What is Network Security Testing?
Network security testing is performed to determine whether a network is vulnerable to attacks from the internet or even from the internal network. This testing includes a review of all network infrastructure and systems accessible from the internet.
What are Network security testing tools?
Before you can understand network security testing tools, you might need to understand network vulnerabilities. Network vulnerabilities are holes in a network that can cause an attack and an attacker can exploit these holes in the network to gain access to your computer or any other computer on the web.
Network security testing tools are automated tools that scan the network for security vulnerabilities.
Best network security testing tools provide a comprehensive view of the security posture of your network. Modern network security testing tools come with various features to help network administrators identify anomalies and potential security issues and monitor and track network security across multiple locations. There is more to it than just protecting the perimeter regarding network security, network security testing tools can also protect your internal network against external threats.
List of 10 Best Network Security Testing Tools
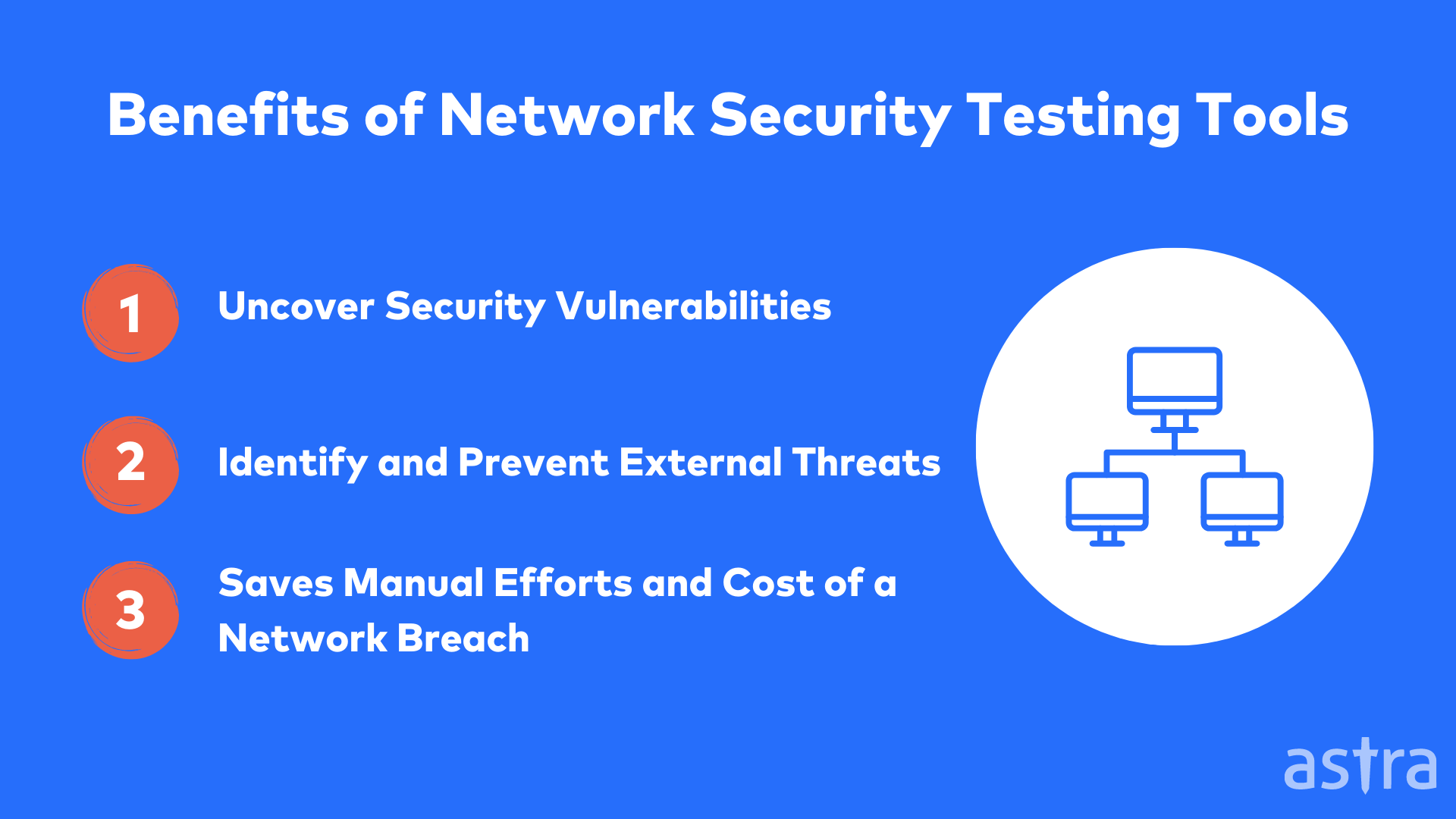
Benefits of Using Network Security Testing Tools
Network security testing tools are an essential part of an information security plan.
A network penetration test can be used to identify and prevent security risks in the networks. The results of the tests are analyzed to find any holes in the safety and to point out weaknesses in the existing security system. Network security testing tools help a business perform regular network security assessments with efficiency.
Also, a network penetration test online can increase IT security and keep data safe without putting extra pressure on the servers or interfering with business. The potential threats are identified along with suggestions for fixing them.
Also Read: Security Testing Software – 5 Things to Understand Before You Choose One
5 Different techniques used to perform Network Security Testing
1. Network Scanning
The Network scanner is a potent tool to scan a network and get information about the network. The network scanning tool can monitor the network, identify the hosts connected to the network, and identify the services running on the network like FTP, HTTP, POP3, and SMTP. The Network scanner also identifies the operating system running on the host and the version of the operating system.
2. Vulnerability Scanning
Vulnerability scanning is a network security process that detects and analyzes flaws in computers and computer systems and reports the information to administrators. This information helps plan security patches or upgrades. It can also help in determining the security status of a network.
Vulnerability scanners have been around for a long time. Still, they have been made more effective by using sophisticated techniques, such as fuzzing, and they are now considered an essential tool in supporting compliance with regulatory standards.
Also Read: Why Firewall Penetration Testing is Essential to Your Security Strategy
3. Ethical Hacking
Ethical hacking is the practice of testing a computer system, network, or web application to find security weaknesses (holes) before a malicious hacker does. It is the surface area testing of a system, network, or web application. Ethical hacking aims to find security weaknesses before a malicious hacker does.
4. Password Cracking
Password cracking is of two types:
Dictionary Attack: This method uses a dictionary (a word list) to crack passwords. The word list has all the possible passwords. So the computer compares the password given by the user to the word list to find out the matching password.
Brute Force Attack: This method uses an automatic program to crack passwords. The program tries all possible combinations of characters until it finds the correct password. Brute force attack is a time-consuming process.
5. Penetration Testing
Penetration testing evaluates computer security by simulating an active attack on a computer system or network. Penetration testing service is typically performed by ethical hackers, also known as white hat hackers, or by security professionals attempting to determine the extent of damage or risk before an actual attack.
Penetration testing differs from vulnerability scanning and compliance auditing in that the primary aim of penetration testing is to exploit potential vulnerabilities in a given target. In contrast, vulnerability scanning and compliance auditing are more passive tests.
Among other things, you can use a network penetration testing tool to perform an online firewall penetration test. It helps you understand how efficient the firewall is in the face of an imminent hack.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide | API Penetration Testing: What You Need to Know
10 Best Network Penetration Testing Tools
Network security is one of the biggest concerns of any business. Cybercriminals are constantly working on new ways of breaching network security and stealing valuable information. Network security tools are used to defend a network and network security testing tools are for assessing the security strength.
You need to be thorough in your network security testing and find vulnerabilities in networks before hackers do. There are a lot of network security testing tools out there. Some of the best are listed below.
1. Astra Security
Astra’s Network Security Solution is a unique product of Astra Security, a comprehensive security assessment of your network that can help you find and fix security risks. Astra’s solution is a solution that helps you to identify the security gaps in your network and helps you in plugging the holes.
The Astra Network Security Solution is the most comprehensive solution to perform a complete network security assessment. The solution scans and checks your network to identify the network devices, network ports, and network protocols to find out the vulnerabilities in your network and help you fix the vulnerabilities in a timely manner.

2. NMAP
Network Mapper, or Nmap, is an open-source utility for network exploration, security auditing, and network discovery. It was designed to rapidly scan large networks, although it works fine against single hosts.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
While Nmap was developed for UNIX-based operating systems, it also runs on Windows, and there are also versions available for most other major operating systems.
3. Wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Wireshark can be used to capture and interactively browse the contents of network traffic.
Wireshark is also commonly used to analyze data from a trace file, generally in the form of a pcap (the file format of libpcap). Wireshark has a GUI and comes in both 32-bit and 64-bit versions.
4. OpenVAS
OpenVAS is a vulnerability scanner that can perform a complete vulnerability scan of the network infrastructure. OpenVAS is an international project that is used by many organizations all over the world. It is available for free and can be used with commercial products.
Greenbone owns OpenVAS tool and the paid solution is called Greenbone Security feed while the free one is called Greenbone Community feed
5. Metasploit
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is open-source, free, and available to the public.
The project provides information about security vulnerabilities used by penetration testers during security audits and network administrators to ensure the correct configuration of the network’s devices.
6. Nikto
Nikto can be used to rapidly detect suspicious behavior on a network. It is an open-source web server scanning tool. Nikto checks HTTP servers and server configurations for vulnerabilities. The scanner is updated automatically. Some cool features are
- Full HTTP proxy
- Customized reporting in XML, HTML, and CSV formats
7. PRTG Network Monitor
The PRTG network monitor is a comprehensive network monitoring solution that comes with a web-based interface. All devices and traffic in your entire IT infrastructure can be monitored with this tool and it is suitable for all shapes and sizes of businesses. The tool monitors networks using SNMP protocol.
Also Read: 7 Best API Penetration Testing Tools And Everything Related
8. Snort
Snort is an open-source tool for intrusion detection and prevention. It uses protocol analysis to detect worms, port scanning, and other attempts of network intrusion. It describes network traffic with the help of a Modular Detection Engine and a Basic Analysis along with Security Engine.
9. Intruder
Intruder is an automated vulnerability scanner that can detect vulnerabilities in your network systems. They offer enterprise-grade vulnerability scanning for businesses of all sizes. It can easily detect issues such as SQL injection, and cross-site scripting. It prioritizes the vulnerabilities based on the context and helps you remediate with effect.
10. Syxsense
Syxsense is a unique tool that not only finds the issues in your network security but also employs the solutions (at least the simpler ones). Among its features are
- Port scanners
- SNMP ports
- RCP policies
Also Read: 11 Top Penetration Testing Tools/Software
How much does a Network Security Testing Tools Cost?
Network security testing tools can be costly, and it depends on the tools you are using and the number of networks you are scanning and a lot more factors that are usually discussed before signing a contract. A network security scan should be conducted at least twice a year to check the network’s security and make sure it is secure against threats. On average, the cost usually ranges from $500 to $2500 per network scan.
3 things to know before buying the best network security testing tools
With the number of different network security testing tools available, businesses are faced with a bewildering number of choices when it comes to selecting the best network security testing solution, and keeping that in mind, we have prepared a list of a few things to keep in a while buying a network security testing tool.
1. Ease to use and Friendly UI
One of the critical factors for organizations to choose a network security testing tool is the ease of use. A simple interface and easy-to-follow instructions are always appreciated. Even the most advanced tools are rendered useless when the user does not know how to use them. A good tool will have an easy-to-use interface, step-by-step instructions, and a detailed user guide.
2. Comprehensive scan report
Understanding the threats against your business is crucial when it comes to risk management. A comprehensive security testing report is essential to keeping your business safe. A comprehensive security testing report can uncover high-risk vulnerabilities, help you better understand your network, and help achieve compliance.
3. Updated with Latest Vulnerabilities
No automated security testing tool is perfect. Hackers are constantly finding and releasing new vulnerabilities. An automated network penetration testing tool should have an updated database of security vulnerabilities so that no vulnerability is left unnoticed.
Astra’s Pentest Solution: All in one Security Solution
No matter how big or small your company is, hiring a pentesting vendor to protect your network and applications is vital. Hiring a good pen testing solution will not only protect your business but your data as well. Astra Security is an excellent solution for your business.
Astra Security has been in the industry for many years now; it offers multiple pen testing solutions, including Network, Web, API, Blockchain, and Cloud penetration testing.
The Astra Penetration Testing Solution is a “Next Generation” Penetration Testing software used by thousands of organizations worldwide. Astra’s pentest solution is well-known for its excellent vulnerability scanner with more than 3000 tests, making it a perfect choice for penetration testing.
Have a sneak peek at Astra’s Dashboard.
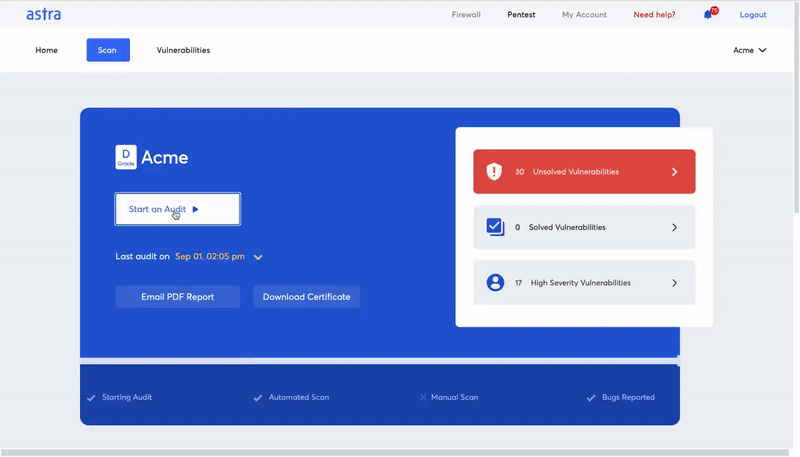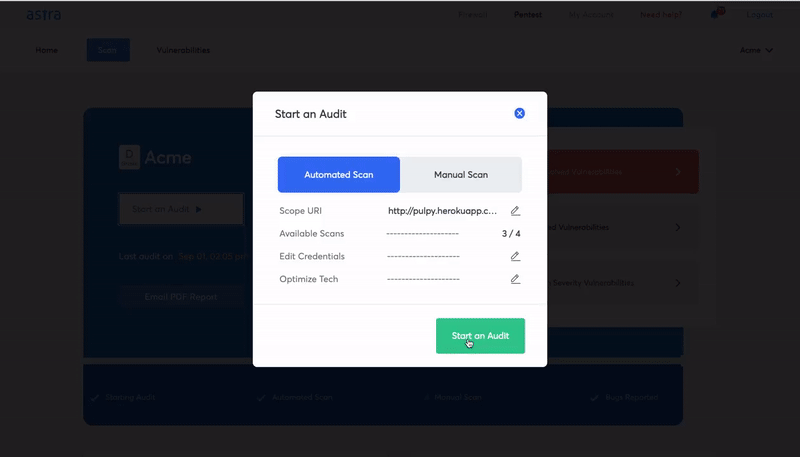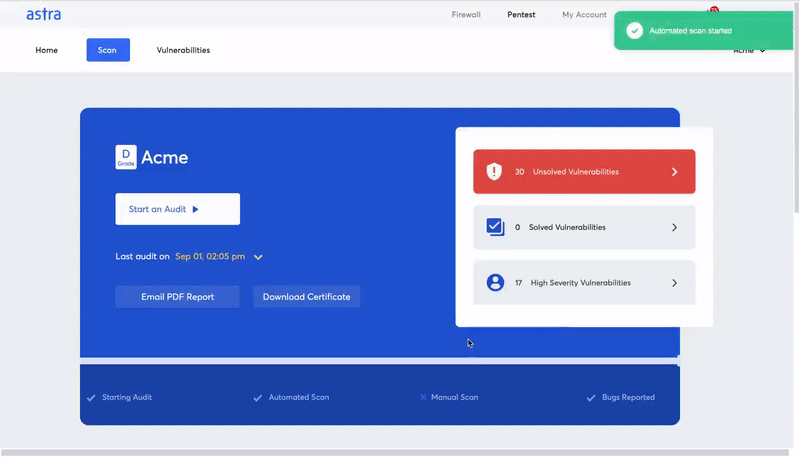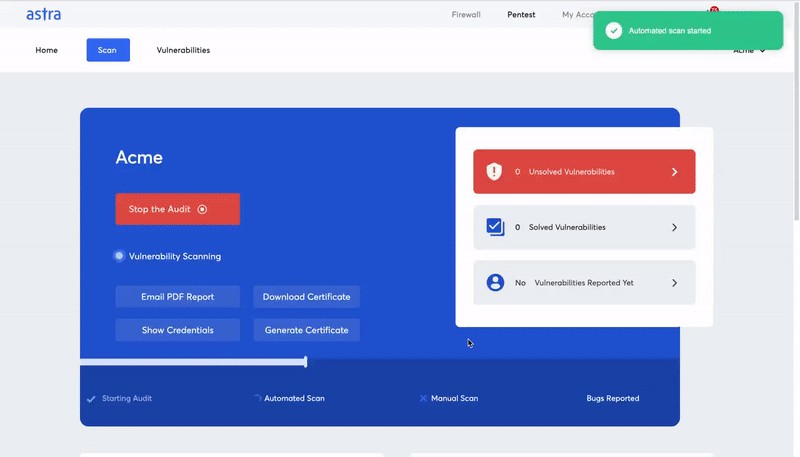
Conclusion
Network security testing is a vital part of the information security management process. It involves testing the security of an organization’s network infrastructure, applications, systems, and services to find vulnerabilities that could be exploited by a malicious individual, hacker, or group. Various organizations use network security testing tools to keep their network secure from hackers. Secure your network too before it’s too late. Get in touch with Astra today.
FAQ’s
1. What is Network Security Testing?
Network security testing identifies security vulnerabilities in the network by using software applications and tools designed to detect and protect the network from malicious attacks.
2. What are Network Security Testing Tools?
Network security testing tools are automated tools that scan the network for security vulnerabilities. Modern network penetration testing tools have various features to help network administrators identify anomalies and potential security issues and monitor and track network security across multiple locations.
3. Is it legal to scan any Network for security risks?
The question about the legality of port scanning is quite frequent. The law is quite clear about it: you can not scan any network without the owner’s permission legally.
4. Can Astra help me with Network Security Testing?
Astra’s network security testing service is a top-notch way to improve your security, and we can even help you out if you’re just getting started. We have the tools and experience to find vulnerabilities and help you implement security to make sure your network stays safe. It’s time to get proactive and keep your business safe.
















