A Black-box penetration test is a third-party testing service that aims to find & exploit vulnerabilities in a system as an outsider. The security expert is provided with no information about the target system prior to the testing. Except for the target URL and (maybe) access similar to an end-user. This means the tester has no access to source code (other than publicly available code), internal data, structure & design of the application before the testing.
The name “black box’ is suggestive of the dark, no-information starting point in the test.
A black-box penetration test tests your live application, on run-time. It is thus also called Dynamic Application Security Testing (DAST). A black-box pentest service provide the great testing to your external assets like:
- Web-apps
- SaaS apps
- Network
- Firewall
- Routers
- VPN, IDS/IPS
- Web servers
- Application servers
- Database servers, etc.
While black-box pentesting is not an alternative to a complete security review, it helps in testing the application from the POV of an end-user or a hacker. It can flag serious vulnerabilities in your web-facing assets such as – validation errors, information disclosure via error messages, server misconfigurations, and so on.
8 Benefits Of Black-Box Pentest
Black-box penetration test on its own is not sufficient for identifying all security vulnerabilities in a system. Though, when coupled with source code review and other tests, it provides a wholesome picture of the security status of the system & network.
Here’s how you can benefit from a black-box pentest:
- It tests your application as a hacker. In a true sense
- It finds the exposed vulnerabilities on your networks and apps
- Since it tests the application on run time, it can help you detect implementation & configuration issues
- It detects incorrect product builds (e.g., old or missing modules/files)
- It can detect security issues relating to people – by employing social engineering techniques
- It can detect security issues that arise as a result of interaction with the underlying environment (e.g., improper configuration files, unhardened OS, and applications)
- It can detect issues like input/output validation errors, information disclosure in error messages, etc
- It can be cheaper to conduct a black box penetration test compared to other pentesting types like – gray box & white box

3 Drawbacks Of Black-Box Penetration Testing
A black-box penetration test is an important component of application security testing. However, in no circumstance, should you trade off a comprehensive review of the source code and internal system for a black-box pentest.
Since a black box does not include internal testing, a system may falsely appear to be ‘secure’ if the tester fails to find any vulnerabilities in the external components. In reality, the application may have a pile of vulnerabilities beneath the surface.
In other words, vulnerabilities identified in a black-box test indicate that the target system has a weak security build. The same can’t be said when it does not highlight any important security vulnerabilities. In that case, the vulnerabilities are just hidden inside the internal systems.
To sum up, a black box penetration test:
- Doesn’t provide a complete picture of the target’s security system
- Is based on endless guesswork, and trial & error.
- Can range either way on the time scale. It can take the least amount of time to identify vulnerabilities or can take months to recon and identify a single vulnerability. It all depends on the expertise of the tester.
Why Astra is the best in pentesting?
- We’re the only company that combines automated & manual pentest to create a one-of-a-kind pentest platform
- Vetted scans ensure zero false positives
- Our intelligent vulnerability scanner emulates hacker behavior & evolves with every pentest
- Astra’s scanner helps you shift left by integrating with your CI/CD
- Our platform helps you uncover, manage & fix vulnerabilities in one place
- Trusted by the brands you trust like Agora, Spicejet, Muthoot, Dream11, etc.

Black-box vs Gray-box vs White-box Penetration Testing
Clearly, black-box penetration testing isn’t enough. This is where gray-box & white-box penetration testing comes in. To better understand these three penetration testing styles, let’s look at their differences:
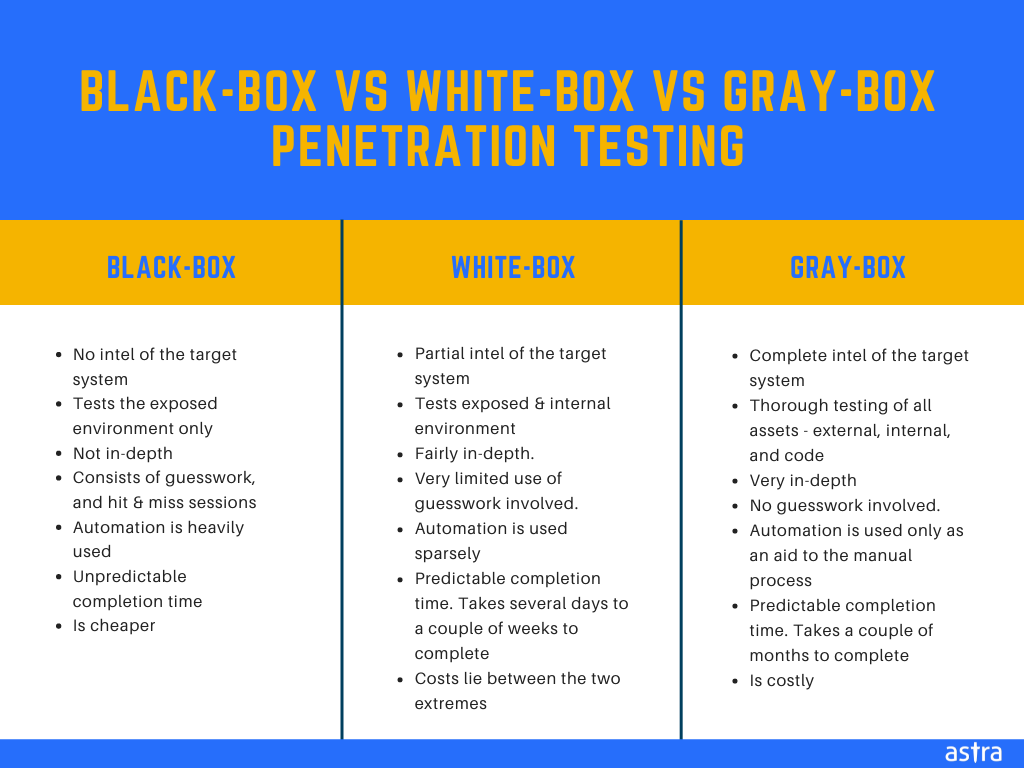
Black-box
- Is conducted without any prior intel of the target system.
- Only tests the exposed environment.
- Is not at all in-depth.
- Consists of guesswork, and endless hit & miss sessions.
- Automation is heavily used.
- ETAs are unpredictable. Can be very fast or take months on end.
- Is cheaper.
Gray-box
- Is conducted with partial intel of the target system.
- Tests exposed vulnerabilities in outer systems as well as hidden vulnerabilities in internal systems.
- Provides a fairly better picture of the system’s security.
- Very limited use of guesswork involved.
- Automation is used sparsely. Only to replace repetitive and tedious scanning work.
- Takes a predictable amount of time to complete. Time often ranges from several days to a couple of weeks.
- Costs lie between the two extremes.
White-box
- Is conducted with complete intel of the target system.
- Conducts thorough testing of all assets – external, internal, and code.
- Provides a complete picture of the system’s security.
- No guesswork involved.
- Automation is used only as an aid to the manual process. Only to replace repetitive and tedious scanning work.
- Takes a couple of months to complete.
- Is costly.
Keeping in mind the limitations of a black-box penetration test, at Astra, we offer both black-box & gray-box penetration testing. Black box pentesting helps with regular pentest of your application which you can use at your own code push cycle’s pace. The gray box testing ensures that our security experts try to break into the application like a hacker and look into the internal as well as external threats.
All vulnerabilities are then reported on our Pentest dashboard, which simplifies overall vulnerability management for both the involved parties – the tester & the client. More information here.
6 Common Black-box Penetration Testing Techniques
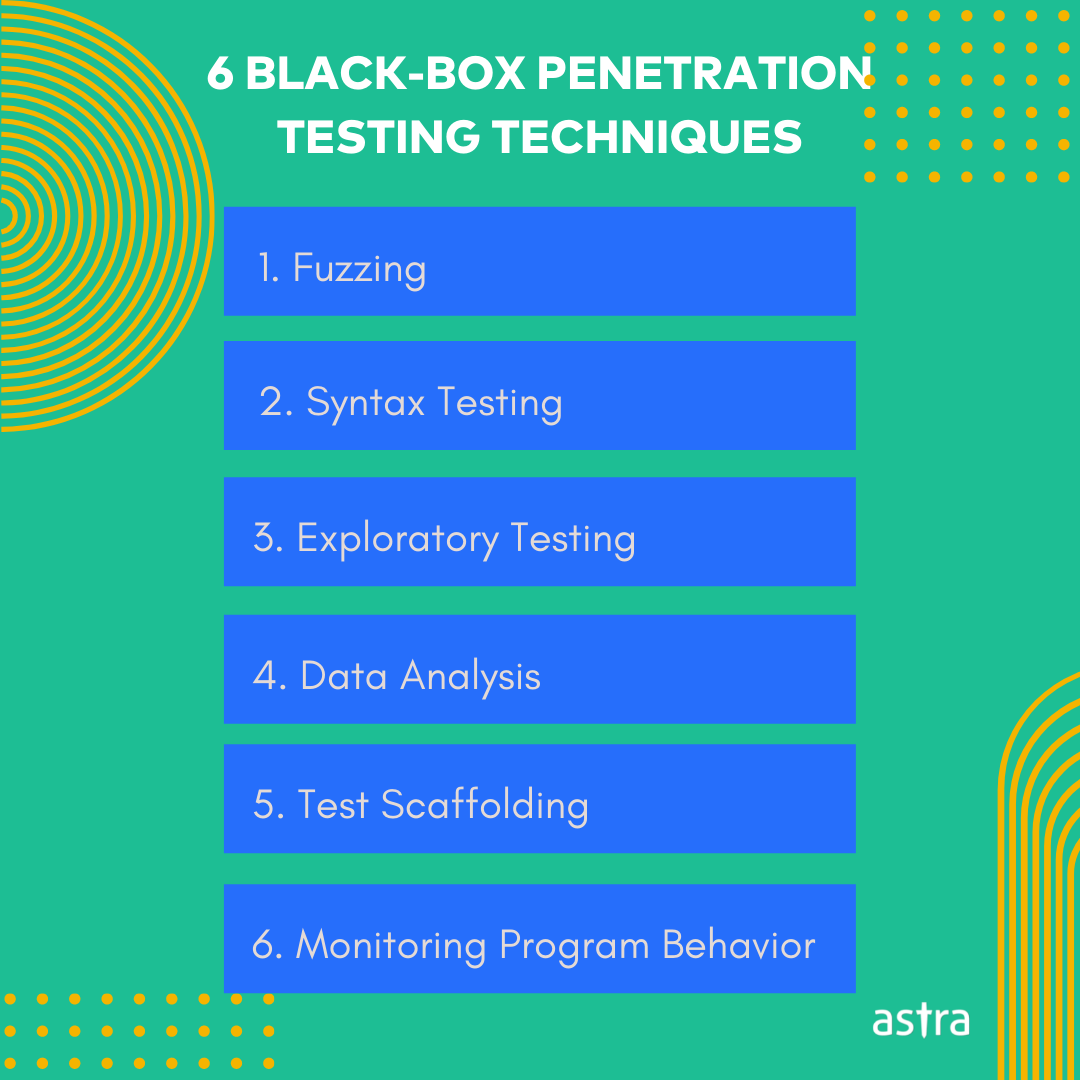
1. Fuzzing
Fuzzing is a process to test web interfaces for missing input checks. It’s done by injecting random or well-crafted data, also called noise injection. The goal is to identify unusual program behavior that results from noise injection. The success of Fuzzing may indicate the lack of proper checks in the software.
2. Syntax testing
Syntax testing is a process to test the data input format used in a system. Usually, this is done by adding input that contains garbage, misplaced or missing elements, illegal delimiters, etc. The aim is to find out the outcomes in case the inputs deviate from the syntax.
3. Exploratory testing
Exploratory testing is testing without any pre-formed test plan or expectation of a specific outcome. The idea is to let outcomes or anomalies of one test guide another. It is especially helpful in black-box penetration testing, where a big find may shape the whole test.
4. Data analysis
Data Analysis in black-box pentest refers to the review of the data generated by the target application. It helps the tester understand the target’s internal functions.
5. Test scaffolding
Test Scaffolding is a technique to automate intended tests with tools. This process helps the tester find out critical program behavior otherwise not possible in manual testing. These tools usually include debugging, performance monitoring, and test management tools.
6. Monitoring program behavior
Monitoring program behavior helps the tester understand how the program responds. With this technique, the tester may find unspecified symptoms that are indicative of underlying vulnerabilities. This process can be automated to save testers from manually checking for anomalies in program behavior.
Black-Box Penetration Testing Checklist
Based on the OWASP Top 10 vulnerabilities, here’s a checklist to make sure your black-box pentest covers all crucial areas.
- Attempt to find and exploit all the input fields including hidden ones.
- Use automated tools to detect vulnerabilities.
- Scan networks for exposed ports, systems and services.
- Attack using different credentials or through brute force.
- Try to intercept and modify communication between clients and servers.
Black-Box Penetration Testing Steps
A typical black-box penetration testing goes through these 5 stages:
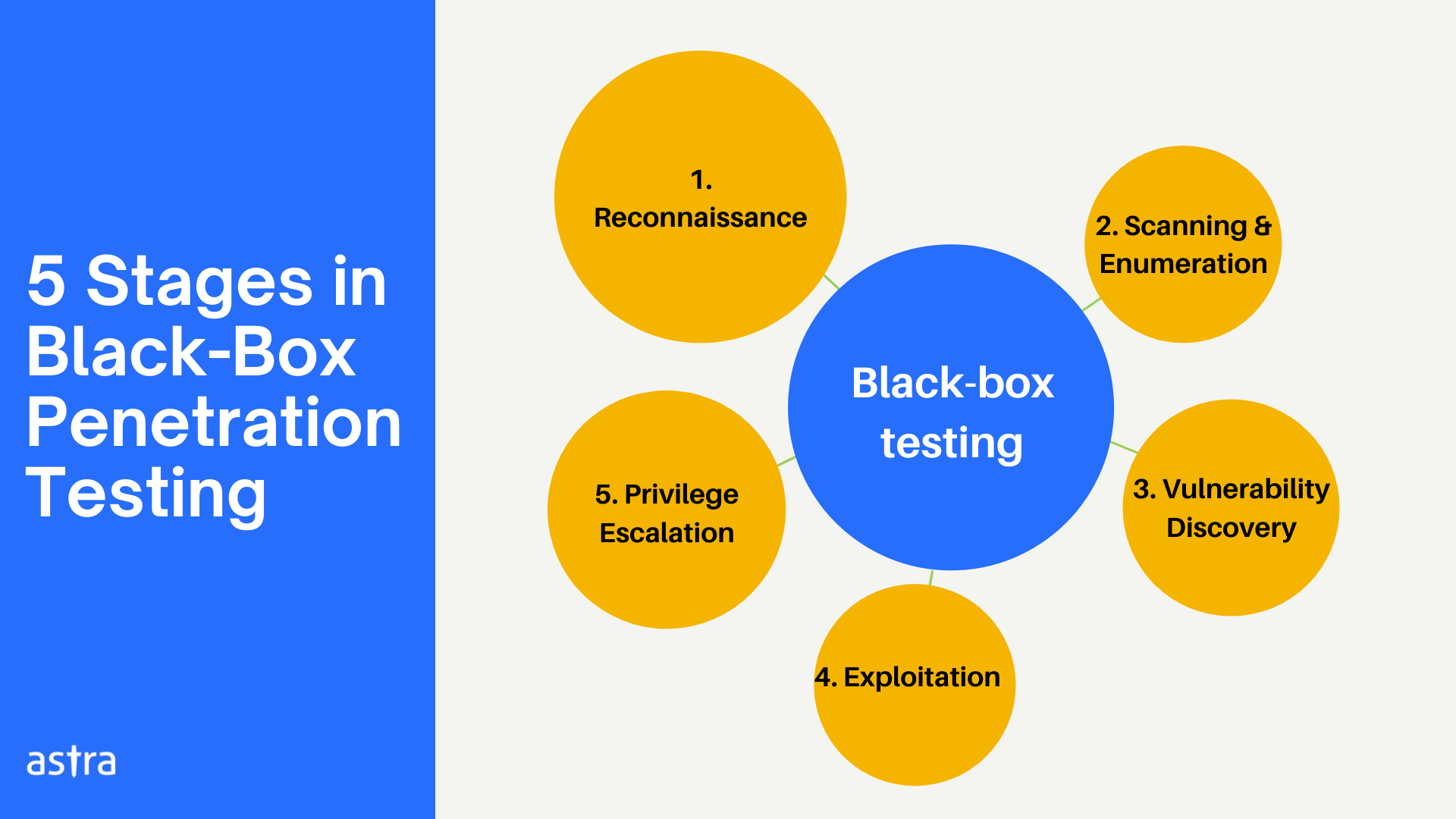
1. Reconnaissance
Reconnaissance is the process of gathering preliminary information about the target system. The intel may include information like – IP addresses, email addresses, employee information, websites, exposed pain points, and so on.
2. Scanning & Enumeration
Scanning & Enumeration is where more reconnaissance is done. This is where the tester looks for more data about the target like types of running software, operating system, versions, connected systems, user accounts, user roles, etc.
3. Vulnerability Discovery
With the above reconnaissance, the tester now looks for public vulnerabilities in the target systems & networks. This may include known CVEs in the system, versions, or third-party applications used by the target.
4. Exploitation
Exploitation is where the tester crafts a malicious request, or social engineer to exploit the identified vulnerabilities. The goal of this step is to get to the heart of the system via the shortest route possible.
5. Privilege Escalation
After the tester breaks into the system, they try to escalate their access level to gain complete access to the system and database. This stage is called Privilege Escalation.
Black-Box Penetration Testing Cost
A full-scale black-box penetration testing carried out by ethical hackers is usually priced between $5, 000 to $50,000 per test.
This is more costly when compared to a white box pentest and a gray box pentest which is much cheaper.
Black Box Penetration Testing Tools
Black-box Penetration Testing By Astra Security
Astra Security offers a black-box pentest with Astra’s automated vulnerability scanner. Our scanner scans your application & network for 2500+ exposed vulnerabilities, with new vulnerabilities added from time to time.
We also conduct static & dynamic code analysis, business logic testing, and payment gateway testing as is done in a white-box pentest under our manual pentest engagement.
Here’s what else you get with Astra Pentest:
- An intuitive vulnerability management dashboard
- Detailed vulnerability reports (including PoCs, steps-to-reproduce, selenium scripts, etc.)
- Monetary loss value associated with a vulnerability
- Intelligently calculated risk score for each vulnerability
- Hacker-style pentest with 2500+ tests
- Ability to collaborate within our dashboard with security engineers manual scanning/pentest
- A grading system to rank the security of your assets
- Detailed steps-to-fix and fixing advice from security engineers
- Publicly verifiable certificate
Learn more about Astra’s Pentest Suite here.

Conclusion
As celebrated software engineer & author Boris Beizer said,
“Software never was perfect and won’t get perfect. But is that a license to create garbage? The missing ingredient is our reluctance to quantify quality.”
Security of software is an ongoing process. You develop, test, secure, and repeat. There are various ways to test an application. Penetration testing is one of the most common.
Black-box penetration testing helps you test your live application for implementation, validation, and other errors. On its own, black-box penetration testing does not reveal everything wrong with the application’s security. Combining a black-box penetration test with other tests, such as source code review, increases its effectiveness.
FAQs
What is the timeline for Black-Box Penetration Testing?
The timeline for Black-Box Pentesting is 7-10 days. The rescan after fixing the vulnerabilities takes 3 more days. The timeline may differ slightly based on the scope of the test.
How much does penetration testing cost?
The cost for penetration testing ranges between $99 and $399 per month for websites.
Why choose Astra Pentest?
The security engineers at Astra perform extensive manual pentest on top of machine learning-driven automated scans. The vulnerability reports appear on your dashboard with detailed remediation guides. You will have access to a team of 2 to 10 security experts to help you with the fixes.
Do I also get rescans after a vulnerability is fixed?
Yes, you get 1-3 rescans based on the type of Pentesting and the plan you opt for. You can avail these rescans within 30 days from the initial scan completion even after the vulnerabilities are fixed.
















