There were 5.6 billion malware attacks in 2020. As bad as it may look it was a 43% improvement on the stats from 2018. Google has been detecting 600-800 malware infected sites per week in 2021, whereas it had detected 3000+ per week in 2019. It is good news for all technology enthusiasts and security-minded people. But at the same time, there has been a 485% increment in ransomware attacks since 2020 according to a survey by ISACA. There is no permanent relief from the fear of getting hacked.
It all boils down to how security conscious your organization is and how well prepared you are to survive cyber-attacks. Your best course of action is consistent penetration testing and vulnerability remediation. We will discuss what penetration testing is, what is the Pentest process, how it helps you defend your business and more.
Wrap your head around Pentesting
The underlying concept of Penetration testing or pen testing is simple. You invite security engineers to test your website, application, or network. They simulate a hack and try to penetrate your system. They find the weaknesses and try to assess how dangerous those weaknesses can be. Then they create a report documenting the vulnerabilities and recommending fixes.
A lot more than what meets the eye goes into the execution of a vulnerability assessment and penetration testing (VAPT) operation. This article will cover five indispensable steps of the Pentest process. But before we get into all of that, let us understand why this is important.
What makes Pentesting important?
Cybercrime has reached a point of sophistication where targeted attacks are almost impossible to detect or prevent until some damage is done. 73% of black hat hackers opine that malware scanners are obsolete. However, there are 30,000 cyber attacks every day and very few of them are targeted towards a particular organization.
When it comes to breaching a website, hackers want to cast as wide a net as possible, hence they automate the attacks. The only way to do that is to search for websites and networks with known vulnerabilities. For instance, a site using cross-site scripting or a vulnerable plugin is an easy target.
You need consistent Pentesting because you do not want to be an easy target.
Are you unable to access your website? Is your website experiencing hacking issues? Find out in 15 seconds.
Who needs Pentesting?
Any business with a digital existence and a willingness to manage risk and protect their customers’ interests should have penetration tests performed. However, regular penetration testing with pen-testing software is essential for certain industries.
- Service providers need to conduct security audits every two quarters in order to stay SOC 2 compliant (SOC stands for Service Organization Control). Penetration testing is required as a part of the SOC 2 Type II audit.
- Banking institutes need penetration testing to stay compliant with the Payment Card Industry Data Security Standards (PCI DSS). This is essential to ensure the security of the sensitive data of cardholders.
- Healthcare institutes operating under the Health Insurance Portability and Accountability Act, 1996 (HIPAA) are bound to conduct regular security audits and Pentesting is one of the popular methods to achieve that.
Whom should you trust it with?
It is best to engage with professionals who are adequately trained to handle penetration tests and are well-equipped to ensure excellence at each step of the Pentest process.
You need to work with a company that offers:
- Exhaustive range of tests
- A quick and comprehensive report
- Assistance in fixing the security loopholes
- And yet keeps it simple and hassle-free for you.
Read Also: Looking for a VAPT provider? This is What You Should Know
The Pentest Process Explained
The Pentest process starts with planning, and ends with a report documenting the results and remediation, and there are three more stages in between. Let us see what the 5 steps in the Pentest process are, and why each of them is important.
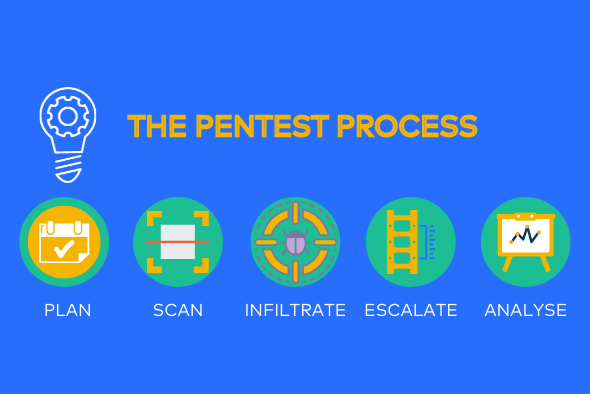
Step 1. Plan
This stage has a couple of aspects to it.
- The pen-testing team consults with the target organization, learns about their objectives, sets the rules of engagement, and agrees upon the legal implications.
- The pen testers use a variety of tools and techniques to gather as much intelligence as they can about the target. This makes their simulated attack more precise as well as fruitful.
The planning stage determines the number of important factors before the rest of the Pentest process unfolds.
- The scope of the penetration test: It defines the assets that are within the scope of the pentest as well as those that are out of scope.
- Testing methodology to be used: The tools and techniques used for a test are determined in this stage.
- Setting goals: The penetration test should address certain concerns the client might have, its result should also align with the business goals of the client organization.
- Selecting potential vulnerabilities: The pre-engagement phase or the planning stage helps the pen-testers identify certain vulnerabilities that are most likely to be present in the client’s systems.
Step 2. Scan
Once the planning and scoping is done, the obvious subsequent step is to scan the target system for vulnerabilities. The goal of penetration testing is to check the target system for a list of known vulnerabilities. All of that takes place in this stage.
The scan can be automated, manual, or a combination of both. The last one is the most prescribed approach.
The tester sends probes to the target and monitors how the target responds to various inputs. One can use the static or dynamic scan to test applications. A lot of vulnerabilities are revealed during this stage. Some of them are
- SQL injection
- Cross-site scripting
- Remote code execution
Step 3. Gain access
When a hacker finds a vulnerability in your application or website, their goal is to use it as an entry point to gain access to valuable information and maintain and expand that access. The point of pentesting is simulating a hack to help you prepare for one, hence a Pentester does the same.
Gaining access to a target system can be as simple as accessing an exposed private URL but not always. Sometimes the Pentester may have to run an exploit in order to gain access. There are a couple of things to remember in this regard:
- Not all vulnerabilities can be used to gain access, it is important to choose one that can.
- Pentesters should run an exploit to gain access only if they are absolutely sure that the vulnerability exists in the target system and if the rules of engagement allow it.
- The pentester must ensure that no system functionalities are compromised in the process of gaining access.
Step 4. Retain and elevate access
Once the Pentester has access to the system, the task that follows is to maintain and elevate that access even after a system reboot or modification.
Attackers need a shell that gives them administrative access to make any real harm. By maintaining access they can look for opportunities to elevate access. They can use an exploit to do it. If it does not work, then they can look for additional vulnerabilities like misconfigurations or faulty file system permissions.
Elevating access like this is also referred to as privilege escalation where an attacker escalates from low privilege to high privilege and gains deeper access into the system.
Step 5. Analyze and report
Through the last four stages, the Pentester has identified the vulnerabilities, tried to exploit them, gained and escalated access with some of them. All these activities help the testers gather insights about the vulnerabilities.
The fifth phase consists of translating the insights into consumable information and then reporting them to the target organization.
The tester rates the vulnerabilities in terms of exploitability, severity, and the threat it poses to the business.
A detailed VAPT report is created with a list of the vulnerabilities, the score or rating corresponding to each vulnerability, and detailed guidance for remediation.
The VAPT providers need to put two separate reports together – one to help the developers with the resolution of the issues, and the other one for the business users to comprehend the nature and severity of the security threats.
Tools used in different stages of the Pentest Process
There are a lot of tools that you can choose from to conduct each step of the Pentest process. We are listing a handful of them here.
- Shodan, Netcraft, Threat Agent, Blind Elephant, are some tools used in the planning and recon stage.
- Some tools used in the scanning stage are Astra vulnerability scanner, Hydra, Powershell Suite, Zmap, etc.
- You can use tools like Nmap, Metasploit, Burp Suite, for gaining and retaining access.
In fact, a lot of these tools can be used for multiple stages of the Pentest if you know what you are doing.
Cyber security is a complicated subject with high stakes, hence, it is always recommended that you rely upon experts when it comes to running penetration tests or fixing vulnerabilities.
There are open-source tools and free checklists that you can use to conduct a DIY pentest, but you already know how quickly things can go south once you try to exploit a vulnerability.
Let Astra help
Astra Security’s Pentest solution can make the seemingly complex vulnerability management and penetration testing process seem like a breeze.
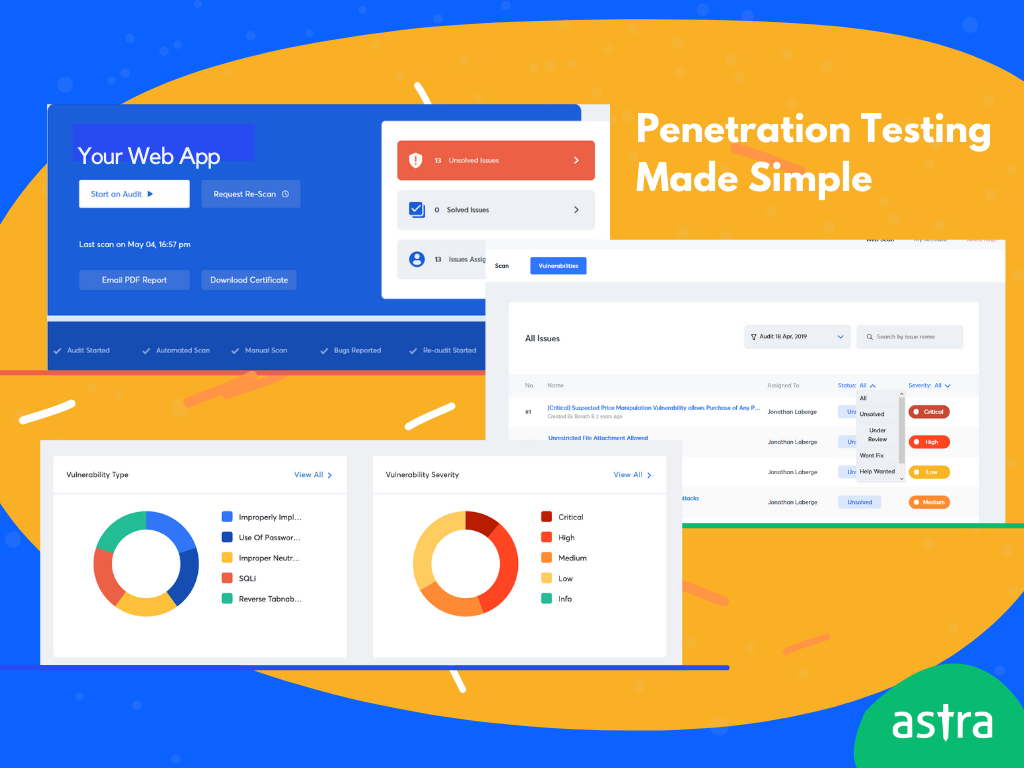
The security engineers at Astra run a large set of manual and automated tests to identify and rate vulnerabilities present in your system.
Your developers get a step-by-step video PoC to fix the vulnerabilities. They also get ample time with the security engineers to discuss any roadblocks in terms of remediation.
Most importantly, you get a dedicated dashboard to monitor and fix the vulnerabilities even while the security audit runs.
It does not get any simpler than this.
In conclusion
Penetration testing is a necessity even if it is not mandatory by your industry standards. Understanding how it works will help you assess the offers made by various VAPT companies. It will also help you ensure that you are getting the best solution available to you.
Now that you know how a Pentest works, and why you might need one, all you need to do is find a VAPT company that can cater to your specific needs.
FAQs
How much time does the Pentest Process take?
The Pentest Process can take 4-10 days depending on the nature and scope of the Pentest. After you have fixed the identified vulnerabilities, the rescan can take half the time taken by the initial test.
How much does Pentesting cost?
The cost of penetration testing for web applications is between $700 and $4999 per scan, depending on the number of scans and the scope of the test. The cost of Pentesting for cloud infrastructures like AWS and GCP is between $499 and $999 per scan.
Why should you trust Astra with Pentesting?
With 8000+ tests according to global security standards, Astra ensures that all security loopholes are identified. The VAPT dashboard offers dynamic visualization of the impact and severity of threats. It helps you prioritize the remediation. Astra assists you in fixing the vulnerabilities and certifies your web app.
Do I get rescans after the vulnerabilities are fixed?
Yes, after you have finished fixing the vulnerabilities you will get 1-3 rescans based on the plan, to ensure all the loopholes are covered. You will have 30 days after the initial test completion to avail the rescans.
















