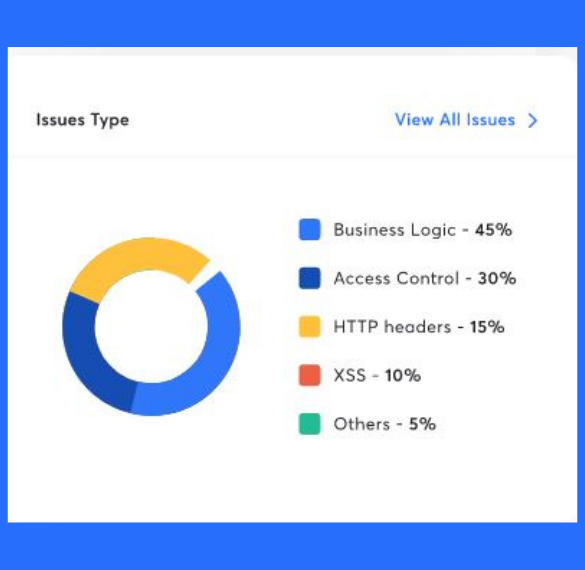
Article Summary
Network Security Testing aims to assess and analyze the security posture of an entire network. It involves all the devices, applications, and services running on the network. We will discuss various tools and techniques used in this holistic approach to cyber security.
Are you confident about the network security measures you have taken to ensure protection from cyber attacks? Yes? That is wonderful news! Do you need regular Network Security Testing? Yes you do, because hackers are incredibly motivated and you might have something they want – personal information of customers, credit card information of shoppers, everything has great value for them.
Just 10 stolen credit cards from every hacked website can earn hackers $2.2 million per month. A major strike like the British Airways attack of 2018 where the details of 380,000 credit cards were stolen, must have earned the hackers around $17 million, assuming they sell one credit card for $45 in the underground selling forums. (Source)
It is on you to protect all that information, and you would want a consistent and systematic verification of your cyber defenses. Read on to learn more about Network Security Testing, and how it is essential for the well being of your business.
What is Network Security Testing?
Network security testing is a holistic approach to finding security vulnerabilities and loopholes across a network that may contain multiple network devices, applications, and be in direct contact with customers, other businesses, and the government. Regular security tests of a network leads to the revelation of vulnerabilities and allows the owners to take responsive and preventive measures to ensure better security.
Why is network security testing important?
We are often tricked into thinking that buying a firewall or running a security audit once in a long while is enough to maintain the security posture of a network. While these measures are important, they are not quite adequate, given the kind of threats you are dealing with.
If you follow the OWASP top 10 or SANS 25 vulnerabilities, you will notice that several CWEs or Common Weakness Enumerations are mapped to each of those vulnerabilities. For instance, in 2021, there have been more than 318,000 occurrences of the 34 CWEs mapped to just one vulnerability category – Broken Access Control.
Now, we are talking about one sort of vulnerability off one list of vulnerabilities. The intention behind establishing this is to help you realize how difficult it can be to maintain a near perfect security posture. All it takes to wreak havoc is a line of loosely written code. According to a report, security breaches took 228 days to get detected and 80 more to contain. Prevention, it seems, is the best cure.
Network Security Testing helps you –

Read also: What is Network Penetration Testing? And How to Perform it?
Different Approaches to Network Security Testing
Network security is a broad term and it involves different strategies and methodologies. We will have a brief discussion about some of those approaches.
White Box Security Testing
White box method refers to a methodology of security testing where the testers know how the system works. They examine control flow, data flow, code implementation, and error handling. This sort of testing determines whether the code implementation is in line with the intended design.
Black Box Security Testing
Black box testing service is a mode of testing in which the testers do not have internal information about the target network. This process of testing emulates a real attack. Black Box testing is useful for testing server misconfigurations, and deployment issues.
Grey Box Security Testing
The Grey Box method combines the White Box and Black Box methods of Network Security Testing. In this process the testers work with limited information like login credentials. These tests are great for understanding how much access a privileged user has and how much damage a hacker with similar privileges can cause.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide
Different Types of Network Security Testing
Depending upon the nature of your business, the industry you are operating in, and your specific goals, you can choose a certain type of security testing. You often need to combine multiple of those to get the desired results. We will look at some of the different forms of security testing.
Network Scanning
Network scanning is a routine procedure performed by network administrators to identify the active devices within a network. The goal is to monitor and manage the systems, make an inventory of devices, and to compare the inventory of devices to the expected number of devices to assess the network’s health.
Network administrators usually employ a feature in the network protocol to identify the responding devices. Attackers use a similar strategy. They would first figure out the IP address range assigned to a company using DNS or WHOIS protocol. Then they would scan the addresses within that range to find out servers, operating systems, and services running on them, and try to find a way to breach.
Attempting a network scan from an attacker’s point of view to find vulnerabilities and patch them up is a pretty neat way of assessing and maintaining security health.
Also Read: Network Security Testing and 5 Best Network Security Tools in 2022
Vulnerability Scanning
Vulnerability scanning is the process of scanning networks, servers, and applications, for security vulnerabilities and loopholes with the help of automated scanners. These scanners are computer programs that enlist all IT assets operating within a network and find out operational details about them along with the vulnerabilities.
When it comes to network security scanning, vulnerability scanners look into the devices, and access servers connected to a network, and find unknown perimeter points such as remote access servers.
Password Cracking
Password cracking is one of the many ways used by attackers to gain access to a network. For instance, if an attacker wants to upload and execute a file on a target application, having the credentials of a legitimate user makes the job much easier. With the privileges granted to users, a hacker can do a lot of damage to a network.
There are generally two kinds of password cracking attacks
- Dictionary attack: It uses a long list of passwords to guess the actual password. The program runs until either the passwords match or the list is exhausted.
- Brute force attack: In this case the password cracking program checks all possible combinations of a given character set to guess the password.
Network users often use easy to remember passwords for login and authentication. While these passwords might qualify as strong according to the set of password strength standards set by a company, they are easy to crack, and therefore a major threat to an organization.
System administrators and Penetration Testers use Password cracking to find out users who might be using weak passwords, and remedy the situation.
Ethical hacking
Ethical hacking is the authorized emulation of a hack to find out security vulnerabilities in a network, a website, or an application. Ethical hackers, also known as White Hats, are security experts who use their skills to gain access to a system and discover the vulnerabilities and the risk associated with them.
Ethical hacking follows certain rules such as,
- It has to be a legal procedure.
- It is conducted under predetermined rules of engagement.
- The scope of the hack is decided and strictly followed.
- The ethical hackers often have to sign a non-disclosure agreement.
- The hack should not interfere with business functionality.
The goal of an ethical hack is to report vulnerabilities before hackers with malicious intent exploit them.
Penetration Testing
Penetration Testing refers to the process of finding vulnerabilities in a network, website, or application, discovering how much risk those vulnerabilities pose, and helping the target organization fix those vulnerabilities.
The term Penetration Testing is often used interchangeably with Ethical Hacking. Remember, Ethical Hacking is a broad term covering a lot of different methods, and penetration testing is just one of them.
Nevertheless, Penetration Testing also known as Pentest is one of the most popular ways to conduct Network Security Testing.
In this method, the security experts uncover vulnerabilities inherent in a network, and try to exploit each of the vulnerabilities to an extent. The goal is to find out how much access a certain vulnerability may yield to an attacker. Then they prepare a Pentest report that documents the vulnerabilities along with the degree of risk posed by them. The report also recommends steps to remediate the uncovered vulnerabilities.
Read also: Breaking Down The Pentest Process – A 5 Step Guide
Different Network Security Devices
Network security devices are placed to monitor and control network traffic. These are used to flag malicious traffic, and protect the network from threats. As an aftermath of Network Security Testing, the experts can recommend one or more of these devices. Let us look at some popular Network Security Devices.
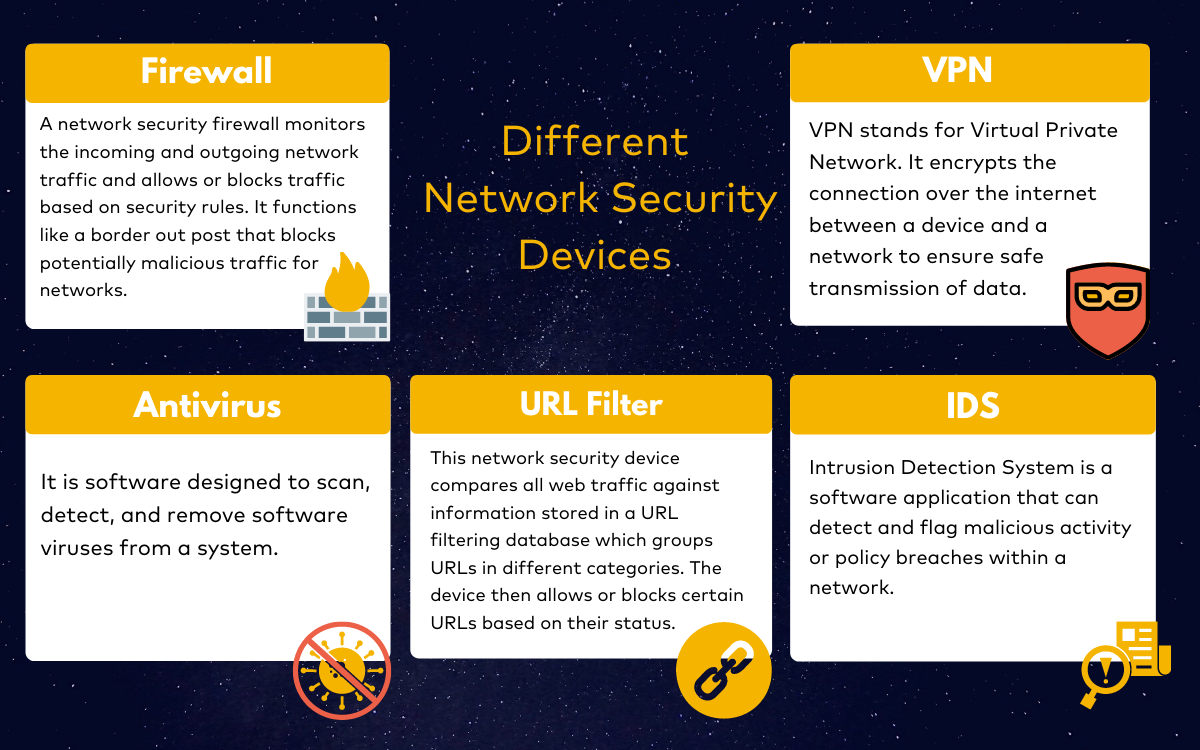
Also Read: 11 Top Penetration Testing Tools/Software of 2022
What are the business outcomes of Network Security Testing?
There are some very clear benefits of performing regular Network Security Testing. It is a practice that comes with a genuine ROI and long term advantages.
- The average cost of a security breach is somewhere between $4-5 million. You save yourself from that peril with the help of a security test every once in a while.
- Protect partners, third parties, and stakeholders by securing your network.
- With adequate security measures in place, you can significantly reduce network downtime thereby aiding business continuity.
- Comply with regulatory requirements with ease by conducting consistent Network Security Testing.
- Build trust among customers and clients by taking adequate measures to protect their data.
Some Popular Network Security Testing Tools
- Astra Pentest: A comprehensive Network Security Testing solution that takes care of every step of the process and leaves very little for the users to do. The security experts at Astra run automated and manual scans of your network to uncover vulnerabilities. This is followed by manual Pentest to assess the vulnerabilities. The Pentest report comes with detailed guidelines and video POCs for your developers to use for remediation.
- NMAP: It is a popular open source tool used for Network Mapping and scanning. It can perform port scanning, service fingerprinting, detect misconfigurations, among other things.
- Wireshark: It is a network protocol analyzer that supports more than two thousand protocols. It continuously scans a network for vulnerabilities.
- Metasploit: It is a tool for Pentesters to deliver payloads and exploits into Networks to exploit and assess vulnerabilities.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
In conclusion
Network Security Testing is not a one time procedure nor is there a one size fits all approach to it. You have to take it seriously, practice it consistently, and enlist the best quality help that you can find. Whether you are operating within a private network or connecting to a public network, you have to stay accountable for security, and that is why it is important for you and your business.
Supported by a practice of regular Network Security Testing you can protect your assets, stay compliant, build trust, and save money.
FAQs
- How much time does it take to perform a Network Penetration Test?
It usually takes up to 5 days to complete a Network Penetration Test. - What is the cost of performing Networking Pentest?
It depends upon the scope of the Pentest. A ball park figure would be $999 per scan. - Why is Astra a good choice for Network Security Testing?
Astra Security functions like your in-house security team and takes the pressure off your shoulders. With 8000+ tests, a dedicated team of expert Pentesters, and meticulous remediation support, Astra is quite hard to beat.