Vulnerability assessment aid in finding out pesky vulnerabilities lying within a security system be it for networks, web applications, or more through a thorough vulnerability analysis. This article will deal with providing a detailed view of what it is along with some vulnerability assessment examples.
What is Vulnerability Assessment?
Vulnerability assessment is the process of detecting the vulnerabilities extant in your systems, analyzing them, and finding out ways to fix them. It’s a popular form of security testing where you use automated tools to scan your systems for vulnerabilities and categorize them according to their severity.
Some vulnerability assessment examples include network vulnerability assessments, mobile application vulnerability assessments, web app vulnerability assessments, and database assessments.
Importance of Vulnerability Assessments
Let us understand the impact a vulnerability can have on your organization with an example:
You run a WooCommerce store with a stable stream of orders. Now, a hacker decides to buy some stuff from your website for a tiny fraction of its actual cost through PayPal. He picks some products, adds them to the cart, put the billing details in, and then put a traffic interceptor into action while proceeding to PayPal. He’d intercept the request and tamper with the vulnerable parameters to change the price. That way he can get an item worth $100 for $1 or for free if he wants.
Now, the hacker would fail if the IPN (instant payment notification) validation is up, and it invalidates the order, but if the hacker finds a way around it, you are set up for loot. To protect your websites from this sort of exploitation, make vulnerability assessments a habit.
The Advantages of Vulnerability Assessment of a System
Here are some of the important advantages of carrying out vulnerability assessments:
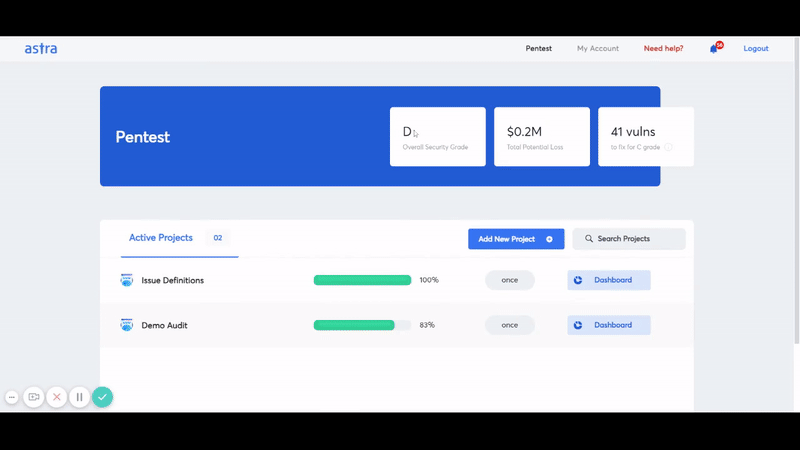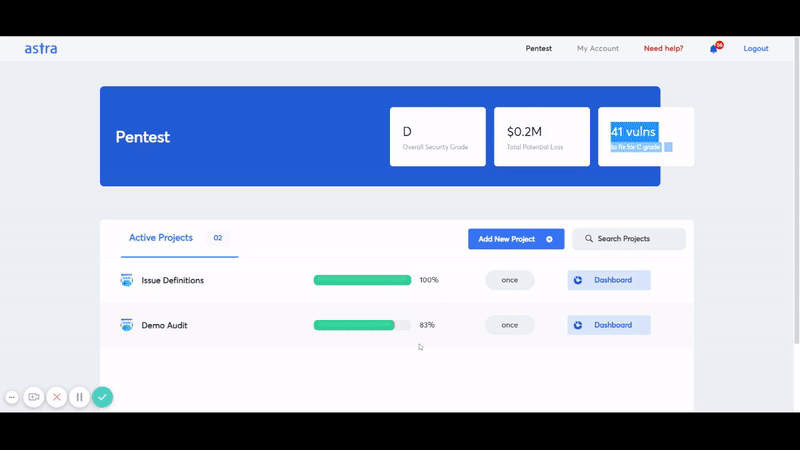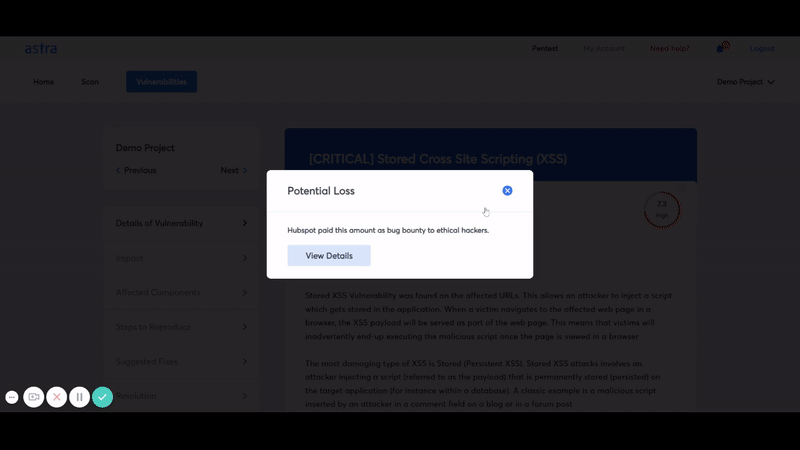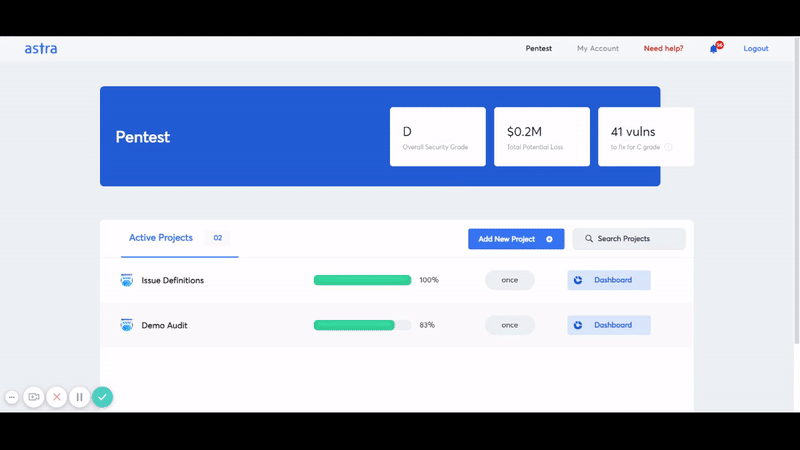
- Maintain Compliance: You need it to maintain compliance with security regulations relevant to your industry vertical. You can use the compliance reporting feature in Astra’s Pentest dashboard to get a picture of your compliance situation as the vulnerability scan report is produced.
- Improved Security Posture: Improving your security posture has a direct impact on your revenue stream. It also allows you to rest easy knowing your assets are secure.
- Build Trust: It also helps you build customer trust and retain the trust and loyalty you have acquired over the years.
Types of Vulnerability Assessments?
There are several types of security vulnerability assessments:
1. Network Vulnerability Assessment
In network vulnerability assessment, vulnerabilities in the network infrastructure, including devices, systems, and applications are scanned and detected for remediation.
2. Application Vulnerability Assessment
This type of assessment focuses on identifying vulnerabilities in web applications, mobile applications, and other software applications.
3. Host vulnerability assessment
This type of assessment has an advantage in identifying vulnerabilities in individual systems or servers.
4. Physical vulnerability assessment
This assessment focuses on identifying vulnerabilities in physical security controls, such as locks, doors, and other physical access controls.
5. Cloud vulnerability assessment
Focuses on identifying vulnerabilities in cloud-based systems, including cloud applications, infrastructure, and services.
6. Wireless network vulnerability assessment
Identification of vulnerabilities in wireless network infrastructure, including access points, routers, and other wireless devices.
What Threats Can Be Avoided by Vulnerability Assessments?
Performing vulnerability assessments can help organizations avoid a wide range of security threats, including:
- Unauthorized access: Vulnerability assessments can identify vulnerabilities that could be exploited by hackers to gain unauthorized access to sensitive data or systems.
- Data breaches: By identifying vulnerabilities in software applications and systems, vulnerability assessments can help prevent data breaches that could compromise sensitive data.
- Malware infections: It can identify weaknesses in systems and applications that could be exploited by malware, helping organizations prevent infections.
- Denial of service (DoS) attacks: By identifying vulnerabilities in network infrastructure, vulnerability assessments can help prevent DoS attacks that could disrupt critical services.
- Insider threats: Vulnerability assessments can help identify vulnerabilities that could be exploited by insiders to gain unauthorized access to sensitive data or systems.
Best Practices in Vulnerability Assessment
Here are some of the best unavoidable practices to be followed for vulnerability assessments.
1. Frequent Vulnerability Scans
Ensure to carry out frequent vulnerability scans as vulnerabilities can arise at any point within a system for example upon releasing a glitchy update. It is vital to scan for known vulnerabilities, CVEs, and vulnerabilities based on bug bounty reports, OWASP Top 10, and SANS 25.
2. Scan Behind Logins
Here the credentials for the web asset are provided to a login recorder which is then used to access the website to check for vulnerabilities internally. This is important to discover any issues with role-based access, authentication, and authorization.
3. Prioritization of Vulnerabilities
Upon detection and identification of vulnerabilities, they should be prioritized by the vulnerability assessment provider so that remediation becomes an easy chore for you. It enables you to take up the most critical vulnerabilities initially without wasting time on low-priority flaws.
4. Detailed Vulnerability Reports
The provision of detailed vulnerability reports is another best practice that shouldn’t be ignored. A good vulnerability report mentions the list of vulnerabilities, their CVSS and risk scores based on prioritization as well detailed information and remediation steps possible for each vulnerability at length.
What is meant by authenticated and unauthenticated vulnerability assessment?
You would often come across a feature – authenticated vulnerability scanning – while looking for vulnerability assessment tools. What does it mean? Well, an authenticated vulnerability scanner can scan the pages behind the login screen whereas an unauthenticated scanner can perform a perimeter scan from the outside.
Authenticated vulnerability assessment has some clear benefits, such as:
- The discovery of hidden vulnerabilities
- Fewer false positives
- Visibility into OS functions, applications, inventory, and configuration
- A detailed picture of patch requirements.
This is a very important feature but a handful of vulnerability assessment providers have this figured out. Astra Security’s login recorder extension, for instance, makes scanning behind the login screen very simple for the users. They can allow to authenticate with the scanner once and forget about it.
How To Perform A Vulnerability Assessment?
We can divide the entire process of vulnerability assessment into three simple parts.
1. Scope Of Vulnerability Assessment
The first step is to determine the scope of the vulnerability assessment. This depends on the assets that you want to scan for vulnerabilities. According to the scope of the scan, you can decide whether to use an application scanner, network scanner, or host-based scanner.
2. Vulnerability Scans
The second step is the vulnerability scan. In this step, the automated scanner uses a vulnerability database to scan the target system for common vulnerabilities.
3. Vulnerability Analysis
The vulnerabilities found during the vulnerability scans are identified and analyzed based on their risk level for prioritization during remediation.
4. Vulnerability Assessment Report
Then comes the vulnerability assessment report. It documents the vulnerabilities that were found during the scan along with their CVSS score. It also suggests necessary steps to fix a certain vulnerability.
5. Vulnerability Remediation
Once you have received the vulnerability scanning report, it is time for vulnerability remediation. You can assign the vulnerabilities to the developers in your company, who can follow the suggestions in the report and consult security experts if need be, to fix the issues detected.
What is the significance of a vulnerability assessment report?
A vulnerability assessment report lists down the vulnerabilities found in a system according to their severity, and the risk they pose to the system and to the organization. It plays an important part in the vulnerability management cycle.
The vulnerability assessment report
- helps you prioritize the critical vulnerabilities,
- helps the developers find the fixes faster,
- helps you understand the standing of your organization with respect to compliance requirements.
How Are Vulnerability Assessment and Penetration Testing Different?
As you’ve already figured, vulnerability assessment is a mostly automated process that helps you detect common vulnerabilities in a system. Manual penetration testing tackles the limitations posed by vulnerability assessment which include false positives, no human support, and missing vulnerabilities.
Differences of pentesting over vulnerability assessments include:
- The involvement of human intelligence makes it easier to uncover difficult vulnerabilities.
- Manual pentesters can ensure zero false positives.
- Pentest reports are more exhaustive and contain thorough guidelines for remediation.
- Some pentest companies like Astra Security offer expert remediation support through collaboration with the developers.
Limitations of Vulnerability Assessment
Vulnerability assessments have some limitations, they include:
- The automated scanner misses some vulnerabilities.
- False positives are a devastating problem when you’re trying to run an agile development process.
- Remediation guidance is not too robust.
- There is no human support available if developers hit a roadblock trying to follow the fix guidelines.
The Top 5 Vulnerability Assessment Tools
1. Astra Pentest
A feature-rich tool for automated vulnerability scanning and manual pentesting. It is a comprehensive solution with provisions for continuous scanning, scanning behind the login screen, and CI/CD integration.
2. Tenable Nessus
Nessus is a powerful vulnerability scanning tool with features like malware detection, asset discovery, sensitive data discovery, and configuration error discovery.
3. Wireshark
Wireshark is a useful network protocol analyzer. It is a great tool for protocol inspection and analysis of live data on a network.
4. Burp Suite
Burp Suite is a widely used tool for request interception, automated pentest, brute forcing, fuzzing, and vulnerability scanning.
5. Acunetix
Acunetix has a powerful vulnerability scanner that works wonderfully for detecting web misconfigurations, web security scanning, and password testing.
Advantages of Using Astra Security
Astra Security offers both automated vulnerability scanning and manual pentesting. The combination of both approaches makes it a perfect tool for any business across industries. The vulnerability assessment tool by itself is an elegant tool with top-of-the-charts features.
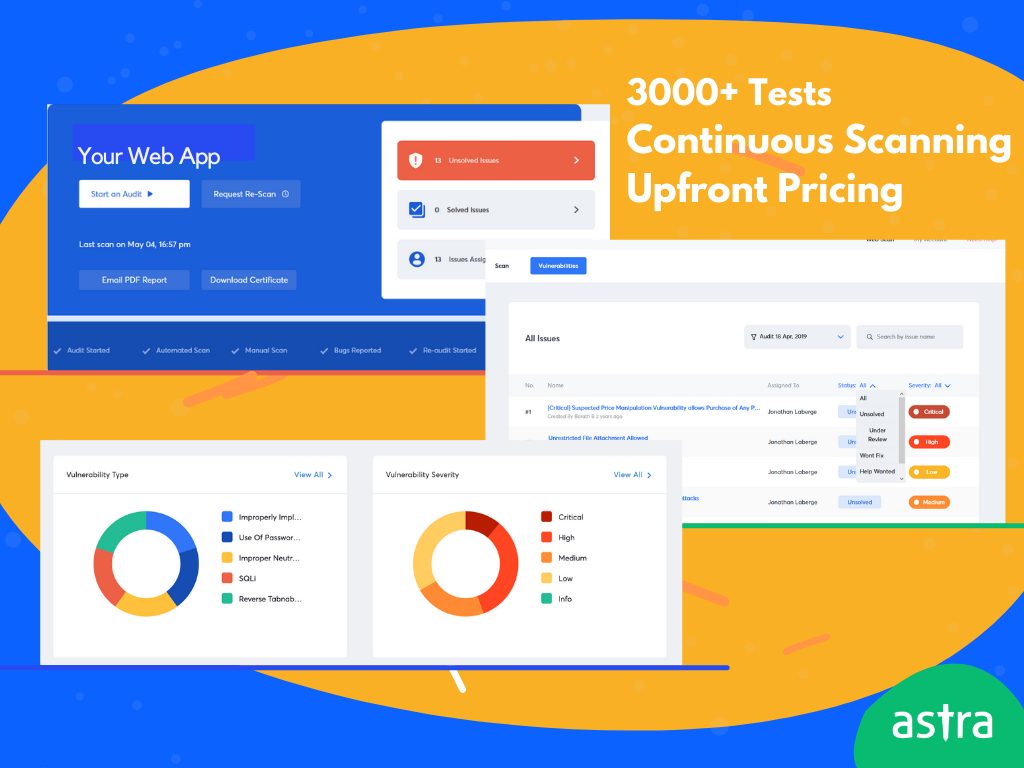
- 8000+ tests adhering to OWASP top 10, SANS 25, and covering ISO 27001, SOC2, HIPAA, and GDPR compliance requirements
- CI/CD integration ensuring continuous scanning of your web application with every code update
- Intuitive dashboard for vulnerability monitoring and management.
- Compliance monitoring within the pentest dashboard.
- Step-by-step guidance for remediation
The detailed vulnerability assessment report with risk scores for each vulnerability helps you prioritize critical vulnerabilities. The security engineers and researchers at Astra stay on their toes to include new CVEs in the scanner database as soon as they’re discovered ensuring that your systems get minimum exposure to new threats.
The manual pentest by Astra’s security experts on top of the vulnerability assessment ensures zero false positives, detection of business logic errors, and other hidden vulnerabilities. And you can collaborate seamlessly with the security experts to remediate the issues.
Conclusion
Periodic vulnerability assessment is no longer a choice, it has become a compulsion for businesses given the current cyber threat landscape. However, it does not have to be a hurdle. With the right tool, the right strategy, and the right vulnerability assessment partner, you can easily integrate vulnerability assessment with your SDLC. With some support from security experts, you can turn the vulnerability scanning exercises into a high ROI event. The sooner you implement it, the better.
How to know if anyone needs vulnerability assessment?
Vulnerability assessments are vital and highly recommended after any update to the system as well as regularly for the maintenance of asset security. It is a good practice to conduct a vulnerability assessment once in two weeks or a month. It is ideal for SMEs, government organizations, and large enterprises.
What is the purpose of vulnerability assessment?
Vulnerability assessments are carried out with the purpose of detecting vulnerabilities within different assets like web and mobile applications, network security, and cloud infrastructure. It is done to identify and mitigate vulnerabilities before they are exploited by hackers.
















