be exploited.
Website penetration testing service uses the findings (the list of vulnerabilities) of vulnerability assessment and exploit them to work out the degree of risk attached to it. It is akin to checking the strength or any weaknesses of your windows or doors.
Basically, vulnerability assessment is an initial step in the whole process. Whereas, Online Website Security Testing or pentesting Vulnerability assessment can use both automated & manual scans. Whereas, penetration testing is generally a manual process done by experienced security engineers.
Why Do You Need Website Penetration Testing?
It is crucial to identify your site’s security loopholes so that you are never caught off guard. Website penetration testing lets you know the possible mishaps that could take place through the exploitation of vulnerabilities such as SQL injections, and cross-site scripting. This invariably contributes to better risk management for your website.
I have seen website owners often ask things like, “Mine is just a small website, do I need a Website Penetration Testing?“. The answer is yes. Research has it that nearly 60% of cyberattacks target small businesses. So, there’s a good chance of your website being targeted, if left untended.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

In a nutshell, online penetration testing can help you in the following ways:
- To identify and fix security flaws in your website.
- It gives you a holistic view of misconfigured integrations implemented within a site.
- Penetration testing emulates real-life attack scenarios and helps in mitigating risks.
- It can help you in achieving certain compliance requirements such as GDPR, ISO 27001, PCI-DSS, HIPAA, and more.
- It enables you to uncover potential vulnerabilities in your site.
- It can save you from legal consequences and hefty penalties under data security policies.
- It helps in preparing your security team to cope with a real-life cyber attack.
Also Read: Continuous Penetration Testing: The Best Tool You’ll Find in 2022
Benefits of Conducting Website Penetration Testing
1. Detection of vulnerabilities
Website penetration testing can help in the detection and identification of vulnerabilities hidden within the website be it any CVEs, logic errors, or payment issues. This helps in the quick remediation of any critical vulnerabilities that may be affecting your website security.
2. Enhances your website security
A bonus that comes from conducting a website pentest is the enhanced security it offers your website on top of the measures already implemented to protect it. The efficacy of these security measures can be tested to ensure that any required improvements are made in time and any potential risks are thwarted.
3. Aids in achieving compliance
Through the detection of vulnerabilities and enhancement of your security measures. Website pentests also, directly and indirectly, help with maintaining compliance. Many regulatory standards such as PCI-DSS, HIPAA, ISO 27001, and others either mandate or recommend a penetration test to be carried out without which, you would be liable to pay hefty non-compliance fines.
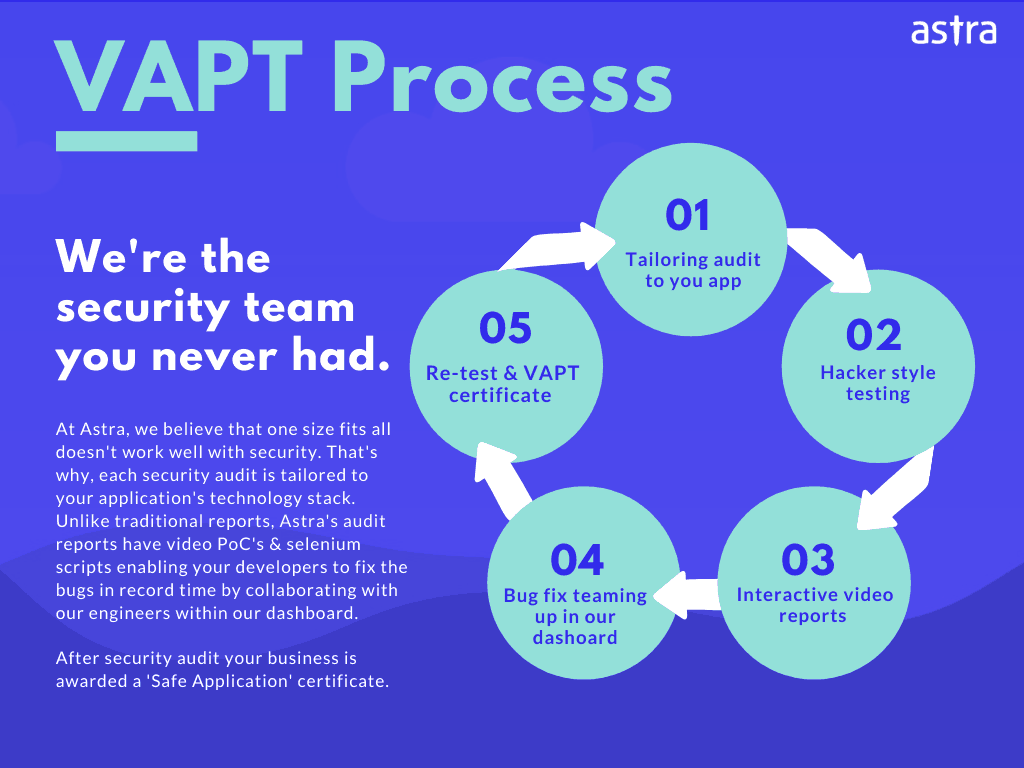
Methodology for Website Penetration Testing (Tools Included)
Web services pentest is done primarily in 3 phases:
- Information Gathering: In information gathering, the pentester tries to find fingerprints in the backend of the website. It usually includes Server OS, CMS version, etc.
- Discovery: The second step is where automatic tools are deployed to uncover any known security flaws or CVEs in the respective services. Here, a manual security scan by engineers is also required in order to discover business logic vulnerabilities because these kinds of flaws are often missed by the scan made with automated tools.
- Exploitation: In the final step of exploitation, the goal is to leverage any vulnerabilities discovered in the second phase. This is often done manually to weed out false positives. The exploitation part is also used to exfiltrate information from the target and to maintain persistence.
1. Information Gathering
The first phase is information gathering in which, the pentester tries to find fingerprint the backend services of the website i.e. Server OS, CMS version, etc.
Here is a list of tools you can use in the information-gathering phase:
- Network Mapper a.k.a. NMAP: The well-known recon tool helps discover open ports, and scan targets by bypassing the firewalls. Also, users can try Zenmap which is the GUI version of Nmap.
- Harvester: This tool collects Open Source Intelligence (OSINT). OSINT is the information present in the public domain regarding your target i.e. Whois registration info, company emails, etc.
2. Discovery
The second step is Discovery in which automatic tools are deployed to uncover any known flaws or known CVEs in the respective services. Some tools that can help with the discovery of vulnerabilities include:
- Astra Vulnerability Scanner: This constantly evolving scanner can test for more than 8000 vulnerabilities, and CVEs. The automated scanning tool comes with an intuitive dashboard that displays detected vulnerabilities in real-time.
- Nikto: Nikto is a tool specifically designed to scan vulnerabilities in around 270 types of servers. It can extensively search for 6700 server misconfiguration.
- Burp Suite: This is a website pentesting framework built on java. It has a built-in proxy that intercepts traffic between your browser and the website pentesting target. This proxy can be then used to manipulate requests or for fuzzing to discover vulnerabilities in a website.
3. Exploitation
The vulnerabilities discovered using automated vulnerability scanning tools are carefully exploited by certified pentesters or using automated pentesting tools.
Some tools that can help with the exploitation of vulnerabilities are:
- Astra Security: Astra provides the perfect blend of automated vulnerability scanning and manual penetration testing with expert-certified pentesters. This tool not only has 8000+ test cases but can also generate AI-test cases specific to your business to detect logic errors, payments gateways issues and more.
- Metasploit: This is an industry-standard when it comes to the exploitation of the target. If you find any vulnerabilities, there are a plethora of exploits to choose from. Finally, pair your exploit with a suitable payload and you are good to go.
- SQLMAP: Sqlmap is a one-stop solution to find any SQL injection vulnerabilities on your website and exploit them. Sqlmap can fuzz the target parameters in the URL and even data fields on the page to find any SQL injection points.
Website Penetration Testing Checklist
Information Gathering
- Port Scanning
- Web Server, CMS Version, and OS fingerprinting.
- HTTP Methods
- Cookie Attributes
Discovery
- Finding alternative content i.e. directory/files brute force.
- Finding default configurations or misconfigurations.
- Login Fuzzing.
- Testing Session Tokens.
- Injections: SQL, XSS, XML, Template, OS Command.
- Open Redirection.
- LFI & RFI attacks.
- Business Logic Flaws.
- Denial of Service.
- Testing REST and SOAP web services.
Encryption Flaws
- Heartbleed
- Poodle
- HTTPS strip
- Oracle Padding Attack
- Weak Cryptography or Poor implementation
Exploitation
- Browser hijacking using XSS.
- Data Exfiltration using various injections.
- Authentication Bypass.
- Offline password cracking.
- Cross-Site Request Forgery.

Final Thoughts on Website Pen Testing
Website penetration testing is important for everyone operating online, be its small blogs or large corporations. Moreover, there are plenty of tools available freely to conduct online penetration testing. The steps of a web pen test information gathering, discovery & exploitation guide and organizes the whole process.
So get started today and test the security of your website with wholesome tools like Astra Security. Our community of experienced security experts will pentest your website and report any vulnerabilities in a detailed and easy-to-understand manner. They will also provide you with the fixation steps and even promise to help you or your developer in patching it.
FAQs
How much does website penetration testing cost?
Website penetration testing costs between $349 and $1499 per scan depending on the number of scans and the plan you are on. Check out Astra’s pricing.
What is the timeline for Website Penetration Testing?
The timeline for website Pentesting is 7-10 days. You start seeing the vulnerabilities from the 3rd day on your dashboard. The timeline may differ a little depending upon the scope of the test.
Why choose Astra Pentest?
1250+ tests, adherence to global security standards, an intuitive dashboard with dynamic visualization of vulnerabilities and their severity, security audit with simultaneous remediation assistance, and multiple rescans, are the features that give Astra an edge over all competitors. Check Astra’s Pentest features here.
Mine is just a small website, do I need a Vulnerability Assessment & Website Penetration Testing?
Yes. Research has it that nearly 60% of cyberattacks target small businesses. So, there’s a good chance of your website being targeted, if left untended.

















Thanks for explaining the things. There are many-things which clears my doubt regarding penetration testing.
Thank you, Amit
This is really a nice and informative article.
wonderful writeup in a common man language. Thnak you for not bombing jargons!
Are website penetration testing and online pentesting the same?
Hey Aisley, website penetration testing and online penetration testing are interchangeable terms referring to the penetration testing done to find vulnerabilities within a website before any harm or breach occurs, hope this helps you.
Why should we use online pentesting platforms?
Hey Jessica, opting for online penetration testing platforms helps ensure the security of a system through the identification of vulnerabilities and their subsequent exploitation to understand the extent of possible damage. This can help in placing appropriate security patches to ensure that the system stays safe from any malicious attacks.