In a DevOps environment, annual penetration tests do not cut it. The constant evolution of the cyber threat landscape coupled with the regular code updates on your software application necessitates a more consistent security testing solution. That’s where continuous penetration testing comes in.
Imagine a pentest tool that is integrated with your CI/CD pipeline and starts a scan whenever you push new code or launch an update. This is the future of security testing, and you need to embrace it today.
What is Continuous Penetration Testing?
Continuous penetration testing is the process of consistent monitoring of software assets along with periodic vulnerability scans. As opposed to traditional pentesting which takes place once or twice a year, continuous pentesting approaches security testing with more immediacy.
It combines constant monitoring with demand-based testing to offer continuous visibility of an organization’s security posture.
It works wonders in the DevOps environment where new code is pushed regularly, cloud instances are built in a flash, and regular experiments are done with user experience.
How Does Continuous Pentesting Solution Work?
Continuous automated penetration tests are comprised of a few key components:
- A vulnerability scanner that automatically scans for vulnerabilities in the code
- A continuous monitoring system to keep track of new assets and changes in the environment
- Integration with the CI/CD pipeline to launch new scans whenever there are code updates
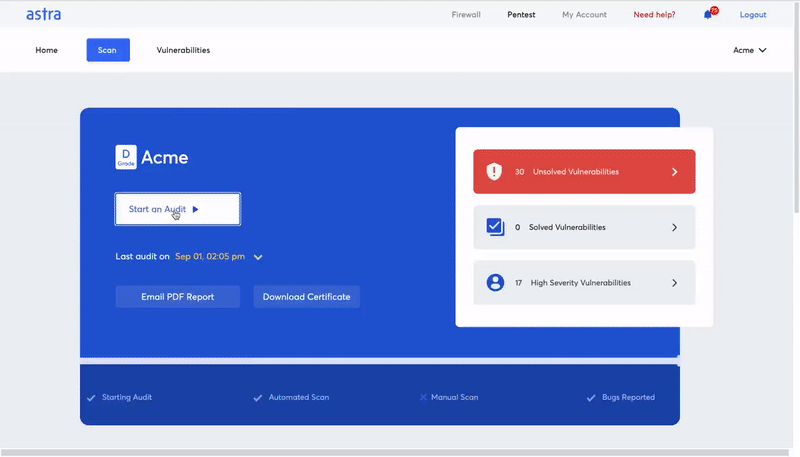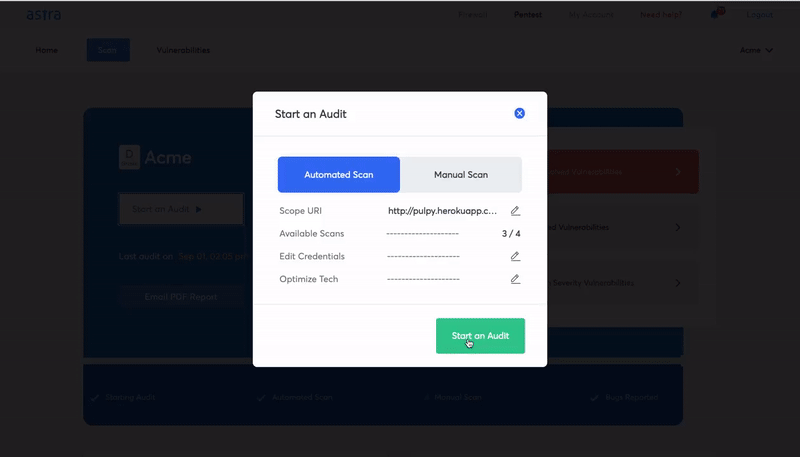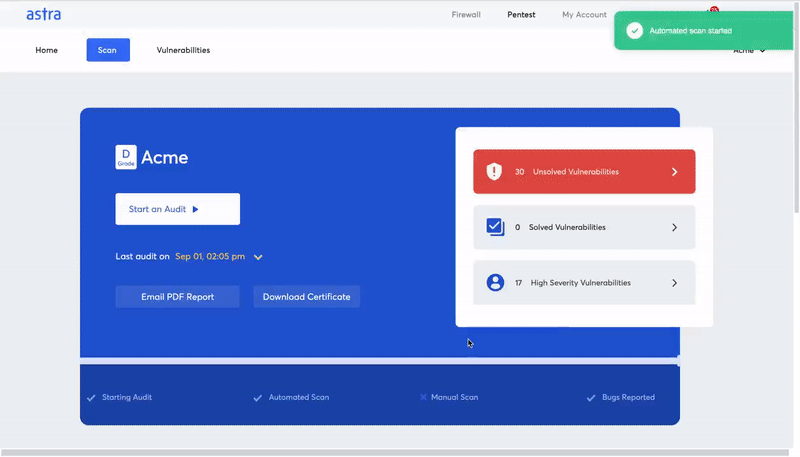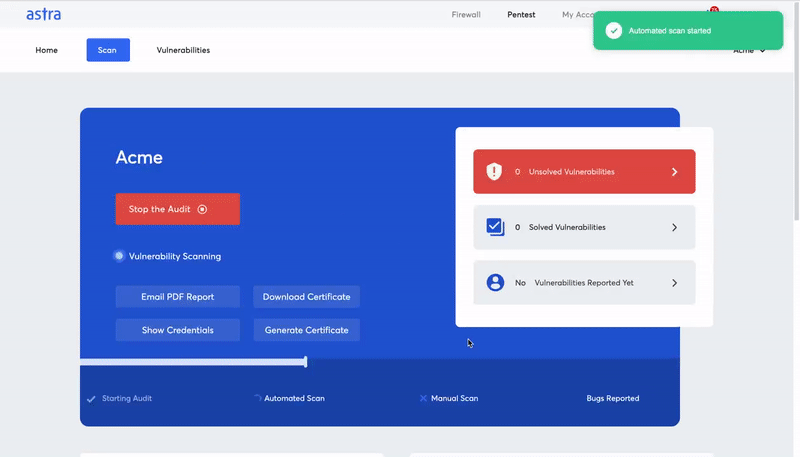
Once you have integrated the pentest tool with your CI/CD pipeline, it should work on its own based on an initial baseline pentest. You should be able to schedule the tests, automate the entire process, and relax.
3 things that make continuous penetration testing necessary
The need for continuous penetration testing by third-party arises from the following three factors:
1. The ever-changing cyber threat landscape
New threats emerge daily and old ones mutate. Continuous security testing allows you to keep up with the latest attacks and defend your systems better.
If you think about it, with annual pentesting, you live in a blind spot between two consecutive tests. A lot can happen in that period of time, especially if you are making changes from your end.
2. The regular updates to your codebase
With new code being pushed constantly, there is always a chance for vulnerabilities to slip through the cracks. Continuous pentesting can help you identify these issues before they cause problems.
3. The need for continuous feedback
In a DevOps environment, it is important to get feedback early and often. Continuous pen testing can help you do just that by providing regular reports on the state of your security posture.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

How can an organization benefit from continuous pen-testing?

There are many benefits of continuous pentesting, some of which are listed below:
It helps you stay ahead of the curve: Continuous pentesting allows you to keep up with the latest attacks and defend your systems better.
It helps you find vulnerabilities early: By identifying vulnerabilities early, you can prevent them from causing problems later on.
It helps you get continuous feedback: Continuous pentesting provides regular reports on the state of your security posture. This can help you identify areas that need improvement.
It helps you automate the process: Continuous pentesting allows you to automate the entire process, from scheduling tests to generating reports.
What are the key features needed for continuous pentesting?
The key features needed for continuous pentesting
A vulnerability scanner can automatically scan for vulnerabilities in the code.
A continuous monitoring system keeps track of new assets and environmental changes.
Integration with the CI/CD pipeline to launch new scans whenever there are code updates.
Astra’s continuous penetration testing platform
Astra security has taken the concept of continuous penetration testing and given it the perfect manifestation in the Astra Pentest Platform. It is carefully designed to lift your security testing experience from the present and gently place it in the future.
First, they create a vulnerability scanning dashboard that allows you to monitor, manage, assign, and update vulnerabilities from the same place. They also let you collaborate with security experts from the same dashboard.
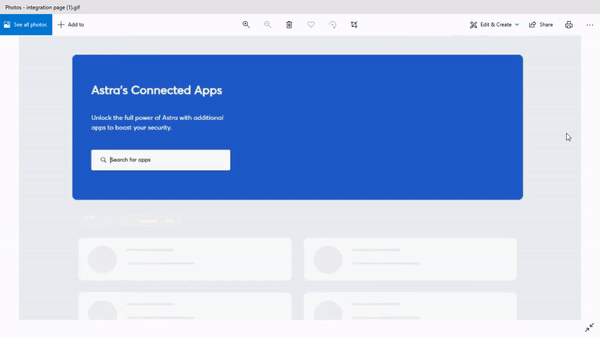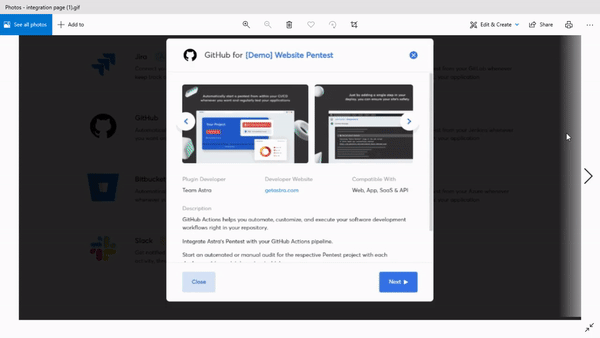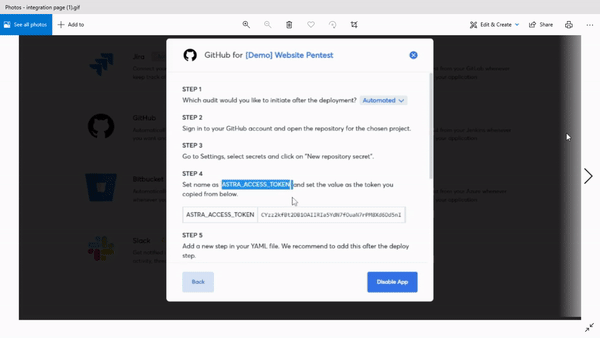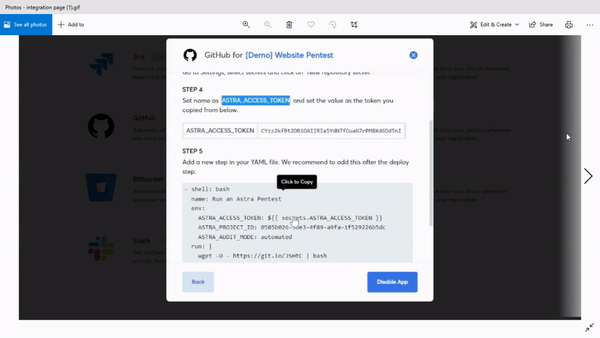
Second, they launch a bunch of integrations that tie the pentest tool with your CI/CD pipeline and other workflow management tools like Slack and Jira. This makes things even easier for you since you no longer need to visit the dashboard to start a scan.
Whenever you push new code, Astra scans it for critical vulnerabilities making it virtually improbable to launch a vulnerable software version. There is continuous monitoring and scheduled scanning on top of all this.
From scoping the pentest to helping you with remediation, Astra’s continuous pentest platform brings the whole thing down to a few clicks. The following are some features that put Astra right at the top when it comes to pentest.
CI/CD integration
This is the feature that brings Astra’s continuous pentest offering to life. CI/CD stands for continuous integration and continuous delivery. It is a method of software development that makes it possible to launch and update applications at a crazy pace.
Integrating a pentest tool with an organization’s CI/CD pipeline means that vulnerability assessment becomes a natural part of the development cycle and you do not have to think about it separately.
Scan behind logged-in pages
When an external DAST scanner scans a page on the other side of the login, it stops working as soon as the session expires. It requires you to manually authenticate the scanner periodically to keep it functional.
Not with Astra! A login recorder extension by Astra Security ensures that you share some information to authenticate the scanner once and never worry about it again.
Regularly updated scanner rules
The security experts at Astra update the scanner rules every week to keep you ahead of the curve. A quick story about this.
A major vulnerability was recently announced by PrestaShop. Users of some versions of PrestaShop were found critically vulnerable to SQLi. But Astra Website Protection was already protecting against that vulnerability, without any special scanner rule put in place. (We have reinforced the scanner rules for the said vulnerability.)
Optimized for your technology
Astra’s Pentest Platform is optimizable for your framework. Whether your site is built on WordPress, Magento, Joomla, or PrestaShop, you can make slight manipulations (usually just a couple of clicks) to make a huge difference in the efficiency of the scanner.
Manual pentest and zero false positives
We have been talking about continuous pentesting – it is essentially automated. However, with Astra, you get vetted vulnerability assessments and manual penetration testing done by experts.
Not only does this ensure zero false positives, but also a more complete picture of your security posture. With the manual pentest, we can find business logic errors that are not detectable with automated scans.
Equally capable of testing single-page apps
Astra’s range in terms of scope of pentest and variety of applications that it can test is enviable. I mean we find ourselves hard-pressed to find limitations in the platform. (But we eventually do, how else do you improve?)
Security testing and emboldening with the same tool
Yes, we help you mitigate the risk and remediate vulnerabilities. But there’s more. You can use Astra’s Website Protection to secure your site.
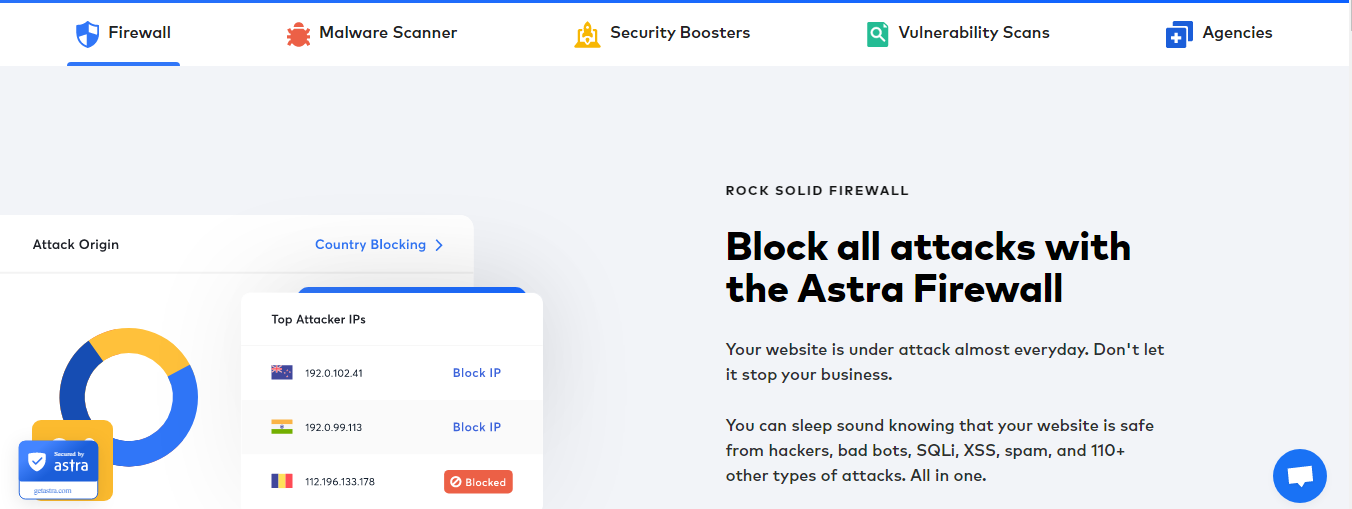
It comes with a firewall, malware scanner, boosters, flexible settings, and a dozen nobs that you can twist to make the security solution yours (it’s very effective out-of-the-box too). The best part is that you manage this from the same dashboard. Let that sink!
Bottomline
Continuous penetration testing helps you get consistent visibility into your system’s security posture as opposed to the point-in-time snap-shot afforded by a traditional annual pentest. We are not here to discard the importance of point-in-time penetration tests. They are extremely important considering the depth they bring onto the plate. That is exactly why Astra combines the rapidity and efficiency of automated pentest with deep manual pentesting.
FAQs
What is the cost of continuous penetration testing?
With Astra, you get continuous pentest at $199 per month.
How often does the automated scan occur?
You can schedule the automated scans according to your needs. Nevertheless, a scan takes place whenever some new code is pushed or an update is launched.
How does continuous pentest work?
Continuous pentest works through the integration of a security scanning tool with your CI/CD pipeline.
















