Web Application Security Testing is assessing your web application’s web security software for flaws, vulnerabilities, and loopholes in order to prevent malware, data breaches, and other cyberattacks. Meticulous security testing reveals all hidden vulnerable points in your application that run the risk of getting exploited by a hacker.
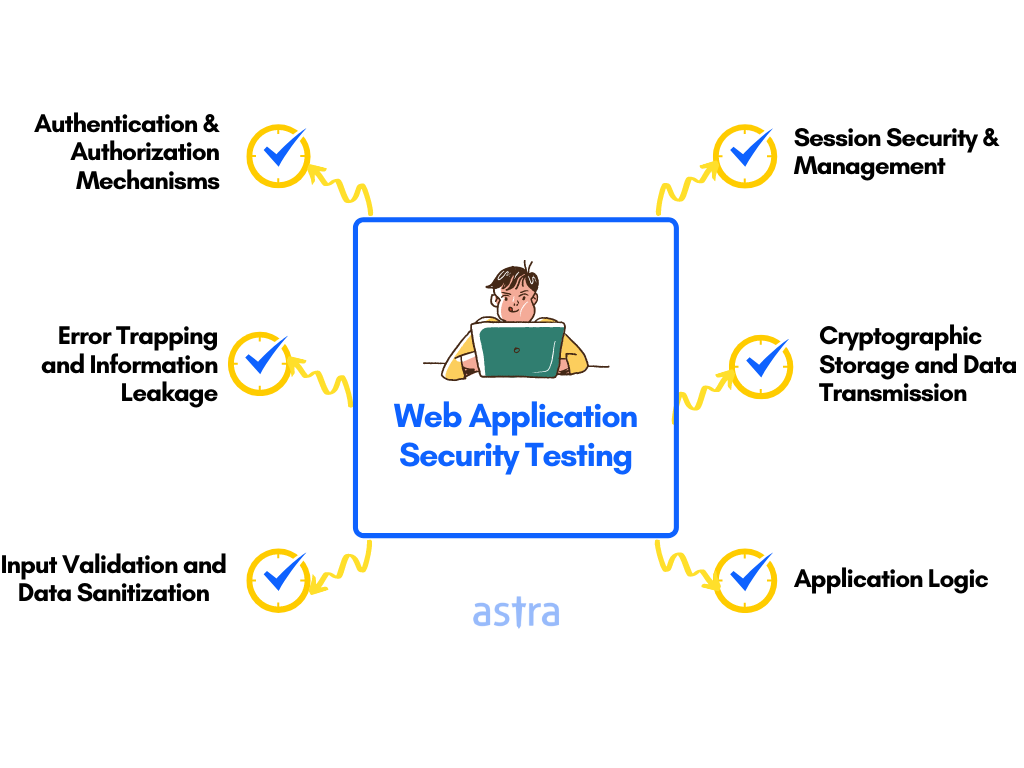
Types of Web Application Security Testing
There are three approaches to web application security testing, namely:
Black-box security testing
Black box pentesting requires the pentester to think outside the box and employ methods that a true hacker would carry out to break into a system since they are completely uninformed and has no knowledge of the systems.
White-box security testing
White box security testers have complete knowledge of the system and complete access. The advantage, in this case, is that the tester has unbridled access and knowledge of the system, including code base code quality, API documentation, and internal designs.
This way the pentest can identify even remotely located vulnerabilities, thus giving a nearly complete picture of the security.
Gray-box security testing
With gray-box security testing, the tester has only limited knowledge of the system. The advantage of this approach is that with the limited amount of knowledge, the tester has a more focused area of attack and thus avoids any trial-and-error method of attack.
Why you must not neglect Web Application Security Testing?
Digitization bestowed us with many boons and some new banes – Hackers & Cyber threats. With every passing day, hackers are developing more and more sophisticated techniques to bypass previously established security standards. Regular web security testing helps you stay on top of the vulnerabilities that may be used against your app.
For the longest time, developers’ complete focus was converged on building apps and software without giving a second thought to its security. Cybersecurity was being brushed under the carpet at boardroom discussions and business meetings. This changed when security breaches in business giants started making headlines and companies started losing millions. This is when cyber threats were acknowledged and cybersecurity was given due importance and priority.
Hence, you must not overlook web application security testing if you want to:
1. Identify flaws and vulnerabilities in your application:
The most important benefit you can get out of thorough security testing is that it uncovers all security flaws and vulnerabilities in your application. Web app security testing has emerged as a crucial step in the Software Development Life Cycle (SDLC), making developers mindful of security while they build the application.
2. Comply with laws:
Councils and conglomerates were formed, and laws were implemented to regulate data security & privacy in web applications. Web application security testing was mandated for many businesses (such as e-commerce, finance, banking, etc) to protect user interests.
It is very important for a business owner to conduct web app security testing for their application and that too regularly in order to comply with the current laws. Web security testing is not limited to just businesses but is equally crucial for developers, who push out web apps for public use on app distributor platforms or as a SaaS (Software as a Service).
3. Analyze your current security:
Web app security testing also checks your current security measures and detects loopholes in your system. The firewall dedicated to protecting your web app can have vulnerabilities too. The web application security test helps you spot those weaknesses and fix them before they are exploited.
4. Detect security breaches and anomalous behavior:
Another huge benefit of conducting a security audit is that it helps you identify security breaches or hacker behavior in your application. As per IBM, on average, it takes companies 192 days to identify a data breach in their system. By this time, the damage may become irrevocable. Periodic web security testing sniffs out hacks and breaches in due time saving your business from adverse consequences.
5. Formulate an effective security plan:
Detailed outcomes of an audit can help you plan and prioritize risk responses better against a breach or a hack. It also helps you formulate an incident response mechanism as per your app’s or business needs.
Who performs Web Application Security Testing?
You can either hire professional web application security testing tools to audit your application or have an in-house team perform security testing for you regularly. If you’re a solopreneur or an app developer, you can perform preliminary web application security testing on your own as well.
Note: Owing to the complex nature of security testing, there are too many ways one can falter. Hence, it is advised that you go with professional security testing for the best results and better protection of your app and its users.
That said, you sure can perform a preliminary web app security testing (minus the code analysis) yourself. Refer to the next section.
Common Terms Used in Web Security Testing
- Vulnerability: A vulnerability is a security risk in a web application that can be potentially exploited by hackers to gain access to the app or data.
- XSS: XSS, short for Cross-Site Scripting, is a type of attack in which an attacker inserts malicious JavaScript code to extend an attack from one compromised website/application to another.
- SQLi: SQL Injection is a very critical vulnerability. In SQLi, hackers inject malicious SQL queries into the website via form inputs, GET, POST, Cookies, etc. It can give hackers access to your database, file system, and in most cases complete server. SQLi is caused due to lack of input sanitization and escaping. This is one of the most critical vulnerabilities which can compromise the entire web app.
- Spoofing: Phishing and email spam are the biggest opportunities for hackers to enter the network. They often spoof a web app’s emails & messaging to trick a user into clicking on some malicious email attachment. It can compromise an entire enterprise with ransomware, cryptojacking scripts, data leakages, or privilege escalation exploits. This can be prevented with the help of {DMARC/SPF} records.
- URL manipulation: Attackers often manipulate client-browser communication to intercept crucial data & credentials. If they do this by modifying some information in the request URL, it’s known as ‘URL manipulation’.
- CSRF: Cross-site request forgery is a web application vulnerability that lets an attacker jump the same-origin policy and take actions on behalf of the user.
How to perform Web Application Security Testing manually?
To perform web services pentest manually, follow these steps:
- Asset discovery: Identify your application’s security areas and its complementary assets that would be included in the testing.
- Check for outdated versions: Verify if your application is up to date. Repeat with other assets.
- Check permissions: Check if your app follows secure rules for user permission and roles.
- Check security protocols: Check if there are security measures such as a firewall, malware scanner, SSL, etc. in place.
- Analyze code rigidity with penetration test: Analyze your code for CVE, code injection, SQLi, and other common attacks. (This would require more hands-on experience with security testing.)
- Test database security: Check if your database is hardened against malicious SQL queries or not.
- Run configuration tests: Check your application as well as your network’s configuration structure and determine if they are secure.
- Check network assets: Test your router, switches, printers, servers, desktops, etc. against known CVEs and specially crafted attacks.
- Business logic: Check your application for vulnerabilities in terms of design and implementation.
- Client-side logic: Check if the JavaScript loading on browser web pages follows the correct rule.
- Input validation: When accepting user data on your web app, check if input validation is in place.
- Authentication & session management: Check authentication rules and ensure that session management is not vulnerable.
- Configuration: Check your web app for missing or misplaced configurations.
- Authorization check: Verify if your web app allows unauthorized access.
Testing Methodology for Web Application Security Testing (in Phases)
Phase I: Initiation
- Define the scope of testing for an application
- Document initial testing requirements
- Develop testing & scanning schedule
- Understand implemented functionalities in an application
- A sampling of browser-server traffic flow
- Finalize the format of testing deliverables
Phase II: Evaluation
- Perform static code analysis of an application
- Server Infrastructure Testing & DevOps
- Identify the loopholes in the business logic
- Do authorization checks for user access (UAC)
- Schedule manual & automated application scanning using tools
- List commercial and open-source tools for security testing
Phase III: Discovery
- Perform dynamic analysis & penetration tests
- Payment manipulation testing
- Test for known CVEs
- Technology-specific attack vectors and payloads
- Verify findings and remove false positives
- Catalog all the exposed vulnerabilities
- Collection of evidence and Video POCs
Phase IV: Reporting
- Determine ease of vulnerability exploitation
- Document app vulnerabilities details
- Research and document technical solutions or recommendations for fixes
- Do an Independent quality review
- Get a VAPT Certificate for security audit from a reputed vendor
What are web security testing tools?
You can automate most of the discovery and testing processes with tools available online. Here are some of the web application security testing tools you can use for the purpose of web security testing:
- Astra’s Pentest Suite
- Nikto
- NMap
- BurpSuite
- Arachini
- Harvester
- Testssl
- OpenVAS
- Metasploit
- SQLMap
- XSSer
Astra’s Pentest Solution
Looking for professional web app security testing? Look no further. Astra’s Pentest solution has got you covered with its well-designed tests that pack both power of automation and human intelligence.
Astra Pentest provides checklists for vulnerability assessments and a web application security testing checklist.
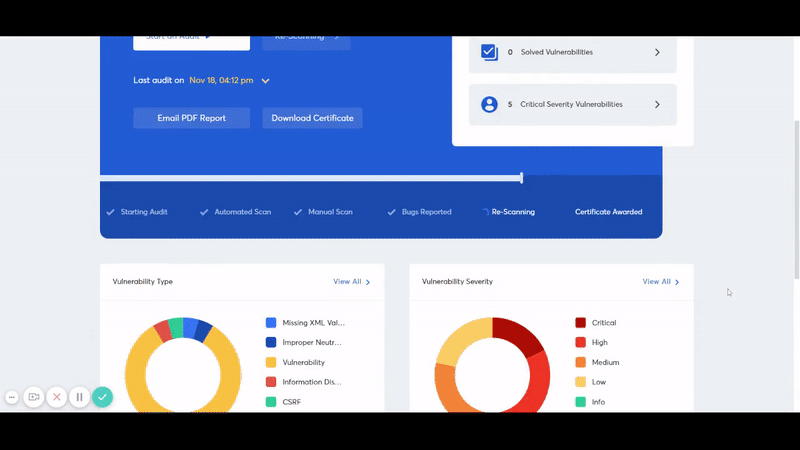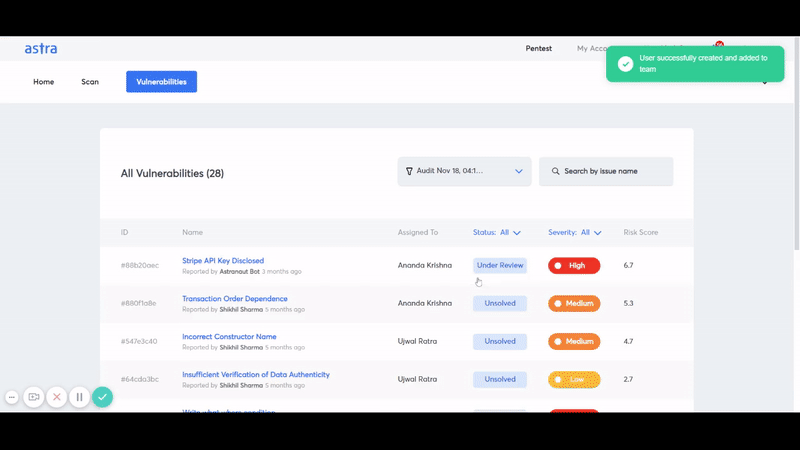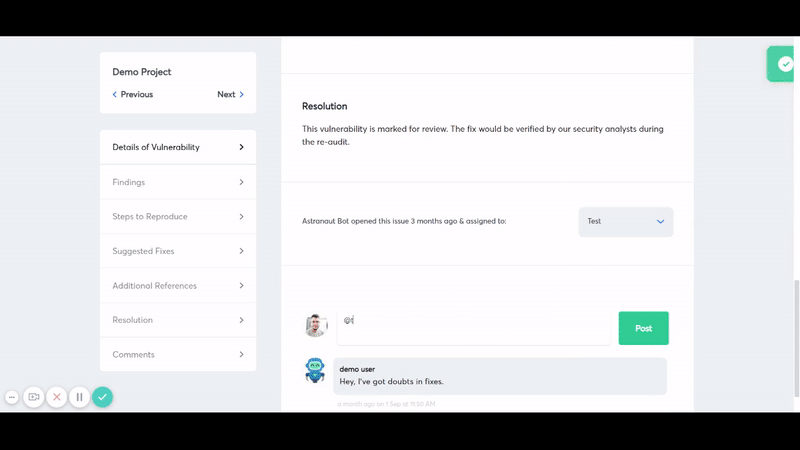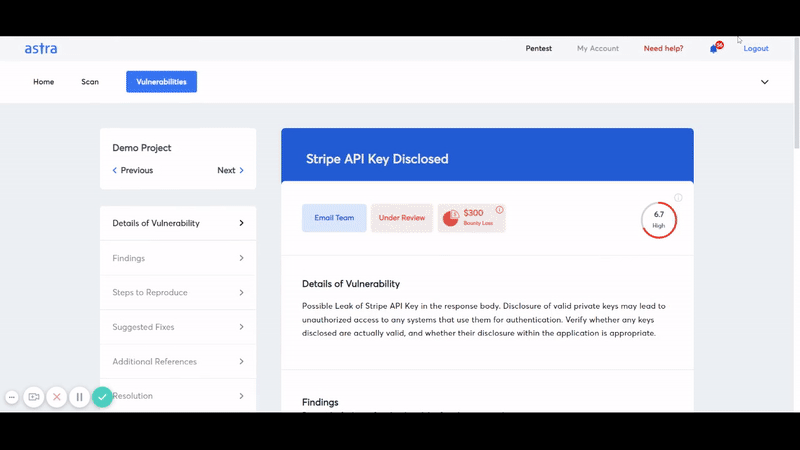
Astra Security detects security loopholes in your Network including AWS, Azure, or any other cloud and Application (Web application & mobile application), routers, IoT, with 8000+ security tests which include — security control check, static and dynamic code analysis, configuration tests, Server Infrastructure Testing & DevOps, Business logic testing among various others.
FAQs
1. What is the timeline for web application security testing?
Web application security testing takes 7-10 days. However, the vulnerabilities start appearing on your Astra security audit dashboard from the 3rd day, so that you can start working on the fix.
2. How much does security testing cost?
Security testing for web applications costs $199-$7,999 per scan depending on the number of scans and the plan. You’ll find the detailed pricing here.
3. Why choose Astra for Web App Security Testing?
8000+ tests, adherence to global security standards, an intuitive dashboard with dynamic visualization of vulnerabilities and their severity, simultaneous remediation assistance, and multiple rescans, all these features give Astra an edge over competitors.
4. Do I also get rescans after a vulnerability is fixed?
Yes, you get 2-3 rescans depending on the plan you are on. You can use the rescans within a period of 30 days from initial scan completion even after a vulnerability is fixed.
















