Network vulnerability scanning refers to the thorough hacker-style inspection of network ports and systems to detect vulnerabilities that can affect security and possibly lead to a breach. Network vulnerability scanning can be performed on firewalls, switches, routers, wireless access points, and other networking devices.
There are a few different tools that do vulnerability scanning, but most of them are just a server’s or network’s worst nightmare. That’s what this blog is going to look at in terms of what, why, and how on network vulnerability scanning.
What is Network Vulnerability Scanning?
Network vulnerability scanning is the process of detecting vulnerabilities in network systems, network devices, and network services. The vulnerabilities can be a result of misconfiguration, open ports, or outdated software running on the network and can be exploited easily by hackers.
Network vulnerability scanners are a critical part of any IT organization’s arsenal. They are used to detect security issues in the network by performing a comprehensive analysis of the network to identify holes in the network security.
Also Read: Top 7 Cyber Security Auditors for SaaS Companies | 10 Best Cyber Security Audit Companies [Features and Services Explained]
What is the importance of Network Vulnerability Scanning?
Network vulnerability scanning is an essential part of any IT department’s security infrastructure. Although it’s an essential part of any IT department’s security infrastructure, there is still some confusion as to what network vulnerability scanning really is, as well as what it does, and why you might use it.
Network vulnerability scanning is an integral part of the security assessment process of any network or system. It is a complex process, given the number of systems that need to be scanned, so it is best to approach this in an organized and systematic way.
Network vulnerability scanning is a great way to gauge the security of your network. It helps you identify the weak points in your system that you need to patch up. This blog will take you through a complete guide to understanding these scans and how you can use them.
Also Read: Network Security Testing and Best Network Security Tools in 2022
Understanding Top 3 Network Vulnerabilities
Most of the security breaches that we hear about in the news are network breaches. If a network is vulnerable to attack, the network is vulnerable to network vulnerabilities. It is at the network level that many attacks begin, including traditional breaches and sophisticated malware attacks.
It is a good idea to understand network vulnerabilities so that you can take steps to prevent them. There are three main network vulnerabilities that you will want to understand:
1. Misconfigured devices
Misconfigured devices are easily accessible to attackers through which they can access other devices in the network. In a majority of cases, attackers use misconfigured devices in order to expand their presence within a target network. This is also a good way to collect privileged information. All it takes is a single misconfigured device to compromise the entire network.
2. Unpatched systems
Organizations often neglect updating their systems and this makes them vulnerable to attacks. This security hole can be easily exploited by attackers. The unpatched systems are open to vulnerabilities and cybercriminals can easily send in viruses, Trojans and Ransomware.
This increases the risk to the organizations and the customers as well. At Astra, we have come across many organizations that have not updated their systems for the last several years. This has led to the creation of a vast number of vulnerabilities that can be exploited by attackers.
3. Human error
Humans are the weakest link in the security chain. It’s quite easy for an attacker to trick employees to gain access to the network. For example, social engineering is one of the most common methods used by attackers to gain access to the network.
Best Practices to avoid Network Security Risks
Network security risks are a serious threat to any business. It is important to take preventive measures to avoid these risks and ensure that your business functions smoothly without any interruptions. The following are four best practices that you can implement to ensure a secure network.
1. Segmentation of network
Segmentation of network means that you separate the network into different segments. This way you can provide security to your network. You need to ensure that the internal network is not connected to the external network. The machines present in the internal network are not accessible from the external network.
2. Network Vulnerability Scanning
There is no way to avoid security threats, but you can minimize these threats by performing network vulnerability scanning on a regular basis. The scanning helps in detecting the vulnerabilities in the network and removing them.
3. Backup
Back up your data on a regular basis so that you can recover it if you face any data loss due to any security breach.
4. Install an IPS/IDS
Make sure to have an IPS or an IDA installed on your network. This software provides the necessary protection against malicious attacks on the network.
Top 3 Open Source Network Vulnerability Scanning Tools
Network vulnerability scanners are used to scan systems or networks for possible security vulnerabilities. These scanners require a lot of time and effort to manually test systems and networks for vulnerabilities.
Open source network vulnerability scanning tools can be used to automate the process of network scanning. These tools are free and can be used to test both networks and individual systems.
The following are some of the best open source network vulnerability scanning tools:
1. NMAP
Network Mapper, or Nmap, is an open-source utility for network exploration, security auditing, and network discovery. It was designed to rapidly scan large networks, although it works fine against single hosts.
2. Wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Wireshark can be used to capture and interactively browse the contents of network traffic.
3. Metasploit
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is open-source, free, and available to the public.
Furthermore, open-source scanning tools can be used to test networks of any size.
Also Read: 11 Best Penetration Testing Tools/Software of 2022 [Reviewed]
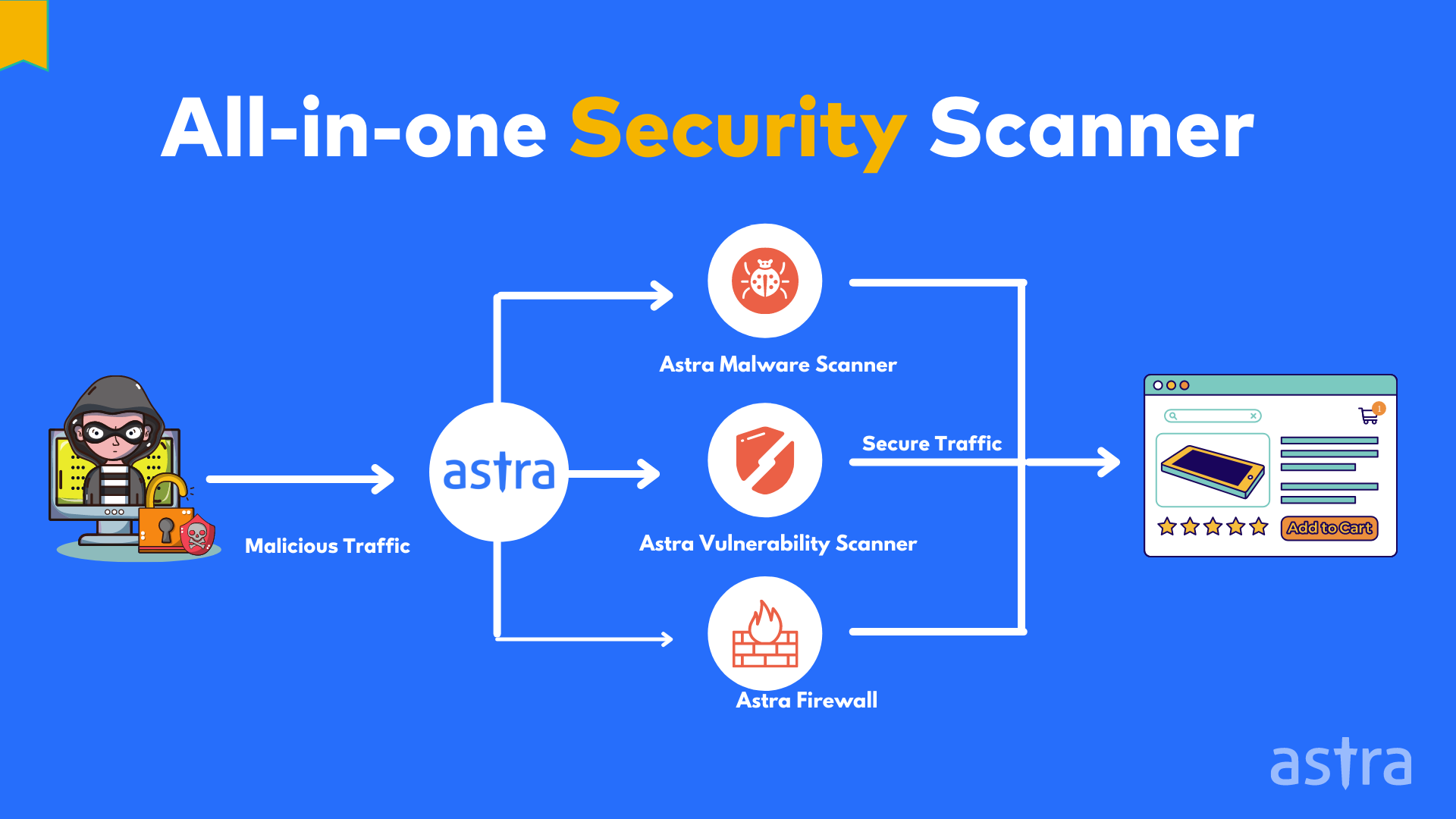
Why Choose Astra Security for Network Vulnerability Scanning?
Astra Security is a Top rated Network Vulnerability Scanning company. We have a team of professional pentesters and auditors who are skilled in network penetration testing and network security management.
At Astra, we provide the best network vulnerability scanning and network security services to our clients. We help you to reduce security risks by providing you with the right set of tools and services. Our network vulnerability scanning services include network pentesting, network auditing, network monitoring, network security management, and much more.
Conclusion
Network vulnerability scanning is an essential practice for any company that is concerned with its business continuity. This blog post has provided you with comprehensive information on network vulnerability scanning, as well as how to get started with a network vulnerability scanner. If you have any questions about network vulnerability scanning or how to get started with a network vulnerability scanner, please contact us anytime. Thank you for reading!
What is the cost of Network Vulnerability Scanning?
Depending on the scope of the scan, a network vulnerability assessment can cost up to $200
How is network vulnerability scanning different from web app vulnerability scanning?
In the case of web app vulnerability scanning, the scope of the scan is limited to the application at hand, whereas a network vulnerability scan takes all the apps and services running on a network.
















