A network vulnerability assessment is a network security practice that helps organizations identify, quantify and prioritize the risks and vulnerabilities in their network infrastructure that could result in malicious exploitation. It also helps your dev teams to fix those vulnerabilities through detailed remediation steps.
In other words, network vulnerability assessment is all about knowing your weaknesses before someone else does.
This article will focus on the network vulnerability assessment process (including its what, why, and how).
So, let’s get started!
Factors to Consider For a Network Vulnerability Assessment
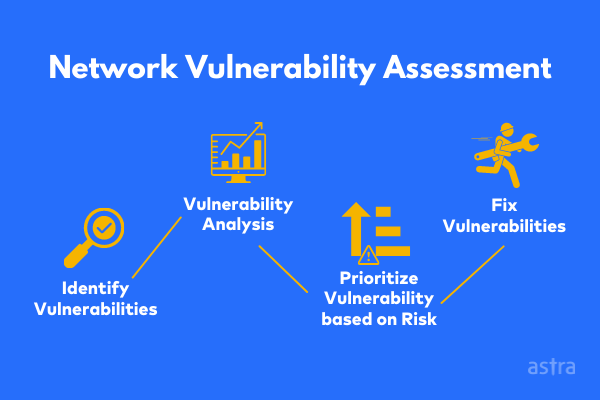
There are many factors to consider when conducting a network vulnerability assessment, but some of the most important aspects include:
- Identifying all network systems and devices in your network infrastructure
- Determining how these systems and devices are interconnected
- Analyzing system configurations and installed software for known vulnerabilities
- Scanning for open ports and services that could be exploited
- Testing for weak passwords or other authentication issues
Read Also: Top 6 Web Pentest Tools You Should Not Miss in 2022
Why is Network Vulnerability Assessment Necessary?
As we’ve already discussed, network security breaches are becoming increasingly common and costly. It is necessary to know the potential security vulnerabilities in the network infrastructure.
Organizations must secure their networks and applications from any kind of hacking threats or cyberattacks. To do this, individual organizations can implement application and network security controls. And one of the critical network security controls/practices is to perform an in-depth network vulnerability assessment.
Conducting a network vulnerability assessment helps organizations to detect any kind of weaknesses in their system before attackers do. It also provides detailed information on how to fix those vulnerabilities with priority.
Not only that but network vulnerability assessment is also required by many compliance standards such as PCI-DSS, HIPAA, SOX, ISO, etc.
Also Read: 10 Best Cyber Security Audit Companies [Features and Services Explained]
Most Common Network Vulnerabilities
Unpatched software and operating systems
Unpatched software and operating systems are one of the most common causes of network vulnerabilities. Hackers can exploit these vulnerabilities in the network to further gain access to sensitive data or launch attacks on other organizations using the infected network devices (botnet).
Weak passwords
Weak passwords are another major cause of network vulnerabilities. Hackers can use brute force attacks to guess weak passwords and gain access to sensitive data.
Open ports and services
Open ports and services are also a critical element to look at when you’re planning to secure your network. An attacker can bypass your security controls via open ports and can further harm your network systems by gaining access to it.
Insecure Wireless Networks
One of the most common types of vulnerabilities is an unsecured wireless network. Hackers can easily exploit these networks to gain access to sensitive data or launch attacks on other systems.
Lack of encryption
Another common vulnerability is a lack of encryption. This leaves any data vulnerable to interception by hackers.
Also Read: Top 5 Software Security Testing Tools in 2022 [Reviewed]
Best Practices to Prevent Network Compromise or Data Breach
Now that we’ve discussed some of the most common network vulnerabilities, let’s take a look at some best practices to prevent them.
1. Patch systems and software regularly
One of the best ways to prevent network vulnerabilities is to patch or update systems and software on a regular basis. The updated software and systems will help reduce vulnerability exploitation risks as well as prevent you from attacks that could be performed on vulnerable/older versions of systems or software.
2. Use strong passwords
Another important practice is to use strong passwords for your network access control and admin areas in your networking devices. Strong passwords such as passphrases are difficult to guess and they can easily prevent any unauthorized access using any automated tools such as brute-forcing.
3. Use two-factor (2FA) authentication for access
Enabling two-factor authentication for yourself and your team members can be very effective to improve the security posture of your organization. The 2FA requires users to provide two forms of identification, such as a password and a fingerprint or an access card before they can gain access to sensitive data.
4. Encrypt your data
Enabling encryption for your data at rest and in transition is another best practice for preventing network and data breaches. The encryption allows organizations to transform their readable data into an encrypted data format. This can stop hacking attacks because the data is now encrypted.
5. Implement user access control to secure sensitive data
Implementation of proper user authentication and giving user-level or admin-level privileges to only authorized and trusted users can secure the sensitive data of your and your customers from falling into the hands of hackers. For example, only allowing administrators to access certain areas of the network.
6. Monitor network activity
There are dedicated companies in the cybersecurity industry that only offer network monitoring solutions. And by knowing this you can guess how important it is to regularly monitor your network in real-time. Network monitoring is as important as any other network security control. It allows an organization to see any unauthorized intrusion and incoming or outgoing network attack traffic. This helps to take immediate actions to remedy or prevent the intrusion.
7. Use network security solutions
There are many different network security solutions available that can help to protect against attacks. These solutions can include firewalls, intrusion detection systems, antivirus software, zero-trust network security, DDoS mitigation solutions, etc.
8. Perform regular VAPT for your network devices
Performing periodic vulnerability assessments and pentest for your organizations’ network assets can assist with recognizing any security weakness in the network that could be taken advantage of by hackers. These tests can likewise assist with the decision of implementing network security practices to patch security weaknesses before these are exploited in the wild by hackers.
The vulnerability scanning and pentest also help you achieve certain pentesting compliance for GDPR, PCI-DSS, HIPAA, etc.
Also Read: What is Network Vulnerability Scanning? The Ultimate Guide
Steps to Conduct Network Vulnerability Assessment
Now that we’ve discussed some of the most common network vulnerabilities and best practices to prevent them, let’s take a look at the steps involved in conducting a network vulnerability assessment.
There are typically four steps involved in conducting a network vulnerability assessment:
Step One: Planning
This includes identifying the scope of the assessment, setting up the test environment, gathering any necessary tools and resources, and doing any further planning and preparation to begin with a network vulnerability assessment.
Step Two: Data Collection
The next step is to collect data about the network. This data can be collected manually or through automated means. It should include information about the network architecture, devices, and configurations.
Step Three: Scanning, Analysis and Reporting
Once all of the information about the network has been collected, it needs to be analyzed properly in order to identify any potential vulnerabilities.
Organizations can use different automated vulnerability scanners to scan their networks for vulnerabilities. After the vulnerabilities have been identified in scan results, they need to be documented in a comprehensive report that can guide on steps to reproduce and fix these vulnerabilities.
Step Four: Remediation
The final step is to remediate any vulnerabilities that were identified. This can involve patching systems and software, changing configurations, or implementing new security measures.
By following these steps, organizations can conduct a thorough assessment of their network and identify any potential vulnerabilities and security loopholes.
Top 4 Free Tools for Network Vulnerability Assessment
There are many different open-source and commercial tools available for conducting a network vulnerability assessment. Some of the most popular open-source tools include:
- Nessus (essentials): Nessus essentials is a remote vulnerability scanning developed by the company Tenable. It can be used to scan your system and applications for security weaknesses. Nessus is available in both free and paid versions. The paid version is named Nessus professional.
- OpenVAS: Open Vulnerability Assessment System (VAS), also known as GNessUs is an open-source vulnerability scanner that is a part of Greenbone Vulnerability Manager (GVM). OpenVAS has some matching features of the tool Nessus.
- Nmap: Nmap (also known as network mapper) is a free and open-source network exploration tool developed by network security expert Gordon Lyon. This tool helps you with security audits of your network. It sends malicious network traffic and analyzes the response from the network device.
- Wireshark: Wireshark is another widely-used open-source network security tool that helps you with network packet capture, analysis, monitoring, troubleshooting, and more.
These are just some of the many different tools available for conducting a network vulnerability assessment. By using these tools, organizations can identify any potential weaknesses in their network and take steps to remediate them.
Also Read: 11 Top Penetration Testing Tools of 2022 [Reviewed]
Why Choose Astra Pentest for Vulnerability Assessment?
Astra Pentest offers a variety of robust and unique features that puts Astra Pentest at the top when compared with other VAPT providers. It is a comprehensive security suite that includes vulnerability assessment, penetration testing, and vulnerability management.
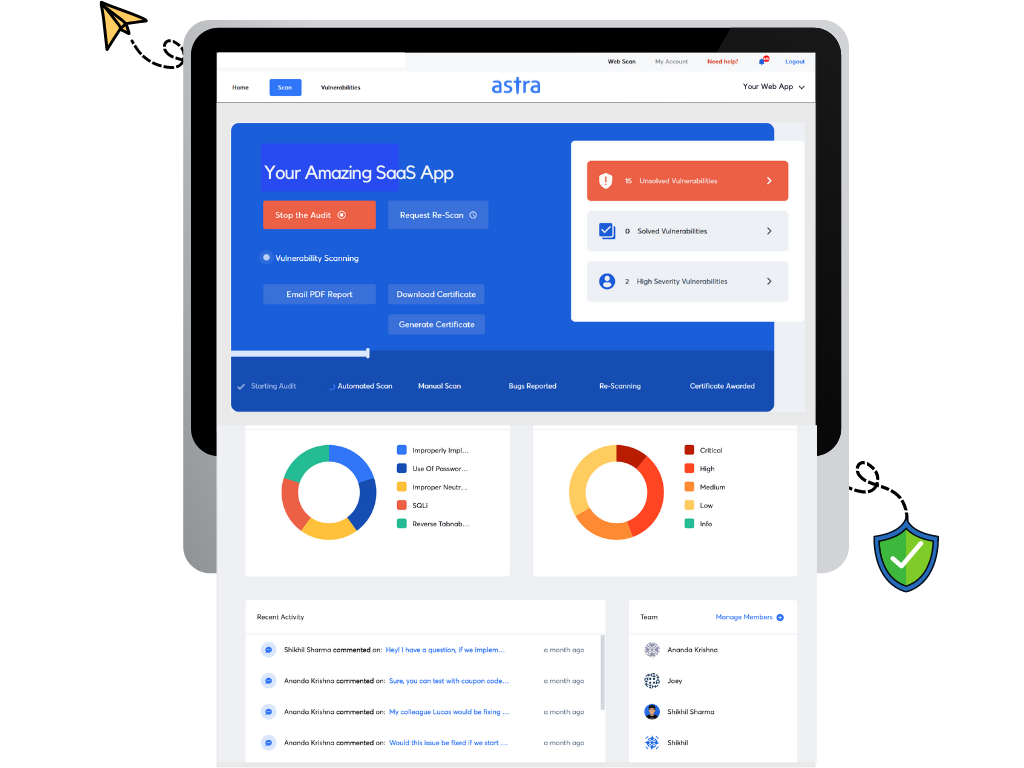
There’s much to talk about Astra Pentest, but for now, just to keep it short, let’s just look at the amazing features Astra Pentest provides:
- Continuous Scanning using Automated Vulnerability Scanner.
- A mix of Automated and Manual Penetration Testing with over 3000 test cases.
- Detailed vulnerability analysis with risk-grading, potential loss in $, CVSS score, severity, impact, etc.
- A collaborative Vulnerability Management Dashboard.
- CI/CD and Integration (with Gitlab, GitHub, Jenkins, Slack, Jira, etc.)
- Dedicated Pentest Compliance Dashboard with separate test cases for ISO27001, GDPR, PCI-DSS, SOC2, and HIPAA.
- Publicly verifiable Pentest Certificate and more.
Final Thoughts…
Network vulnerability assessment is a process that should be done regularly in order to identify and address any potential vulnerabilities. By using the steps and tools outlined in this article, you can conduct your own assessment quickly and effectively. Having a secure network is essential for protecting your data and your customers’ data, so make sure to take the time to perform a thorough assessment on a regular basis.

















Loved how thorough it was. I keep checking your posts, they’ve been very helpful, thanks.
Thanks Charlene. I’m glad to you like my articles. 🙂