George Washington once said — the best defense is a good offense, with companies doing one pentest a year, which typically drags on for a few months Mr. President’s wise words need to be followed better.
Is the traditional annual pentest enough to keep your business safe? This is where penetration testing as a service (PTaaS) steps in! Before we jump in, let’s start by understanding what PTaaS is in detail.
What is Penetration Testing as a Service (PTaaS)?
Penetration Testing as a Service (PTaas) is defined as the process of leveraging human intelligence, automated tools & agile delivery methodologies to continuously find vulnerabilities in a given scope.
PTaas brings security engineers closer to the development team & makes the entire penetration test process more effective in terms of both time & cost.
Why Do You Need a PTaaS Over Traditional Pentesting?
While traditional penetration testing has served organizations well, it often lacks the agility and scalability needed in today’s dynamic threat landscape. Here’s a comparison between PTaaS & Traditional Pentesting on factors that modern engineering teams care about:
| Feature | PTaaS | Traditional Pentesting |
|---|---|---|
| Model | Continuous | Project-based, one-time engagements |
| Agility | Adapts to changing environments | Inflexible and reactive |
| Reporting Timelines | Vulnerabilities are reported as soon as they are found | Weeks or months for complete reports |
| Scalability | Highly scalable to the evolving needs | Scales with increased time & money investment |
| Cost-Effectiveness | Pay-as-you-go, predictable costs | Upfront costs, less flexible budgeting |
| SDLC Integration | Seamlessly integrated into development processes | Separate from the development cycle |
Designed as a project-based service, the traditional one-time engagement model is characterized by hefty upfront payments, patchy communication from security analysts, and lengthy penetration testing cycles. The wait for the final report – delivered in weeks or months – leaves you vulnerable in between and hinders timely remediation.
In contrast, PTaaS adopts modern engineering methodologies to deliver continuous security testing, real-time reporting, and agile pentesting models integrated seamlessly within your development lifecycle.
This leads to faster identification, enhanced agility, and improved ROIs. It helps you transition from reactive fixes to continuous improvement. PTaaS accelerates your giant leap from DevOps to DevSecOps.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

How Does a PTaaS Platform Work?
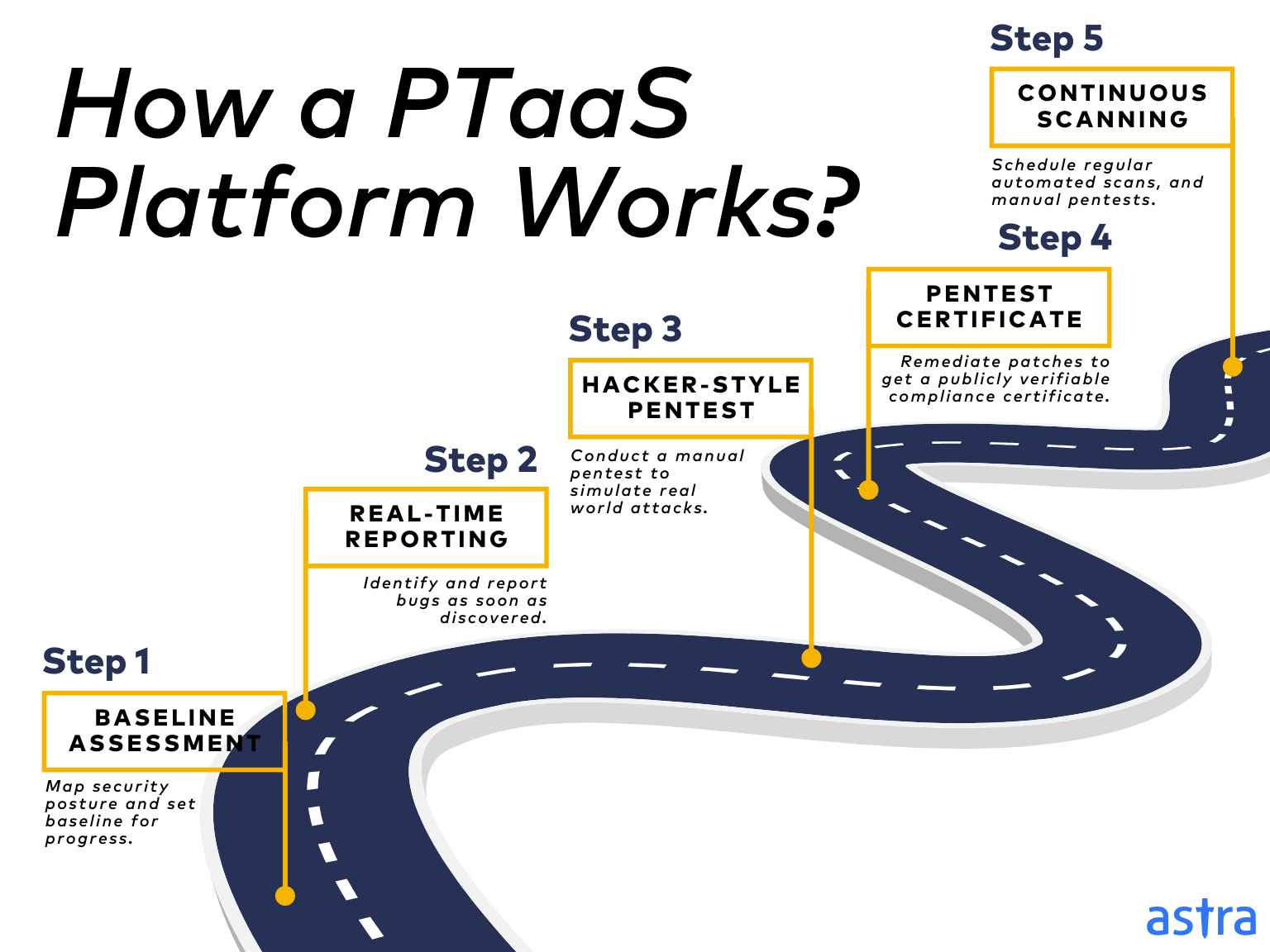
Step 1: Baseline Assessment
The process starts with an automated scanning engine to map your systems, applications, and network to generate an initial report of your current security posture – how the security measures in place would fare in case of an attack.
This report acts as the baseline against which all future progress is measured. As such, it also details proof of findings and recommendations for enhanced security measures.
Step 2: Real-Time Reporting
With the onslaught of emerging CVEs and cyberattacks, real-time reporting is the cornerstone of contemporary digital security. Vulnerabilities are identified and reported as soon as they are discovered.
This near real-time pentest reporting empowers you to address issues swiftly, minimize exposure, and enable proactive remediation.
Step 3: Hacker-Style Pentesting
While automated scans are effective, they can’t replicate the ingenuity of human attackers. PTaaS goes beyond by employing experienced pentesters to conduct “hacker-style” offensive security tests that simulate real-world attacks.
They leverage their years of experience in thinking like a hacker, AI-powered test cases, and industry-standard tools to uncover attack vectors, such as payment manipulation and business logic vulnerabilities — which often go undetected by automated vulnerability scanners.
Step 4: Pentest Reports and Certificates
Instead of simply pinpointing vulnerabilities, the ideal PTaaS platforms offer end-to-end vulnerability management services. This translates to providing detailed reports with Proof of Concepts (PoCs), vulnerability details, CVSS score, and steps to recreate and patch the same.
Moreover, after remediation, they verify the above to help you generate clean reports and publicly verifiable pentest certificates that facilitate compliance audits and strengthen your stakeholders’ trust.
Step 5: Continuous Vulnerability Assessment & Penetration Testing
With new zero days being identified daily, continuous vigilance is crucial. The ideal PTaaS platform helps you schedule regular automated scans and regression tests and run ad-hoc pentests.
Moreover, they help conduct quarterly or half-yearly manual pentests to identify new vulnerabilities that might have surfaced to ensure compliance across standards such as SOC2, ISO27001, CIS, GDPR, and HIPAA.
What Should You Expect From a PTaaS Platform?
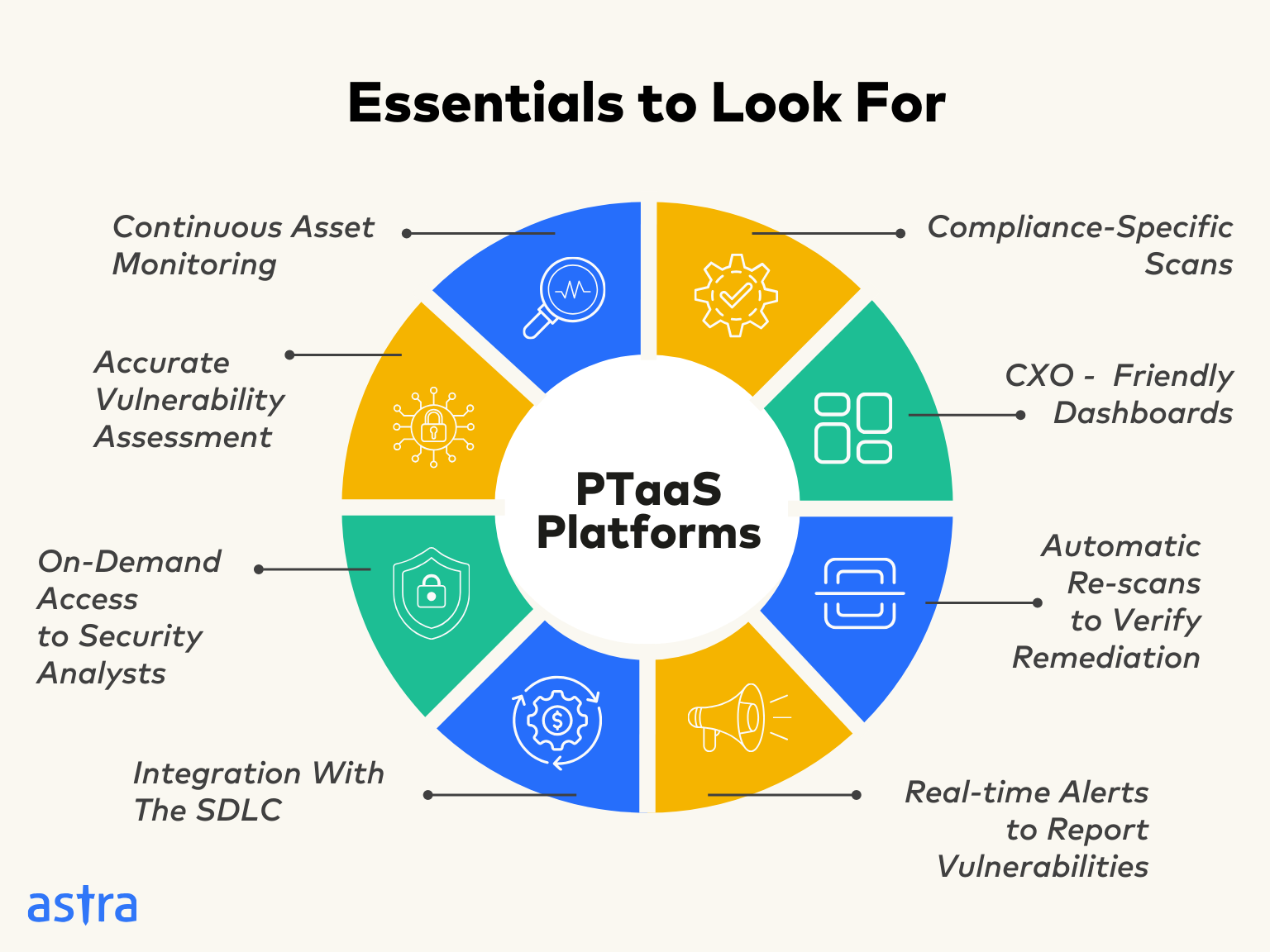
- Continuous monitoring of your assets
- On-demand access to pentesters and security analysts
- Fast results from human-led & automation-powered Pentests
- Accurate vulnerability assessment
- Integration with your SDLC
- Real-time alerts to report vulnerabilities
- Minimal gap between discovery and remediation of vulnerabilities
- Automatic rescans to verify the remediation
How to Choose a PTaaS (Penetration Testing as a Service) Platform?
With many local and international PTaaS vendors in the market and diverse offerings, choosing the ideal platform can take time and effort. Here are some essential features to look for in your ideal PTaaS vendor:
1. Comprehensive Vulnerability Detection:
The automated and manual pentest should scan and identify known, unknown, and emerging vulnerabilities, including those listed in OWASP 10 and SANS 25. They should also actively look for attack vectors specific to your industry and the tech stack you use.
2. Advanced Threat Detection:
While individual low-risk vulnerabilities seem harmless, they can create high-criticality attack vectors together. This is especially true for vulnerabilities related to business logic, IAM (Identity and Access Management), and payment manipulation.
Due to their sophisticated nature, most automated tools miss them, necessitating timely manual penetration testing by certified experts.
3. Zero False Positives:
False positives often lead to wasting time and precious resources across the board. The ideal PTaaS platform should offer minimal false positives – through expert vetted results of automated and manual pentests – if not eliminate them altogether.
4. Engineer-Friendly Reports:
Clear and concise reports are essential for long-term security and effective decision-making. Customizable reports, based on user roles with developer versions, including vulnerability details, CVSS score, impact, PoC, and steps to replicate and patch it, go a long way.
5. ‘Platform’ Approach to PTaaS:
Choose a company that offers a centralized dashboard to track real-time updates on penetration tests, key reports, and streamlined communication to avoid bottlenecks. An intuitive interface, customizable views, and easy user management help avoid bottlenecks and delays.
The Best PTaaS (Penetration Testing as a Service) Platform: Astra Pentest
Astra is a one-of-a-kind PTaaS Platform that makes otherwise chaotic penetration tests a breeze. Astra’s continuous vulnerability scanner emulates hacker behavior to scan applications for 9300+ security tests. CTOs & CISOs love Astra because it helps them fix vulnerabilities in record time and move from DevOps to DevSecOps with Astra’s CI/CD integrations.
Astra is loved by companies across the globe. Last year, Astra uncovered 2,000,000+ vulnerabilities for its customers, saving customers $69M+ in potential losses due to security vulnerabilities.
With zero false positives, seamless tech stack integrations, and real-time expert support, Astra makes pentests simple, effective, and hassle-free.

Still don’t believe us? Take a look at what some of our 650+ customers have to say!
What to Look For in a PTaaS Solution?
1. Depth and Breadth of Pentest Capabilities:
A PTaaS solution is only as good as the skillset of its security analysts and engineers. Look for platforms equipped with scanners to run event-triggered, continuous, and ad-hoc scans across various types of assets designed by qualified security engineers with hands-on experience.
2. Quality of Pentesting Experience:
The security engineers should also have industry standard certifications like OSCP, CEH, CISSP etc. It’ll be fair to mention that the security industry has enough talented security engineers who do not take the certification route but are still on top of their game. Experience in pentesting specific types of applications as tours contribute significantly to the quality of the pentests, especially with complex applications.
3. Remediation Support:
Look for platforms offering customizable executive reports for CXOs and exhaustive reports for developers for automated and manual pentests. Some basics include vulnerability details, CVSS score, compliance impact, and steps to replicate and patch it.
Pro Tip: An active customer support team also helps solve planning and execution bottlenecks by providing better insights into vulnerabilities to speed up the remediation processes.
4. Seamless Workflow Integrations:
Validate the availability and viability of integrations with your CI/CD pipeline, such as Jira, GitHub, GitLab, Slack, etc., to facilitate the transition from DevOps to DevSecOps, i.e., prioritizing security.
5. Compliance-Specific Scans:
Although most compliance guidelines with industry-specific regulations (e.g., HIPAA, PCI-DSS, SOC2, ISO 27001, etc.) necessitate only one annual pentest, PTaaS platforms offer unique real-time monitoring capability.
Pro-Tip: With in-built compliance-focused scans and reporting algorithms, they help you avoid fines associated with data breaches.
Final Thoughts
While vulnerability assessments and traditional pentests served their purpose, today’s dynamic threat landscape demands a more proactive approach: penetration testing as a service (PTaaS).
In the coming years, the PTaaS model will continue to evolve to become a natural extension of both, the engineering and security teams of an organization. According to Gartner, PTaaS appeals to organizations that aren’t looking to merely achieve but ‘beat compliance’, and we couldn’t agree more!
Building on traditional pentesting functionality, PTaaS equips you with real-time vulnerability detection, reporting, zero false positives, seamless CI/CD pipeline integration into your development process, and faster remediation.
Choose a platform with comprehensive testing, advanced threat detection, and user-friendly features. Embrace a proactive approach to security with Astra’s PTaaS Platform.
FAQs
1. What does PTaaS mean?
PTaaS (Penetration Testing as a Service) platforms offer an all-in-one experience by combining human, AI-augmented, and automated Pentesting services to deliver a holistic security approach. It is crucial to help your business make the leap from DevOps to DevSecOps.
2. What is the cost of Penetration Testing (PTaaS)?
The cost of Penetration Testing depends upon the scope of the test, the size of your organization, and the number of scans. It ranges between $400 and $1000 per scan for websites and between $700 and $4999 for applications.
3. What is the timeline for Pentesting (PTaaS)?
A typical automated pentest can take anywhere from a few minutes to 36 hours. Manual pentest can take a bit longer and usually range between 7-10 business days. However the same may vary based on the scope of the pentest and complexity of the digital asset being scanned.
















